IP bans are common, and here are a few methods to get out of them.
No matter if you have done anything suspicious or not, you can or might have already faced IP bans.
In fact, an IP ban is a handy feature offered in many digital security products. For instance, you can use Cloudflare to IP ban entire countries, and webmasters often do this.
But if all of this sounds strange, you should first know what an IP address is. These are akin to real-world addresses. However, IP addresses are meant for the digital landscape, aka the internet.
Every internet-connected device has an IP address they use to ‘talk’ to other devices.
So, when your computer tries to connect to my website, which has a list of banned IPs, including yours, you see a warning similar to “Your IP has been banned” or “Access Denied”, etc.

Alternatively, you can also see such warnings if your ISP has banned a specific resource you’re trying to visit.
Why is my IP banned?
There are a few reasons besides a webmaster innocuously banning IPs or your ISP acting as per local governmental guidelines (or pressure).
Abuse
Every web property we use has specific terms most of us never care to give a look at. In most cases, this is normal user behavior and doesn’t come under any scanner.
However, it becomes a problem when a user tries exploitation or practices malicious intent.

For instance, a user is typically slapped with an IP ban if they try to gain unauthorized access to the admin console of any website.
Moreover, you might be creating more user accounts with the same IP address than allowed in the website’s fair use policy.
These were just a few examples, and there can be countless more where you might have deviated from normal user behavior, resulting in such bans.
Hacks & Shared IP
In some cases, a bad actor may use your IP address for illicit activities. This can be a result of a hack, and you might have active malware doing all the dirty work on your device.
Here, your computer might be sending spam or anything else based on the hosted malware. These activities highlight your IP address on the other end, resulting in an IP ban.
Besides, most users have shared IP addresses allotted by ISPs, and we can also get banned because of the actions of someone else.
Target Audience & Safety
An online pizza shop serving New York City has no reason to allow people from Pakistan or elsewhere. Every internet user eats up some resources, and if there is no ROI for the website owner, it isn’t financially lucrative to let such an audience in.
In addition, a few countries are known for cyberattacks on websites based in their rival countries.
Consequently, this helps webmasters optimize resource consumption and safeguard their projects from attacks.
Now that we know a few reasons behind IP bans, let’s talk remedies.
Ways to Overcome IP Bans
While IP bans are easy to implement, they aren’t foolproof. There are 8 ways around them, as discussed below.
- 1. Proxies
- 2. VPN
- 3. Tor
- 4. DNS Flush
- 5. Cloud computer
- 6. Anti-detect browser
- 7. Contact Admin
- 8. Removal from Blacklists
- Show less
Proxies
A web proxy helps in spoofing your IP address. They are generally a few clicks process to broadcast a different identity to the rest of the internet.
A proxy server routes the traffic through itself and acts as a mediator between you and others. Consequently, your web activity is known with the proxy server’s IP and not with your actual IP address and location.
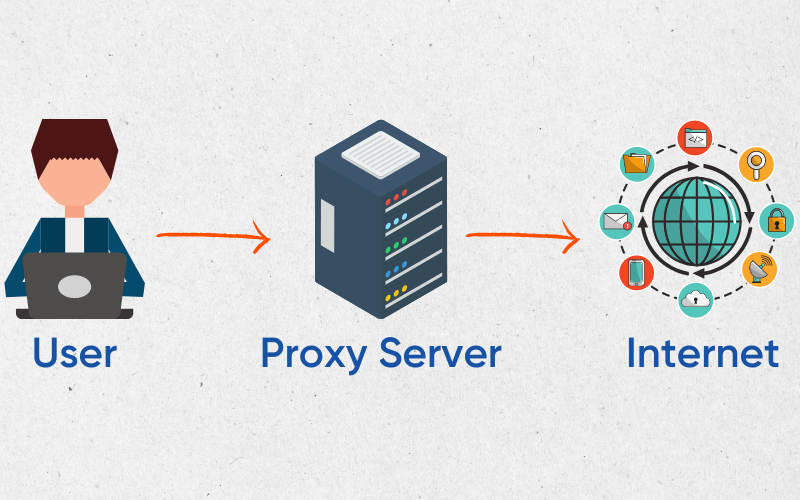
The easiest way of using a proxy is through a browser extension. There are free proxies, known as public proxies, which are generally free to use with data limits. However, most free proxies are a privacy hazard, and we strongly recommend against using them.
One of the proxy services we recommend is LimeProxies. They have multiple servers located across Europe, the Americas, and Asia. Besides, you can take their free three-day trial to see if they fit your bill.
VPN
You can consider VPNs as private versions of proxies. However, a VPN not only spoofs your geolocation but also encrypts the data transfer. Another major difference is that a proxy covers just an application (like a browser); however, a VPN takes care of an entire device.
Meaning a VPN covers browsers, installed applications, and every outgoing request.
In addition, most VPNs are armed with user-friendly features such as split tunneling, where you can allow specific applications out of the encryption tunnel.
There are many more advanced aspects that make VPNs the darling of security researchers. Still, you may face speed throttling, thanks to the encryption, which gets more pronounced with subpar VPNs.
However, that’s not the case with something like NordVPN.
To use a VPN, one downloads its application and connects to a preferred VPN server with just a toggle. Alternatively, there are more geeky ways to use a VPN with the provided configuration files; however, it depends on the operating system.
Related: Proxy vs VPN: What Are the Differences?
Tor
Tor is a free and open-source way to anonymity. This is a community-supported project run by volunteers, who act as relays around the world. Every request you make is passed from three relays before landing on its intended destination.
This is done via a special browser known as the Tor browser. This is presently available for Windows, MacOS, Linux, and Android. The only downside can be speed and a few websites blocking Tor traffic altogether.
Notably, Tor is very similar to using a proxy, and using this browser doesn’t protect the operating system. Instead, anonymity is limited to the Tor browser itself.
DNS Flush
Domain Name System, also known as the phone book of the internet, helps match domain names (geekflare.com) to machine-readable IP addresses (145.42.79.57).
For this process, our machines contact the DNS server, which helps the website load in the browser. However, this happens only the first time, and a device keeps periodically renewed local copies of DNS records to reduce latency.
But a change at the source could lead to this access denied warnings, resulting from stale DNS entries. And for that, we have to manually flush the DNS.
Cloud computer
Straightaway, this is a pricey solution to this simple issue. Regardless, you can subscribe to cloud computing, which offers a whole different machine to use remotely.
Put simply, a cloud PC is a computer with all the standard resources (CPU, RAM, hard drive, etc.). And you only need an internet connection and a secondary device (PC, smartphone, tablet, etc.) to use that computer located elsewhere.
At Shells, this starts at just $5 per month. Typically, this is an advanced product with the primary intention of reducing infrastructure costs for startups.
However, no one is stopping you from using them personally.
Anti-detect browser
GoLogin
GoLogin is a premium solution that isn’t directly related to IP bans but online anonymity in general.
Specifically, GoLogin is about managing multiple profiles from a single web browser. These profiles are saved in the cloud, and you can play with different parameters to get anonymous browser fingerprints for robust web privacy.
Regarding IP bans, one has to integrate proxies into GoLogin. You can use public proxies or buy premium ones directly from their dashboard.
So while you can bank on GoLogin to fight bans, this browser is primarily aimed at 360-degree private browsing. It does so by randomizing browser fingerprints which are predominantly used for targeted advertising.
Nstbrowser
Nstbrowser is another anti-detect browser, which is totally free, helping fight IP bans with its native automatic proxy rotation.
Not just this, you can bank on this privacy tool to manage multiple profiles with unique browser fingerprints to bypass website blocking. You can use effective and free RPAs to deal with data scraping and multi-account management without detection.
Nstbrowser is compatible with Windows/Mac/Linux, and it allows sharing those profiles with other devices, without leaking user data.
You may start with its free subscription for managing unlimited profiles, with a 1000 cap on profile launch limit!
Also read: Anti Detect/Multilogin Browsers to Try
Contact Admin
If nothing has worked for you till now and you’re sure about not abusing the service, contact the website admin.
It might be complicated since you can’t visit the website in the first place. So I suggest searching any social media handles of the website for any profiles that might link to someone in command.
Here, you can explain your issue, and they might consider letting you in.
Removal from Blacklists
These are the databases of IP addresses banned for unwarranted behavior. And as already stated, the reason can be a hack or someone sharing the same IP with you.
You can check by finding your IP address from whatismyipaddress and entering that into any blacklist checker.
Besides, you will also see the name of the blacklist, like this:
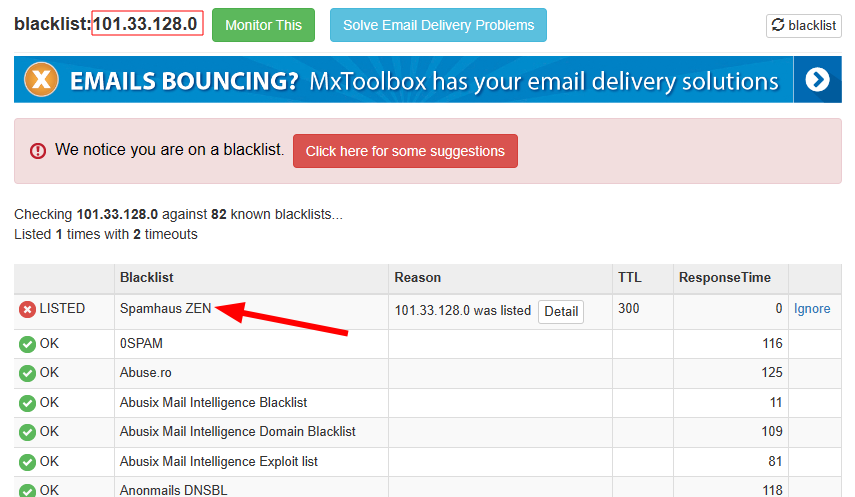
I have tried this with a random Chinese IP address, and it was listed on Spamhaus ZEN. Now if the owner of this IP address wants this cleared, they have to google the blacklist to find the associated website. Next, one should search for a procedure for removal.

Alternatively, one can contact them if the removal process isn’t there to proceed further.
However, this is a very tedious solution that doesn’t always work. The easiest way is just to get a new IP from your ISP if you’re using a dedicated one.
For a shared IP, most ISPs rotate this periodically. Additionally, switch off your WiFi router overnight, and most probably, you’ll have a different one the next morning. This is because most ISPs use the DHCP protocol for assigning an IP address. So, if you’ll just go offline and come again, chances are you’ll get a different IP address.
Still, the time period for IP renewal may differ. For instance, some Comcast users reported having the same IP address for years, surviving blackouts, and whatnot. So, if waiting it out isn’t working, try the other solutions listed above.
Get your IP unbanned!
IP bans aren’t scary in normal circumstances. You can simply wait them out, subscribe to a VPN/proxy, or get a cloud computer. Besides, contacting the website administrator or getting yourself removed from a blacklist is always an option.
Still, it can also happen with malware on your computer, which is actively attacking others. In that case, using a good antivirus will resolve it.

