Software as a Service (SaaS) is a cloud-based delivery platform where all software applications are hosted by a service provider of your choice. The software capabilities are available to customers exclusively over the Internet. Rather than purchasing and installing software on individual computers or local servers (which would need to be purchased separately), users remotely subscribe to SaaS applications and access them remotely.
SaaS Architecture offers several benefits, and its importance has only increased in the last year. There are no signs that this trend will reverse in the coming years.
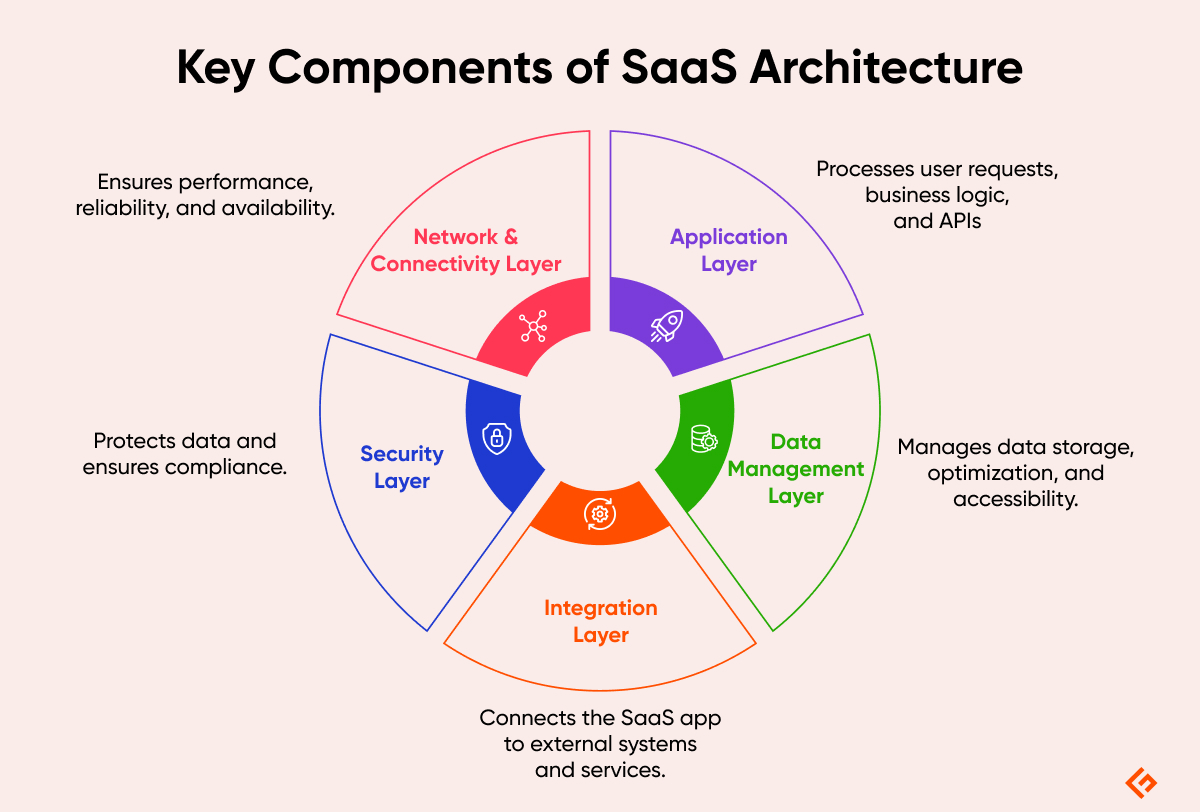
A solid SaaS architecture is foundational for ensuring the success of a SaaS application. Below are the critical components that achieve this state:
- Scalability is implemented by elastic resources, heavy usage of microservices, and leveraging load balancing and caching techniques.
- Security is accomplished by shared responsibility models, data isolation techniques, and robust continuous monitoring.
- Efficiency is demonstrated by optimized resource utilization, implementation of continuous integration and continuous deployment (CI/CD), and robust logging and diagnostic tools.
What is SaaS Architecture?
SaaS architecture is the underlying structure of a Software as a Service application. It’s a platform owned by a third-party provider and designed to provide software to users over the Internet. It involves multi-tenancy, where a single instance of the application serves multiple customers and integrates capabilities for communication with other systems.
This architecture contains cloud-based infrastructure, microservices, APIs, CI/CD pipelines, and monitoring tools to ensure software delivery and operation.

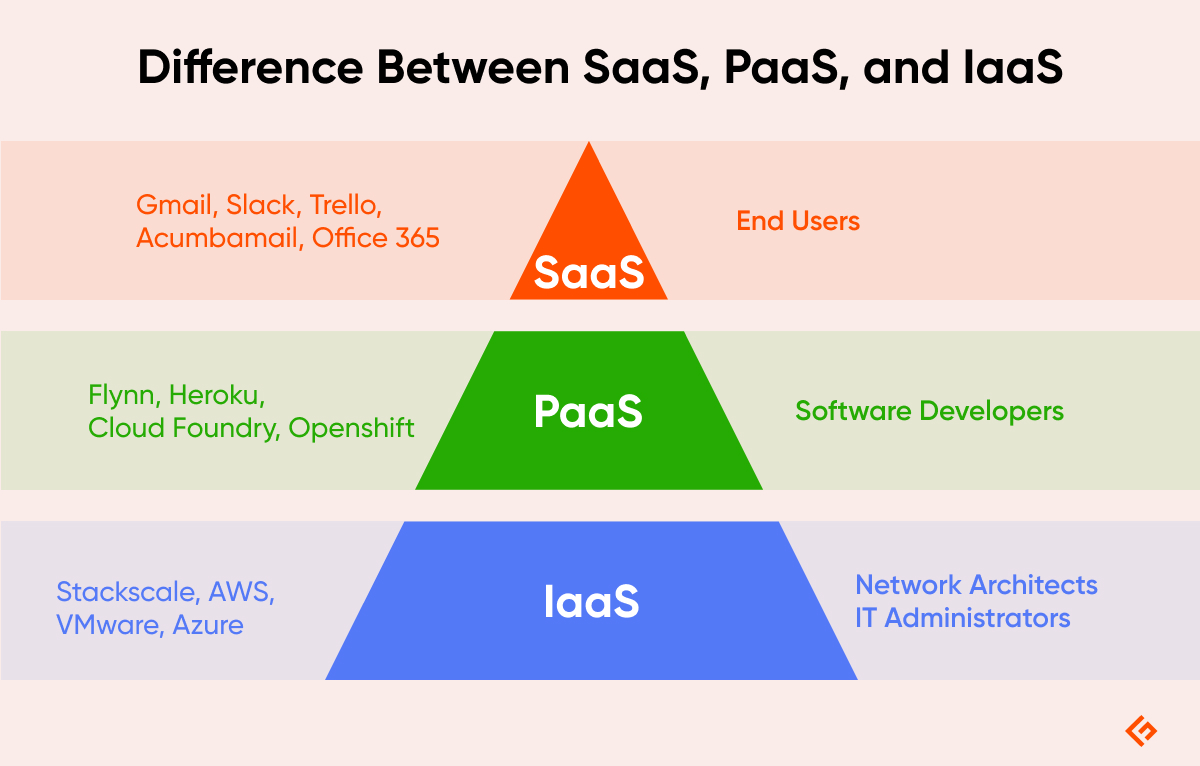
Difference Between SaaS, PaaS, and IaaS
Apart from SaaS, there are other cloud service types, namely Platform as a Service (PaaS) and Infrastructure as a Service (IaaS). The primary difference between SaaS, PaaS, and IaaS lies in the level of control and responsibility the user has over the IT environment and applications.
SaaS
- Provides ready-to-use software applications over the internet.
- Users have the least control. They only manage application settings and data.
- The SaaS provider handles the infrastructure, middleware, application software, and security.
- Examples include Salesforce, Google Workspace, and Microsoft 365.
PaaS
- Provides a platform to develop, run, and manage applications. It only serves the tools developers will need to implement their software, but it does not include underlying infrastructure maintenance to be in the hands of developers.
- Users control the applications and data while the PaaS provider manages operating systems, middleware, runtime, and infrastructure.
- The user is responsible for developing and managing the applications. The provider maintains the platform environment.
- Examples include Google App Engine, Microsoft Azure, and Heroku.
IaaS
- Provides virtualized computing resources over the internet.
- Users have the most control. They manage operating systems, applications, storage, and network configurations. That also means users have to maintain most of the overall cloud solution components.
- The provider handles the physical hardware, networking, storage, and virtualization. Users are responsible for everything else above this layer.
- Examples include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
To sum it up, SaaS provides the least control but the most convenience, while IaaS offers the most control but the least convenience. PaaS represents a balance point where users focus on application development without worrying about infrastructure.
Multi-Tenant Facility
SaaS architecture is created to facilitate multi-tenancy use cases. This means multiple customers (tenants) share the same infrastructure and codebase but do not share data. Any customization is specific to each customer, and the performance of the environment would affect others if one or more users are utilizing the resources with some high loads (scalability factor).
To understand it in more detail, we need to examine specific components of SaaS multi-tenancy.
1. Shared Infrastructure
Multi-tenant SaaS applications run on one shared hardware, networks, and storage. This is how it optimizes resource utilization.
Sharing infrastructure reduces costs and creates economically interesting solutions for both the provider and customers.
2. Data Isolation
While tenants share the same database, logical isolation mechanisms (such as tenant ID columns) ensure that each tenant’s data is kept separate. It would be a serious security breach if tenants could see each other’s data. Even if the infrastructure is shared, the data must not be shared in any way.
Data encryption at rest and in transit adds an additional layer of security, which is in addition to the requirement that data be inaccessible to other tenants.
3. Tenant Context
All components of the application are tenant-aware. This simply means the components of the architecture can identify and appropriately handle data and configurations separately for different tenants.
SaaS architecture uses configuration management to store tenant-specific settings, which leads to better customization within a shared codebase.
4. Scalability
Cloud infrastructure has built-in specific functionality that allows the SaaS application to scale its resources dynamically. This can be further tailored to concrete tenant demand so that the application’s performance stays consistent.
Scaling alone would not solve the problem of a sudden, huge increase in request demands. Efficient load balancing across servers ensures balanced resource usage horizontally (spreading the load between more parallel infrastructures configured alike).
5. Shared Codebase
A single codebase simplifies maintenance and updates, as new features and fixes are deployed across all tenants simultaneously.
Proper version management practices are essential to ensure that customizations for specific tenants do not interfere with the core codebase.
6. Customization
Tenants can enable or disable features based on their needs through configuration settings. You can do this even without changing the underlying code.
Additionally, UI themes and branding can be customized on a per-tenant basis to provide a personalized approach.
7. Monitoring and Analysis
Monitoring tools can track performance and usage metrics at the tenant level to ensure issues are identified in time.
In addition, aggregated analytics provide insights into overall system performance and help the provider make data-driven decisions for capacity planning.
Key Components of SaaS Architecture
Now, let’s break out the different layers of SaaS architecture and explain what role each plays. From there, we will explain how they cooperate with each other. This synergy and integration between the layers is obviously very important. It will define how effective the platform as a whole will be in delivering your results.
Application Layer
The Application Layer is a critical component of the SaaS architecture, as it bridges the user interface and the data storage layers. This layer is responsible for processing requests coming first-hand from the users. It implements business logic and provides APIs for integration with other systems.
The layer performs calculations, transformations, and validations on the data to meet business requirements before presenting the results to the user. The application layer also ensures that operations such as database updates and financial transactions comply with the application’s integrity rules.
The importance of the application layer sits in the following three aspects:
- Performance means how efficiently it handles business logic and data processing. Result in faster response times. This is crucial for maintaining a high-performance user experience.
- Flexibility is achieved by separating business logic from the UI and data storage. This is how you scale different parts of the application independently.
- Security, because it is your goal to protect the application from a wide range of security threats and to ensure compliance with regulatory standards.
The application layer consists of several standalone parts, which are listed below.
1. User Interface (UI)
The UI is the front-end part of the application that users interact with. It includes all the visual components that receive and present data to users, such as web pages, mobile app screens, or even dashboards.
A well-designed UI enhances the user experience by providing an intuitive and responsive interaction with the software. It also ensures that the application is accessible from various devices and platforms.
2. Business Logic
The business logic is the core computational part of the application that implements the rules and processes your business model shall deliver. It handles data processing, decision-making business rules, transaction flows, and data validations.
Centralizing business logic ensures that rules and processes are consistently applied across the application, regardless of the use case you are about to execute.
You also want to ensure that the business logic is modular. Only modularity will allow applications to scale over time as the scope increases.
Finally, by embedding security protocols and validations within business logic, the application can protect against unauthorized actions and data breaches.
3. Application Programming Interfaces (APIs)
APIs are sets of protocols and tools that allow software components to communicate with each other. They give you the endpoints through which external systems can interact with the application’s interfaces and visual inputs.
APIs are key integration components that interact with other applications and services. They effectively allow data exchange, and application functionality can be extended to support new features without disrupting the existing system.
Data Management Layer

The Data Management Layer is a fundamental component of SaaS architecture. It is responsible for managing all aspects of data handling and ensuring that data is organized, accessible, and protected.
Efficient data organization through appropriate database models (relational or NoSQL) ensures that data is easy to access and manipulate. Proper schema design, caching, and indexing are crucial for maintaining high performance and query optimization.
Data storage solutions must be scalable to accommodate growing data volumes over time. Flexibility in handling unstructured data through NoSQL databases and data lakes fulfills that need.
Well-designed data management reduces latency and can have a cross-layer impact on the users.
These are the key parts of the data management layer:
1. Databases
Relational Databases (RDBMS) organize data into predefined tables with rows and columns, using Structured Query Language (SQL) for data ingestion and manipulation. Those databases enforce ACID (Atomicity, Consistency, Isolation, Durability) properties, ensuring reliable transactions and data integrity. Examples of such databases include MySQL, PostgreSQL, Microsoft SQL Server, or Oracle Database.
On the other hand, NoSQL databases store and manage data without requiring a fixed schema. They accommodate a variety of data models, including document, key-value, graph, and column-family. They are designed to scale horizontally, handling large volumes of unstructured or semi-structured data. Examples of such databases include MongoDB, Redis, Cassandra, or Neo4j.
2. Data Storage
You can distinguish storage as primary and secondary. The first is for immediate, frequently accessed data storage to enable quick read/write operations necessary for application performance (SSD volumes, database server storage).
The second one’s main purpose is for long-term storage with less frequently accessed data, like backup and archival purposes (Amazon S3, Google Cloud Storage).
3. Data Management
You can organize the data inside a data warehouse or a data lake. A Data Warehouse consolidates and stores large volumes of structured data from multiple sources. The data is optimized for query and analysis. Amazon Redshift, Google BigQuery, and Snowflake are the most well-known examples.
Data Lake stores raw data in its native format, including structured, semi-structured, and unstructured data. This allows data scientists and analysts to perform various types of data processing. Examples include Amazon S3 (with AWS Lake Formation), Microsoft Azure Data Lake, and Google Cloud Storage (with BigLake).
4. Data Optimization
This is accomplished by several techniques, which usually have to be done in parallel to give the biggest advantage:
- Indexing improves the speed of data retrieval operations by creating data structures that enable fast queries.
- Partitioning divides large databases into smaller, more manageable pieces to improve performance.
- Replication ensures data availability and fault tolerance by copying data across multiple servers.
- Backup and recovery protect data against loss or corruption by creating copies that can be restored in case of failure.
Integration Layer
The Integration Layer in a SaaS architecture enables interaction between the SaaS application and other external systems and services. This layer facilitates data exchange and process synchronization, ensuring the application can operate within enterprise ecosystems.
The Integration Layer supports real-time (synchronous) and delayed (asynchronous) data exchanges. Each of them is suitable for various business needs. Data synchronization ensures that data updates are consistently made across different systems. That prevents data silos and inconsistencies.
By integrating with other systems, the SaaS application can automate complex workflows involving multiple steps and even a number of systems. Integration layer can facilitate event-driven architectures where actions in one system trigger automated workflows and processes in another.
These are the key parts of the integration layer:
1. Application Programming Interfaces (APIs)
APIs provide a standardized way for different software components to communicate. They define rules and protocols for accessing the functionalities and data of the SaaS application. APIs form modular integration, which makes it easy to scale and enhance the application by adding new functionalities or connecting additional systems.
REST APIs use HTTP requests to GET, PUT, POST, and DELETE data. They are used mainly because they are simple and scalable.
SOAP APIs are protocol-based and use XML for messaging. They offer a more rigid structure and are more reliable overall.
GraphQL APIs allow clients to specify the structure of the response data.
2. Middleware
Middleware is an intermediary layer that enables communication and data management between different systems. It handles tasks such as message transformation and routing. Middleware ensures that data sent from one system is transformed into the appropriate format for the receiving system. It abstracts the integration logic from the individual applications and reduces system dependencies.
There are various types of middleware:
- Message Brokers enable asynchronous communication between applications by routing, transforming, and queuing messages (e.g., RabbitMQ, Apache Kafka).
- Enterprise Service Bus (ESB) integrates various applications by routing and transforming data between them (e.g., MuleSoft, Apache Camel).
- Integration Platform as a Service (iPaaS) is a Cloud-based platform that provides tools for integrating cloud and on-premises applications (e.g., Dell Boomi, Jitterbit).
Security Layer
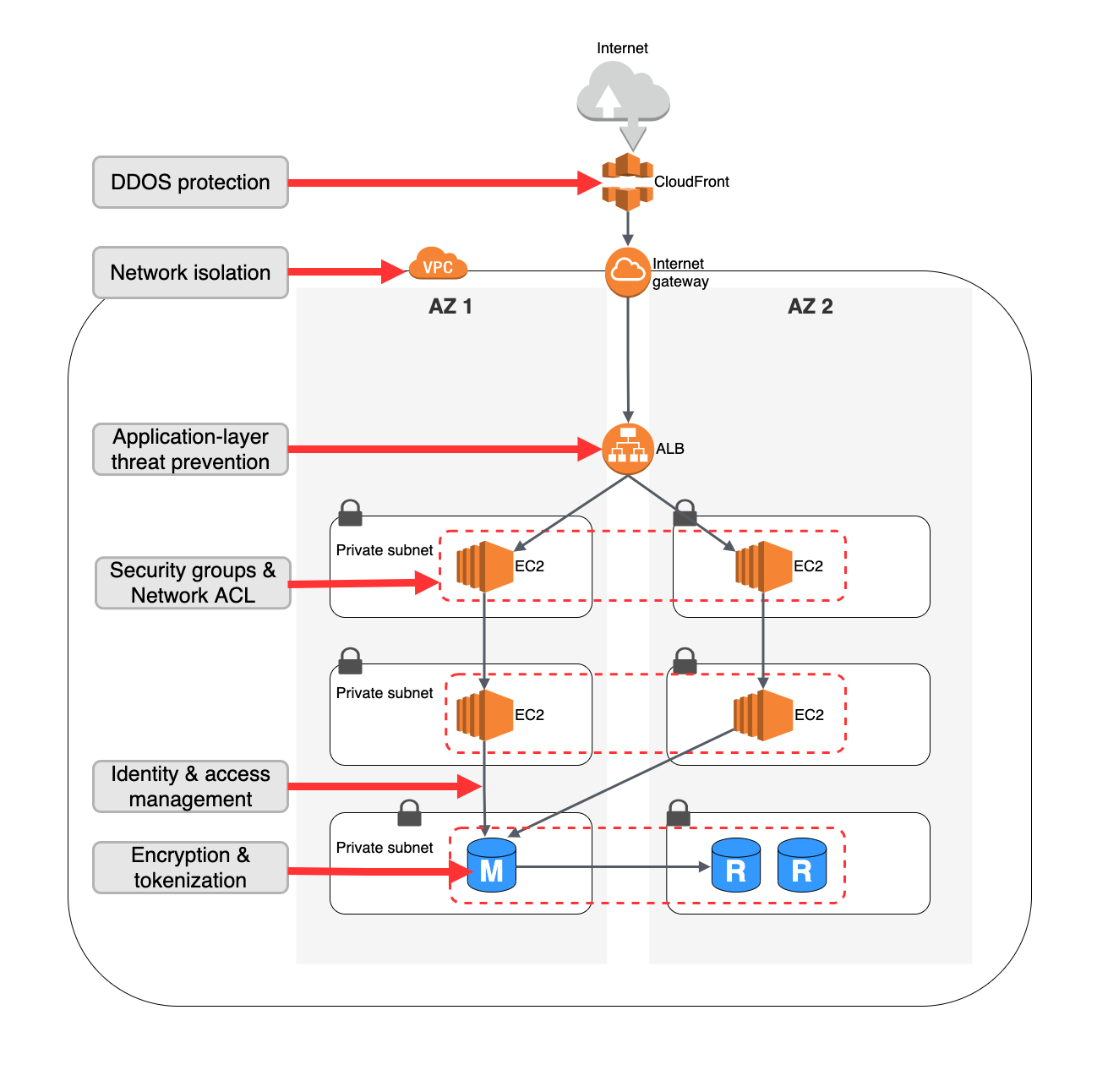
The Security Layer of a SaaS architecture is responsible for protecting sensitive data and ensuring compliance with regulations. This layer includes a range of security measures across various components of the architecture.
Security does not stay just within its isolated area, but it touches all the rest of the layers as well:
- Application layer by following secure coding guidelines to prevent vulnerabilities such as SQL injection. Also, secure session management practices should be implemented, including secure cookie handling or session expiration.
- Data layer by implementing database security best practices such as fine-grained access control, data encryption, and regular security patches. It also maintains detailed audit logs for database transactions.
- Network layer by implementing firewalls and intrusion detection systems (IDS) and virtual private networks (VPN), as well as protecting against distributed denial-of-service (DDoS) attacks.
These are the key parts of the security layer:
1. Authentification
This is where the identity of users attempting to access the application is verified. Only legitimate users can access the system. These are the common techniques how to achieve just that:
- Single Sign-On (SSO) allows users to log in once and access multiple related systems without re-authenticating.
- Multi-factor authentication (MFA) requires additional verification steps, such as a code sent to a mobile device and the username and password.
- OAuth/OpenID Connect is a standard protocol for secure user authentication and authorization across different services.
2. Authorization
Once in the system, authorization determines the permissions and access levels granted to authenticated users. The goal is to prevent users from accessing resources and performing actions for which they do not have authorization. These are the options you can use for that:
- Role-Based Access Control (RBAC) can assign permissions based on predefined user roles, such as admin, user, or guest.
- Attribute-Based Access Control (ABAC) grants access based on user attributes and environment conditions.
3. Encryption
It protects data by converting it into an unreadable format that you can decrypt only by authorized users. The goal is to ensure the confidentiality and integrity of data. You can achieve that by the following methods:
- Encryption at Rest, when data is stored on disks (databases, storage), is encrypted using algorithms such as AES (Advanced Encryption Standard).
- Encryption in Transit is when data transmitted over the network is encrypted using protocols like TLS (Transport Layer Security).
4. Data Protection
You need to know how to safeguard data against breaches, loss, and corruption. It is, therefore, critical for maintaining compliance with data protection regulations (e.g., GDPR, CCPA). Again, here are some techniques how to achieve that:
- Data Masking hides sensitive information within a dataset to protect it from unauthorized access.
- Data Anonymization removes or modifies personal identifiers to prevent the identification of individuals.
Network and Connectivity Layer
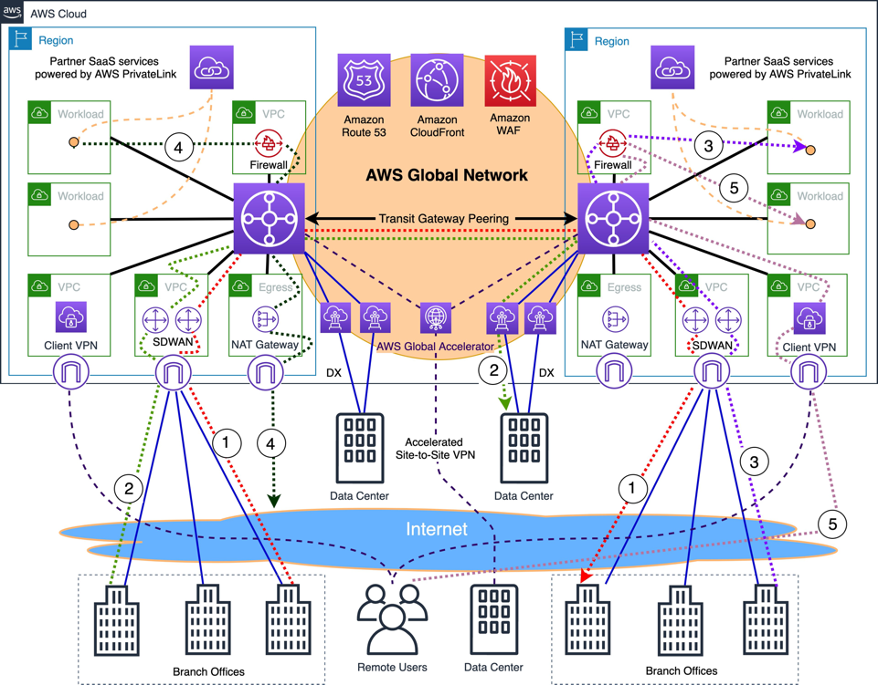
The Network and Connectivity Layer within a SaaS architecture plays a crucial role in ensuring that the application is reliably accessible and fast for users regardless of location. This layer includes network infrastructure, load balancing, and content delivery networks (CDNs), all of which contribute to optimal performance and high availability.
1. Network Infrastructure
This provides the foundational framework for data transmission and communication between clients and the SaaS application.
One part is data centers, which are physical or virtual facilities housing servers and storage and are geographically distributed to ensure redundancy and low latency. Then, networking hardware includes routers, switches, and firewalls to control and manage data traffic. Lastly, virtual networks are software-defined networks (SDNs) that provide flexible and scalable networking solutions through completely virtualized infrastructure.
2. Load Balancing
The main function is to distribute incoming network traffic across multiple servers and ensure that no single server becomes a bottleneck.
You can choose between Hardware Load Balancers (dedicated physical devices), Software Load Balancers (virtualized solution within cloud infrastructure), or Global Load Balancers (multiple data centers or geographic regions).
The main goal is to prevent overloading any server in the infrastructure, balance traffic, and help handle server failures by redirecting traffic to healthy servers.
3. Content Delivery Networks (CDNs)
This component distributes the content across a network of geographically dispersed servers. The main goal is to deliver web content faster to users based on their current location.
To accomplish that, you can use Edge Servers (located at the edge of the network closer to users) or Points of Presence (PoPs), which are strategic locations where CDNs can store cached content.
By caching and serving content from servers closer to the user, CDNs significantly reduce latency.
Multi-Tenancy in SaaS
I have already covered the multi-tenancy aspect of SaaS architecture in high-level detail. But its importance and impact inside SaaS are so high that it’s worth delving much deeper into this topic and really understanding what multi-tenancy can offer.
Take Office 365 as an example. It’s built on a multi-tenant model, allowing users from different organizations to use shared resources and infrastructure while maintaining isolated data and configurations. Salesforce’s CRM system uses a multi-tenant architecture to serve thousands of organizations, each with its own isolated data but benefiting from the same core functionality.
Now, let’s examine why Single-Tenant and Multi-Tenant architectures differ.
Single-Tenant vs. Multi-Tenant Architectures
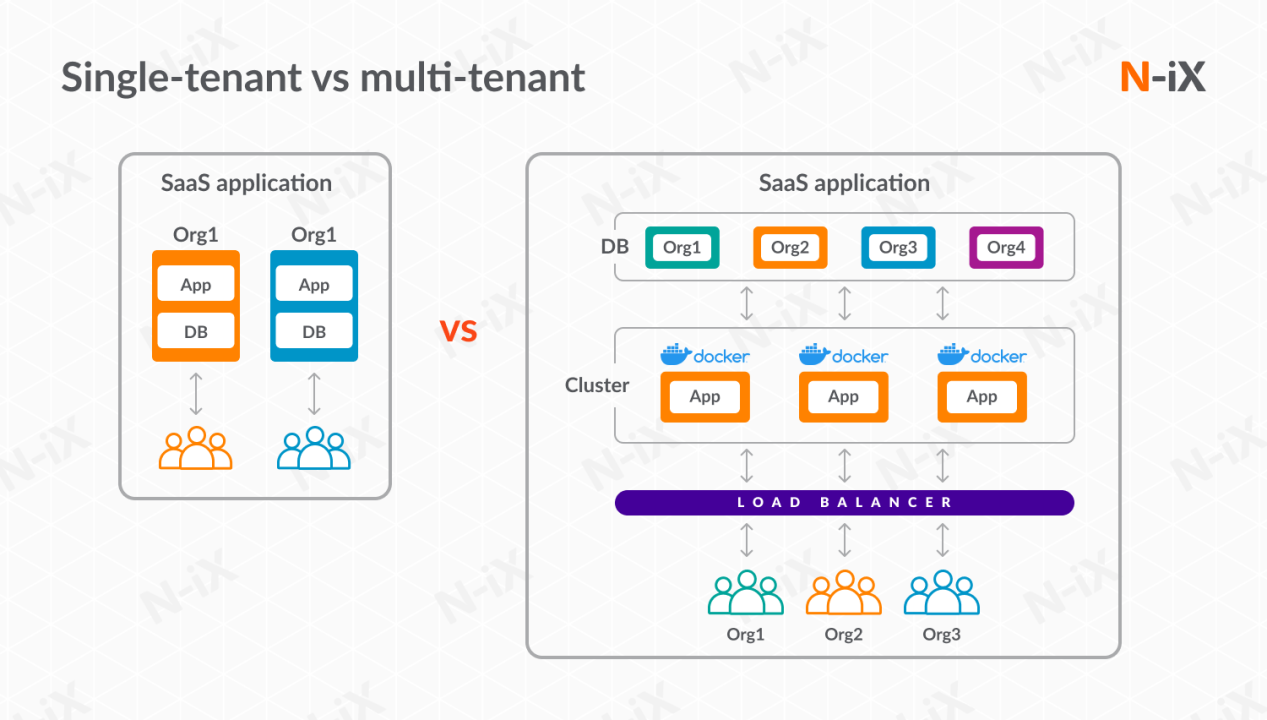
In Single-Tenant architecture, each customer (tenant) has a dedicated instance of the software with strictly isolated infrastructure and databases. That means the tenant gets full control over the platform’s performance or configuration. When scaling needs arise, additional instances are required. This increases the pressure on internal human resources and the time they need to resolve the infrastructure situation. What’s more, each instance has to scale independently.
In Multi-Tenant architecture, multiple customers (tenants) share a single software instance, including infrastructure and databases, with logical data isolation. Multiple tenants share the same resource. Such infrastructure reduces overall costs per tenant. In this case, the architecture can scale more easily by adding resources to a single instance or cluster. It will immediately affect the rest as well, which means the process of global scaling is significantly simpler.
Key Differences
Here are in summary the key differences of Single and Multi-Tenant architecture:
| Feature | Single-Tenant | Multi-Tenant |
|---|---|---|
| Resource Allocation | Dedicated resources for each tenant. | Shared resources across tenants. Requires careful management of the resources. |
| Cost | Higher costs due to separate instances. The more tenants, the less effective the model overall. | Lower costs due to shared infrastructure |
| Scalability | Limited and complex to scale. Scaling involves setting up new instances from scratch. | Highly scalable and efficient. It is easier to scale by adding resources to a shared pool. |
| Maintenance | Each instance requires individual updates | Centralized updates benefit all tenants |
| Customization | High degree of customization per tenant | Limited to shared application customizations. Changes must be managed within a shared environment without affecting other tenants. |
| Security | Physical and logical isolation. It is easier to enforce strict security policies. | Requires robust logical isolation and security measures. |
| Compliance | Easier to comply with specific regulatory requirements per tenant. | Provider needs to ensure compliance across all tenants. |
Advantages of Multi-Tenancy for Providers
By using a single infrastructure, providers significantly reduce hardware, maintenance, and operational costs. The costs of updates and system improvements are shared across all tenants, which, of course, makes it more economical.
Shared resources can be dynamically allocated based on demand, maintaining optimal performance in each situation. Scaling the application by adding resources to the existing infrastructure is much easier than managing multiple isolated instances.
You can apply updates, bug fixes, and enhancements to a single codebase, which reduces complexity and ensures consistency across all tenants. Centralized updates also mean quicker deployment of new features and security patches.
The ability to serve multiple customers from diverse industries simultaneously increases overall market potential. Providers can offer tiered pricing plans based on the level of service, features, or resource usage.
By analyzing usage data from multiple tenants, providers gain insights into the service’s usage. It’s then easier for them to identify trends and make data-driven improvements.
Advantages of Multi-Tenancy for Customers
Customers benefit mainly from the reduced costs of shared infrastructure. This directly leads to lower subscription fees compared to single-tenant solutions. Also, customers do not need to invest in and maintain their infrastructure.
Another advantage is scaling. Customers can scale their usage up or down according to their needs without worrying about underlying infrastructure constraints. The flexibility to start with minimal resources and expand as required is fundamental to this architecture setup, and it is one of the main reasons I chose it in the first place.
You can automatically receive new features and security updates without manual intervention or additional costs. Regular updates ensure that all customers are using the latest version of the software at all times and in all instances in parallel.
SaaS providers typically invest heavily in security measures, including data encryption and regular security audits. That means users can rely on the latest security trends and feel safe about their data. Major SaaS providers also comply with various industry standards and regulations, so customers can be certain they meet their own compliance requirements.
SaaS solutions can be deployed rapidly, allowing businesses to implement new tools and technologies without long waiting times. By relying on the SaaS provider for infrastructure and application management, users can focus on their core business activities and innovation.
Benefits of Multi-Tenancy
Now, let’s enumerate the most important benefits of SaaS architecture.
Resource Optimization
If the infrastructure or application resources are shared among the tenants, operational costs are reduced for both the provider and tenants.
For example, the same physical servers, storage, and network resources are available to all customers. Resources such as CPU, memory, and storage can be dynamically allocated based on real-time demand. When one tenant’s demand decreases, the freed resources can be reallocated to other tenants who need them.
Or take another example concerning the databases. Instead of each tenant having a separate database, a multi-tenant database can serve multiple tenants. This reduces the overhead of managing multiple database instances.
Cost Efficiency
As the infrastructure is the same for all parties, providers have to do each action only once (e.g., updates, patches, and maintenance operations).
Infrastructure, maintenance, and operational costs are shared among multiple tenants, which again reduces the cost per tenant and maximizes the provider’s return on investment.
As a direct consequence, reduced hardware and operational costs lead to lower subscription fees for customers and higher profit margins for providers.
Simplified Maintenance
Centralized updates and a single codebase are key strategies in multi-tenant SaaS architecture that significantly reduce maintenance and support. These approaches offer several advantages regarding service reliability.
For example, all tenants run the same version of the software, ensuring uniformity and reducing the risk of compatibility issues.
Regarding testing activities, with a single application version, the testing process is more straightforward, as updates only need to be verified once before deployment. For example, any updates are deployed simultaneously to all tenants, reducing the time required compared to individually updating multiple instances.
A single codebase also means less complexity. Developers maintain one codebase rather than multiple versions, and fixing a bug in the single codebase immediately positively affects all tenants.
Scalable Operations
Elastic scalability is a critical feature in SaaS architecture, and you can automatically adjust resources to handle varying loads. This is how it ensures optimal performance and availability at any time.
You can choose horizontal scaling, which involves adding or removing instances of application components (e.g., servers, VMs, containers) to handle changes in load. This can even be done automatically through scripts or cloud management tools. You can also apply vertical scaling, which involves increasing or decreasing the capacity of a single instance (e.g., adding more RAM or CPU).
Vertical scaling is usually more limited by the physical constraints of the hardware compared to horizontal scaling.
Security
Robust data isolation and encryption ensure each tenant’s data remains secure, private, and protected from unauthorized access. Data is logically separated and inaccessible to other tenants despite sharing the same physical infrastructure.
Each tenant can use a dedicated database instance or even separate schemas. As an additional step, you can implement row-level security. This basically means that even if tenants share the same tables, they can’t see each other’s data. Data is controlled via the tenant’s identifier stored in each table row.
Encryption transforms data into a secure format that can only be read or decrypted by someone with the appropriate cryptographic key. You can encrypt full disks and databases or go for file-level encryption. This is how you achieve encryption at Rest. Now, you also need to take care of data in transit. That’s achieved by protocols like HTTPS, ensuring secure communication between clients and servers. Alternatively, you can opt for a Virtual Private Network (VPN) that encrypts network traffic between remote users and the SaaS infrastructure.
Challenges in Multi-Tenancy
It’s not only about the positives of multi-tenancy but also some drawbacks to consider. Let’s categorize them based on their primary nature.
Security and Data Isolation
The nature of multi-tenancy increases the risk of data breaches and unauthorized access since multiple tenants share the same infrastructure. Yes, we described before how important the security layer plays in SaaS across all the layers. But that’s also why external attacks concentrate here.
You just have to make sure you have robust logical isolation techniques in place, using partitioning and encryption, to ensure tenant data remains separate. Enforce strict access controls and role-based access controls (RBAC) to limit access to sensitive data. Conduct regular security audits and compliance checks to identify vulnerabilities.
Performance Contention
Performance issues can arise when multiple tenants concurrently demand high resources, leading to resource contention and performance degradation.
So, what can we do to prevent this from happening?
- Implement resource allocation and quotas to ensure fair distribution of resources among tenants.
- Utilize auto-scaling to dynamically adjust resources, considering the actual demand to maintain performance levels.
- Continuously monitor performance metrics and use load balancing to distribute traffic evenly.
Customization Limitation
While multi-tenancy allows some level of customization, it can be restrictive compared to single-tenant setups, where each instance is highly tailored to individual needs.
To prevent that, extensive configuration settings should be offered that allow tenants to personalize their experience without changing the core codebase. Adopt a modular architecture where tenants can add or remove modules based on their requirements without affecting others.
Complexity Management
Managing a multi-tenant environment is complex, especially as the number of tenants grows.
Use centralized management and monitoring tools to oversee the entire multi-tenant environment. Automate routine tasks such as updates, backups, and performance tuning to reduce manual intervention and errors. Finally, segment tenants based on usage patterns and requirements.
Backup and Disaster Recovery
Ensuring effective backup and disaster recovery in a multi-tenant environment is critical but can be more challenging due to the shared infrastructure.
Therefore, you should implement automated, regular backups with versioning and test that the recovery processes are working regularly. Design a redundant infrastructure with failover capabilities to minimize downtime in a disaster. Ensure backups are segmented and encrypted per tenant to facilitate easier recovery.
Compliance Challenges
Multi-tenancy can complicate compliance with industry regulations and standards, even more so when dealing with sensitive information.
A solution to that would be to adhere to compliance frameworks like GDPR, HIPAA, and SOC 2 by embedding compliance requirements into the software development lifecycle. To meet regulatory requirements, use strong encryption for data at rest and in transit. Maintain detailed logs and documentation to support compliance audits and reporting.
SaaS Design Principles
Designing a solid SaaS architecture requires adhering to some fundamental principles, without which the result would not work ideally. I already touched upon them indirectly before; now, let’s summarise them to make them very clear.
Scalability
To allow the SaaS platform to adjust to actual needs (that might again change with every second), the architecture must be capable of different types of scaling:
- Horizontal means the possibility to easily add or remove new server instances or clusters as the load requires.
- Vertical means the possibility of increasing or decreasing computing resources (CPU, disk, memory, etc.) on the same instance.
- Auto-scaling, which means a combination of the two above in addition to that done in a completely automated way. That is, you just schedule the rules based on which the auto-scaling shall jump in, and all the rest will be done by scripts on your behalf.
Reliability and Availability
The architecture must support multiple nodes that are equal to each other but spread the load across different locations in the world, mainly depending on the location of the users accessing the applications. This is how you guarantee high service availability. If one of the nodes goes down, others can substitute until you fix the faulty node.
It also needs to maintain secondary disaster recovery sites in geographically distant locations from the primary site to ensure recovery in case of service or data disasters.
Lastly, automatic failover strategies should be implemented to switch to backup instances or servers when a failure is detected.
Data Security and Privacy
Address compliance with data privacy regulations (e.g., GDPR, CCPA) and industry best practices.
API-First Design
Designing APIs as the foundation of an application, especially in SaaS architecture, offers many benefits, including improved integration, extensibility, and overall system robustness.
APIs enable different applications to communicate regardless of the underlying technology stack. Designing an application around APIs means creating a modular architecture where individual components can be developed and scaled independently. New features or modules can be added as plug-ins through APIs.
Cost Optimization
There are more ways to optimize costs in SaaS.
For one, the aim is to continuously analyze and adjust the types and sizes of instances to match workloads. Either you leverage the auto-scaling techniques or purchase reserved instances for predictable workloads to take advantage of significant cost savings compared to on-demand pricing. In addition, you can utilize spot instances for flexible, non-critical workloads, such as batch processing jobs, to benefit from lower rates.
Another way is to use serverless functions to run code in response to events. You only pay for the compute time consumed, not for idle time. You can also deploy serverless API endpoints using services like AWS API Gateway, Azure API Management, or Google Cloud Endpoints to manage and scale API traffic.
And lastly, cost monitoring tools help track, analyze, and optimize cloud spending through detailed metrics and actionable insights.
SaaS Application Models
Let’s reiterate the basic difference between the three main SaaS models.
In a single-tenant architecture, each customer has a dedicated instance of the application and its associated resources. This model provides high customization and security at the cost of increased management. It suits businesses with strict regulatory requirements, high-security needs, or specific customization demands, such as financial institutions or healthcare organizations. Higher costs are associated with greater control and isolated environments for each tenant.
A multi-tenant architecture allows multiple customers to share a single instance of the application, segregating data logically and sharing the underlying infrastructure. This model is cost-efficient and scales easily. It’s ideal for SaaS providers serving a large number of customers with similar needs, such as CRM systems or e-commerce platforms. However, lower customization and increased complexity in ensuring data isolation and privacy are the trade-offs to take.
Hybrid models combine elements of single-tenant and multi-tenant architectures, so it’s a mix of dedicated and shared resources depending on each tenant’s specific needs. This approach aims to balance cost efficiency with customization requirements. It’s suitable for SaaS providers targeting diverse customer segments with varying levels of customization and security needs, such as enterprise software companies. The trade-off here is an increase in architectural complexity and the potential for higher costs.
Best Practices for Building SaaS Applications
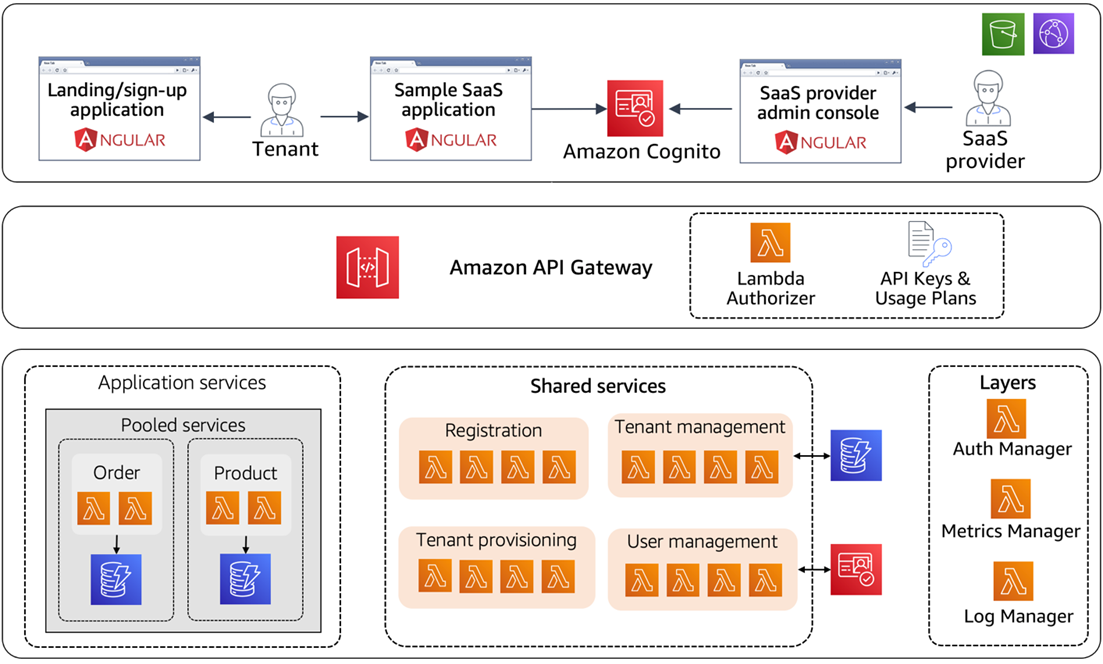
The best practices for building SaaS applications are listed below.
Design for Scalability
Architect the application to handle increased loads by scaling resources horizontally (adding more instances) or vertically (upgrading existing resources). Use auto-scaling features provided by cloud services to dynamically allocate resources based on demand. Employ a microservices architecture to allow independent scaling of different components.
Prioritize Security
Implement strong authentication and authorization mechanisms to protect user data and prevent unauthorized access. Encrypt data at rest and in transit, and regularly update security protocols to address emerging threats. Execute regular security audits and vulnerability assessments to identify and mitigate potential security issues.
Focus on High Availability
Ensure continuous availability of the application by deploying across multiple data centres or cloud regions using load balancing. Implementing failover strategies. Design redundancy into every critical component to prevent single points of failure. Regularly test disaster recovery plans to ensure readiness in case of disruptions.
Enable Multi-Tenancy
Design the architecture to support multiple tenants sharing the same instance while ensuring data isolation and privacy between tenants. Use tenant identifiers to logically segregate data and implement access controls. Provide tenant-specific customization through configuration settings without compromising the shared infrastructure.
Implement Continuous Integration/Continuous Delivery (CI/CD)
Automate the build, test, and deployment processes to ensure reliable delivery of software updates. Use version control systems, automated testing frameworks, and deployment tools to put into practice the CI/CD pipeline. Ensure that every change is automatically tested and deployed to minimise human error.
Optimize for Performance
Continuously monitor and optimize application performance through efficient coding practices, database tuning, and caching mechanisms. Use performance profiling tools to identify bottlenecks and optimize critical paths. Implement content delivery networks (CDNs) to reduce latency and improve load times for global users.
Monitor and Log Everything
Implement comprehensive monitoring and logging to track the health and security of the application. Use centralized logging systems to collect and analyze logs from all components, facilitating troubleshooting and incident response. Set up alerts and dashboards to proactively address potential issues before they impact users.
Design for Customization and Extensibility
Allow customers to customize the application through configurable settings, APIs, and plug-ins without altering the core codebase. Use modular architecture to enable the easy addition of new features or integrations. Encourage third-party developers to extend the application’s functionality through documented APIs and developer tools.
Ensure a Great User Experience (UX)
Focus on creating an intuitive, responsive, and accessible user interface that meets the needs of diverse users. Conduct usability testing and gather user feedback to improve the user experience continuously. Ensure the application is visually appealing, easy to navigate, and performs well across different devices and platforms.
Build for Global Access
Design the application to be accessible and performant for users worldwide by leveraging cloud regions and CDNs. Implement internationalization and localization to support multiple languages and regional preferences. Ensure compliance with local regulations and data protection laws to meet global user standards.
SaaS Architecture Patterns
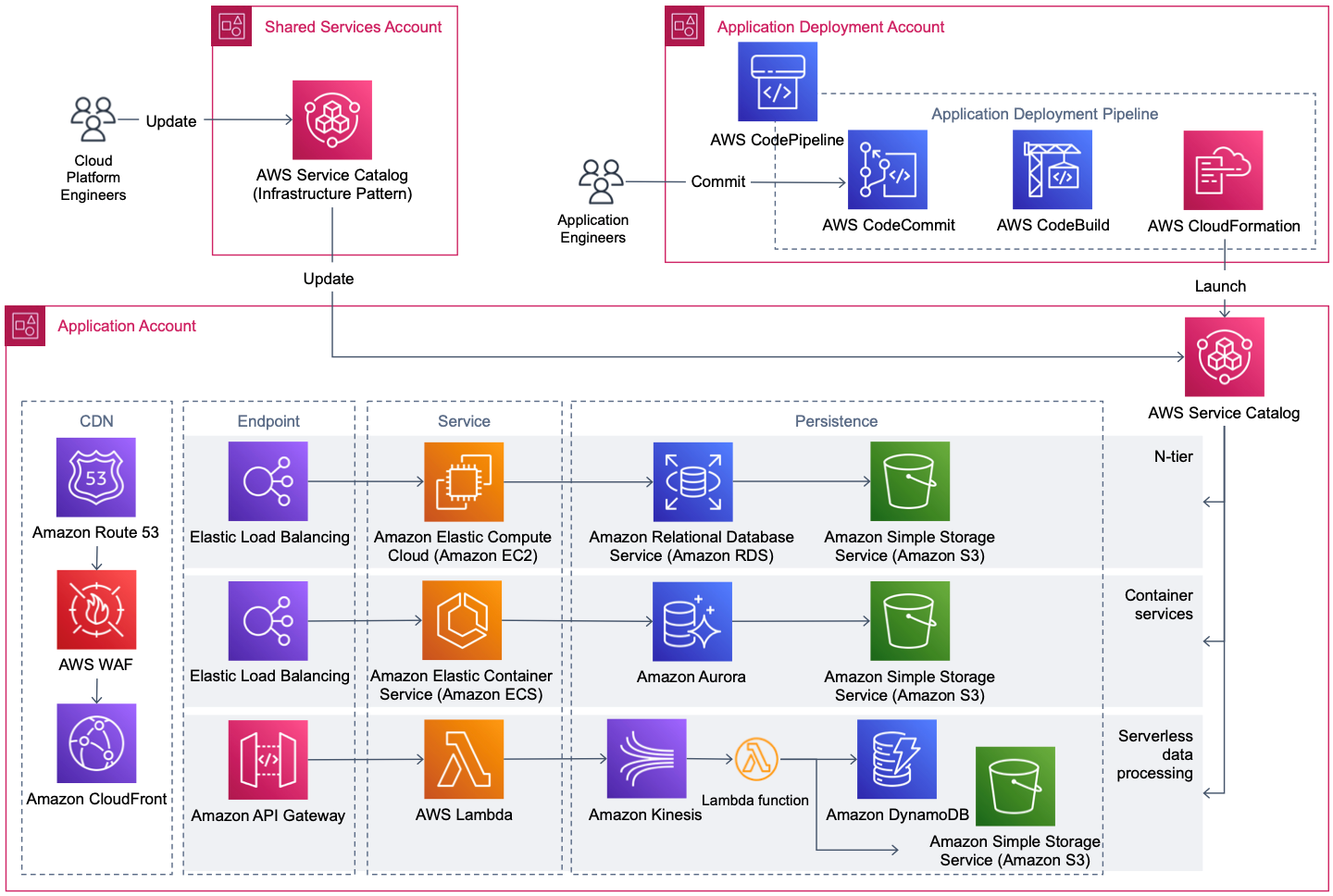
Here is the list of the most known patterns you came across.
Layered Architecture
Layered architecture organizes the application into distinct layers, each with specific responsibilities. Typically, it includes presentation, business logic, data access, and database layers.
This separation of concerns improves maintainability, as each layer can be modified or replaced independently without affecting others. It also improves code reusability, as common functionalities can be centralized in their respective layers.
However, it can lead to performance overhead due to inter-layer communication and sometimes make changes across multiple layers difficult. This pattern is well-suited for enterprise applications with clear functionality.
Event-Driven Architecture
Event-Driven Architecture (EDA) is centered around the production, detection, consumption, and reaction to events. It emphasizes decoupled and asynchronous system interactions.
Components communicate through events, ensuring that changes or actions are propagated across the system without tight dependencies. This architecture enables high scalability and responsiveness, making it ideal for real-time applications like IoT systems or financial trading platforms.
However, robust event processing mechanisms and monitoring are required to ensure event integrity and consistency. It also demands careful handling of eventual consistency and complex debugging scenarios.
Service-Oriented Architecture (SOA)
Service-Oriented Architecture (SOA) defines discrete, interoperable services communicating over a network to perform business processes. Each service encapsulates specific business logic and data, prioritizing modularity and flexibility in developing distributed systems.
SOA facilitates easier integration with legacy systems and third-party services. It enhances overall system agility.
However, managing numerous services and ensuring reliable communication and transactional integrity can be challenging. This often involves standards like SOAP and WSDL, although newer implementations may use RESTful services.
Serverless Architectures
Serverless architectures abstract infrastructure management. It enables developers to focus on writing code that runs in stateless compute containers, triggered by events, and managed by cloud providers.
This model supports Function-as-a-Service (FaaS), like AWS Lambda, which scales automatically with demand and charges based only on actual resource consumption. Serverless architectures provide high flexibility, fast deployment, and cost savings for unpredictable workloads and event-driven applications.
However, they can introduce cold start latency, dependency on vendor-specific services, and state management and integration testing challenges. They are ideal for microservices, event processors, and backend services with variable loads.
How to Choose the Right Cloud Provider for SaaS Applications
Today, there are already far too many SaaS applications from which to choose. So, how can you be sure you pick the right one for your needs? Basically, you have roughly only three options/categories to choose from.
AWS, Azure, and GCP Comparison
AWS, Azure, and GCP are the leading cloud providers offering comprehensive services tailored for SaaS applications.
AWS excels in extensive service offerings, robust security, and a mature ecosystem. It’s ideal for diverse workloads, and it’s hard to find a weak point.
Azure integrates perfectly with Microsoft products. It gives you strong support for enterprise environments and hybrid cloud solutions.
GCP is known for its advanced data analytics and machine learning capabilities. It’s especially suitable for data-intensive applications, and it offers competitive pricing and innovative infrastructure solutions.
SaaS Factory by AWS
The AWS SaaS Factory program provides resources, best practices, and technical guidance to help companies migrate to or build SaaS solutions on AWS. This program offers workshops and collaborative sessions with AWS experts to optimize the development and operational processes.
It enables fast adoption of SaaS models by addressing architectural, operational, and business considerations specific to SaaS. AWS SaaS Factory aims to accelerate time-to-market and enhance the scalability and security of SaaS applications.
Managed Services and Monitoring
Cloud providers like AWS, Azure, and GCP offer managed services that simplify infrastructure management. This enables focus on application development rather than maintenance.
Managed services include databases, networking, security, and serverless computing, which automate many operational tasks. Additionally, built-in monitoring tools such as AWS CloudWatch, Azure Monitor, and Google Cloud Operations provide visibility into application performance and resource utilization.
Security and Compliance in SaaS

There are some key data privacy regulations you will need to implement often as part of SaaS compliance and security.
The General Data Protection Regulation (GDPR) is a comprehensive data protection law in the EU that prioritizes user privacy and data protection requirements. It provides strict guidelines for processing personal data, including obtaining explicit consent and data subject rights (e.g., access, correction, and deletion).
Health Insurance Portability and Accountability Act (HIPAA) is a US regulation that sets standards for protecting sensitive patient health information (PHI). It requires safeguards to ensure the confidentiality and availability of electronic PHI. It’s imperative to use encryption for data at rest and in transit, conduct regular risk assessments, implement access controls, train employees on security practices, and ensure compliance through regular audits.
Service Organization Control 2 (SOC 2) is an auditing framework for service providers to manage customer data based on five trust service principles: security, availability, processing integrity, confidentiality, and privacy. To maintain certification, consider developing comprehensive security policies, continuous monitoring, robust incident response mechanisms, and regular SOC 2 audits.
Best Practices for SaaS Security
To guarantee encryption requirements, encrypt sensitive data both at rest and in transit to prevent unauthorized access. Use SSL/TLS for data in transit and strong encryption algorithms (e.g., AES-256) for data at rest. Regularly update and rotate encryption keys and perform encryption audits.
To satisfy monitoring needs, implement continuous monitoring to detect and respond to security incidents in real time. Use centralized logging and monitoring tools to track application performance, access logs, and security events. Set up alerts for suspicious activities. Integrate with Security Information and Event Management (SIEM) systems for advanced threat detection and perform regular log reviews.
To handle vulnerabilities, regularly scan for vulnerabilities in your SaaS application and infrastructure to identify security weaknesses. Automated tools are used to perform static and dynamic analyses. Schedule periodic vulnerability scans and conduct penetration testing.
Secure and Scalable Identity and Access Management (IAM)
The most common solutions for implementing robust IAM services for your platform are AWS IAM, Okta, and Auth0.
AWS IAM allows you to securely manage access to AWS services and resources for users and applications. It supports fine-grained access control through policies, roles, and multi-factor authentication (MFA). To make it effective, stick to the definition of least privilege access policies, use IAM roles to delegate access without sharing credentials, and enable MFA for an additional layer of security.
Okta provides cloud-based IAM solutions, including Single Sign-On (SSO) and Multi-Factor Authentication (MFA), to securely manage user identities and access applications. What needs special care here is implementing SSO to reduce password fatigue, utilizing adaptive MFA to balance security and usability, and enforcing policies to handle secure access across multiple applications.
Auth0 is an identity management service that offers authentication, authorization, and user management. It supports various protocols and integrates with multiple platforms. Use Auth0’s extensible capabilities to customize authentication flows. Also, role-based access control (RBAC) should be implemented to manage user permissions and leverage social logins to simplify user onboarding without affecting overall security.
SaaS Architecture Examples
Here are some popular examples of successful SaaS architecture implementation execution.
Microsoft Office 365
Office 365 uses a multi-tenant architecture. It leverages Azure cloud services for scalability and reliability. It integrates tightly with Azure Active Directory for identity and access management. The architecture includes components for Exchange Online, SharePoint Online, and Teams.
Adobe Creative Cloud
Adobe Creative Cloud provides a suite of design tools through a multi-tenant model, with services running on Adobe’s cloud infrastructure. It offers a centralized application manager for installing and updating software and cloud storage for project files. The architecture integrates APIs to extend functionality and supports collaboration features, enabling multiple users to work on projects simultaneously.
Slack
Slack employs a multi-tenant architecture to support its messaging and collaboration platform, with AWS as the primary cloud provider. The architecture includes channels, direct messaging, and integrating numerous third-party services through APIs. It maintains high availability and real-time communication through scalable infrastructure and data isolation mechanisms.
Salesforce
Salesforce’s multi-tenant architecture supports various CRM functionalities that run on the Salesforce Platform. The architecture includes Sales Cloud, Service Cloud, and Marketing Cloud components. It enables custom application development and deployment within the same infrastructure, ensuring extensibility and scalability.
QuickBooks Cloud
QuickBooks Cloud uses a multi-tenant architecture hosted on AWS to deliver accounting and financial management services. The architecture integrates with various banking and financial services through APIs. It provides real-time data synchronization and reporting and utilizes AI for features like automatic transaction categorization.
Dropbox
Dropbox operates on a multi-tenant architecture with cloud storage and synchronization services built on its Magic Pocket infrastructure and partnerships with cloud providers like AWS. The architecture includes components for file storage, sharing, and collaboration, with real-time synchronization and advanced sharing permissions. Dropbox Paper extends the platform with integrated document editing and teamwork features.
Google Workspace
Google Workspace, utilizing Google’s multi-tenant architecture on Google Cloud Platform (GCP), includes applications like Gmail, Google Drive, Google Docs, and Google Meet. The architecture supports centralized identity management through Google Accounts. High availability and real-time collaboration are ensured through distributed data centers and worldwide networking infrastructure.
Future Trends in SaaS Architecture
Looking into the future of SaaS and its trends, the main areas of interest are AI, edge computing, and green cloud infrastructure.
Integrating artificial intelligence (AI) into SaaS applications will enhance functionality with features like predictive analytics, personalized user experiences, and automation. AI transforms SaaS applications by enabling smarter decision-making and delivering more tailored user experiences.
This can be seen already in Salesforce Einstein, which incorporates AI to extract insights, make predictive recommendations, and automate workflows. Another example is Adobe Sensei, which Uses AI to enhance creative tools with features like content-aware fill and automated tagging.
Edge computing means processing data closer to where it is generated to reduce latency and bandwidth usage. As a side effect, it greatly enhances real-time processing capabilities. Lower Latency improves performance for applications requiring immediate data processing, such as IoT devices and real-time analytics. Edge computing is particularly beneficial for heavy data applications like video streaming.
Sustainable cloud infrastructure helps lower carbon footprints and promotes eco-friendly practices. Increasing focus on sustainability drives cloud providers to adopt green practices to reduce their environmental impact. Major cloud providers like AWS, Azure, and Google Cloud are investing in renewable energy projects to power their data centers. Those efforts also lead to the implementation of advanced cooling technologies and optimizing resource allocation to reduce energy consumption.
-
 EditorRashmi Sharma is an editor at Geekflare. She is passionate about researching business resources and has an interest in data analysis.
EditorRashmi Sharma is an editor at Geekflare. She is passionate about researching business resources and has an interest in data analysis.


