SQL Injection is a cyberattack that allows hackers to insert malicious SQL code into an input database query to manipulate a web application or website database, potentially leading to unauthorized access and data theft.
Hackers use three main tactics – In-band, Inferential, and Out-of-band SQL Injection – to exploit vulnerabilities in web applications and gain unauthorized access to sensitive information stored in the website’s SQL database.
Identifying SQL injection vulnerabilities can be done through manual and automated testing. These processes include checking error messages, reviewing input validation procedures, etc, to identify any potential vulnerabilities.
Geekflare has researched and compiled a list of the best SQLi vulnerability scanners based on key features such as ease of use, pricing, and detection accuracy.
- suIP.biz
- SQLMap
- Pentest Tools SQL Injection Scanner
- InsightAppSec
- Acunetix
- Probely
- Wapiti
- Intruder SQL Injection Scanner
- Detectify
- Show less
suIP.biz
suIP.biz is a popular SQL injection scanner that supports all leading database management systems. It can help find SQLi vulnerabilities in various databases such as Microsoft SQL Server, Oracle, MySQL, and PostgreSQL.
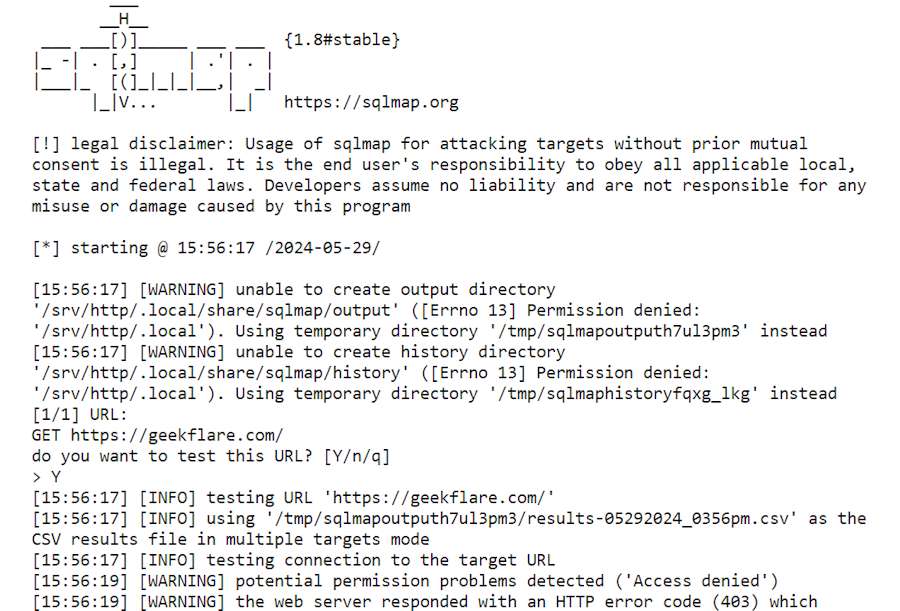
suIP.biz supports all the common SQL injection techniques, including time-based blind, boolean-based, error-based, out-of-band, stacked queries, and union query-based.
To generate an SQL vulnerabilities report, you just have to paste your URL and click the submit button. Super IP is a free tool.
SQLMap
SQLMap is an open-source tool that helps you discover SQL injection vulnerabilities, exploit them, and take over database servers. It covers common SQL injection techniques, including out-of-band, boolean-based blind, time-based blind, error-based, stacked queries, and union query-based.
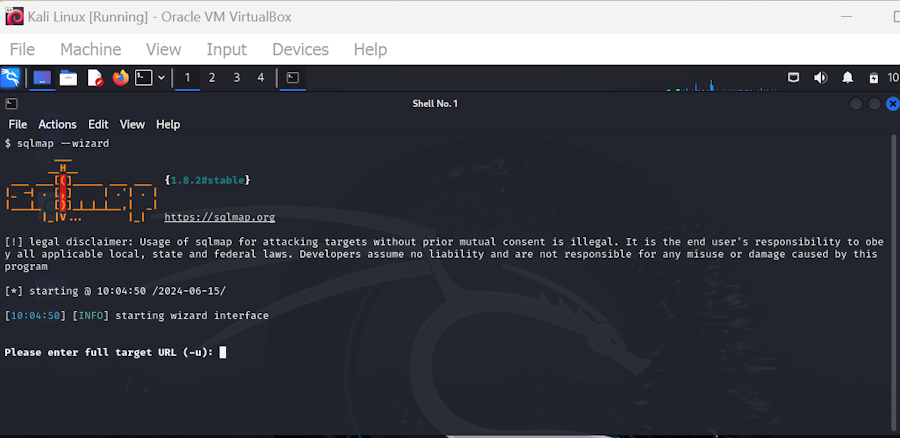
SQLMap allows you to enumerate users, privileges, roles, password hashes, databases, tables, and columns. Additionally, it can identify various password hash formats automatically and help you carry out dictionary-based attacks to crack passwords.
SQLMap is a free tool, and you can download it from Git. Its powerful detention engine supports all leading database management systems, including MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, and more.
Pentest Tools SQL Injection Scanner
Pentest Tools’ SQL Injection Scanner is powered by its proprietary scan engine. It crawls and performs a deep inspection of your application’s web pages and parameters to discover vulnerabilities.
A good thing about Pentest Tools’ SQL Injection Scanner is that it makes reading vulnerability reports easier. You will receive detailed information on findings, risks associated with each finding, and recommended steps to fix these vulnerabilities.
Pentest Tools’ SQL Injection Scanner allows you to see visual representations of risk ratings. This feature helps you prioritize tasks in vulnerability management.
Pentest Tools’ SQL Injection Scanner offers the following plans:
| Plan | Key Features | Monthly Pricing |
|---|---|---|
| Free | Light tools exclusively, Two-factor authentication | Free |
| Basic | Simple reporting, Automation capabilities, Multiple workspaces | $85 |
| Advanced | Advanced reporting, Scanning internal networks, Scan behind login | $190 |
InsightAppSec
InsightAppSec is a black-box security scanner that automatically discovers vulnerabilities in web apps and APIs. With fewer false positives, it can test your web app for over 95 attack types, including SQL injection, XSS, CSRF, and more.
InsightAppSec’s Universal Translator can normalize traffic from different formats, protocols, and modern development technologies. As a result, it can efficiently attack your web app to discover vulnerabilities regardless of the technology your app uses.

InsightAppSec supports 95 attack types, and you can export findings in CSV, PDF, and interactive HTML formats. What’s more, it can help you identify your application security compliance risk by customizing your reports to various regulations, including SOX, HIPAA, PCI-DSS, and OWASP Top 10.
InsightAppSec offers cloud and on-prem scan engines with automated scheduling and blackouts, starting at $175 per month per app and a 30-day free trial.
Acunetix
Acunetix is a powerful SQL injection scanner that can test your web application for advanced injection techniques, such as classic, blind, and out-of-band SQL injections.
Acunetix detects 7000+ web vulnerabilities. In addition to SQL injections, it can scan your web application for various other vulnerabilities, including, but not limited to, various types of cross-site scripting attacks, cross-site request forgery attacks, directory traversal attacks, and more.

Acunetix also analyzes your web server’s security configurations, sending notifications about misconfigurations, weak passwords, or missing content security policies (CSP). This feature enhances your web server’s security.
Additionally, Acunetix can work as a vulnerability assessment tool. It classifies identified vulnerabilities and reports them with details about possible security implications and fixes.
Acunetix is available as an on-premises and cloud-based service. The on-premises service is available for Linux, Windows, and macOS. It has built-in compliance reports for various security audits, such as HIPAA and PCI DSS.
Acunetix follows a custom pricing plan. You need to contact the company to get the cost estimation for your requirements.
Probely
Probely is a comprehensive discovery and vulnerability scanning tool. It creates an inventory of your web assets, including web apps and APIs, and scans vulnerabilities by scanning the entire external attack surface.

With Probely, you can detect around 3000 types of vulnerabilities, including SQL injections and XSS. Its headless chrome-based spider can crawl Single-page Applications and rich JavaScript apps with the same ease to offer you maximum coverage.
Probely offers a detailed report of the findings, including tips for fixing vulnerabilities. It allows you to automate security testing efficiently by integrating it with your software development lifecycle.
Probely is a web-based vulnerability scanner and comes with three pricing plans:
| Plan | Key Features | Monthly Pricing |
|---|---|---|
| Lite | Partial and incremental scans, Web and API scanning | Free |
| Pro | Built-in roles and permissions, Compliance reports, Agent to scan internal targets | $98 |
| Enterprise | Single-Sign-On (SSO), Dedicated account manager, Custom scanning profiles, Custom roles and permissions | $665 |
Wapiti
Wapiti is a command-line web security scanner that performs black-box scans to find vulnerabilities in web applications. It crawls the web pages of a deployed application and creates a list of URLs, forms, and their inputs. Then, it tries to inject payloads to find out the vulnerable scripts.
Wapiti can scan your web application for multiple SQL attack techniques, including time-based, boolean-based, and error-based.
In addition to SQL vulnerabilities, Wapiti can scan your application for various other vulnerabilities, such as XML eXternal entity (XXE) injection, detection of subdomain takeover vulnerabilities, cross-site request forgery (CSRF) basic detection, carriage return, line feed (CRLF) Injection, and more.
Wapiti is free to use. It can generate reports in HTML, CSV, XML, TXT, and JSON.
Intruder SQL Injection Scanner
Intruder SQL Injection Scanner is an automated scanner that employs leading scanners, including OpenVAS, Tenable Nessus, and Nuclei to find vulnerabilities.
You can use it to scan single-page and multi-page applications. What’s more, Intruder SQL Injection Scanner allows you to scan behind-login pages easily by adding authentication. It can identify SQL injection vulnerabilities and 75+ other security issues found in web applications.

You can also easily integrate Intruder SQL Injection Scanner with your DevOps process, enabling you to ensure security throughout the software development lifecycle. To make collaboration easier, you can integrate it with GitHub, Azure DevOps, GitLab, Jira, and ServiceNow.
Intruder offers three SQL injection scanner plans—Essential, Pro, and Premium—each priced based on the number of applications and infrastructures to scan. Its Pro Plan comes with a free 14-day trial. To get information about how much you need to pay, you have to submit details on how many applications you want to scan and how many infrastructures you wish to target.
Detectify
Detectify is a powerful web application security scanner that can scan a wide range of security vulnerabilities, including SQL injections, SSL and encryption misconfigurations, input sanitation problems, vulnerabilities behind authentication, and more.
Detectify makes vulnerability management easier by offering a complete overview of all security issues and expert tips for fixing them. The filter and tag findings feature also helps you prioritize vulnerabilities.
Another good feature of Detectify is that it performs extended fingerprinting of your application, allowing it to scan your app thoroughly without running irrelevant tests. Its crawler can scan single-page applications and JavaScript-heavy applications equally.
Detectify offers two pricing models: the Full EASM solution and the Small Attack Surface. The price of the Full EASM solution plan depends on the number of domains, subdomains, and applications in your attack surface.
Detectify offers two plans: Surface monitoring at €275 and Application Scanning at €82 monthly.
What Is SQL Injection?
SQL injection is a cyberattack where a threat actor injects a malicious SQL command into a database query to execute harmful code on your web application server.
SQL injections often happen when your web application includes user-generated inputs in SQL queries without proper validation or sanitization.
Needless to say, SQL injection attacks are one of the most common web application injection attacks. Hackers target websites with SQL injection vulnerabilities, which allow them to manipulate data in the database, impersonate user identities, and potentially execute commands on the operating system.
Example of SQL Injection Attack
Suppose you have a web application with a login form where users enter their username and password. The application takes the user input and constructs an SQL query to check if the provided credentials are valid.
Let’s say the application’s SQL query looks like this:
SELECT * FROM users WHERE username = 'inputUsername' AND password = 'inputPassword';Now, imagine a malicious user enters the following input in the username field:
admin' --And leaves the password field empty. The application will construct the SQL query by inserting the user input directly into the query string:
SELECT * FROM users WHERE username = 'admin' -- AND password = '';Let’s break down what happens here:
- The single quote
'afteradmincloses the username string. - The space after the single quote is used to separate SQL statements.
- The double hyphens
--indicate the start of a comment in SQL, which means the rest of the line will be ignored.
So, the actual SQL query that gets executed becomes:
SELECT * FROM users WHERE username = 'admin' --The -- comment effectively nullifies the password check, and the query now only checks for the username admin.
If there is a user with the username “admin” in the database, the query will return that user’s record, and the attacker will gain access without knowing the actual password.
The attacker can even take it further and input something like:
' OR 1=1--The resulting SQL query becomes:
SELECT * FROM users WHERE username = '' OR 1=1--In this case, the OR 1=1 condition is always true, so the query will return all records from the “users” table, potentially exposing sensitive information of all users.
This example demonstrates how an attacker can manipulate the SQL query by injecting malicious input, bypassing authentication, and gaining unauthorized access to the database.
Also Read: Frequently Asked SQL Interview Questions and Answers
Types of SQL Injection Attacks
There are three main ways to classify SQL injection attacks based on the injection patterns.
1. In-Band SQL Injection
It is one of the most common forms of SQL injection. In this type of attack, a threat actor utilizes the same communication channel to execute an SQL injection attack and retrieve results.
Here are two types of in-band SQL injection attacks that are widely prevalent.
- Error-Based SQL Injection: Error-based SQL injection exploits database error messages to gather information. Attackers deliberately use incorrect syntax to cause errors that may reveal the database structure and other details.
- Union-Based SQL Injection: Union-based SQL injection utilizes the UNION SQL operator to merge the results of multiple SQL queries to get a single result. This helps the attacker retrieve data from different tables within the database.
2. Inferential SQL Injection
Inferential SQL, also known as injectionBlind SQL injection, does not directly reveal the result of an injected query in the application’s response. Instead, the attacker infers information based on the application’s behavior or error messages to the attacker’s payload.
Here are two subdivisions of inferential SQL injections.
- Boolean-Based Attack: In a Boolean-based SQL injection attack, the attacker sends a query to the application’s database and analyzes the variations in response to determine if the injected query is true or false. This allows the attacker to gather information about the database without directly seeing the query result in the response.
- Time-Based Attack: Time-based Inferential SQL Injection involves injecting SQL queries that cause the application to delay its response. Attackers can infer information based on the delay in the application’s response, allowing them to extract data from the database without directly viewing the results.
3. Out-Band SQL Injection
Out-of-band SQL Injection is an advanced technique in which the attacker uses a different communication channel to extract data from the database instead of relying on the application’s response. This is particularly useful when the application is not able to return data directly due to security measures.
For example, instead of retrieving data directly in the HTTP response, the attacker could inject a query that causes the database server to perform an action that can be observed externally. For instance, the attacker could inject a query that makes the database server send an email containing the desired data.
Preventing SQL Injection Attacks
Here are some ways to prevent SQL injection attacks.
- Input Validation: Input validation is a process of analyzing user inputs and disallowing ones that don’t meet specific criteria. It is the first step toward securing your application from SQL injection attacks.
- Error Handling: Effective error handling is a must in mitigating error-based SQL injection attacks. Make sure that your web application doesn’t reveal sensitive information about the database or query syntax in error messages.
- Implement Prepared Statements: Parameterized queries or prepared statements are effective ways to fortify your defense against SQL injection attacks. They help separate the SQL query logic from user input, ensuring that user-supplied data is never treated as executable code.
- Use Stored Procedures: Stored procedures are sets of SQL statements stored in a database. SQL statements can be executed repeatedly by calling the procedures, preventing hackers from executing malicious commands on the database.
- Use Third-Party Security Tools: Third-party security tools like Cloudflare WAF or SUCURI effectively enhance application security and mitigate malicious attempts.
Additionally, you should do proactive database monitoring to discover any security issues before they can do any harm.
Frequently Asked Questions
The most common cause of SQL injection vulnerabilities is when a web application fails to validate and sanitize user-supplied data before incorporating it into SQL queries.
No, automated tools cannot detect all types of SQL injection vulnerabilities, especially if a web application has customized input validation and sanitization. Combining manual testing with automated testing is the most effective way to identify all potential SQLi vulnerabilities.
The frequency of testing for SQL injection vulnerabilities in web applications depends on factors like complexity, code change rate, and data criticality. However, regular testing is important to prevent hackers from exploiting SQLi vulnerabilities.
It is recommended to integrate security testing into CI/CD pipelines and conduct scheduled scans with automated tools at least weekly, especially after significant updates.
To secure databases against SQL injection attacks, use prepared statements or stored procedures, validate input with allow-lists, and minimize application and OS privileges.
You should also implement least privilege and avoid escaping all user-supplied input to prevent SQL injection attacks. Using third-party applications such as Securi is a must to enhance your application security.
Read More About Attacks
-
 EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.
EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.


