The web is either surfaced or deep (and dark).
It would be an understatement to say that most of the internet operates behind the scenes.
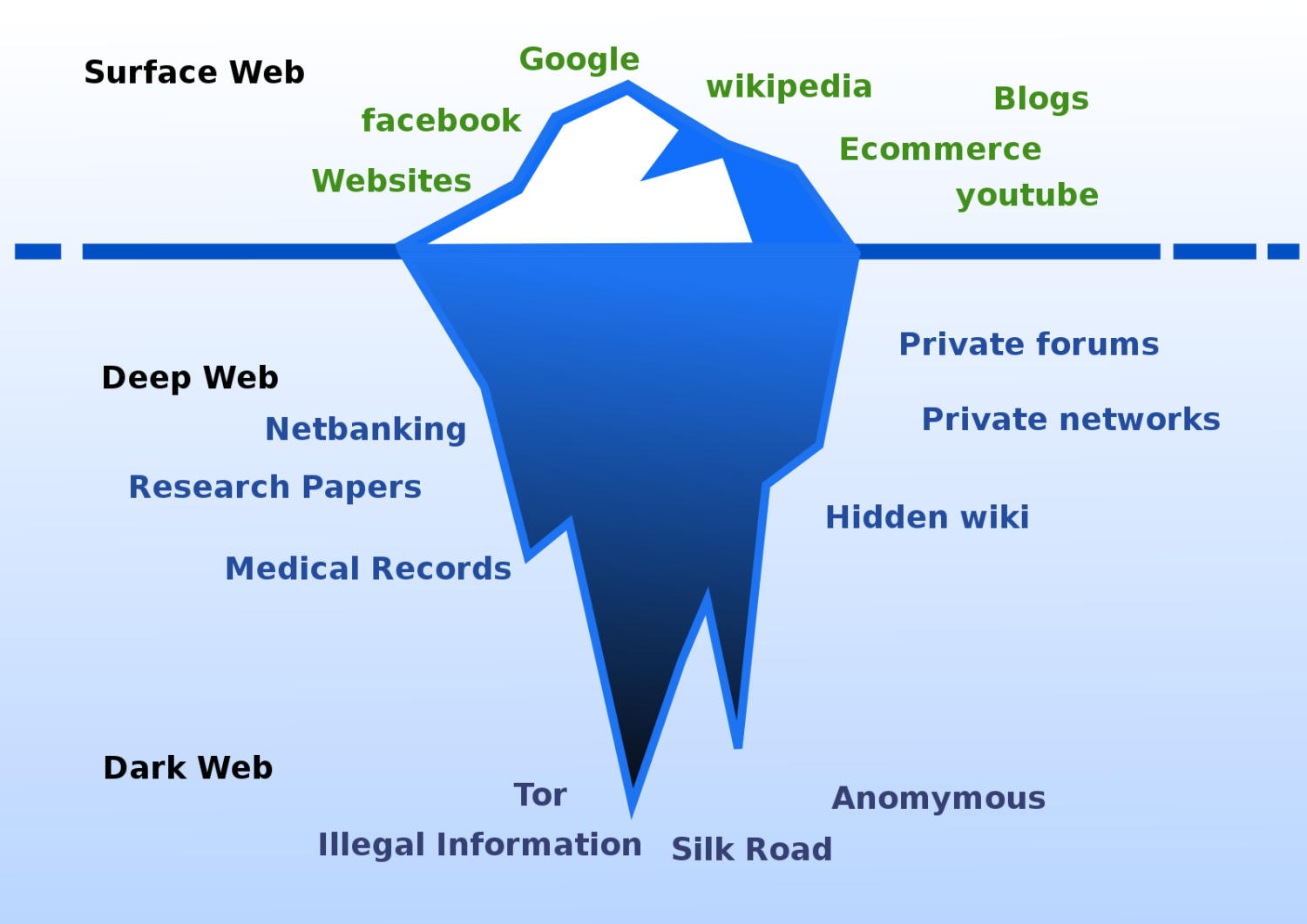
What we actually see, the surface, open, or visible web, just constitutes 5 to 10% of the total internet.
The rest is known as the deep or hidden web. And the dark web (aka darknet) is still a smaller section, up to 5% of the entire internet.
To understand this better, let’s back up a little bit.
Internet and Search Engines
I hardly enter any URLs in the web browsers. Instead, what I (and most of us) rely on is search engines.
Just type a few characters, and it auto-suggests where we can pick the desired result to hit enter. It’s easy and works every time.
This internet search works because of crawling. Google, Bing, Yahoo, and all major search engines have bots that update their internet registries regularly whenever anything gets published on the internet. They index new entries and then show them for the relevant search queries made by the end users (us).
However, a few things aren’t made for the general public. Some of these password-protected pages (deep web) are marked with a “no-index” tag which prevents search bots from crawling them. Others (dark web) use specific protocols that the normal browsers (Chrome, Edge, Firefox) can’t connect with.
Further sections speak about all this in detail.
What is the Deep Web?
The deep web is simply the non-indexed part of the internet. Most of that is legal, like your financial information in banks, social media accounts, email archives, cloud storage, academic journals, streaming libraries, etc.
A simple example of the deep web would be your email account. Another is Netflix, which is only accessible to its subscribers.
In a nutshell, the deep web remains “open” to its respective owners and stays “closed” to others. And if someone tries to access the deep web without proper authorization, it would be termed as hacking, which is again illegal.
Lastly, it isn’t dangerous, and we interact with our respective shares of the deep web on a daily basis without acknowledging it.
But that can’t be said for the section of the internet we are about to discuss.
What is Dark Web?
Like its name, it’s dark (within deep), meaning it’s hard to find.
Dark web hosts project which ends with .onion (aka onion sites) and not .com, .net, .org, etc. that we generally operate with. And since normal browsers can’t browse such websites, you need something like the Tor browser to surf the dark web.
Tor browser is a tool used to browse the web privately. It’s run by global volunteers who become relay operators by donating their bandwidth and IP address for whatever Tor users do.
So what makes the dark web risky and a place we should generally avoid?
A major chunk of the dark web is home to illegal activities or things, such as banned drugs, weapons, stolen identities, for-sale malware, looking-for-work cybercriminals, and whatnot.
In addition, just surfing the dark web can unleash malware on your computer. Besides, governments might actively monitor such activity, and anyone showing a keen interest in the dark web can become a law enforcement target.
Did you hear about the silk road, an online black market infamous for unlawful activities that was shut down in 2013 by the FBI? It was part of the dark web.
Still, some of the dark web is very “standard,” like this Facebook (onion) site:
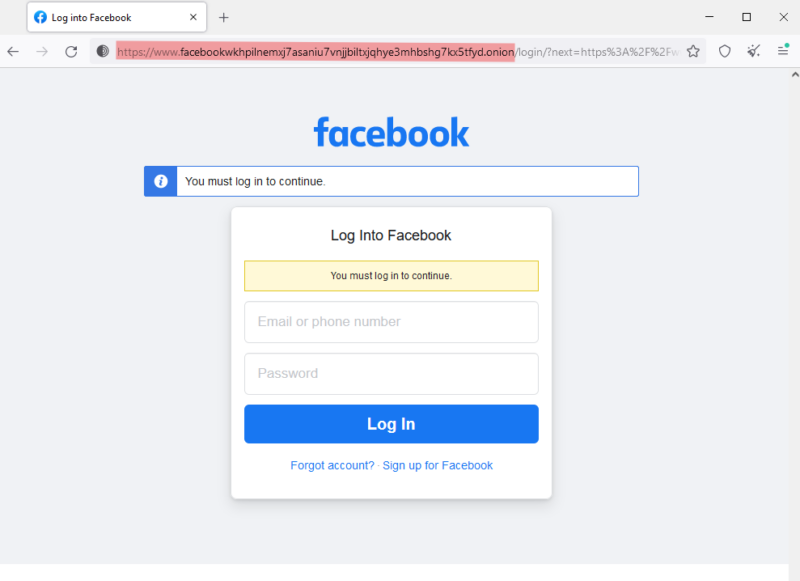
Meta (Facebook’s parent) made this onion website for its users on Tor browsers because it showed errors for its normal website (facebook.com). Therefore, it’s a perfectly safe place on the dark web, like many other onion sites you can easily google.
Some onion sites for your reference:
Facebook: https://www.facebookwkhpilnemxj7asaniu7vnjjbiltxjqhye3mhbshg7kx5tfyd.onion
NY Times: https://www.nytimesn7cgmftshazwhfgzm37qxb44r64ytbb2dj3x62d2lljsciiyd.onion
CIA: http://ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion/
** Please note you need the Tor browser to visit these websites.
Dark Web vs. Deep Web
While the dark web is a part of the deep web, there are stark differences between those two. Let’s summarize both of these for a clear understanding.
| Deep web | Dark web |
| 90-95% of the internet. | 1-5% of the internet. Part of the deep web. |
| Personal or commercial information | Public websites and mostly illegal e-stores |
| Accessible with necessary authentication | A part is open for public access |
| Little to no malware risk | Frequent malware infections |
| Not indexed by search engines | Not indexed by search engines |
| It can be used with Chrome, Edge, Firefox, etc. | The best way to use it is via the Tor browser |
| Ex. Gmail, Dropbox, etc. | Ex. Facebook onion portal, etc. |
Even though the dark web is not for the average user, it has some good use cases. This bright side of the dark web chiefly includes whistleblowing and sensitive journalism.
People use it to share information when their local governments act hostile or snoop extensively. For instance, Edward Snowden used the dark web to reveal that NSA surveils all US citizens, even if someone has no criminal history.
What followed is already covered by various media outlets, and repeating that will just be redundant. But case in point: it’s good to know to use the dark web in those dire times of need.
How to Safely Access the Dark Web?
Let’s start this section with a disclaimer: there is nothing like 100% safety on the internet. No tool or cybersecurity expert can guarantee that without lying. So, despite whatever I tell you in this “safe ride to Dark web guide”, things can be traced back to you in rare cases, and this can haunt your future.
If you’re still up for looking at the dark side of the internet for reasons best known to you, here are a “few” things to take note of.
#1. Anonymity
While Tor is a good starting point, the best options are dedicated, secure operating systems like Tails, Subgraph, Kodachi, whonix, etc.
These operating systems send every outgoing request, not just the web browsing ones, through the Tor protocol, ensuring robust protection. Besides, some additional protective measures may include application sandboxing, erase-on-shutdown, etc., based on a particular OS.
#2. Extra Protection
Consider using a VPN before connecting to the Tor network. There are many, but my personal favorite is ProtonVPN (free version available).
It’s important to note that Tor runs fine on its own, and by using a VPN additionally, we are just adding another layer of security and hiding the very fact that you’re using Tor. It’s a rare protocol, and people don’t use it normally. So you become a subject of interest by just using it, even if you browse the open web with it.
#3. Separate Identity
At this point, you have everything for a quick joyride to the dark web. But you need more than this if you want to take part.
A discrete online identity, which has nothing to do with your present one. Separate email, phone number, anonymous payment channel,…..the list can be long based on what you aspire to get involved with on the dark web.
There are instructions available for these on the web, and covering everything here will send us way off the scope of this article. But you get the drift. Don’t use anything that can be linked back to your original identity.
Ideally, you should have a separate anonymous identity for each substantial outing on the dark web. But a single set is generally enough if it’s just about one or a few “informational” visits.
One of the best ways to maintain privacy in your communications is by using encrypted email services. Proton Mail, the best secure email service, offers end-to-end encryption, ensuring that your emails remain private and inaccessible to third parties. Unlike mainstream email providers, Proton Mail does not log IP addresses or track users, making it an excellent choice for anonymity.
Is it Illegal to Access the Dark Web?
As a law enforcement officer, would you suspect someone always (or mostly) present at the crime scene?
The same goes for accessing the dark web. It’s mostly illegal, and some governments have their officials watching the dark web very closely for obvious reasons.
Therefore, although it’s not illegal to just access the dark web, it makes you one of a kind. And in the absence of an effective disguise, you can be summoned by your local authorities.
For instance, Harvard University received a bomb threat via a disposable email in December 2013. They immediately informed the FBI, which singled out all the campus students using Tor in that time frame. Finally, one of them, Eldo Kim, confessed to using Tor and Guerrilla Mail to send bomb threats to the university authorities to postpone the exams.
Consequently, using Tor (to visit the dark web) is something an average internet user does not do. And if you’re on that path, you better have reasonable explanations if it comes to that rare encounter with law enforcement.
Dark Web Monitoring
The dark web is home to stolen identities, credit cards, national IDs, passports, etc. And since we can’t access every dark web onion site to see if our own credentials are up for sale, we have some monitoring tools embedded within NordVPN and 1Password.
NordVPN is a high-performing VPN we frequently recommend to our readers, and
Still, dark web monitoring is a common extension nowadays, available with many VPNs, password managers, and antivirus software. So you can also subscribe to the tools of your choice if these two don’t cut it for you. Just ensure to check the features list carefully before opting for anyone.
It’s Not a Wrap-up for You!
The dark web is indeed dangerous. Cybercriminals, law enforcement, etc., all of these and more might closely observe who chooses to enter that dubious digital realm. In addition, there is always a malware risk in that uncharted territory.
On the other hand, the deep web is that hidden part of the internet, which is personal and open to its respective owners.
Finally, I made the distinction clear enough between the deep and the dark web and flagged the dangers of roaming in the latter.
PS: A few dark web investigation tools to look out for.

