Let’s get informed about this 192.168.1.1 and learn best practices for utmost security.
Every device that connects to the internet needs an identity, better known as an IP address. And there are two types of it: public and private.
The public ones are by which every device is known to the outside internet. On the contrary, a private IP address is for internal network communication.
This private address network is used by a WiFi router which distributes the internet to the connected devices, creating a sub-network.
What does this have to do with 192.168.1.1?
192.168.1.1 is the default IP address (aka default gateway) typically assigned to the routers themselves in the private network.
There are others as well, such as 10.10.0.1, but 192.168… is the most commonly used by many router manufacturers.
On a user level, the primary objective is to access the router administration and network settings dashboard. The tweaks afterward depend on the specific router brand and model, however.
On a Windows PC, one can open the command prompt and type ipconfig/all to check the default gateway for the active connection.
So either you can let it remain untouched or modify a few things for a better and safe private network.
A Robust Home Network
One seldom thinks that their WiFi router can get hacked.
And since it’s the entry point to your home network, it’s fairly right to assume that every connected device becomes a target once the router’s security is jeopardized.
But there is always something you can do about it.
Changing Default Password
Changing factory-set passwords to their stronger versions is the first step everyone must take immediately.
Based on the router interface, the exact steps may differ.

Still, you can find these options primarily under security, maintenance, or something similar.
If you don’t remember the stock password, try using password, admin, root, etc. Alternatively, contact your service provider for the details. The default password may also be written under the device or on the box in some cases.
Moreover, you can use your smartphone to check the active password.
For iPhone, enter Settings > Wi-Fi, and tap 🛈 beside the connected network. Now, tap on the Password to reveal it.
For Android, enter Settings > Network & internet, and tap on the active Wi-Fi. Now, tap the gear icon and then Share. This will reveal a QR code for WiFi sharing with the password indicated below it.
However, this is valid for stock Android, and the exact procedure depends on the subject Android UI.
And yes, why not change the login username as well?
Some ISP-shipped routers might not have this provision to opt for a different username.
Encryption Mode
While we connect the router, we hardly give a thought about how safe data travels over the network.
And just because it’s inside your home doesn’t mean it’s safe from the prying eyes of cybercriminals who might be your next-door neighbor (who knows) or anyone in your WiFi range.
This vulnerability is taken care of by encryption.
Encryption, in layman’s terms, is jumbling up plain text into something illegible.
And there are many encryption standards:
- WEP
- WPA
- WPA2 (AES)
- WPA2+WPA
- WPA3 (AES)
- None (no encryption), etc
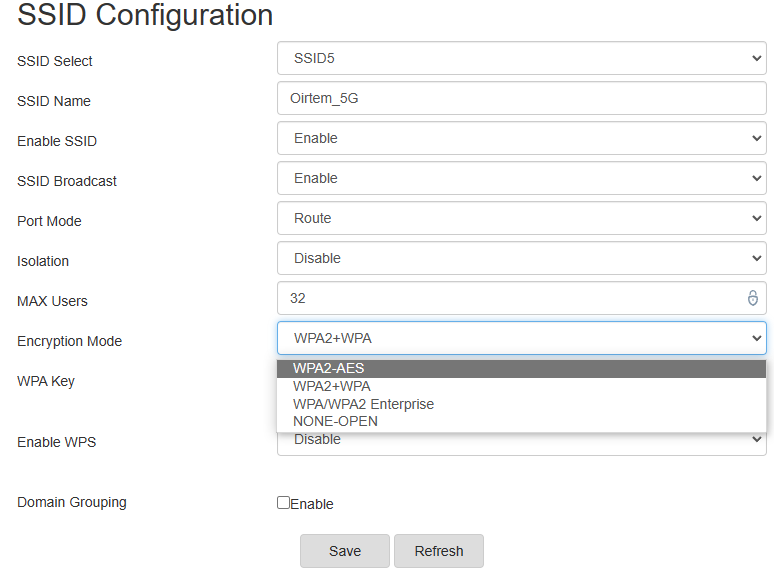
A rule of thumb here is to always use the latest WPA version available with your WiFi router. For instance, my router can do WPA2-AES at its best (which is outdated than the more recent WPA3).
Moreover, switching to AES WPA encryption and disabling TKIP (an outdated encryption protocol) will be better.
Importantly, setting it to Open/None allows people in your range to see everything, including the websites you visit, your personal information, etc., which is absolutely not recommended.
And lastly, using mixed modes (like WPA+WPA2) isn’t secure either; instead, we should enforce the latest security protocols exclusively.
MAC Address Filtering
A Media Access Control (MAC) address represents a device on a network and is linked to the hardware.
This is a handy way to keep outsiders at bay even if they manage to hack your WiFi password.
In short, you need to input MAC addresses for every device which you want to connect to the WiFi router.
This is called MAC address filtering, and it’s an additional security measure that is often used to prevent WiFi theft.
However, this isn’t considered to be very reliable against a skilled bad actor trying to snoop over the data transfer. In such a case, using the strongest possible encryption is the primary security measure one should take.
SSID Configuration
For your WiFi router, you can assume Service Set IDentifier (SSID) as its name. This is what we see in the WiFi scanning, and then tap to connect to it.

The first thing is to change the default SSID name because it can expose the router’s model, which makes it all the more vulnerable to hacking.
Next, one can disable SSID broadcast. This will hide its name whenever a device scans for nearby networks.
Subsequently, you’ll have to manually add this network to all your devices. For that, you’ll need some details like the network SSID, password, and encryption mode (as discussed above) in use.
This makes your private network hard to detect and safe from attacks.
Login URL
Changing 198.168.1.1 to something else, for instance, 198.168.120.1, will further help our cause.
The primary reason to do so is to stay away from the default configurations, just like we did with the password and SSID name.

Remember to match the DHCP Start and End IP addresses with the LAN IPv4 address. Failing to do so might give “LAN address and DHCP should be in the same subnet!” error.
For instance, my original configurations were:
IPv4: 192.168.1.1
DHCP Start IP Address:192.168.1.2
DHCP End IP Address:192.168.1.254
Here, DHCP start and end IP address specify a range of IP addresses that will be dynamically allotted by the router to the connected devices, such as smartphones, PCs, smart TV, etc.
So, when I changed my router login URL (aka default gateway) to 192.168.120.1, DHCP had to be modified accordingly (can you see the difference?).
Others
A few other things weren’t there with my ISP-supplied router, including guest network, automatic firmware updates, range control, disabling remote admin access, and more.
So basically, it boils down to your hardware and its security protocols.
Related: Check out some best WiFi routers for personal and business use.
For instance, you can set up a guest network that has many options like network speed limits, schedule on/off, and more. In short, it helps you to share your network with others without changing the settings of your home network.
Similarly, automatic firmware updates go a long way in ensuring that your router doesn’t have vulnerabilities.
Another crucial option can be turning off remote access. Because though it may feel convenient to access the router from outside, a hacker might exploit this added privilege.
However, try installing a premium VPN on your router if your data is extremely sensitive. This will protect the data with multiple layers of encryption, matching bank-grade security.
Finally, check out if there is any firewall configuration in the router settings. Generally, it’ll be a toggle without many details. Still, turning it on is on the safer side, especially if it isn’t hindering your routine work.
Wrap Up!
192.168.1.1 is the default gateway through which you can access your WiFi router admin panel.
However, there are a few security tweaks that include changing this URL to a different one. Besides, one should update factory-set SSID, password, and mostly everything to their more secure versions, as discussed in this article.
And while it may seem unnecessary, upgrading to a different and more secure router is completely normal.
PS: As an internet source, they don’t have to be immobile, especially when you can have portable routers.

