IT security faces a wide variety of threats every day – from different kinds of malware infecting endpoints and servers to coordinated attacks against entire networks.
Each kind of threat to the IT system requires a particular solution and strategy. This usually forces companies to invest heavily in protecting their vulnerabilities – the more and more varied the number of vulnerabilities, the greater the investment in security.
Not all companies can afford the cost of protecting all their cybersecurity flanks. As a result, many companies adopt the (wrong) strategy of protecting themselves as far as the budget allows. And, consciously or unconsciously, they leave vulnerable areas exposed to very dangerous threats.
The Solution: Unified Threat Management (UTM)

Unified Threat Management, or UTM, traditionally offered a solution for organizations that don’t have the resources – knowledge, people, money, etc. – required to protect all their vulnerable areas. UTM provides a single point of protection against all known types of threats: malware (viruses, worms, spyware, etc.) and network attacks (denial of service, phishing, SQL injection, etc.).
Also Read: Email Security Solutions to Protect from Spam, Spoofing, and Phishing Attacks
Combining performance, security, and compliance capabilities in a single installation greatly facilitates security management for network administrators, thereby lowering the costs of keeping a company’s IT infrastructure protected.
FortiGate NGFW
FortiGate is an NGFW that contains all the capabilities of a UTM since it offers features such as content filtering, antivirus, email filtering, web filtering, and email control. It is a highly recommended product for organizations that meet the condition of being a small or medium-sized company that runs high risks or handles very critical data. It needs to carry out a deep scan of every packet that traverses its network boundaries.

The FortiGate firewall features highly efficient security processors that optimize network performance while protecting the network from cyber-attacks. It is capable of operating in transparent mode or NAT/Route mode. In transparent mode, the firewall is installed between the internal network and the router, so no network changes are required, except for providing the device with a management IP address.
Transparent mode is mainly used when it is necessary to increase network protection, but changing the network configuration is not a viable alternative. In NAT/Route mode, the FortiGate unit is installed as a gateway or router between two networks. This allows the NGFW to hide the IP addresses of the private network through network address translation (NAT).
If your existing infrastructure is on AWS, you can deploy FortiGate on AWS.
Heimdal
Heimdal’s Unified Threat Dashboard is the ultimate solution for businesses looking to protect their digital assets from cyber threats. It combines Heimdal’s top-of-the-line security products into one powerful platform, allowing organizations to easily manage their cybersecurity measures from a single, intuitive dashboard.
The platform provides a comprehensive overview of your organization’s security posture, giving you real-time information on any potential threats or vulnerabilities. It also offers a wide range of features that enable businesses to defend themselves proactively against potential cyber threats, including network scanning, malware detection, and vulnerability assessments.
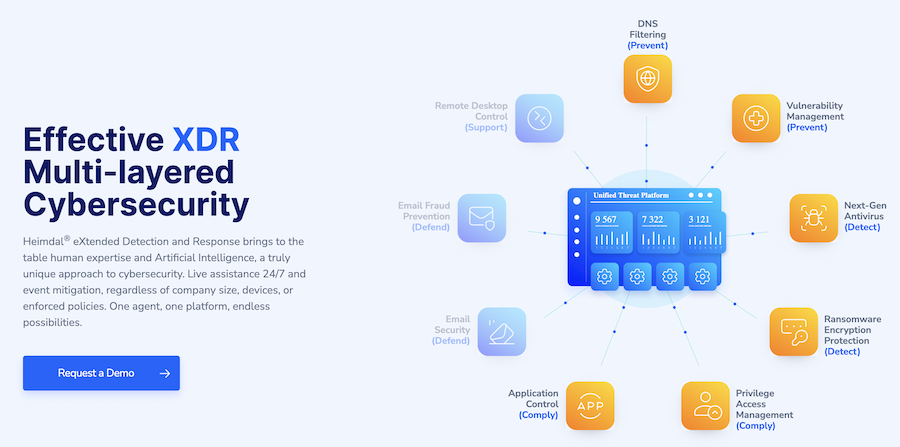
With the Unified Threat Dashboard, organizations can easily monitor their network traffic, identify suspicious activity, and quickly respond to threats. This is achieved through Heimdal’s advanced threat detection and prevention technologies, including Threat Prevention, Patch & Asset Management, and Next-Gen Antivirus.
Businesses can easily customize the dashboard to suit their specific needs, allowing them to focus on the areas of their network that are most vulnerable. Additionally, the platform is designed to be highly intuitive, making it easy for non-technical users to manage their cybersecurity measures effectively.
Their cybersecurity solutions package offers the flexibility to use them individually as standalone products, or to integrate them seamlessly into a cohesive and unified suite. Heimdal’s Unified Threat Dashboard is an essential tool for any business looking to protect itself from the growing threat of cyberattacks. With its powerful features, intuitive design, and comprehensive protection, it provides businesses with the peace of mind they need to focus on what they do best – growing their business.
WatchGuard Firebox
WatchGuard’s UTM Firebox solutions offer enterprise-grade security without the cost and complexity of products specifically targeted at the enterprise segment. They are centrally managed and provide total network visibility. The UTM platform is part of the WatchGuard Cloud ecosystem, including wireless access point management and a multi-factor authentication (MFA) solution.
Firebox covers the features expected of a UTM, such as a firewall, VPN, antivirus, web filtering, and intrusion prevention. To these options, it adds other security tools that complete strong protection of the network and digital assets, with the addition of application layer inspection, deep packet inspection, email protection, and malware detection with behavioral sandboxing, among many others.
The Firebox solutions incorporate several intelligence tools that are continuously updated (in addition to the signature database): new threat data, feedback loops for updating blacklists, behavior-based malware detection, and machine learning for TDR scoring models.
WatchGuard offers its Firebox on a wide range of hardware devices and also provides a virtual version that runs on ESXi or Hyper-V. In addition, there are versions for public clouds on Amazon AWS marketplace and Azure.
Sophos UTM
Sophos UTM is a modular appliance designed to simplify security management with an intuitive interface that makes it easy to create policies to control risks and threats. It also offers clear and detailed reports that provide everything needed to understand a network’s security posture and improve its performance.

The solution uses a multi-layered protection technology that includes Advanced Threat Protection (ATP), an intrusion prevention system (IPS), a virtual private network (VPN), email filtering, and web filtering. The level of protection can be chosen thanks to a modular subscription scheme, as each feature is available on all appliance models.
Sophos UTM users highlight the benefit of centralized integration for easy management, along with a high update frequency that provides peace of mind that no new threat will attack the network before there is protection against it. In addition, firewall and VPN configurations are intuitive and straightforward. The drawbacks mentioned by users of their UTM solution are that it is not compatible with Sophos cloud solutions and that the technical support response time could be better.
In conclusion, for users looking for a simple and effective UTM solution that brings together what is needed to protect networks for organizations that do not have large IT security budgets, Sophos UTM is a good choice.
Cisco Firepower NGFW
Cisco NGFW firewalls offer advanced threat defense capabilities to meet various needs, from small or branch offices to high-performance data centers and service providers. These appliances are available in a wide range of models, including virtual versions – called Firepower NGFW – available for cloud infrastructures.
The advanced threat defense capabilities of the Cisco NGFWs include next-generation IPS (NGIPS), security intelligence (SI), advanced malware protection (AMP), URL filtering, application visibility and control (AVC), and flexible VPN capabilities. The encrypted traffic inspection offered by Cisco in its NGFWs automatically classifies risks, quickly prioritizing threats and reducing the volume of logged events.
The configuration flexibility of these devices allows them to be deployed in clusters that achieve higher performance along with high availability and scalability (both up and down). Integration with Cisco Defense Orchestrator (CDO) unifies the management of physical and virtual firewalls, reducing the need for administration resources.
The costs of Firepower NGFW appliances are high relative to UTM solutions for more constrained environments. However, those who use them in industries that handle highly sensitive information, where a security breach can cost millions of dollars, claim their prices are a bargain.
SonicWall TZ NGFW
SonicWall TZ small form factor next-generation firewalls are designed specifically for the needs of enterprise and midsize businesses, providing them with an enterprise-class security solution that avoids the complexities usually associated with such solutions. SonicWall TZs act as layer seven security appliances focused on preventing all types of cyberattacks by offering advanced features such as application control, web filtering, and advanced routing.

SonicWall TZs offer easy installation and configuration, and once it is up and running, it provides simplified and centralized management. Thanks to its cloud-based Capture Advanced Threat Protection (ATP) sandbox service, SonicWall’s NGFWs can detect sophisticated threats such as encrypted attacks.
They add optional features such as PoE/PoE+ and 802.11ac Wi-Fi support, providing unified security for wired and wireless networks.
Some users of the SonicWall TZ NGFWs argue that not all features work as they should or have side effects or undocumented functionality, forcing them to spend a lot of time resolving issues that should be simpler.
However, they point out that they minimize the time required for extensive security policy deployment. Their diagnostic tools (packet capture, packet response, application flow reporting, etc.) make it much easier to troubleshoot security issues.
Barracuda CloudGen
Barracuda CloudGen is the cornerstone of the company’s Total Threat Protection framework. CloudGen UTM offers simplified administration through a web interface and free cloud-based centralized management.
Its core functions include firewall, application control, IPS, antivirus (web, mail, and FTP in proxy or single-pass-through mode), gateway-based URL filtering (also in proxy or single-pass-through mode), SSL interception and inspection, web proxy with caching, unlimited site-to-site and client-to-site virtual private network (VPN), and spam filtering.

Some aspects that distinguish Barracuda’s solution from other similar products are the implementation of SCADA and industrial control protocols, in addition to the Tunnel Independent Network Architecture protocol and CudaLaunch (a cross-platform VPN app for automated deployments on Windows, macOS, iOS, and Android).
Barracuda offers its UTM products as physical appliances ranging from small desktops to large 2U rackable appliances. There are also versions delivered as virtual appliances for VMware, Microsoft Hyper V, KVM, Citrix Zen, Open Xen, and finally, as a cloud service for AWS, Microsoft Azure, and Google Cloud Platform.
Juniper SRX
Juniper’s SRX appliances provide a high-performance network security solution for large-scale ISPs needing advanced routing and security features. It includes all the features of an NGFW, such as deep packet scanning and IPS. Due to its cost and configuration complexity, it is not suitable for smaller companies that do not have specific resources to manage the security of their infrastructures.

The company offers its NGFWs as physical or virtual appliances, both alternatives being suitable to support active or stand-by configurations when they are part of a high-availability infrastructure. Its users highlight its ability to cope with virtually any situation to which it is subjected, from fulfilling basic router functions for branch offices to stateful firewalls capable of monitoring the complete status of active network connections.
To further extend their performance as edge gateways, Juniper SRX UTMs support advanced features of the Border Gateway Protocol (BGP), which enables peering and the exchange of routing information between autonomous systems. As for their administration and configuration tools, the graphical user interface (GUI) is rather basic, while the CLI is very easy to use and much appreciated by users.
Check Point UTM Appliances
Check Point UTM appliances serve small and remote branch office deployments, offering comprehensive threat prevention and high flexibility in terms of both network connectivity and port density. To repel threats, they offer a firewall, IPS, IPsec VPN, antivirus/spam/bots, URL filtering, application control, and email security functionality.
Check Point UTMs’ Threat Prevention technology allows them to “look inside” SSL and TLS tunnels to detect threats even in encrypted transmissions, ensuring that users comply with corporate security policies while surfing the Internet and using corporate data.

To its menu of UTM features, Check Point appliances add a sandboxing scheme called SandBlast Zero-Day Protection, which provides an innovative solution to thwart unknown malware, zero-day attacks, and targeted attacks.
SandBlast uses a new detection technology that operates at the CPU level and can identify threats before the malware deploys its attack. In turn, the SandBlast threat emulation engine monitors the CPU instruction stream for exploits that attempt to bypass the operating system and hardware security controls.
And that concludes this list of the best UTM solutions for your business. It’s also important to know about the distinction between UTM and NGFW, especially if you haven’t used these solutions before.
Basically, over time, UTM solutions evolved to transcend the limits of small companies with small pockets. And large companies began to see them as exciting options to reduce their budgets. This is how the acronym NGFW (next-generation firewall) came about, which is nothing more than a UTM solution but presented as something more adequate for corporate networks.
What is the Difference Between UTM and NGFW?

In practice, there is no substantial difference between a UTM and an NGFW. The technologies used in both are essentially the same. UTM devices are often classified with lower performance ratings than their NGFW counterparts, but for practical purposes, the differences are mainly in the marketing messages.
A set of vendors coined the term NGFW to define a class of products that contained all the features of a UTM but could be inserted into an enterprise network.
The reason for giving these devices a different name was to move away from the belief that a device capable of bringing together all the features of a UTM would never reach the performance standards of enterprise networks. However, as the hardware evolved, the ability of these devices to achieve multi-gigabit speeds began to prove that they were indeed suitable for large enterprises.
A Solution for Every Need
Whether you run a small business with no specialized IT security staff, or you are in charge of protecting a large company’s networks from the many threats that lurk around, the list of UTM products we have compiled here is sure to provide the right choice for your needs.
More On Security
- Best SIEM Tools to Secure Your Organization from Cyberattacks
- Best Data Security Solutions to Safeguard Your Business
- Best Enterprise Password Managers to Protect Your Business Assets
- Best Secret Management Software for Application Security
You can trust Geekflare
At Geekflare, trust and transparency are paramount. Our team of experts, with over 185 years of combined experience in business and technology, tests and reviews software, ensuring our ratings and awards are unbiased and reliable. Learn how we test.

