Phishing attacks continue to pose a significant threat to businesses by putting sensitive information at risk.
Businesses can strengthen their defenses & minimize the impact of phishing attacks by implementing robust security measures and using the power of anti-phishing tools.
Let’s dive into the best Anti-phishing tools. Later in this article, I will explain more about how to identify phishing scams and the effect of phishing on your business.
- 1. Avira
- 2. TitanHQ Anti-Phishing Protection
- 3. ManageEngine
- 4. Avanan
- 5. ZeroFox
- 6. Cofense
- 7. Check Point
- 8. BrandShield
- 9. Ironscales
- 10. Mimecast
- Show less
You can trust Geekflare
At Geekflare, trust and transparency are paramount. Our team of experts, with over 185 years of combined experience in business and technology, tests and reviews software, ensuring our ratings and awards are unbiased and reliable. Learn how we test.
1. Avira
Avira is a well-known cybersecurity company that offers a range of products and services, including antivirus software & online security solutions. Its phishing protection feature is designed to help users detect and prevent phishing attacks.
This tool actively scans websites and emails in real time, which identifies and blocks phishing attempts before they can reach the user.
Avira Features
- Provides a browser extension or toolbar that integrates with popular web browsers such as Chrome and Firefox. This toolbar displays safety ratings for websites by indicating whether they are safe, suspicious, or known phishing sites.
- Integrated advanced URL analysis techniques to assess the legitimacy of website links. It checks for signs of phishing, such as suspicious domain names or deceptive redirects, to identify potential threats accurately.
- It alerts users when they visit a potentially dangerous website which provides an extra layer of protection.
- Comes with a user-friendly interface which makes it easy for users to understand & navigate the security features. Clear visual indicators and alerts help users make informed decisions while browsing the web or interacting with emails.
- Allow the users to report suspected phishing sites they encounter. This collective intelligence allows Avira to continuously update & improve its phishing protection capabilities that help to keep users safe from emerging threats.
2. TitanHQ Anti-Phishing Protection
TitanHQ’s anti-phishing solution is a cloud-based, AI-driven, enterprise phishing protection and security solution for companies using Microsoft 365. It provides advanced phishing protection against malicious email, utilizing the most sophisticated tools in the IT world.
TitanHQ delivers high anti-phishing accuracy and minimal false-positive results using AI, curated threat intelligence feeds, and end-user feedback.
TitanHQ delivers advanced security with protection from zero-day attacks through multi-faceted analysis of emails, and time-of-click techniques. It can be deployed in minutes and is managed from a single interface, allowing administrators to cleanse multiple inboxes in one click.
TitanHQ Phishing Protection Features
- AI-Driven Analysis: Multiple layers of analysis (textual analysis, link analysis, attachment scanning) and machine learning (ML) detection models are used to analyze the email body and determine if an email is a phishing attempt.
- Post Delivery Remediation: MSPs need a way to remove threats already delivered to their users’ inboxes. Post Delivery Remediation provides the capability to remove malicious mail that has arrived in an inbox.
- Detailed & Insightful Reports: PhishTitan surfaces threat data and analytics to help customers assess their risk profile. Provides automatic warning of suspect emails. Feedback using Outlook add-in.
- Spam & Malware Protection: PhishTitan uses the Microsoft API to integrate into Outlook and scan emails for the most dangerous malicious threats.
- Banner Notifications: To inform and educate users, we provide banners at the top of unsafe emails indicating that this mail has been identified as malicious.
- Industry Leading Support Team: Renowned for our focus on supporting customers with a 98% customer satisfaction rate in 2022.
3. ManageEngine
ManageEngine Browser Security Plus is a comprehensive security solution designed to enhance web browsing security for enterprises. It provides centralized control & allows customization of security settings to meet specific security requirements.
It offers advanced web filtering capabilities that allow administrators to block access to malicious websites, inappropriate content, and other web-based threats. This helps protect employees from accessing potentially harmful websites and reduces the risk of malware infections & phishing attacks.
ManageEngine Features
- Ensures a safe browsing experience for users by actively blocking access to known malicious websites and providing alerts to users when they attempt to access dangerous or suspicious websites.
- It uses threat intelligence to analyze websites and URLs in real-time that detects and prevents users from visiting phishing sites & becoming victims of fraud.
- Allows administrators to enforce security controls on web browsers used within the organization. This includes managing browser extensions, disabling insecure protocols, controlling cookie settings, and implementing other security configurations to minimize vulnerabilities.
- Generate detailed reports and analytics on web usage & user behavior.
- Integrates with threat intelligence data streams to get information on new threats and known malicious websites.
Learn more about these best threat intelligence platforms.
4. Avanan
Avanan is a cloud security company that specializes in providing advanced email & collaboration security solutions. It offers a cloud-native platform designed to protect organizations from various email and collaboration threats, such as phishing attacks, malware, data leakage, and account compromise.
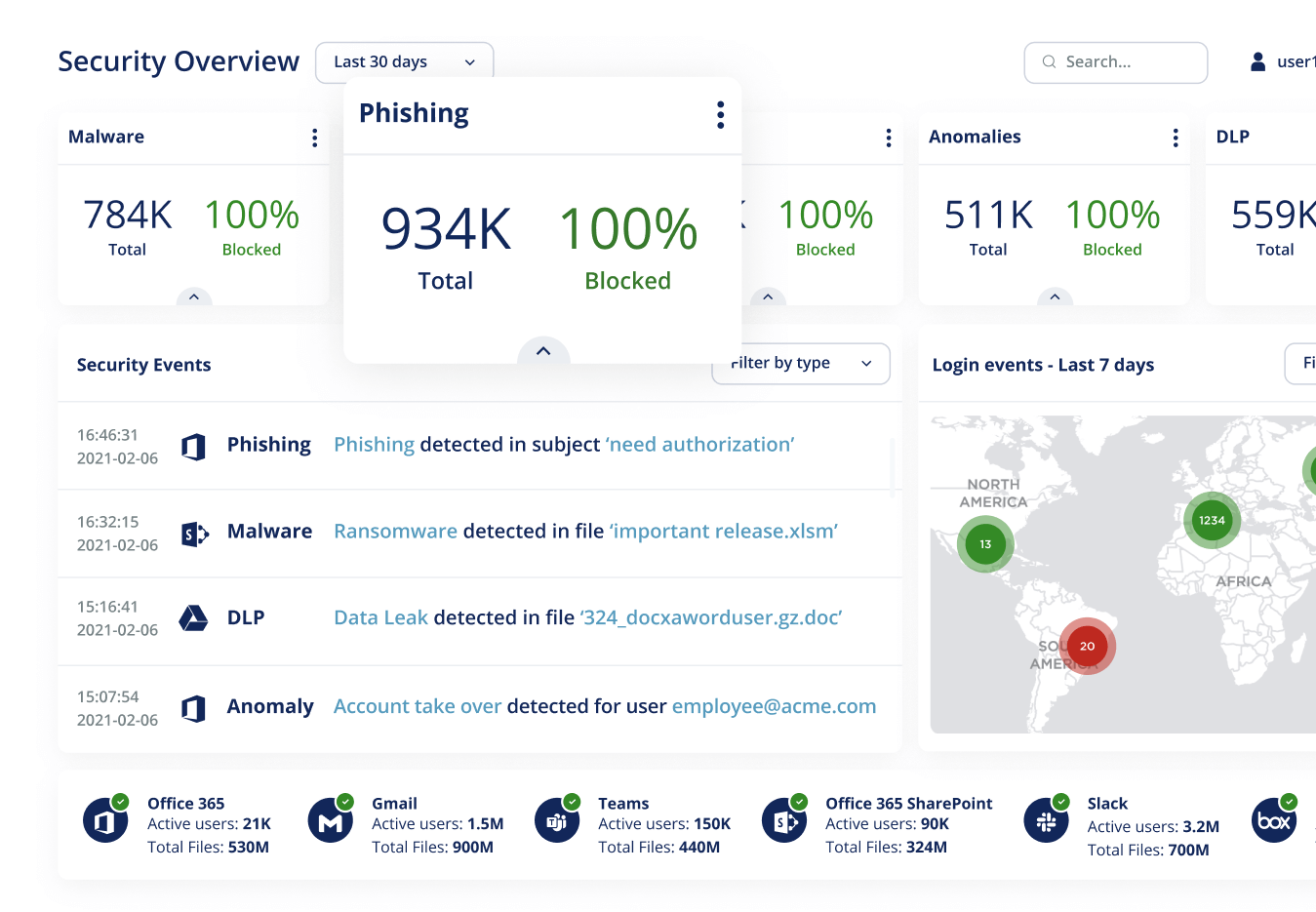
Anti-phishing software is one of the security solutions it provides. Allows the users to actively participate in the security process. That means they can report threats, receive automated alerts about potential attacks, and access educational resources to enhance their security awareness.
Avanan Features
- It uses artificial Intelligence & ML algorithms to thoroughly analyze every aspect of an email. This advanced analysis helps identify sophisticated phishing attacks that may otherwise go undetected.
- Ability to Integrate with API for better identification of user impersonation (pretending to be) and fraudulent messages – particularly in Business Email Compromise (BEC) attacks.
- You can gain complete visibility into your entire suite of cloud applications. This enables you to monitor for malicious behavior, identify compromised accounts, and take proactive measures to prevent further damage.
- Avanan continues to be at the forefront of the security landscape by reporting on modern phishing attacks that bypass conventional safety protocols.
- It provides dedicated one-on-one customer support to ensure a continuous security experience.
5. ZeroFox
ZeroFox Anti-Phishing software protects organizations & individuals from digital threats. These platforms are designed to address a wide range of risks, including phishing attacks, social media threats, brand hijacking, data exfiltration, and more. ZeroFox aims to provide organizations with real-time protection by using diverse data sources and advanced analytics.
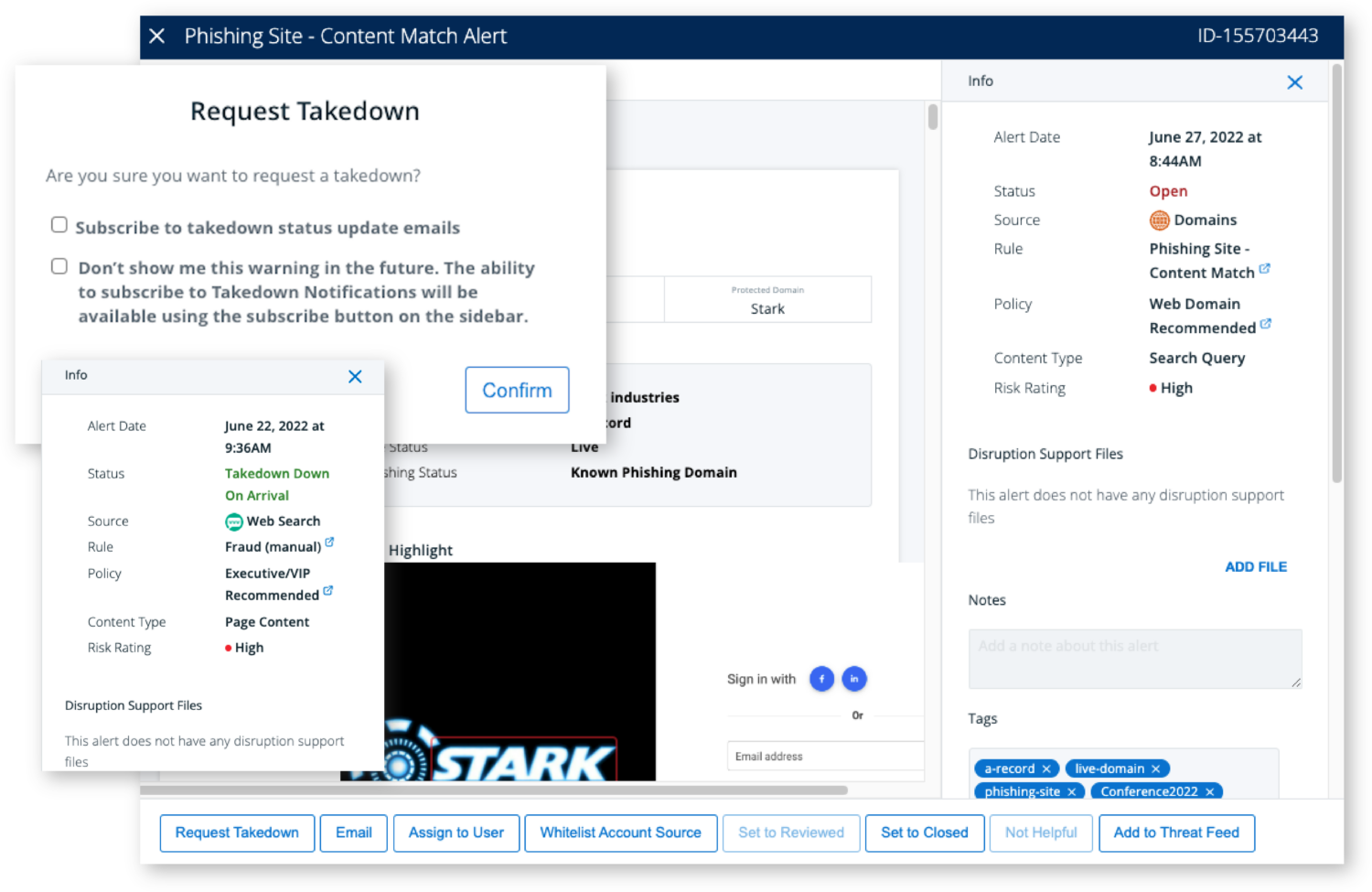
It offers advanced anti-phishing tools and solutions to protect organizations from targeted attacks.
ZeroFox Features
- Advanced detection techniques to identify phishing attacks & malicious websites in real time. This includes monitoring for suspicious URLs, email spoofing, and social engineering tactics commonly used in phishing campaigns.
- Utilizes DMARC (Domain-based Message Authentication, Reporting, and Conformance) and abuse inbox monitoring to protect users wherever they engage, including email communications.
- Security coverage across different platforms, including email, websites, social media, and other digital channels.
The company’s mission is to create a safer digital world by helping organizations safeguard their online presence, protect their reputation, and mitigate potential risks that could lead to financial loss.
6. Cofense
Cofense is a cybersecurity company that specializes in helping organizations defend against phishing attacks and other email-based threats. They provide a range of solutions and services to help organizations analyze and respond to phishing attempts.
Cofense offers a platform called the Cofense Intelligence Platform – which provides live threat intelligence and analysis to help organizations stay ahead of evolving phishing threats. It makes use of machine learning and other advanced techniques to detect and analyze suspicious emails.
The company offers other services also, including incident response solutions, phishing awareness training programs, and managed security services.
Cofense Features
- Cofense offers a phishing simulation platform that allows organizations to create and send simulated phishing emails to their employees.
- Provides incident response solutions to help organizations quickly detect, analyze, and respond to phishing attacks.
- Uses advanced email analysis techniques to detect and identify potential phishing attacks. Their solutions analyze email headers, content, and attachments to discover suspicious patterns and indicators of phishing.
- Allows employees to report suspicious emails through their user-friendly reporting interface.
7. Check Point
Check Point Anti-Phishing is a complete solution designed to prevent and protect against various types of phishing attacks. It offers superior prevention capabilities by blocking even the most advanced phishing attacks, including Business Email Compromise and impersonation.
This product covers multiple attack vectors, including email, mobile devices, and endpoint devices, which ensure that all access points are protected from phishing attacks. This multi-layered approach helps safeguard users across different platforms and devices.
Check Point Features
- Makes use of ThreatCloud AI, which is powered by a powerful threat intelligence database. This integration enables the system to stay up-to-date with the latest phishing threats and provides active protection against emerging attacks.
- User-friendly interface that simplifies the configuration, monitoring, and management of anti-phishing measures.
- Includes click-time URL protection that examines and blocks suspicious links in real-time. This feature reduces the risk of users accessing malicious URLs embedded in emails.
- Check Point Anti-Phishing inspects all aspects of incoming emails, including attachments & links, which ensures that potential threats are detected and eliminated before they reach the user’s mailbox.
- Also provides granular visibility into phishing attacks – particularly in Office 365 and G Suite environments.
- Ability to integrate with existing security infrastructures and workflows without disrupting productivity.
8. BrandShield
BrandShield is a leading brand-oriented digital risk protection company that specializes in monitoring, detecting, and removing a wide range of digital threats that can harm businesses and their brands.
It helps companies safeguard their brand integrity and protect their customers in the online environment with an advanced suite of services.
BrandShield empowers companies by providing them with full visibility of the digital threats they face. You can understand what potential risks are present and take appropriate actions to mitigate them.
BrandShield Features
- The Anti-phishing dashboard offers innovative features such as the Website Duplication Detector, which helps identify copied websites used for phishing.
- It is also possible to speed up the removal of dangerous content by using automated takedown requests.
- Employs experienced enforcement managers who analyze the threats specific to your company and use efficient strategies to counter them effectively.
- Utilizes cutting-edge technology to locate logos within various graphic items. This capability helps in identifying instances of brand misuse or unauthorized usage.
- Major social media platforms are monitored to detect phishing attempts.
- Provides periodic reports that offer detailed insights into the monitoring and enforcement activities that help you stay informed about the effectiveness of the security measures implemented.
9. Ironscales
Ironscales is an integrated cloud email security (ICES) platform that offers a comprehensive solution for enterprise email security. It prevents email spoofing, impersonation, and non-signature-based BEC attacks in real-time. Their unique “fingerprint” technology checks every employee’s inbox for abnormal behaviors.
The platform safeguards organizations against zero-day malware, credential theft, and phishing websites. It uses real-time defense mechanisms, including multi-antivirus engines and visual anomaly detection, to detect and block such threats.
Ironscales Features
- Uses advanced algorithms to identify & flag potential phishing emails.
- The software enables quick incident response by providing automated email forensics, incident remediation, and real-time alerts to security teams.
- Also include features to educate employees about phishing threats, such as interactive training modules and simulated phishing campaigns to improve their awareness about such attacks.
- Uses threat intelligence feeds and data from global security networks to actively detect & block phishing attempts.
- Provides extensive reporting and analytics to give businesses insights into their phishing threat landscape.
10. Mimecast
Mimecast is a company that specializes in providing advanced email & collaboration security solutions to mitigate risks associated with malicious cyberattacks, human errors, and technological vulnerabilities.

Their phishing protection software offers multiple layers of defense against phishing attacks and other advanced threats.
Impersonation Protect: This layer focuses on defending against social engineering attacks such as whaling and business email compromise. Mimecast scans inbound emails for signs of social engineering and blocks suspicious messages.
URL Protect: Mimecast’s software rewrites all links in inbound emails and scans the destination websites in real-time when clicked.
Attachment Protect: This layer prevents employees from opening potentially dangerous attachments. Built-in sandbox technology isolates attachments that contain malicious code.
Here is more information about this Targeted Threat Protection. Feel free to visit this page.
Mimecast Features
- Provides robust protection against various types of phishing attacks without requiring additional infrastructure or excessive IT overhead.
- The software can be implemented across different devices, including mobile devices, without disrupting user workflows.
- Mimecast offers end-to-end threat analysis and reporting that enables organizations to gain insights into ongoing threats and take appropriate actions.
Let’s now learn how to identify phishing scams and the importance of anti-phishing tools.
How to identify a phishing scam?

Phishing scams often arrive in the form of emails, messages, or websites that appear genuine but are designed to deceive unsuspecting victims. Here are some key indicators to look out for:
Suspicious email addresses or domains
Check the sender’s email address carefully. Pay attention to misspellings or variations in the sender’s address.
Urgency and Fear Tactics
Those emails frequently create a sense of urgency or use threats to prompt immediate action, such as claiming an account will be closed if not verified promptly.
Poor Grammar and Spelling
Many phishing attempts originate from non-native English speakers with rushed composition and translation, which results in grammatical errors and typos in their messages.
Suspicious Attachments or Links
Hover your mouse over links before clicking on them to check the URL. Phishing emails may include masked URLs that redirect to fraudulent websites.
And here is a list of the best URL scanners to check if a link is safe.
Requests for Personal Information
Legit organizations rarely request sensitive information via email or text messages. Be cautious when asked to provide personal data, account credentials, or financial details.
Effect of Phishing on Businesses

Phishing attacks can have a severe effect on businesses. It is important for organizations to implement active measures to mitigate these risks. Here are some key strategies for businesses to stay prepared.
#1. Financial Losses
Falling victim to a phishing attack can result in significant financial losses for businesses. Fraudulent access to financial accounts, unauthorized transactions, or stolen customer payment information can directly impact business operations. To minimize financial risks, businesses should:
- Implement robust payment security measures such as encryption & secure payment gateways.
- Monitor financial transactions regularly for any suspicious activity.
- Train employees to identify phishing attempts and report them quickly.
#2. Data Breaches and Loss of Confidential Information
Phishing attacks often target sensitive business data, including customer information, trade secrets, or intellectual property. Exposure to confidential information can harm business operations and customer trust. To safeguard against data breaches, follow these:
- Encrypt sensitive data and implement access controls to limit unauthorized access.
- Regularly update and patch software to address security vulnerabilities.
- Conduct security audits & penetration testing to identify weaknesses in systems.
Your organization may use some of these premium penetration testing tools to identify vulnerabilities.
#3. Reputational Damage
Successful attacks can tarnish a business’s reputation, which leads to a loss of customer trust.
- Establish clear communication channels to address customer concerns and provide timely updates regarding security incidents.
- Invest in brand monitoring and employ reputation management tools to detect & mitigate negative online content related to phishing incidents.
- Educate customers about phishing risks and provide guidance on how to identify and report phishing attempts.
Learn more about online reputation management and some tools that can help you manage your reputation.
#4. Legal and Regulatory Consequences
Depending on the nature of the business and the data compromised, phishing attacks may lead to legal consequences. Non-compliance with data protection regulations such as the General Data Protection Regulation (GDPR) can result in fines.
- Stay informed about relevant data protection laws and regulations.
- Implement security measures aligned with industry standards and best practices.
- Conduct regular security audits & risk assessments to identify potential compliance gaps.
#5. Employee Awareness and Training
Employees are often the first line of defense against phishing attacks. Businesses should prioritize ongoing security awareness training to ensure employees can identify and report phishing attempts effectively. Key strategies include:
- Conducting regular phishing simulation exercises to test employee response & provide targeted training where needed.
- Establishing clear reporting procedures for suspicious emails or incidents.
- Promoting a culture of cybersecurity awareness and responsibility across the organization.
Importance of Anti-Phishing Tools

To mitigate the risks associated with phishing attacks, businesses need to adopt comprehensive anti-phishing tools. These tools offer the following benefits:
Real-time threat detection
Anti-phishing tools use advanced algorithms and machine learning techniques to identify and block phishing attempts in real time that, ensure immediate protection.
Email filtering and link scanning
These tools scan incoming emails for suspicious content, attachments, and URLs that filter out potential phishing attempts before they reach users’ inboxes.
Visit this page for the best email spam filtering and protection solutions.
Employee awareness and training
Many anti-phishing tools provide training modules and simulated phishing exercises to educate employees about the risks and best practices for identifying & avoiding phishing scams.
Reporting and analytics
Detailed reporting and analytics capabilities allow businesses to track and analyze phishing attempts, identify trends, and strengthen their security measures.
Enhanced website protection
These tools also offer website monitoring and protection features, such as safeguarding against phishing attacks targeting online forms, login pages, and customer data.
Conclusion
In this article, we discussed the nature of phishing scams and provided info on how to identify and avoid falling victim to them.
We also explored the best anti-phishing tools and their valuable role in enhancing security.
These tools offer advanced capabilities such as real-time threat detection, email analysis, URL scanning, employee awareness training, and automated incident response.
Organizations can stay one step ahead of cybercriminals and protect their valuable assets by using these tools.

