Vulnerability management software helps you identify, prioritize, and remediate security vulnerabilities in your applications and IT infrastructure across cloud, on-premises, and hybrid environments.
As organizations increasingly rely on IT, they adopt more software, applications, IoT devices, and third-party services. Any unaddressed vulnerability in these assets can lead to data breaches, malware, and other malicious activities.
Implementing vulnerability management software allows your organization to detect and address IT asset vulnerabilities proactively.
Geekflare has researched and compiled a list of the best vulnerability management tools based on key features such as real-time monitoring and alerts, compliance support, customizable reporting and analytics, remediation, and reporting capabilities.
- Tenable Vulnerability Management – Built on Popular Nessus
- ManageEngine Vulnerability Manager – Best for Medium to Large Businesses
- Heimdal – Best To Streamline Patch Management
- Rapid7 InsightVM – Best for Asset Discovery and Risk Analysis
- SecPod SanerNow – Best for Cloud-Based Exposure Management
- Qualys VMDR – Best To Integrate With Qualys Suite of Products
- Fortra Vulnerability Management – Best for Threat Management
- Flexera – Best for IT Asset Risk Management
- Intruder – Best for Small to Medium Businesses
- OpenVAS – Best Open-Source With Commercial Edition
- Acunetix – Best for Web Applications
- Show less
You can trust Geekflare
At Geekflare, trust and transparency are paramount. Our team of experts, with over 185 years of combined experience in business and technology, tests and reviews software, ensuring our ratings and awards are unbiased and reliable. Learn how we test.
Tenable Vulnerability Management
Built on Popular Nessus
Tenable’s Vulnerability Management solution offers complete visibility into your IT environment, allowing you to detect vulnerabilities, identify exploitable exposures, and fix security issues.
Tenable Vulnerability Management solution continuously discovers assets in dynamic environments, such as cloud infrastructures and remote workforces. It then contextualizes vulnerabilities using insights from Tenable Research, enabling prioritized action.
Tenable’s automated prioritization feature enables you to prioritize vulnerability management so that you never miss patching high-risk vulnerabilities. It lets you prioritize asset exposure and monitor remediation trends. You can benchmark progress internally and against your industry standards.
One standout feature of the Tenable Vulnerability Management solution is Tenable AI Aware, a cloud-based vulnerability management solution that helps detect vulnerabilities in AI systems and provides guidance to mitigate these risks. This helps ensure safe AI adoption.
Tenable Vulnerability Management Features
- Continuous asset discovery for known and unknown assets, including dynamic cloud environments.
- End-to-end vulnerability intelligence and exposure-response for effective risk management.
- Prioritization is based on vulnerability context scores.
- SLA-based reporting to track mitigation efforts and align with business objectives.
- Advanced search capabilities for quickly finding vulnerabilities by name or CVE.
Pros
Tenable AI Aware monitors and mitigates risks in AI adoption.
Automated vulnerability rating prioritizes remediation efforts efficiently.
Ensures 99.95% uptime with a service-level agreement (SLA).
Cons
Not a beginner-friendly solution.
Due to high pricing, it is not affordable for small businesses
Tenable Vulnerability Management Pricing
Tenable Vulnerability Management pricing starts at $5,782/year for up to 100 assets. A free trial is available.
ManageEngine Vulnerability Manager Plus
Best for Medium to Large Businesses
ManageEngine Vulnerability Manager Plus is a powerful vulnerability management tool that offers 360-degree visibility into your organization’s security posture. It helps detect and mitigate various vulnerabilities, including OS, third-party applications, and cross-site scripting.
ManageEngine Vulnerability Manager Plus helps detect and resolve security misconfigurations, like default credentials, elevated privileges, firewall issues, directory traversal, expired SSL/TLS, and more. It also quickly identifies high-risk software, including end-of-life, peer-to-peer, and file-sharing applications.
With built-in vulnerability remediation capabilities in ManageEngine Vulnerability Manager Plus, you can easily manage vulnerabilities and meet compliance requirements. A single, centralized console provides full visibility, continuous assessment, and effective threat remediation.
ManageEngine Vulnerability Manager Plus secures endpoints across various environments, including local networks, demilitarized zones (DMZs), and remote locations. It ensures safe working conditions for distributed workforces and provides comprehensive protection regardless of where devices operate. It is available for Windows, Linux, and macOS.
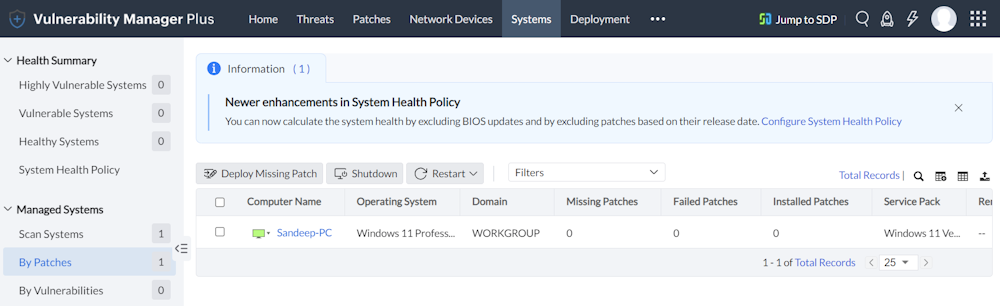
ManageEngine Vulnerability Manager Plus Features
- Assess and prioritize vulnerabilities by exploitability, severity, age, system count, and fix availability.
- Enforce complex passwords, least privileges, and memory protection for system security compliance.
- Identify and resolve web server security flaws for internet-facing devices.
- Detect and remove unauthorized or unsafe software from endpoints quickly.
- Use pre-built scripts to mitigate zero-day vulnerabilities before patches are available.
Pros
Automate patching for Windows, Mac, Linux, and over 500 third-party applications.
Ready-made scripts to protect your network from zero-day vulnerabilities before patches are available.
Comprehensive compliance management support for 75+ CIS benchmarks.
Cons
Occasional false positives.
Patch deployment is not always smooth.
ManageEngine Vulnerability Manager Plus Pricing
ManageEngine Vulnerability Manager Plus pricing starts at $1,195/year for 100 workstations and a single-user license. A free trial is available.
Heimdal
Best To Streamline Patch Management
Heimdal Patch & Asset Management offers vulnerability management by deploying patches to software regardless of location. It provides comprehensive visibility and control over your software inventory, ensuring no critical patches are missed and keeping your software stack fully up-to-date.
Heimdal automated patch deployment lets you update Microsoft, Apple, Linux, and third-party software without manual effort. With its centralized console, you can manage all platforms from one place, simplifying the patch management process and saving time.
With Heimdal, you gain full control over when and how patches are deployed, offering flexibility with custom schedules or fully automated options. This setup minimizes disruptions for your users, whether they work onsite, remotely, or in different locations.
Heimdal Features
- Customize patch schedules to force critical updates, target user groups, and uninstall unstable versions as needed.
- Full automation for hands-free patch management.
- Manage over 200+ third-party applications with automatic patch deployment based on your policies.
- Deploy patches in under 4 hours with pre-tested and secure updates.
- Simplify compliance management with customizable policies, automatic deployment, and audit trails.
- Use efficient P2P distribution to save bandwidth.
Pros
Automatic patch deployment to third parties.
Fastest vendor to end user patch deployment time.
Unified patch management for Windows, MacOS, Linux, and more.
Cons
The focus is on patch management only.
It is difficult to navigate the admin portal.
Heimdal Pricing
Heimdal Patch & Asset Management follows custom pricing based on the number of endpoints in your organization. A free trial is available.
Rapid7 InsightVM
Best for Asset Discovery and Risk Analysis
InsightVM from Rapid7 is a powerful vulnerability management software that offers visibility into your assets in on-prem and cloud environments. It continuously assesses your assets to find vulnerabilities and prioritize them. As a result, you can quickly fix critical vulnerabilities that could harm your business.
Rapid7 InsightVM comes with automation that quickens the vulnerability remediation process. Detailed reports and intuitive dashboards let you check the progress of your remediation efforts. You can also monitor your assets against your industry’s benchmark to comply with regulatory requirements.
Additionally, Rapid7 InsightVM Live Dashboards are interactive and fully customizable. You can create tailored cards and dashboards for any role, from system admins to CISOs. With simple language queries, you can easily track your security program’s progress and gain clear insights into vulnerabilities and remediation efforts.
Rapid7 InsightVM Features
- The Rapid7 Insight Agent collects data from all endpoints, including remote and infrequently connected assets.
- Active Risk scores vulnerabilities on a 1-1000 scale, prioritizing those actively exploited or likely targeted in attacks.
- Goals and SLAs monitor progress, enforce compliance, and support achieving security objectives within set timelines.
- InsightVM’s Threat Feeds deliver real-time threat insights, enabling quick responses to critical vulnerabilities and emerging attacks.
Pros
Live Dashboards provide customizable, interactive tracking for all user roles.
Integrated threat feeds offer real-time threat insights.
Ability to be integrated with Project Sonar to offer attack surface monitoring.
Cons
Memeory consumtion is high.
Scanning is slow.
Rapid7 InsightVM Pricing
Rapid7 InsightVM pricing starts at $2.19/month per asset for up to 250 assets. It offers volume-based discounts. A free trial is available.
SecPod SanerNow
Best for Cloud-Based Exposure Management
SecPod SanerNow is reputed vulnerability management software that finds vulnerabilities in cloud-based and on-premises assets. It leverages its proprietary scanning technology and multi-functional lightweight agent to offer a comprehensive and deep look into your assets and attack surface.
SecPod SanerNow can identify vulnerabilities, exposures, misconfigurations, missing patches, anomalies, and other security issues in less than five minutes. It scans your assets for over 190,000 risk checks.
SanerNow vulnerability management platform offers in-depth details on detected vulnerabilities, including CVSS scores and exploitability levels, helping prioritize risks effectively.
Additionally, it can map vulnerabilities with malware vulnerability enumeration (MVE) data to identify those linked to high-fidelity attacks. This helps your IT teams to prioritize and remediate smartly.
SecPod SanerNow’s integrated and automated patch management supports all major operating systems, including Windows, Linux, and macOS. It can also send patches to 450+ third-party applications.
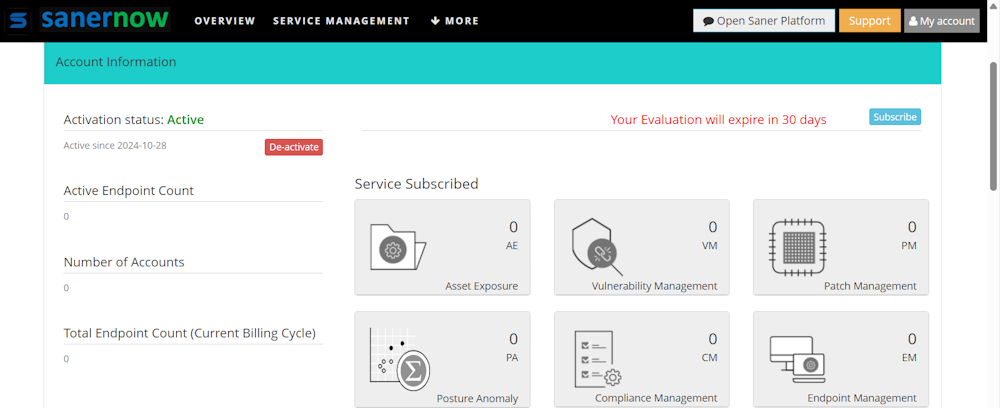
SecPod SanerNow Features
- Discover devices and scan for security risks within 5 minutes.
- Scan for vulnerabilities, exposures, misconfigurations, anomalies, and missing patches.
- Identify dangerous, critical, and exploitable threats.
- Manage risks efficiently through a unified cloud console.
- Generate audit-ready, fully customizable vulnerability reports
Pros
Utilize a built-in Security Content Automation Protocol (SCAP) repository with over 190,000+ checks.
Gain 360-degree visibility into all IT assets.
Fully automated scanning and end-to-end remediation processes.
Cons
Patching is not always smooth on Linux and macOS devices.
Slow performance on low internet bandwidth.
SecPod SanerNow Pricing
SecPod SanerNow follows custom pricing. It also offers a free trial to assess its features.
Qualys VMDR
Best To Integrate With Qualys Suite of Products
Qualys Vulnerability Management, Detection & Response (VMDR) is a powerful tool to manage risks in your hybrid, IT, OT, and IoT environment with deeper visibility into your overall risk posture.
Qualys VMDR can automatically detect and categorize all your assets and create an automated workflow so that you can see every active asset in your hybrid environment. It can detect vulnerabilities and misconfigurations across operation systems, mobile devices, and applications.
Moreover, Qualys VMDR can automatically prioritize the most critical vulnerabilities based on evidence of exploitation and the likelihood of exploitation. It can quickly identify missing patches in on-premises, cloud, and remote endpoints. And you can easily schedule patch deployment.
Qualys Enterprise TrueRisk Platform offers a unified view of your security posture. As a result, you can easily aggregate and measure all security risks in a unified view and understand cyber risks in the context of your business.
Qualys VMDR Features
- Visibility into IT, OT, cloud, on-premises, and IoT assets.
- Transparent risk scoring using Qualys TruRisk will help you prioritize vulnerability remediation.
- Management of End-of-Life (EoL) and End-of-Service (EoS) to avoid unmatchable vulnerabilities.
- Patch automation for all devices across on-premises, cloud, and hybrid environments.
- 25+ threat intelligence feeds and 80k+ signatures to identify current, potential, and confirmed exploitations accurately.
Pros
TruRisk Platform provides a unified view of your cyber risk posture.
Threat intelligence feeds offer valuable insights to improve your security posture.
Easy integration with IT Service Management (ITSM) to close the remediation loop.
Cons
Occasional false positives.
Complex user interface
Qualys Pricing
Qualys didn’t publish any pricing details on its website. A 30-day free trial is available.
Fortra Vulnerability Management
Best for Threat Management
Fortra Vulnerability Management (VM), formerly known as Frontline VM, is a SaaS vulnerability management solution. It uses proprietary scanning technology to find vulnerabilities in your network.
After detecting vulnerabilities, Fortra VM lets you prioritize them and offer remediation information so that you can proactively address security issues. It can also respond based on your pre-set security policies to save time.
Depending on your subscription plan, you can scan monthly, quarterly, or unlimited times. You can also access metadata on larger network clusters, showing their overall risk levels, and overlay threat intelligence for a more precise, more detailed analysis.
Digital Defense’s Network Map lets you visualize your network security quickly, providing a clear overview in highly customizable and interactive graphic visuals. Fortra VM also allows you to take action against clusters or a single asset.
Fortra VM Features
- Security GPA provides a clear grade reflecting your company’s overall security performance.
- A clear metric based on network posture and business risk.
- Prioritize IP devices based on criticality.
- Dedicated Client Advocates provide personalized support.
Pros
Easy integration with SIEM, ServiceNow, Zendesk, and various other tools.
Visualize your network’s security posture with Network Map.
Benchmark your high-risk vulnerabilities against peer organizations for prioritized insights.
Cons
No free trial.
Extensive scanning time even for a few assets.
Fortra VM Pricing
Fortra VM follows custom pricing. Visit the website to get a quote for pricing.
Flexera
Best for IT Asset Risk Management
Flexera Software Vulnerability Manager helps you find, prioritize, and patch vulnerabilities in your organization’s software. It can monitor all applications and systems across all platforms, including on-premises, cloud, and hybrid setups.
Flexera Software Vulnerability Manager leverages AI, machine learning, and human curation to score detected vulnerabilities. As a result, you can quickly prioritize your vulnerability remediation activities. It eliminates the risk of EoL and EoS software vulnerabilities.
Moreover, it also helps you prioritize patch management using its vulnerability and threat intelligence insights. Flexera Software Vulnerability Manager boasts the largest set of third-party patches on the market, so you can deploy patches rapidly. Furthermore, its patch automation option helps you automate the patching process in your organization to save time.
Flexera dashboard provides a clear view of your environment’s vulnerabilities, tracks remediation progress, and offers customizable views for detailed insights.
Flexera Features
- Detects and tracks more applications across all platforms using agent or agentless options with non-intrusive scanning technology.
- Prioritize and automate patching based on your business’s most critical threats.
- Access detailed vulnerability insights and a large patch repository for quick, effective action.
- Streamline detection and patching processes to maintain control and improve your security posture.
- Organize systems based on policies, devices, or advisories for quicker responses from the right teams.
Pros
Having the largest set of third-party patches to deliver patches rapidly.
Smart Grouping feature for quick responses.
Secunia Research ratings offer detailed insights on vulnerabilities for faster remediation.
Cons
The platform occasionally has response delays, and some patches may still appear faulty after being fixed.
No benchmarketing against your industry.
Flexera Pricing
Flexera follows custom pricing. There is no free trial, but you can book a demo to dive into its features.
Intruder
Best for Small to Medium Businesses
Intruder offers continuous vulnerability scanning of assets in your IT environment. It leverages internal, external, and application vulnerability scanning for constant vulnerability management.
Intruder can scan your IT environment for 1,40,000 infrastructure issues and 75+ application vulnerabilities. Once it discovers security vulnerabilities, it reviews them and prioritizes them by severity. Consequently, you can quickly start working on fixing crucial vulnerabilities.
With Intruder, you can also scan APIs and pages behind authentication. The Cyber Hygiene Score lets you understand how your vulnerability remediation efforts are performing compared to your industry’s.
Intruder kicks in automated scanning only once there is any change in your network to avoid a barrage of notifications. It is a cloud-based solution that can alert you through emails, Slack, and Teams.
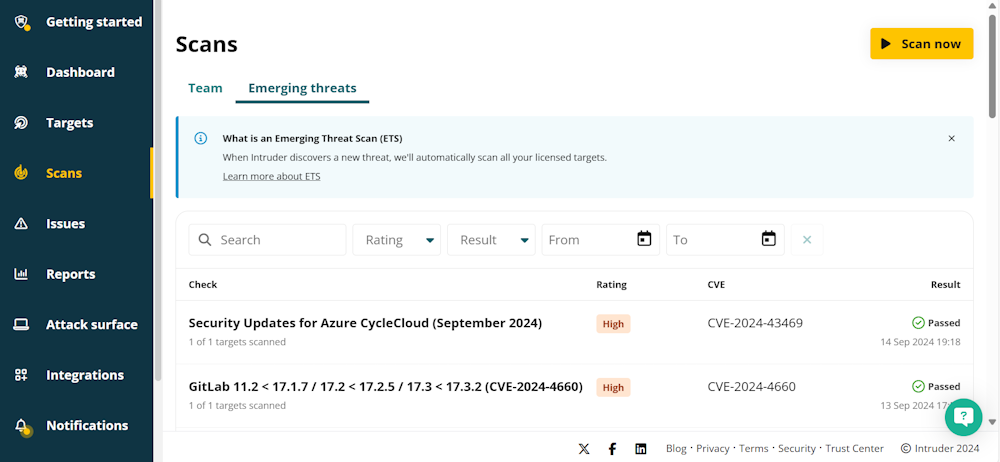
Intruder Features
- Quick setup in 10 minutes.
- One platform to scan applications, APIs, and infrastructures.
- Easy integration with Google Cloud Platform, AWS, and Azure to scan newly deployed services continuously.
- Various scanning options include Emerging threat scans, Network scans, and New Service scans.
- 24/7 automated scanning for new threats.
Pros
Cyber Hygiene Score to track the progress of your remediation efforts against your industry.
Easy integration with compliance platforms, such as Drata and Vanta.
Rapid Response feature to check for proactive defense against emerging threats.
Cons
Reporting could have more details about vulnerability management.
Scanning is slow sometimes.
Intruder Pricing
Intruder pricing starts at $172/month for one application and one infrastructure. It offers a 14-day free trial.
OpenVAS
Best Open-Source With Commercial Edition
OpenVAS is an open-source vulnerability scanning and management tool. It helps you find a wide range of vulnerabilities, such as outdated software, misconfigurations, weak passwords, and more. It supports more than 26,000 common vulnerabilities and exposures (CVE).
OpenVAS has various capabilities, including authenticated and unauthenticated testing, performance tuning, and the flexibility to implement any type of vulnerability test. It also allows you to create custom scans, depending on your requirements.
OpenVAS is designed for security researchers, so it is relatively challenging for normal users to configure it properly. The open-source version is community-supported, so if you’re stuck, you will have to rely on the community for support. The enterprise version comes with full support from Greenbone.
OpenVAS Features
- Comprehensive vulnerability scanning.
- False positive management.
- Remediation guidance.
- Configuration monitoring.
- Compliance auditing.
Pros
Regularly updated feeds for accurate vulnerability detection.
Offers an open-source solution for vulnerability scanning, making it accessible to many users.
Integrates well with Greenbone Security Manager for comprehensive vulnerability management.
Cons
Steep learning curve.
Outdated user interface.
OpenVAS Pricing
The OpenVAS community edition is free.
Acunetix
Best for Web Applications
Acuentix is powerful vulnerability management software that helps you detect and mitigate vulnerabilities in web applications. It can detect thousands of vulnerabilities and misconfigurations.
In addition to offering scan results with remediation advice, Acuentix comes with a host of vulnerability management tools. For example, it can automatically catalog vulnerabilities and give them the status “Open.” It also verifies after you fix vulnerabilities and automatically marks them fixed if the vulnerabilities are successfully fixed.
Acuentix lets you quickly generate technical, regulatory, and compliance reports, such as HIPAA, PCI-DSS, and OWASP Top 10. Moreover, you can export vulnerability data to GitHub, Jira, GitLab, Mantis, and various other issue trackers.
Acuentix’s proof of exploit features eliminate false positives and pinpoint the exact location of vulnerabilities. It is available as a cloud and on-premises solution and supports role-based access.
Acuentix Features
- Discovers all websites, applications, and APIs and crawls even complex and single-page apps.
- Detect over 12,000+ vulnerabilities, including zero-days, with fast, accurate scans.
- Pinpoint exact code issues.
- Integrate directly with developer tools, enabling seamless vulnerability management within CI/CD pipelines.
- Automate scheduled scans to maintain continuous security.
Pros
Predictive Risk Scoring to get an idea of your risk levels.
Blended DAST + IAST scanning for better coverage.
Proprietary AI\ML-driven Predictive Risk Scoring to assess risk levels.
Cons
Customer support could have been quicker.
Occasional false positives.
Acuentix Pricing
You need to contact the company to get a price quote. It offers a free demo.
Why Is Vulnerability Management Software Needed?
Vulnerability management software is needed to help you find, prioritize, and mitigate vulnerabilities in your applications and IT infrastructures.
With the rise of cyberattacks, even a minor vulnerability can lead to data breaches, malware infections, and financial and reputational losses. By continuously scanning your applications and IT environments, vulnerability management software can help mitigate security risks proactively. Moreover, it can also aid in meeting regularity requirements.
If you want full visibility into your attack surface, you can explore these attack surface management tools.
Steps of the Vulnerability Management Lifecycle
The Vulnerability Management Lifecycle is a continuous process that helps organizations identify, assess, and address security risks across their IT assets.
Here are the key steps of the Vulnerability Management Lifecycle.
- Asset Discovery: Identify and inventory all assets across your IT environment.
- Vulnerability Scanning: Regularly scan assets to detect vulnerabilities.
- Vulnerability Assessment: Analyze and prioritize vulnerabilities based on severity, exploitability, and business impact.
- Reporting and Prioritization: Generate reports and prioritize vulnerabilities for remediation.
- Remediation: Apply patches or fixes to address prioritized vulnerabilities.
- Verification: Confirm that remediation efforts effectively resolved the vulnerabilities.
- Continuous Monitoring: Continuously monitor and re-scan assets to identify new vulnerabilities.
Key Features of a Vulnerability Management Software
You can choose vulnerability management software based on the security requirements and features they provide. We have compiled a list of the most important features to help you select the best vulnerability management software.
Asset Discovery and Inventory
Asset discovery and inventory provide a comprehensive overview of all assets in your IT environment, including cloud, on-premises, and hybrid setups. This feature continuously scans for new devices, applications, and endpoints to ensure every asset is accounted for.
Automated Vulnerability Scanning
In addition to allowing you to run on-demand scans and schedule scans, good vulnerability management solutions come with automated scanning.
Automated vulnerability scanning checks applications, systems, and network devices for known security flaws. This feature scans for missing patches, outdated software, misconfigurations, and other vulnerabilities without manual intervention.
Risk-Based Prioritization
Risk-based prioritization ranks vulnerabilities based on factors such as severity, exploitability, and potential business impact. Instead of focusing solely on the number of vulnerabilities, this feature helps security teams address the most critical risks first, reducing the likelihood of high-impact breaches.
Patch Management Integration
Patch management integration is an important feature of vulnerability management solutions. Most reputable solutions can automatically deploy relevant patches. The patch management feature supports all leading operating systems and third-party solutions.
Real-Time Monitoring and Alerts
Real-time monitoring and alerts notify security team members whenever new vulnerabilities or suspicious activities are detected so that they can take proactive steps to address security issues. A reputable vulnerability management tool offers multiple notification methods, such as email, Slack, Teams, and more.
Reporting and Analytics
Reporting and analytics provide comprehensive insights into vulnerabilities, remediation progress, and your overall security posture. This feature offers visual data and trend analysis, helping you assess risk levels and track improvements over time.
Effective reporting gives you a 360-degree view of asset security, including detailed information on identified vulnerabilities. Typical reports cover the following:
- Total scans completed
- Number of vulnerabilities detected
- Recommended remediation actions
- System security summary
- Issues categorized by asset
- Issues categorized by vulnerability
- Suggested steps for remediation
Remediation Tracking
Remediation tracking keeps tabs on the progress of addressing each vulnerability to ensure it is resolved effectively. This feature logs actions taken, verifies that patches or fixes have been applied, and confirms that vulnerabilities are no longer exploitable.
Compliance Management
The compliance management feature of vulnerability management software helps you meet various regulatory compliances, such as HIPAA or PCI-DSS, through systematic identification, assessment, and remediation of vulnerabilities. Good vulnerability management software can also generate various compliance and regulatory reports.
Threat Intelligence Integration
Threat intelligence integration helps vulnerability management software detect emerging threats, new vulnerabilities, and attacker methods. Real-time threat data improves risk assessment and prioritization.
User Access Controls
Most reputable vulnerability management solutions include user access controls that allow you to restrict access to sensitive data. This feature ensures that only authorized people can view or modify vulnerability data.
Explore More Security Solutions
-
 EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.
EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.


