Phishing emails consistently inflict significant harm on internet users. Let’s check out how to steer clear.
The term “Phishing” originated in the 1990s, combining “fishing” and “phreak” (meaning a hack or hacker). Literally, phishing refers to scammers attempting to “fish” sensitive information from individuals using online baits, such as links in emails or SMS.
Typically, hackers aim for login credentials for online banking, social media profiles, etc., but installing malware can also be a primary objective. In the latter case, the idea is to lay future traps with spyware, scareware, or ransomware.
And these aren’t isolated incidents. According to these statistics, 90% of data breaches result from phishing attacks. Besides, roughly 92% of malware is delivered via emails, making this form of online communication a scammer-favourite.
In essence, the issue is more significant than we may realize, and it’s often just a matter of time before someone falls victim to these online frauds.
For the better, this article shares how to detect phishing emails and a few helpful tools to make our emails safe.
Detecting Phishing Emails
#1. Check Sender
The first step is to check the sender’s name. But more importantly, one should take note of the domain name.
For instance, this email address is our own, and I can say that because of the domain name (@geekflare.com).
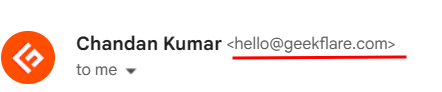
Quite often, users see the name but hastily forget to verify the original source of communication. They think it’s from someone they know, giving out personal information to the bad actors.
#2. Verify Links
Phishing emails are mostly harmless if you don’t click anything from their contents, including the attachments.
In addition, advanced antivirus software or email services may alert about fraudulent links the email might have.
For instance, I get this warning from my antivirus software about any potential hazard:
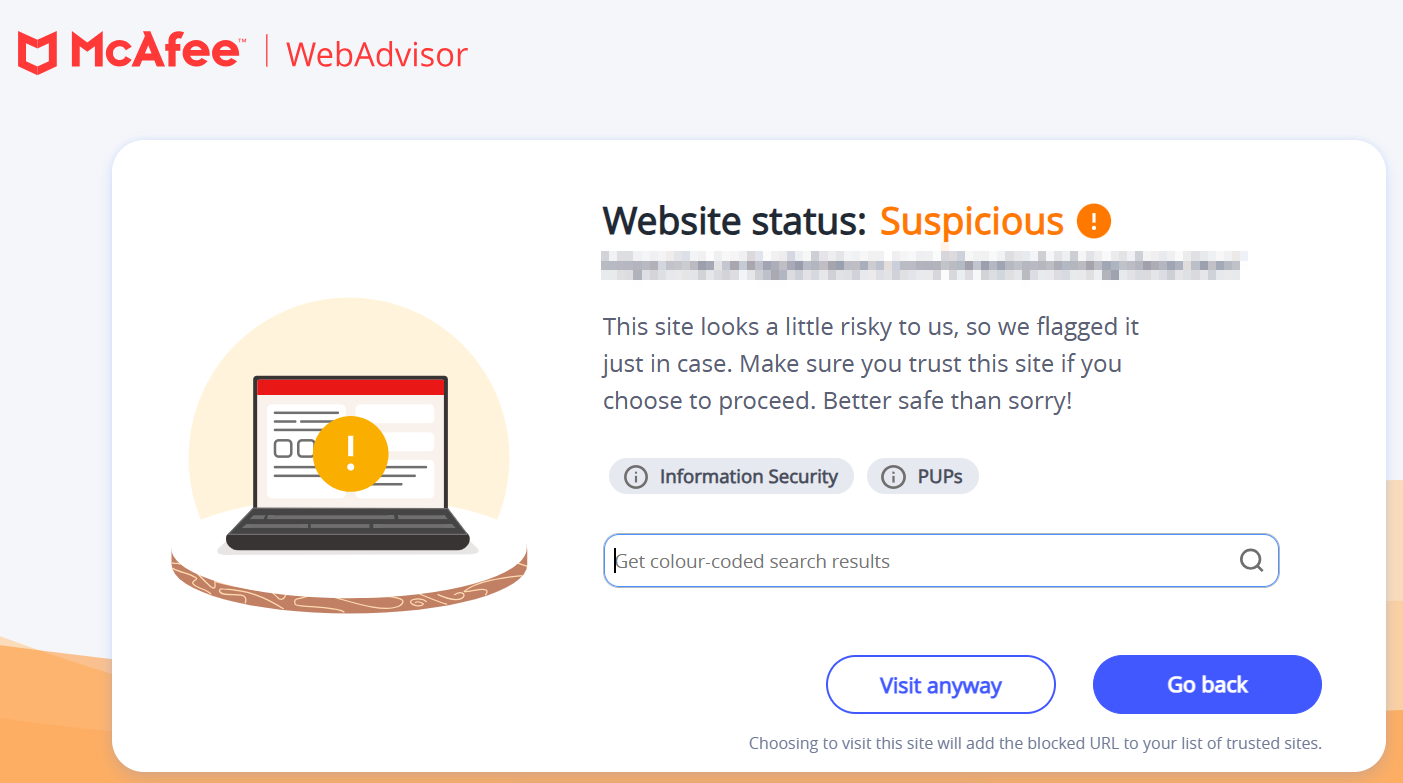
But the problem with such tools is an abundance of false positives. In that case, one can also copy-paste the link in any search engine, like Google search, to get an idea about the sender’s intent.
Another indicator of secure links is that they start with https:// and not http://. But one should note that though https indicates a safe connection, it doesn’t always point toward a legitimate, non-phishing website.
One should also verify the misspellings as similar-looking versions give added benefit to the hackers.
Another clever trick played over innocent people is using URL shorteners like Bitly. In such a case, one can paste the links in URL expanders, such as CheckshortURL, to peek over the actual destination.
One can also try to contact the sender via other communication channels to verify the email’s authenticity.
#3. Language
Despite the sophistication of phishing attacks, grammar seems to be their perennial weakness. Common giveaways of phishing emails are generalized salutations (e.x., Dear user) or a message body depicting poor language structuring.
The email may lack professionalism or talk in an overtly personal tone. Or, it can simply request sensitive information nonchalantly. Besides, such emails often try to impart a sense of urgency, pushing the user to click without giving time for rational thinking.
Overall, this isn’t something we can define in black and white, and the onus is on the reader to look for any red flags.
#4. Attachments
Phishing emails can have attachments that, upon clicking, can run malicious scripts on your device to install malware, including ransomware, spyware, etc. Also, such harmful programs can alter the DNS cache, taking you to malicious replicas of genuine websites even after entering the correct web address.
Powerful antivirus software plays guardian in such situations. In addition, built-in security features can scan the files and alert the user against opening them.
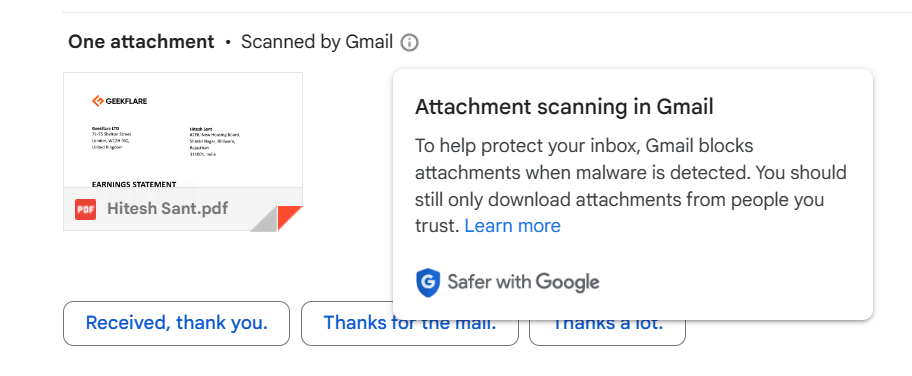
The rule of thumb here is not opening the embedded files until you are completely sure about the outcomes. So, these were a few warning signs.
Below are a few tools that can help detect phishing emails based on the level of AI integration, advanced email and URL analysis and ease of deployment.
- 1. PhishTitan
- 2. CheckPhish
- 3. isitphish
- 4. OPSWAT
- 5. Email Veritas
PhishTitan
PhishTitan, developed by TitanHQ, offers cutting-edge anti-phishing protection. This AI driven solution, is tailored for companies using Microsoft 365, with a setup time of under 10 minutes. PhishTitan uses advanced layers of analysis and machine learning (ML) models to detect phishing emails and provide cutting-edge defense against sophisticated phishing threats.
PhishTitan ensures unparalleled accuracy in anti-phishing measures while minimizing false positives. It provides advanced security by thwarting zero-day attacks through email analysis and time-of-click techniques using AI, curated threat intelligence, and user input.

PhishTitan’s swift deployment and centralized management streamline operations, enabling administrators to secure multiple inboxes effortlessly from a single interface.
PhishTitan Features
- AI & LLM Driven Analysis – PhishTitan employs layers of analysis and machine learning (ML) models to detect phishing emails. Curated feeds identify malicious URLs.
- Auto Remediation – Post Delivery Remediation allows MSPs to swiftly eliminate threats from users’ inboxes, promptly removing malicious mail that has already been delivered.
- URL Rewriting – PhishTitan rewrites URLs to ensure Link Lock protection. It inspects and rewrites all URLs to detect links to malicious sites, ensuring safety.
- Advanced M365 Security – Integrated with M365, it scans all emails (internal and external), augmenting EOP and MS Defender for unbeatable phishing protection.
- Stop Business Email Compromise (BEC) – Through real-time analysis and threat assessment, PhishTitan neutralizes Business Email Compromise (BEC) and spear-phishing scams before they begin.
CheckPhish

CheckPhish is a free URL and website scanner built for Microsoft Outlook. This is an AI-powered tool that identifies visuals and text to see if there is anything dubious in the incoming mail.
Behind the scenes, every submitted URL is sent via a headless browser to capture crucial information such as a live screenshot, webpage language, DOM, WHOIS, etc. Next, this information is sent to multiple deep-learning models to check for brand logos, sign-in forms, and intent.
This helps analyze and alert in case of various phishing scam categories, such as tech support scams, pharmacy scams, gift card scams, illegal streaming sites, cryptojacking, and more.
CheckPhish also informs if your email has been exposed to data breaches. Finally, you’ll have data about all the historical scans in its dashboard.
Besides this scanner, CheckPhish also offers an anti-phishing API for advanced use cases.
isitphish
Made for developers, isitphish helps you keep your users safe from phishing attacks, including those disguised as emails, messages, or any other form of digital communication.
Based on machine learning, isitphish claims to have 97% accuracy. One can leverage their Python API client to integrate this anti-phishing tool into their products.
It’s based on AWS infrastructure, ensuring you get excellent uptimes.
One can try isitphish with its entry-level plan, offering 1000 calls per month. The good thing is that the tech support isn’t limited to paid subscriptions. Besides, every plan can make 1000 simultaneous queries, including the free forever tier.
OPSWAT

OPSWAT’s MetaDefender Email Gateway Security is powered with advanced heuristic predictive methods and machine learning algorithms to provide excellent anti-phishing and anti-spam abilities.
Every incoming mail is passed through a series of checks, including multiple blacklists and content filters, before landing in the user inbox. This helps OPSWAT defend the user against phishing attempts, social engineering, blackmail scams, and more.
In addition to IP, domain, and URL reputation checks, OPSWAT deploys time-of-click URL analysis. It sends the hyperlink clicks through the MetaDefender Cloud for additional reputation checks against 30+ online resources.
Overall, the idea is to rely on user awareness and leverage multiple protocols to keep the user inbox safe and clean.
Email Veritas
Email Veritas (or eVeritas) combines natural language processing, AI, and stylometry analysis to fight against dangers like spear phishing, business email compromise, malvertising, etc.
It has browser add-ons to color code different emails based on the level of threat detection. Besides, Email Veritas has add-ons for Google Workspace and Microsoft Outlook, which come with native API integration. Also, one can benefit from its Secure Email Gateway to protect any cloud-first IT infrastructure against incoming threats and data loss.
eVeritas has multiple security solutions, including Phishing Detector, Phishing Simulator, and URL checker API.
Awareness & Technology!
Usually, people are asked to watch out for online phishing threats. However, the sheer volume of these attacks means it’s easy to become a victim.
This is precisely where technology comes into the picture. A tech-aware individual added with anti-phishing tools has the best chance of survival in this evolving online threatscape.
More on Phishing & Security
-
 EditorRashmi Sharma is an editor at Geekflare. She is passionate about researching business resources and has an interest in data analysis.
EditorRashmi Sharma is an editor at Geekflare. She is passionate about researching business resources and has an interest in data analysis.


