A good server administrator uses multiple strong passwords that are difficult to memorize; however, it is difficult and inconvenient to enter each one every time you access remote servers. To overcome this problem, in this tutorial, we will talk about passwordless SSH and how you can configure it on Linux!
What is Passwordless SSH?
Passwordless SSH allows you to export a client SSH public key to the remote server so the client can log in without requiring a password. The way to achieve this is by using an asymmetric key pair.
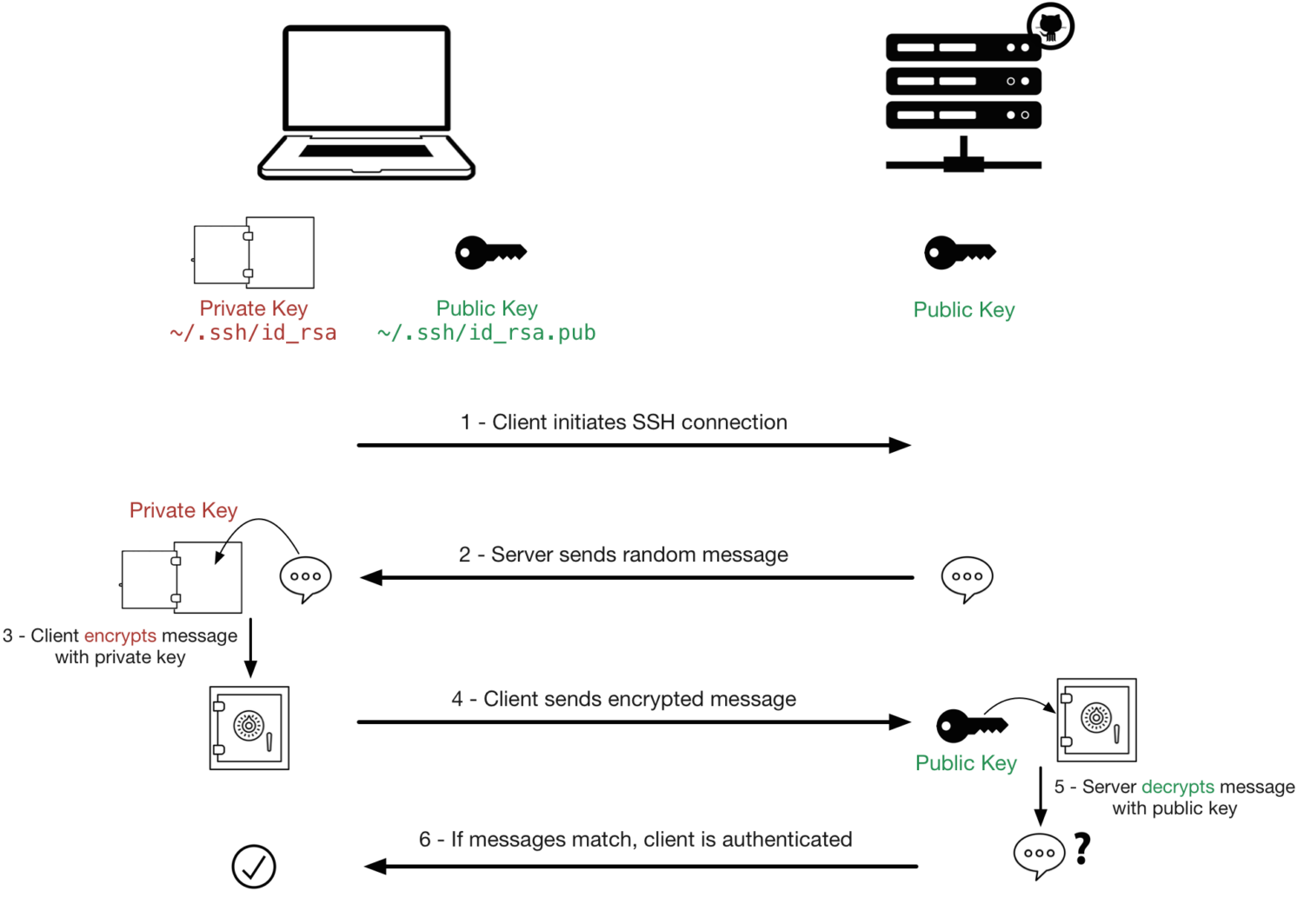
The authentication procedure works as follows:
When the client tries to access the SSH server, the server first checks if the client’s public key is authorized. If authorized, the authentication process continues. If it is not authorized, the process ends, and you cannot access the server.
If the server authorizes the client’s public key, the server encrypts a message with the client’s public key. Once the server has encrypted the message, it sends it to the client.
The client receives the message from the server. Once the message is received, the client tries to decrypt this message with the private key. If the client decrypts the message using the private key, the server will detect it, and the connection to the SSH server is established.
If the client cannot decrypt the message sent by the server, the connection process to the server is aborted.
Why use SSH Passwordless login
Passwordless SSH offers several benefits over traditional password-based login methods. Some of the most important benefits which make using passwordless SSH worthwhile are:
Convenient and Secure Login
The fact that you will not have to remember and enter passwords to connect to an SSH server makes the authentication process convenient. Moreover, it is based on public-private key cryptography, eliminating the risk of passwords getting stolen through man-in-the-middle and other phishing attacks.
Automate Backup Tasks
Using Rsync and other utilities, you can automate the task of making a weekly backup of the content generated in an office in the United States and saving it in an office located in China. The process would be encrypted through SSH and completely automatic because you won’t have to enter any password.
Mount a Remote File System
Passwordless SSH is useful if you need to mount a remote file system with SSHFS. By accessing the SSHFS server without passwords, we can make the SSHFS server mount itself when we start our client.
In addition, multiple git servers use SSH public key authentication. Therefore, the pair of asymmetric keys you create to connect to an SSH server can have other uses, such as authenticating while connecting to our Git server.
Setup SSH Passwordless Login in Linux
#1. Make sure that SSH Server and Client are installed
The first thing you have to do is ensure that the system that will act as the server has an SSH server installed. To do this, we have to open a terminal and type the following command:
sudo apt-get install openssh-serverIf no new package is installed in our operating system, the computer that will act as the server already has the SSH server installed and running. Similarly, ensure that the system that will act as a client has the necessary packages to connect to the SSH server. To do this, open a terminal and type the following command:
sudo apt-get install openssh-clientNowadays, most Linux distributions have an SSH client and server installed by default.
#2. Create the Asymmetric Key Pairs
Once you are sure that the SSH server and the client have the necessary packages, you can generate the asymmetric keys to access our SSH server without entering any password.
To do this, on the computer that will act as a client, you have to open a terminal and type the following command:
ssh-keygen -b 4096 -t rsaThe meaning of each of the command parameters is as follows:
ssh-keygen: it is the command that generates the key pair.
-b 4096: you are indicating that the asymmetric key to be generated has a size of 4096 bits. Other sizes that you can choose, for example, are 1024 or 2048.
-t rsa: Indicates that the algorithm used to generate the key pair must be RSA. Other algorithms that we can use are DSA, ECDSA, RSA1, and ED25519.
Right after executing the command, you will be asked the location where you want to save the keys and the name you want to give them. Just press the Enter key. This way, the keys that will be saved in the standard location, that is, /home/ user /.ssh/ and will have the standard name that id_rsa.
Next, you will be asked if you want to enter a password to encrypt the private key. Since we want to connect to the server without entering any password, press the Enter key without entering any password.
Finally, you are asked to re-enter the password. Since we have not entered any password, press the Enter key again.
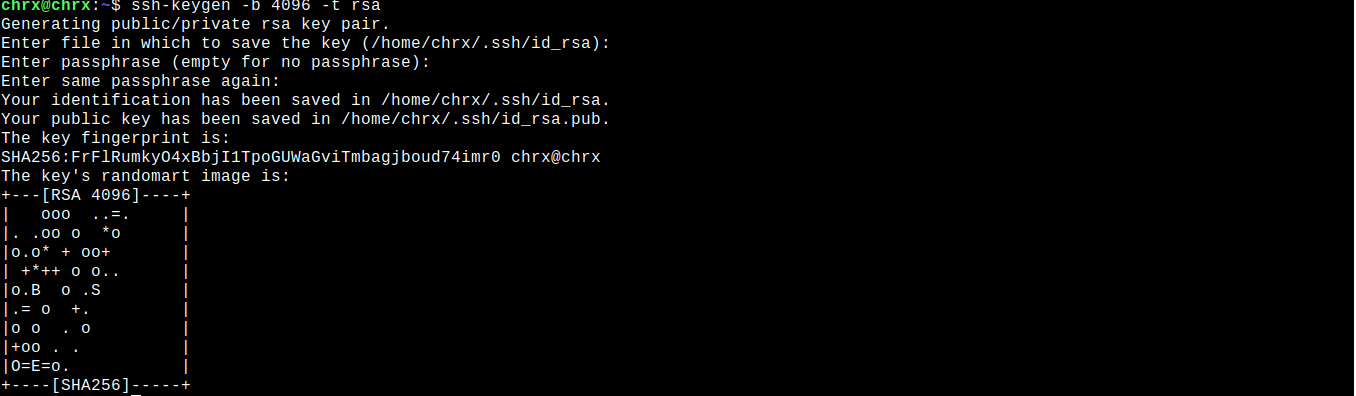
After performing these steps, the asymmetric keys will be created in the location ~/.ssh.
#3. Copy the SSH Public Key to the Remote Server
There are two types of SSH keys for organizing passwordless access via SSH: a non-secret public key (a public key) and a secret key (a private key), id_rsa is your private key, and id_rsa.pub is your public key.
You need to copy the public key to the remote server, either using the command ssh-copy-id or manually.
The typical syntax for the SSH public key copy command is as follows.
ssh-copy-id [email protected]The following example may be clearer:
ssh-copy-id [email protected]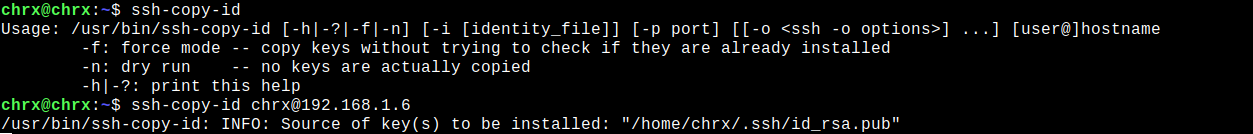
An alternative option is to log in to the remote server and create a text file in the directory ~/.ssh, for example, by running the following command.
nano ~/.ssh/authorized_keysCopy the contents of your file ~/.ssh/id_rsa.pub on your local machine into this file, save the file, and exit the text editor.
#4. Testing Passwordless Access Via SSH
To test if the passwordless SSH just try to access the SSH server:
$ ssh remote_username@server_ip_addressIf all went well, you would be logged in immediately without any password.
Disable SSH Passwordless Login in Linux
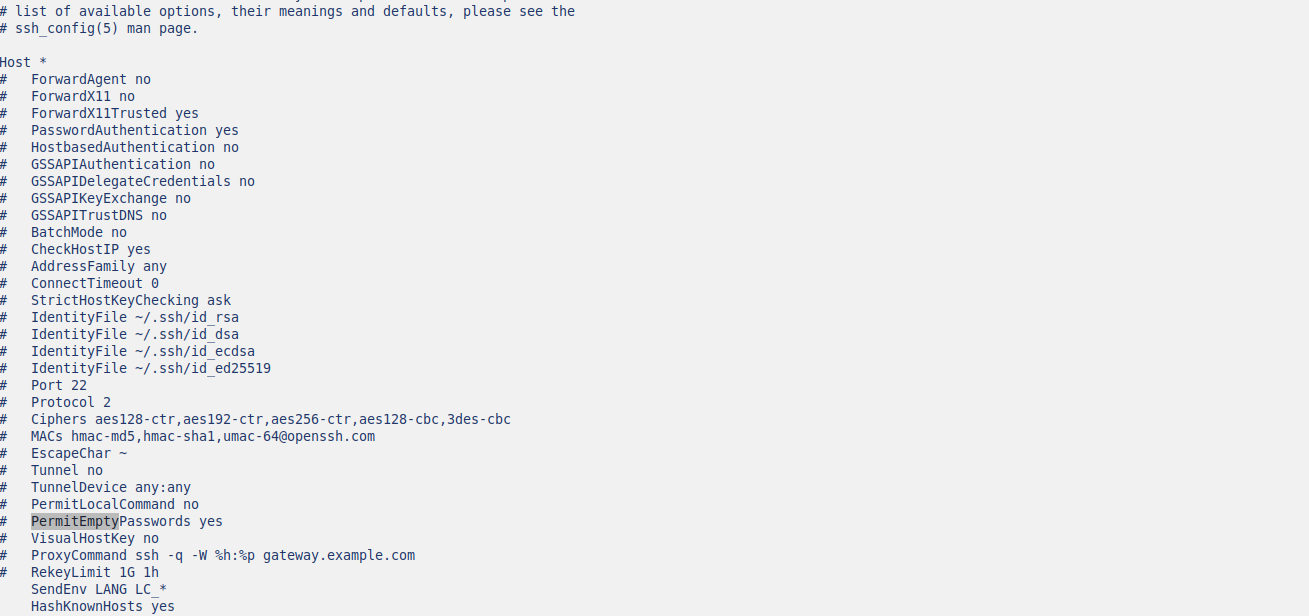
To disable the SSH Passwordless login open the SSH configuration file using your preferred text editor. On most distributions, the configuration file is located at /etc/ssh/sshd_config.
Locate the line that reads PermitEmptyPasswords yes and Change PermitEmptyPasswords yes to PermitEmptyPasswords no.
Save the changes to the configuration file and exit the text editor.
Restart the SSH to apply the changes:
sudo systemctl restart sshd Final Words
Passwords, no matter how complicated, are less secure, and when you have many servers or have to login frequently, the process becomes inefficient. Passwordless ssh authentication using asymmetric keys is not just more convenient but also more secure and protects you against phishing attacks.
You may also explore Symmetric Encryption.

