NMAP (Network Mapper), is one of the famous open-source tools to perform network scans, security auditing, and find vulnerabilities in network infrastructure.
One of the popular know usages of NMAP is to find the open ports in the network. NMAP can be installed on Windows, Linux, macOS, and much more.
In this quick guide, I will explain how to get NMAP installed on Windows OS & some usage examples.
Installing NMAP
- Go to Nmap download link and download the latest stable version
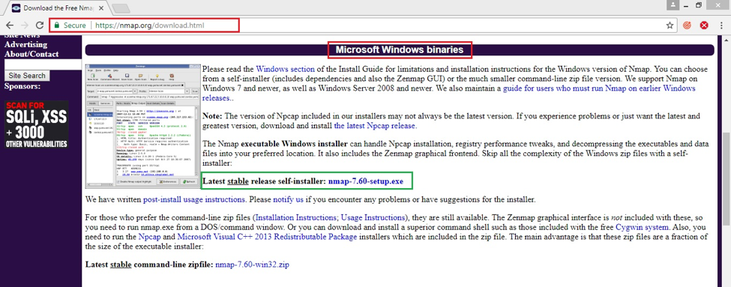
or, use the direct link here to download
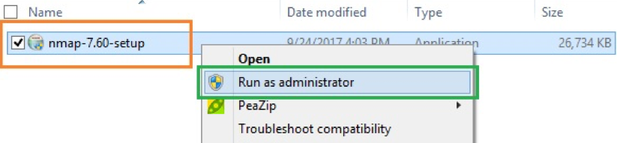
- Go to the location where the file is downloaded
- Right-click on the EXE file and click “Run as administrator.”
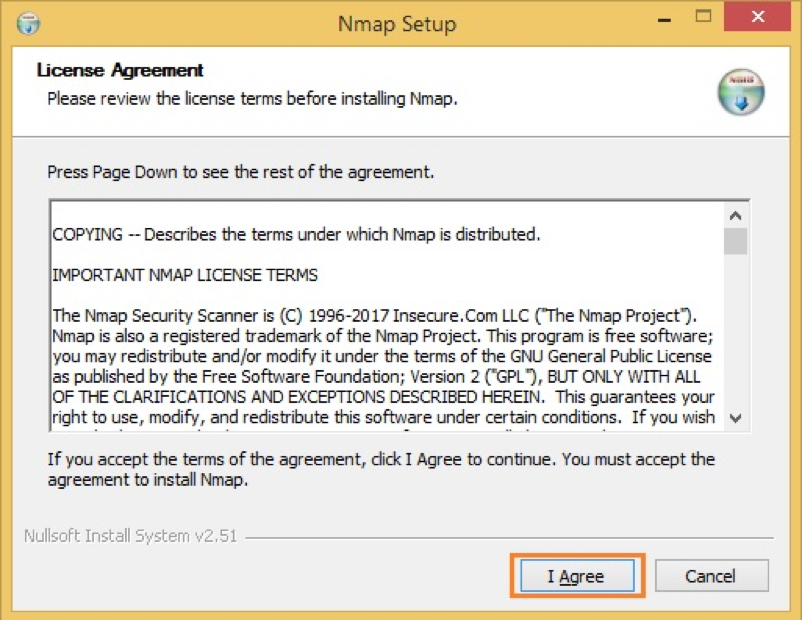
- It will start the installation process, accept the license agreement
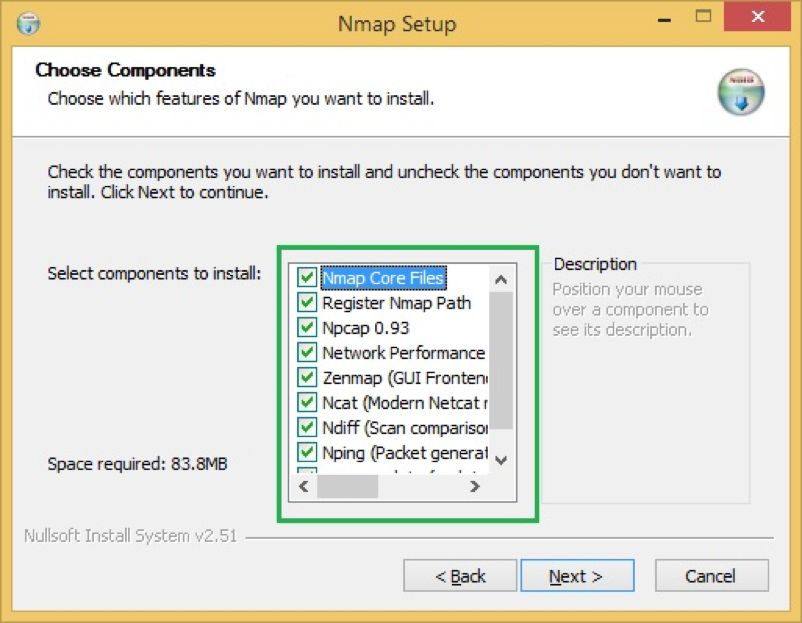
- You can choose what components to install, but it would be good to install all of them
- By default, it will install under
C:Program Files (x86)Nmapbut feel free to change if needed
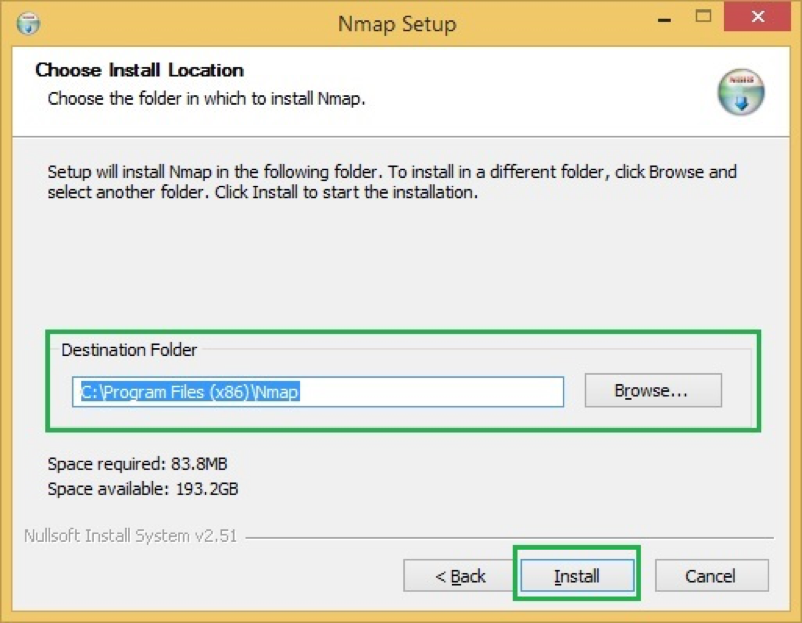
- It will start installing NMAP and once done; you will get confirmation
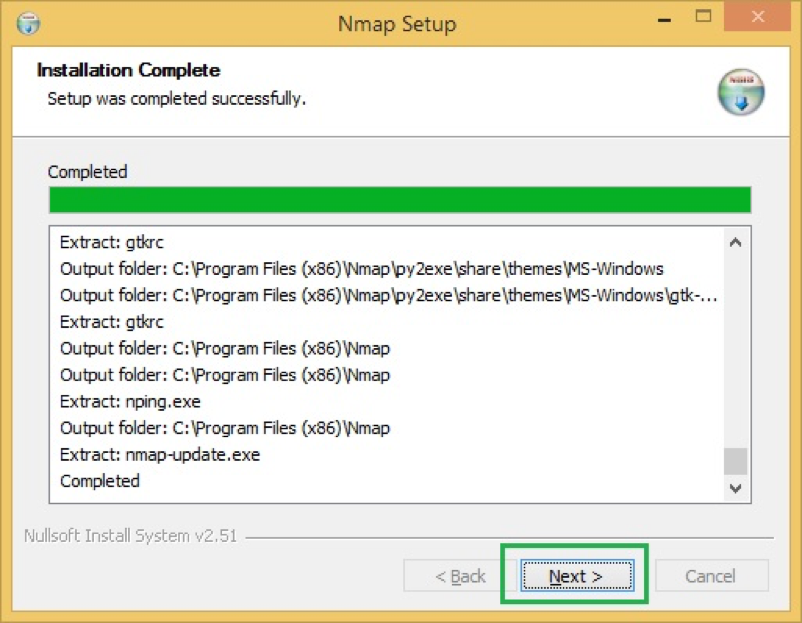
- This concludes NMAP is successfully installed.
Go ahead and play around with the tool to get an idea of how it works. Here are some examples.
Detecting the version
One of the wide uses for NMAP is to fingerprint the OS and running technologies.
nmap -sV $target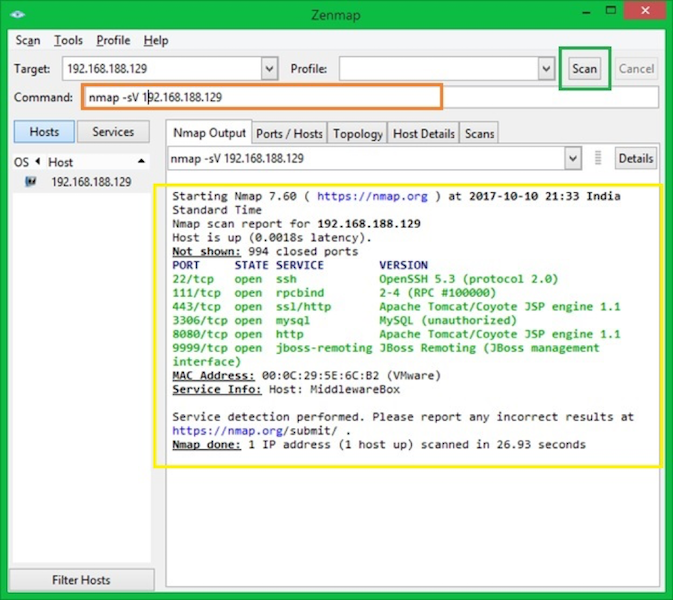
-sV command argument will detect the versions & state of running services
Checking certificate information
OpenSSL is mostly used to perform certificate operations like generation, verification, modification, etc. However, you can do certain things with NMAP as well.
nmap -p $port --script ssl-cert.nse $target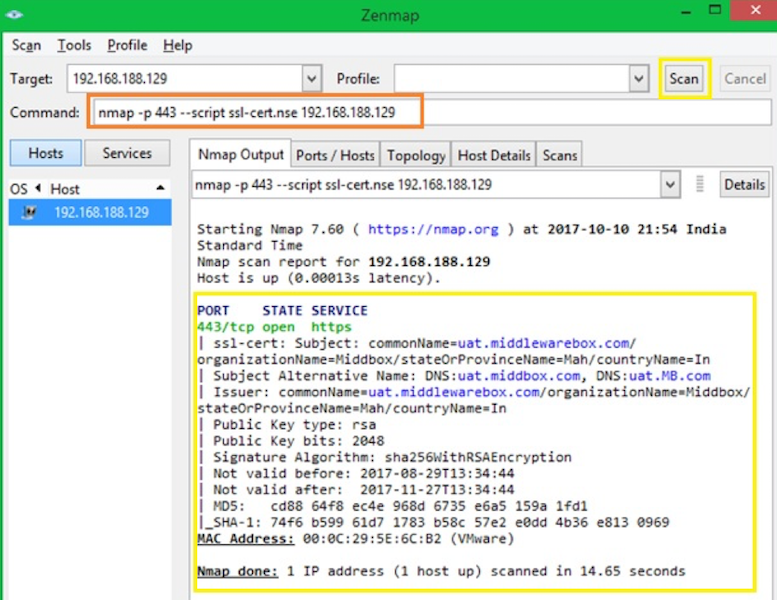
In case you are wondering, ssl-cert.nse the script gets installed along with NMAP. It’s available under the default location C:Program Files x86)Nmapscripts
Checking cipher information
ssl-enum-cihpers.nse script can be used to validate the SSL cipher information.
nmap -p $port --script ssl-enum-ciphers.nse $target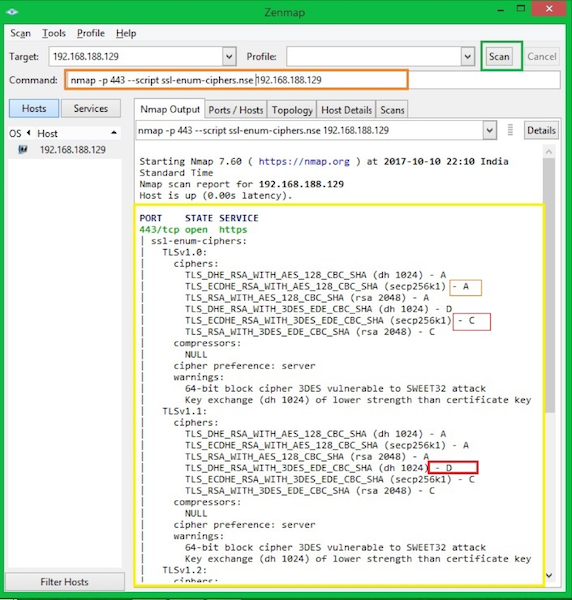
Each cipher suite is shown with a letter grade (A through F) indicating the strength of the connection. The grade is based on the cryptographic strength of the key exchange and of the stream cipher.
The message integrity (hash) algorithm choice is not a factor. The output line beginning with the least strength shows the strength of the weakest cipher offered.
To detect DH (Diffie-Hellman) vulnerability, you can use the below syntax.
nmap -p $port --script ssl-dh-params.nse $target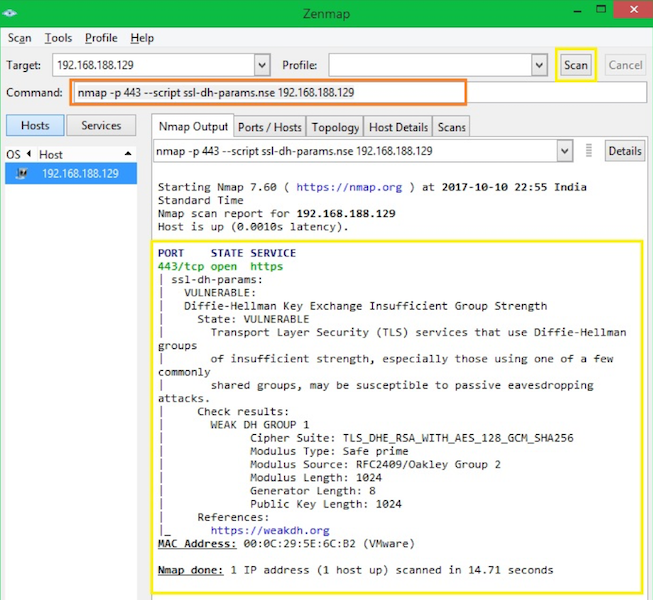
I hope this quick instruction helps you to install and get familiar with NMAP on Windows operating system.
If you are looking to master how to use NMAP then check out this online course by Jimmy Larsson.

