Cyber attacks like data breaches and malware are common nowadays. Digital forensics helps experts find out what happened, how it happened, and how to stop it from happening again.
There are many commercial forensic tools available, but they can be very expensive. Luckily, there are also free and open-source tools that work well. These tools can handle important tasks like network traffic inspection, analyzing digital evidence, log review, extracting metadata, tracing user activity, malware analysis, and identifying unauthorized access.
In this article, we have researched and tested the best free forensic investigation tools trusted by security professionals to investigate incidents and recover evidence.
- 1. Autopsy
- 2. Kit Forensic
- 3. Wireshark
- 4. NetworkMiner
- 5. Forensic Investigator
- 6. FAW
- 7. CrowdStrike
- 8. Kali Linux
- 9. Elcomsoft Forensic Disk Decryptor
- 10. Paladin Forensic Suite
- 11. Mobile Verification Toolkit(MVT)
- 12. Passcape’s Windows Media Forensics
- 13. CredentialsFileView
- 14. SIFT
- 15. Foxton Forensics
- 16. Hashcat
- 17. John the Ripper password cracker
- Show less
You can trust Geekflare
At Geekflare, trust and transparency are paramount. Our team of experts, with over 185 years of combined experience in business and technology, tests and reviews software, ensuring our ratings and awards are unbiased and reliable. Learn how we test.
1. Autopsy
Autopsy is a GUI-based open-source digital forensic program that analyzes hard drives and smartphones efficiently. It is widely used by law enforcement, corporate investigators, and cybersecurity professionals for incident response and forensic analysis.
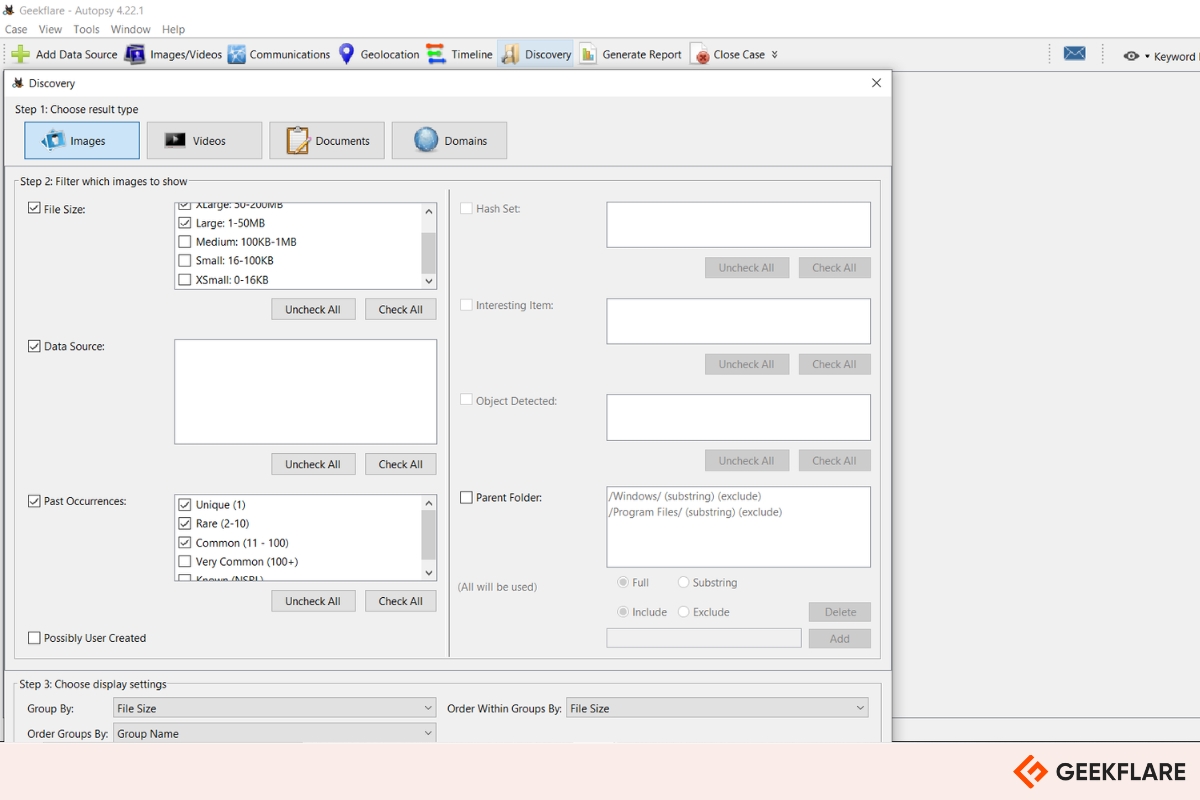
Key features include:
- Email analysis to inspect message content and metadata
- File type detection for identifying and categorizing files
- Windows registry analysis to uncover user activity and settings
- Photo recovery from memory cards and other storage devices
- Geolocation & camera data extraction from JPEG images
- Web browser artifact extraction for tracking user online behavior
- System event visualization through a graphical timeline interface
- Timeline analysis to reconstruct the sequence of events
- Android data extraction, including SMS, call logs, and contacts
Autopsy also supports customizable reporting in formats like HTML and XLS, making forensic findings easy to document and share.
2. Passware Kit Forensic
Passware Kit Forensic is a trusted investigation tool used by top law enforcement agencies, including the FBI and Europol.
It supports password recovery and decryption for over 380 files, such as PDFs, ZIP archives, QuickBooks files, and even Bitcoin wallets. It’s also capable of cracking full disk encryption systems such as BitLocker, FileVault2, and VeraCrypt.
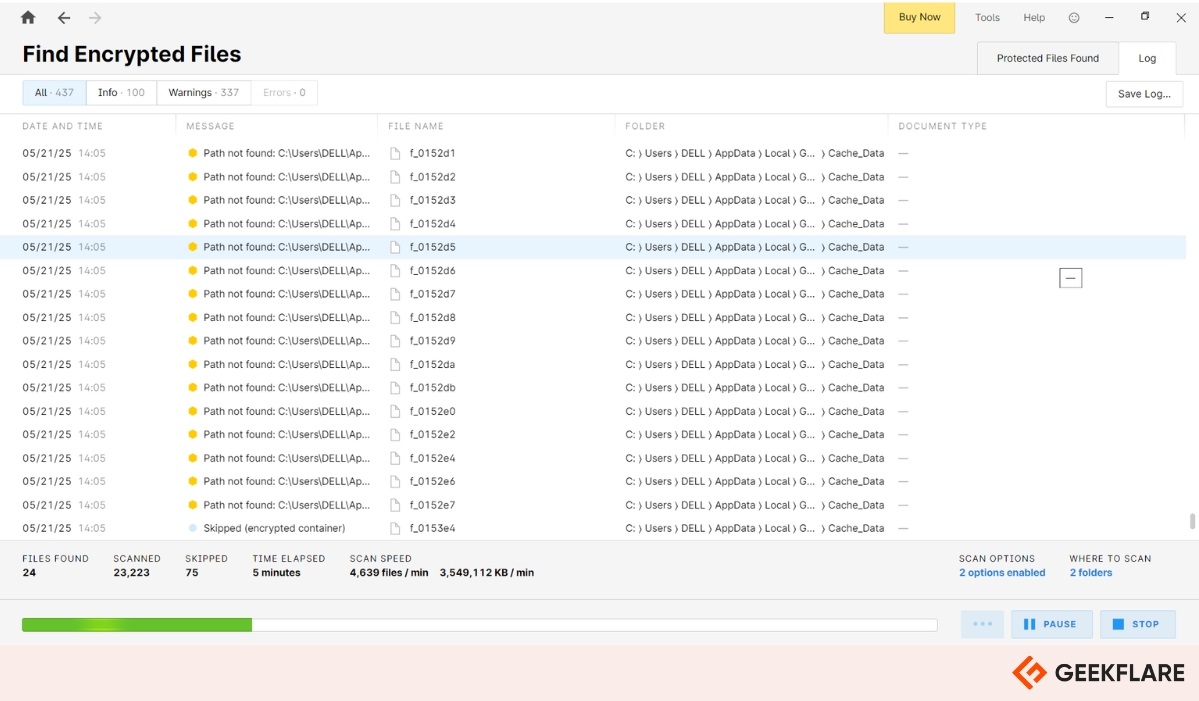
It’s live memory analysis, which allows investigators to extract passwords and encryption keys directly from memory or disk images. This is especially useful when dealing with encrypted drives created using tools like BitLocker, TrueCrypt, Apple DMG, LUKS (1 & 2), and McAfee.
Passware offers different versions based on your needs, ranging from the entry-level Kit Basic to the fully equipped Kit Forensic. There’s also a free, limited version available if you want to try it out before committing to the full toolset.
3. Wireshark
Wireshark is a network capture and analyzer tool to see what’s happening in your network. With features like deep packet inspection, filtering, and protocol decoding, it helps uncover crucial evidence such as IP addresses, payload content, and session details.
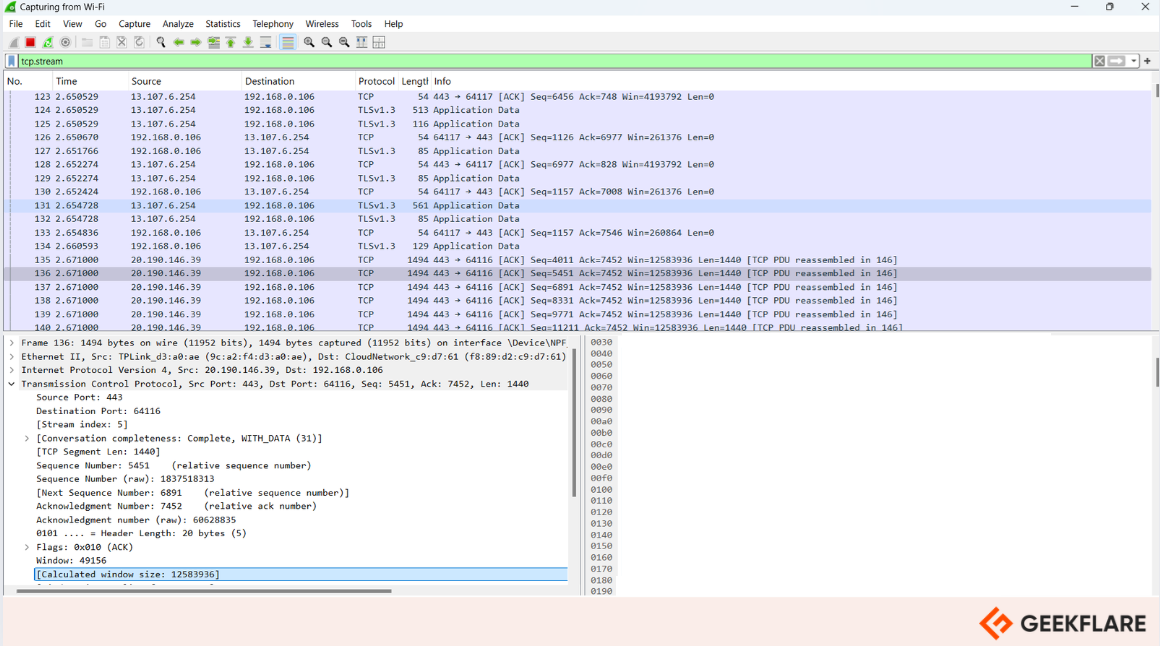
Wireshark is invaluable for incident response, intrusion detection, and network troubleshooting, making it a key tool in the digital forensic investigator’s toolkit.
4. NetworkMiner
NetworkMiner is a powerful network forensics tool available for Windows, Linux, and macOS. It helps identify operating systems, hostnames, sessions, and open ports by analyzing captured network traffic or live packet sniffing.
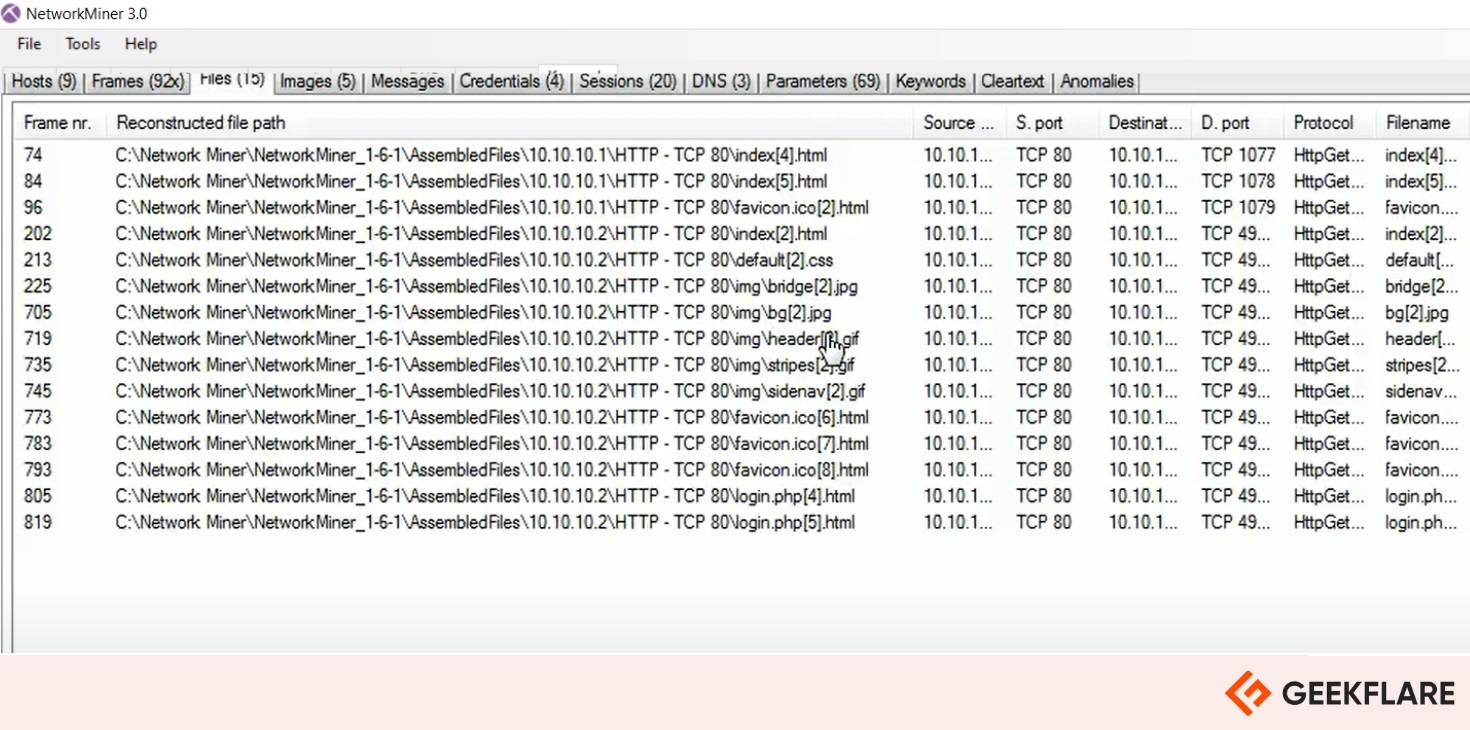
It allows users to extract valuable data, like files, images, emails, and credentials, through a user-friendly interface.
5. Forensic Investigator
If you’re using Splunk, Forensic Investigator is a valuable add-on that brings multiple investigation tools into one place. As a Splunk app, it simplifies digital forensics by combining several handy utilities, including:
- WHOIS & GeoIP lookup – Identify domain ownership and location info
- Ping – Check if a host is reachable on the network
- Port Scanner – Discover open ports on a target system
- Banner Grabber – Collect service and version information
- URL Decoder/Parser – Decode and analyze encoded URLs
- XOR, HEX, Base64 Converter – Quickly convert between common encoding formats
- SMB Share & NetBIOS Viewer – Explore network shares and NetBIOS details
- VirusTotal Lookup – Check files or URLs against known malware databases
6. FAW
FAW (Forensics Acquisition of Websites) is the world’s first and most widely recognized forensic browser. It supports acquiring various web resources, including static and dynamic websites, CMS platforms, e-commerce sites, social networks, and even content from the Dark Web via the TOR network.
FAW captures not just static web content, but also dynamic behavior and multimedia elements over time. You can schedule recordings at set intervals to track how content changes. It’s built-in crawler scans and maps all pages linked from a main URL.
Additional modules allow for specialized captures:
- YouTube: Download and certify videos and related content.
- WhatsApp: Capture and archive entire chat histories.
- Google Accounts: Access and record private pages.
- Streaming Videos: Record streams directly via video URLs.
- Email: Connect to mail servers to download and certify emails in your inbox.
It also supports FTP and SFTP modes for downloading complete sites while preserving original file metadata. Every action within the FAW suite is logged and can be compiled into detailed reports for full transparency.
7. CrowdStrike
CrowdStrike offers a suite of free community tools designed to support cybersecurity professionals in enhancing their security posture and incident response capabilities.
CrowdStrike has some other helpful tools for investigation.
- Totrtilla – anonymously route TCP/IP and DNS traffic through Tor.
- Shellshock Scanner – scan your network for Shellshock vulnerability.
- Heartbleed scanner – scan your network for OpenSSL heartbleed vulnerability.
8. Kali Linux
Kali Linux is one of the most popular operating systems for security and penetration testing, but it has forensic capabilities too. It also offers a strong set of digital forensics and incident response (DFIR) tools for investigating breaches, analyzing malware, or recovering data.
For system activity and breach investigation, Kali supports log analysis, browser history recovery, and audit tracking. It also offers powerful malware analysis tools such as radare2, Ghidra, and strace, which support both static and dynamic analysis.
Its tools, like Scalpel and ExifTool, support file carving and metadata analysis. Its bulk extractor helps scan disk images for sensitive artifacts such as emails, credit card numbers, and URLs.
9. Elcomsoft Forensic Disk Decryptor
Elcomsoft Forensic Disk Decryptor is a decryption tool that gives you instant access to data encrypted using BitLocker, FileVault 2, TrueCrypt, Veracrypt, and PGP Disk.
It performs on-the-fly decryption, allowing users to mount encrypted volumes as drive letters for real-time access to protected data.
Key Features include:
- Zero-footprint operation: Leaves no trace of the decryption process, ensuring complete stealth.
- Access to encryption metadata: Useful for retrieving original plaintext passwords.
- Automatic detection: Identifies encrypted volumes and displays encryption settings.
It offers full disk decryption and automatically searches, identifies, and displays encrypted volumes and details on the volume’s encryption settings. Elcomsoft offers a free trial version of the forensic decryptor.
10. Paladin Forensic Suite
Paladin Forensics Suite is a bootable Linux distribution based on Ubuntu, developed by SUMURI, a company specializing in digital forensics and eDiscovery tools. It supports both 32-bit and 64-bit systems.
Paladin Forensic Suite is designed for data acquisition and analysis; it gives users access to over 100 pre-installed open-source forensic tools right after booting. These tools cover a broad range of functions, including decryption, hardware analysis, password recovery, messenger data recovery, and social media investigation.
It also allows for device cloning, especially useful when storage media can’t be removed. It’s built-in disk manager provides a visual overview of connected drives and partitions, making it easier to manage data sources. The suite automatically logs activity, with logs saved to any connected storage device.
11. Mobile Verification Toolkit (MVT)
Mobile Verification Toolkit (MVT) is an open-source forensic tool that helps users check their mobile devices for signs of spyware or other malicious software.
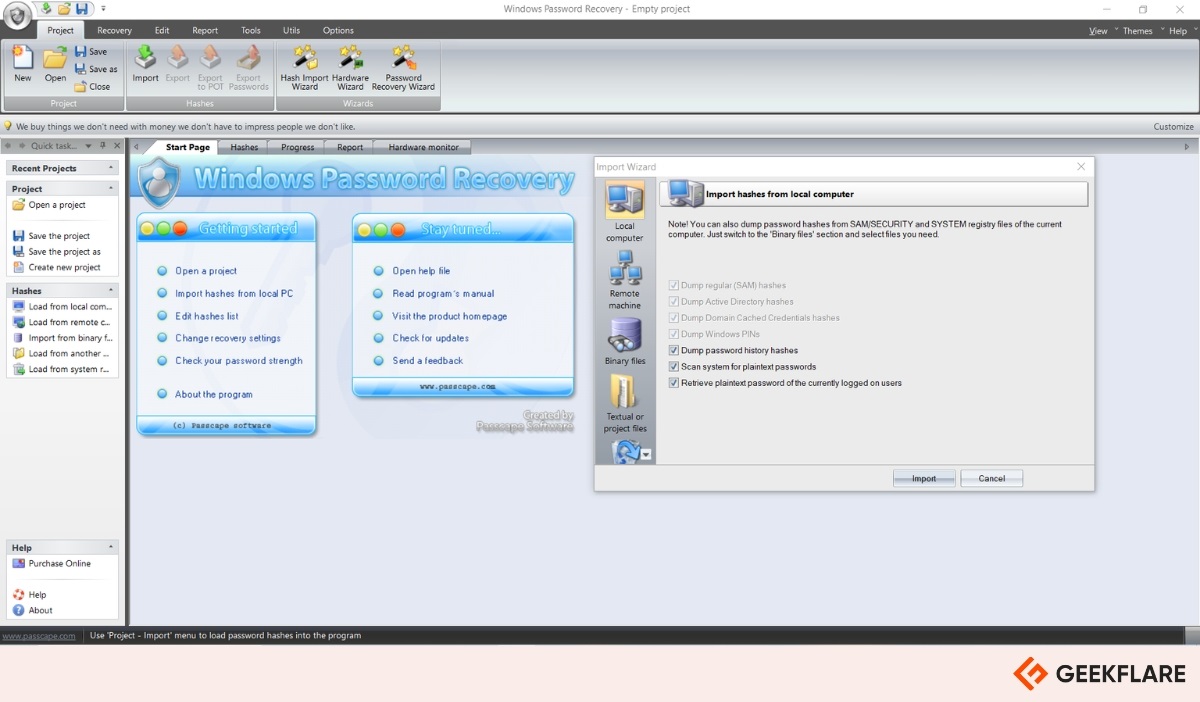
Developed by Amnesty International’s Security Lab in 2021, MVT is designed to make it easier to collect and analyze data from both Android and iOS devices. It scans for indicators of compromise by reviewing things like installed apps, system logs, and backup files.
MVT is especially useful for spotting traces of known spyware, such as Pegasus, and can alert users if their device may have been targeted without their knowledge.
12. Passcape Windows Media Forensics
Passcape Windows Media Forensics is a tool designed to analyze images, videos, and user actions within the Windows Photos app. It identifies faces, tags, locations, and other metadata such as capture time, camera model, and manufacturer.
It also tracks user interactions when media was accessed or modified, and presents findings in a readable format. With support for large media libraries, it streamlines investigations and allows data to be backed up for future analysis.
13. CredentialsFileView
CredentialsFileView is a free Windows utility by NirSoft that decrypts and displays credentials stored by the Windows Credential Manager.
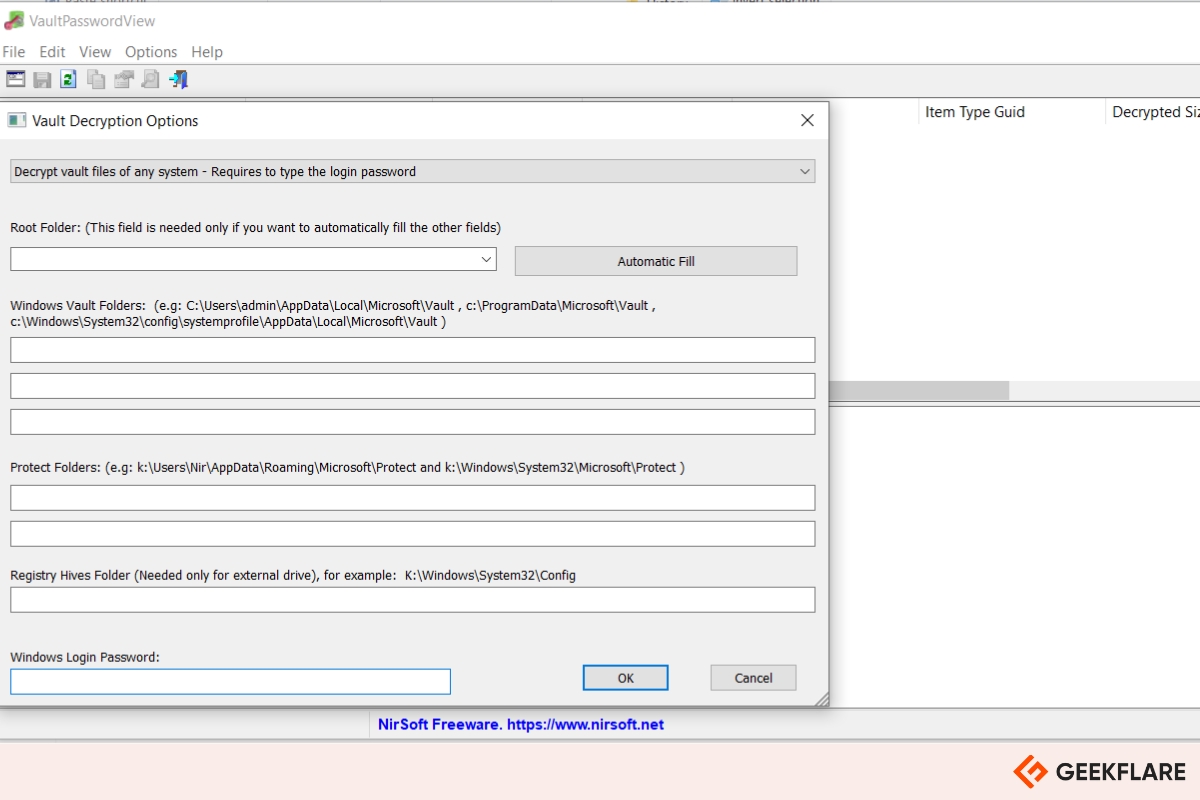
It reveals usernames and passwords saved by Windows services, remote desktop connections, Internet Explorer, Windows Messenger, and mail accounts. It supports both 32-bit and 64-bit systems up to Windows 10.
14. SIFT
SIFT (SANS Investigative Forensic Toolkit) Workstation is a free and open-source suite of digital forensic and incident response tools developed by the SANS Institute. Built on Ubuntu 14.04, it remains one of the most popular platforms for forensic investigations.
SIFT supports many file systems and evidence formats, including NTFS, FAT, ext4, raw (dd), E01, AFF, and VMDK, making it suitable for analyzing file systems, memory images, and network artifacts.
It can be deployed as a virtual machine, installed directly on Ubuntu, or run on Windows using the Windows Subsystem for Linux (WSL).
15. Foxton Forensics
Foxton Forensics offers two powerful and free tools for browser forensics:
Browser history capturer – This tool captures browsing history from popular Windows browsers, including Chrome, Firefox, Internet Explorer, and Edge. Ideal for digital investigations or user activity audits.
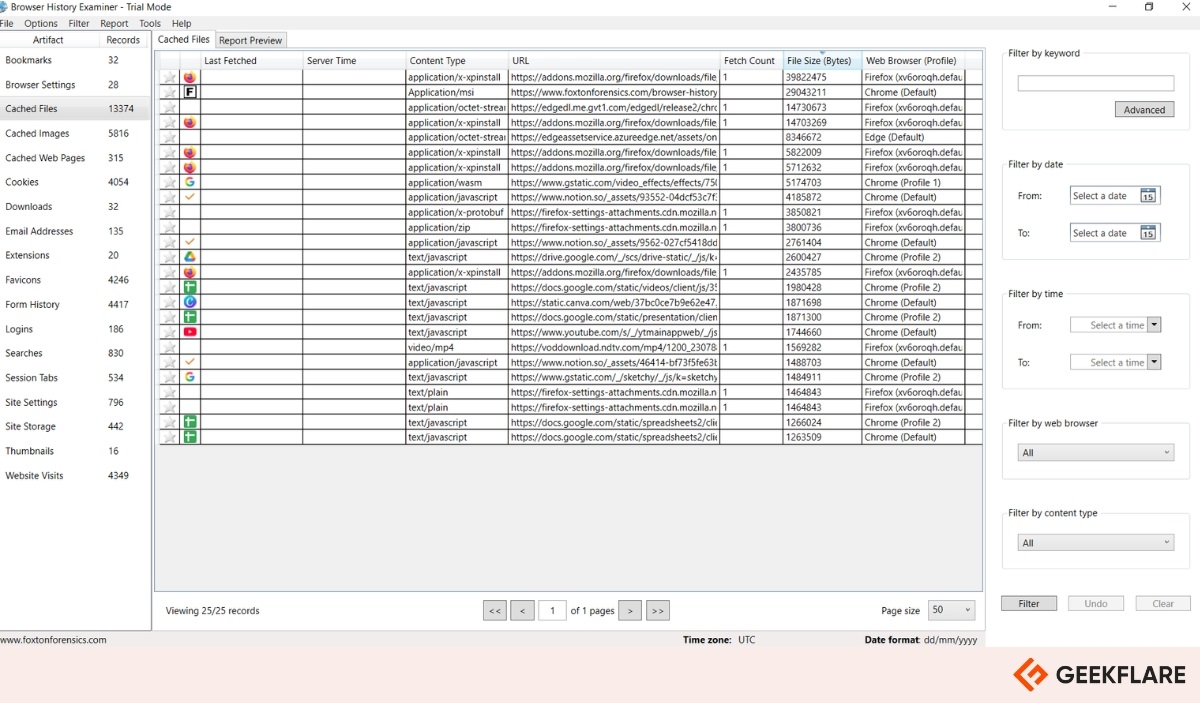
Browser history viewer – It extracts and analyzes internet activity history from most modern browsers. Results are shown in the interactive graph, and historical data can be filtered.
16. Hashcat
Hashcat is a powerful password-cracking tool used by penetration testers, system admins, and threat actors. It works by hashing password guesses and comparing them to the target hash until a match is found.
It supports all major hash formats and uses GPU acceleration for high-speed performance. It offers multiple attack modes, including dictionary, combinator, mask, and its most efficient method, rule-based attack. If you need to crack passwords efficiently, Hashcat is the tool of choice.
17. John the Ripper password cracker
John the Ripper password cracker is a free and open-source password security auditing and password recovery tool. It can be used to find and crack weak passwords in a system.
This tool supports hundreds of hashes and ciphers, including those used in passwords stored in UNIX-based systems, Windows operating systems, macOS, web apps such as WordPress, database servers such as SQL, and encrypted private keys on cryptocurrency wallets, among others.
Honorable Mentions
While I’ve covered the free forensic investigation tools, here are a few honorable mentions that you can consider as well.
18. NMAP
NMAP is a powerful open-source network scanner used for network discovery and security auditing. It is supported on most operating systems, including Windows, Linux, Solaris, Mac OS, HP-UX, etc. It helps identify devices, services, and vulnerabilities across networks.
19. NFI Defraser
NFI Defraser is a forensic analysis tool that helps to detect and restore full or partial multimedia files from data streams, such as unallocated disk space. It is particularly useful for recovering video evidence in digital investigations.
20. ExifTool
ExifTool is a powerful command-line tool used to view, edit, and manage metadata across various file types. It supports a wide range of formats, including EXIF, GPS, IPTC, XMP, JFIF, GeoTIFF, Photoshop IRB, and FlashPix.
21. Toolsley
Toolsley provides a collection of over ten browser-based tools designed for quick and easy file investigation. Without requiring any installation, it allows you to analyze files, verify signatures, inspect binary data, generate hashes, encode text, remove metadata, and even create secure passwords or data URIs; all right from your browser.
22. Dumpzilla
Dumpzilla is a Python-based free tool that extracts and analyzes data from Firefox profiles. It helps inspect browsing history, downloads, cookies, saved passwords, and more.
23. RAM Capturer
RAM Capturer by Belkasoft is a free tool designed for forensic experts to capture the entire contents of a computer’s RAM, even when security measures like anti-debugging or anti-dumping are in place. It works with all Windows versions and editions, including Windows 7, 8, 10, 11, and Server editions like 2003 and 2008.
24. Sleuth Kit
The Sleuth Kit is an open-source set of command-line tools used in digital forensics to examine disk images and file systems. It allows investigators to recover and analyze data from computers, helping uncover digital evidence.
25. CAINE
CAINE (Computer Aided Investigative Environment) is a Linux distro that offers a complete forensic platform, which has more than 80 tools for you to analyze, investigate, and create an actionable report.
26. HashMyFiles
HashMyFiles is a lightweight tool from NirSoft that lets you quickly calculate MD5, SHA1, and other hash values for files. It works on most modern versions of Windows.
27. Magnet RAM Capture
Magnet RAM capture is a free tool designed for forensic investigators to capture the physical memory (RAM) of a Windows computer. It helps preserve volatile data such as running processes, active network connections, and decrypted files for detailed analysis.
28. Magnet Encrypted Disk Detector
Magnet Encrypted Disk Detector (EDD) is a free, command-line tool that checks encrypted physical drives. It supports detection of various encryption types, including BitLocker, TrueCrypt, PGP, VeraCrypt, Check Point, and SafeBoot.

