Email spoofing is a malicious tactic in which cybercriminals send fake emails that look like they come from trusted organizations or individuals. When unsuspecting users act on these emails, they may unknowingly share sensitive data, install malware, or lose money.
In email spoofing, cybercriminals don’t have to hack systems to get inside your IT network. They just need one employee to click a link in a spoofed email. That single click can install malware, paving the way for them to access your network. So, it is important to defend against email spoofing attacks to strengthen your cybersecurity posture.
A successful email spoofing attack can lead to data breaches, financial losses, malware infections, and reputational damage for organizations.
This article will explore everything you should know about email spoofing, its types, reasons, and email spoofing protection measures. Let’s dive in.
How Email Spoofing Works
All emails use the Simple Mail Transfer Protocol (SMTP), a standard protocol for exchanging emails between devices. Threat actors often exploit SMTP to spoof email addresses because it lacks security features like encryption or authentication. Let’s explore how.
An email has three parts: the envelope, the header, and the body. The envelope (SMTP envelope) contains metadata like the sender’s and recipient’s addresses and routing details, but this information is not visible when you open an email. The email header visible in your inbox shows the sender’s name, subject line, and timestamp. The body of the email is the content sent as a message.
In the absence of any email security solution, the SMTP envelope doesn’t check the email header to deliver the email. And recipients don’t see the SMTP envelope. So hackers change the sender’s information (the From section) and the reply-to field in the header through various techniques of varying complexity to make the email appear to be coming from a trusted source.
Additionally, hackers craft deceptive content using the original brand’s logo, fonts, and color scheme to make the email content appear legitimate.
The goal of email spoofing is often to manipulate users into trusting malicious content.
Organizations are increasingly adopting countermeasures like Domain-Based Message Authentication, Reporting, and Conformance (DMARC) to prevent email spoofing. While DMARC addresses SMTP vulnerabilities, many domains remain unprotected, leaving them open to spoofing attacks.
We will discuss these security measures later in this article. Let’s first explore different types of email spoofing.
Different Types of Email Spoofers
There are various methods to spoof emails, and all types differ based on the part of an email a hacker spoofs. Below, we have listed three commonly used email spoofing techniques attackers use for email spoofing.
Sender Spoofing
Sender spoofing is the simplest type of email spoofing and requires no technical expertise. In this type of attack, a hacker just has to spoof the sender’s display name, which can be easily done by creating an email account with the intended name.
Here is an example of a sender spoofing email in which the attacker impersonated our founder.
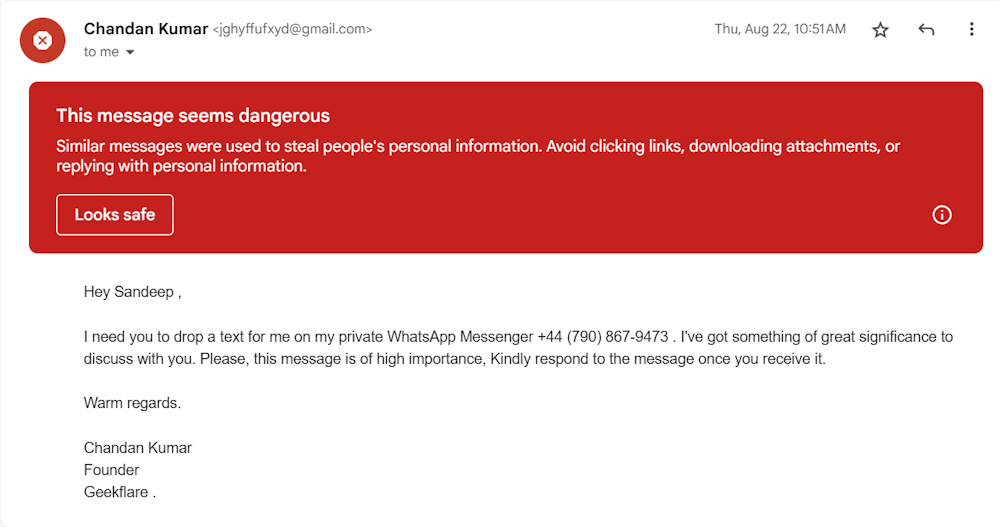
As you can see, the attacker just forged the display name in this email. Sender spoofing emails can pass all spoofing countermeasures because they come from legitimate emails.
You can quickly spot a sender spoofing email by looking at the sender’s email ID, which is often created using a public email domain like Gmail or Yahoo. In the above example, the threat actor used Gmail to send a spoofed email.
Domain Spoofing
Hackers often use email addresses from well-known organizations or individuals to make spoofed emails more convincing.
For instance, they might use [email protected] in the “From” section of an email to trick the recipient into thinking it’s from the Example Company.
What’s surprising is that hackers don’t need to hack the domain of a reliable company, so they can use [email protected] in their email header. Instead, they simply check whether the company has implemented security protocols like DMARC using specialized tools. If the company hasn’t, hackers can exploit this weakness, sending spoofed emails using its domain in the email header.
Lookalike Domain Spoofing
In this type of email spoofing, attackers register a lookalike domain to deceive recipients into thinking the email is from a trusted organization.
For example, they might register paypa1.com, which closely resembles the legitimate domain – paypal.com. The only difference is that the spoofed domain has ‘1’ instead of ‘l’ in the spelling of PayPal. Unaware recipients might overlook slight spelling differences.
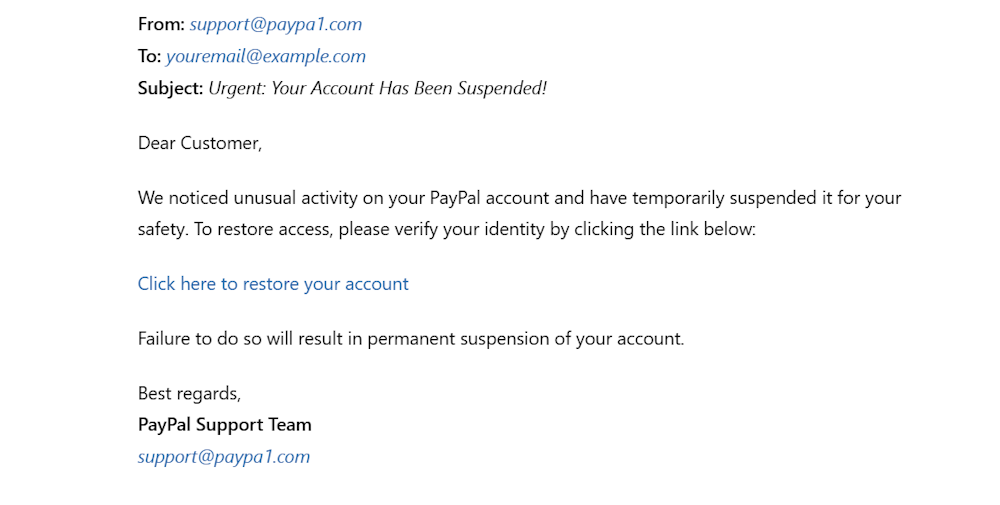
Since these emails come from legitimate domains, they are less likely to be flagged as spam, making them even more dangerous.
Common Challenges of Email Spoofing
Email spoofing is a serious cybersecurity risk because it can be used to fulfill various malicious objectives, such as stealing data or causing monetary and reputation damage. A single click on a malicious link in a spoofed email can install malware.
Despite training employees on email spoofing, many organizations continue to face the threat of email spoofing. Here are the critical challenges of email spoofing.
Lack of Built-in Email Authentication
Most clients rely on Simple Mail Transfer Protocol (SMTP) to move messages from email servers to end users. As SMTP was designed to offer simplicity and efficiency, it lacks built-in email authentication. So, in the absence of additional email security measures like DMARC, it becomes easier for hackers to exploit SMTP vulnerability to spoof emails.
Make sure to implement email authentication protocols like SPF, DKIM, and DMARC. These add layers of verification, making it harder for attackers to spoof emails.
Bypassing Email Filters
Many times, threat actors and scammers only spoof display names by creating email accounts using the names of trusted individuals or organizations. Since they use reputable email service providers like Gmail or Outlook, these spoofed emails can bypass spam filters and land directly in recipients’ inboxes.
For example, a threat actor can create a Gmail address under the name “Amazon Customer Care.” The email would display the sender’s name as Amazon Customer Care, tricking unsuspecting users into believing it’s from Amazon.
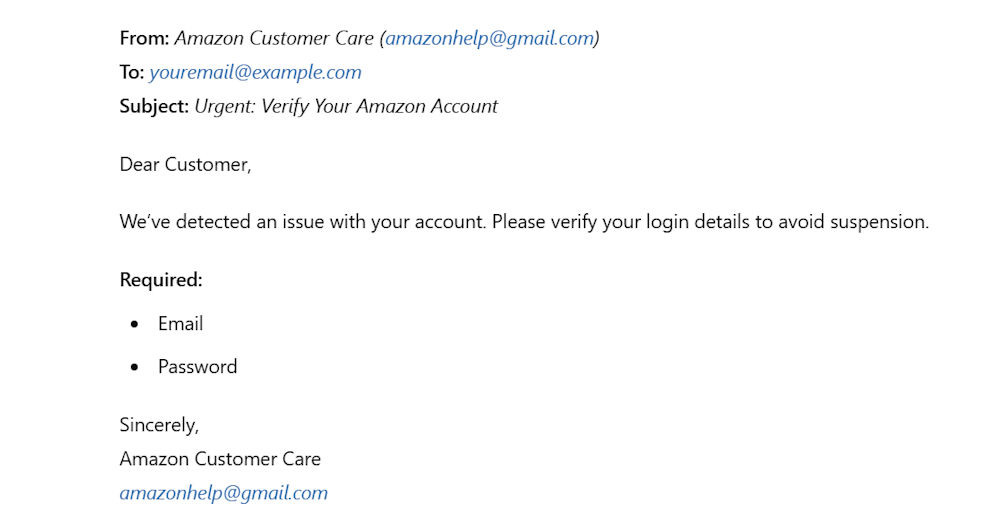
Additionally, skilled hackers may use a legitimate domain to send an email and spoof the sender’s address in the email header. If the legitimate domain doesn’t have proper email security configurations (like DMARC), the recipient’s email server may deliver the email.
If your company uses an email security solution, you should regularly update and configure advanced email filtering tools to block spoofed emails. You should also encourage your employees to verify the actual email address, not just the name displayed in the email header.
Difficulty in Identifying Spoofed Emails
Spoofed emails are often designed to look convincing, making it hard for recipients to recognize them as fraudulent. Subtle changes to email addresses or logos can easily deceive even vigilant users.
Encouraging users to inspect email details closely, especially sender addresses and suspicious links, goes a long way toward dealing with spoofed emails. You should also use email security tools that highlight spoofed or suspicious senders.
Lack of Awareness
A significant challenge in combating email spoofing is users’ general lack of awareness regarding the risks associated with deceptive emails.
Raising awareness helps prevent users from falling for deceptive messages. Therefore, you should make a policy of conducting regular training on recognizing spoofed emails and cybersecurity best practices.
Trusting Familiar Names
Email users often tend to trust familiar names and addresses, and attackers exploit this trust through spoofing. When recipients see an email appearing to come from trusted sources, they are likely to engage with it without much scrutiny. This makes it difficult to curb the menace of email spoofing.
For example, you receive an email from “John Smith,” the CFO of your company. He is asking you to transfer funds to a vendor urgently. Since you recognize the name and often communicate with John, you might trust the email without checking the actual sender’s email address.
That said, you should encourage your employees to verify the sender’s email domain, even if they recognize the name. Tell them to double-check requests for sensitive actions like fund transfers.
Social Engineering Tactics
Spoofed emails often employ social engineering tactics to exploit emotions like fear or sense of urgency. Attackers craft convincing stories, like account suspension or urgent payment requests, which compel recipients to act quickly without verifying the email’s authenticity.
For example, a spoofed email might claim that an account is compromised and requires immediate action. In such a deception and psychologically manipulative situation, the recipients might provide personal information or click on harmful links.
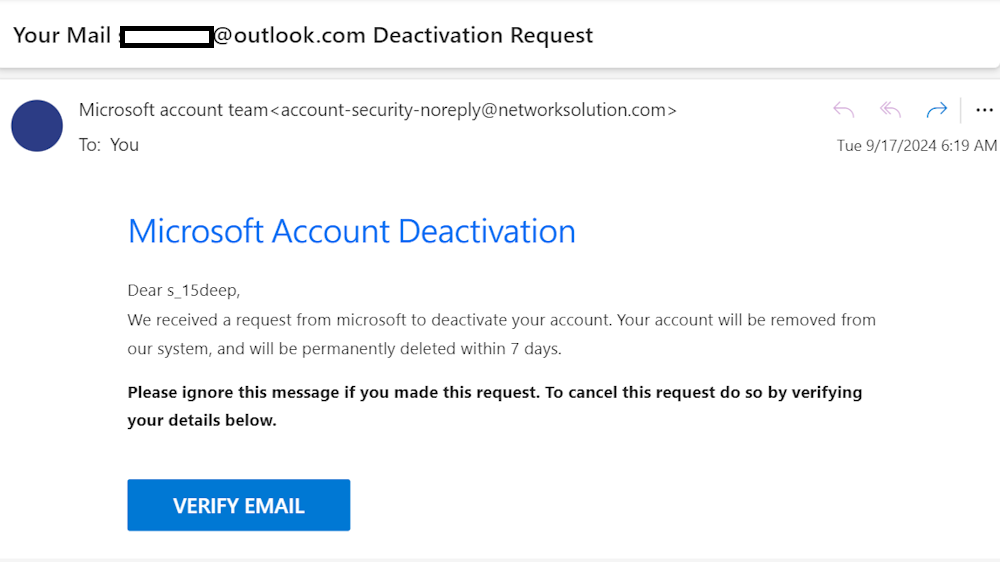
To overcome this challenge, you should educate your employees on common social engineering tactics, such as phishing, baiting, vishing, and spear phishing. You should also encourage them to pause and verify any email that urges immediate action or requests sensitive information.
How To Identify a Spoofed Email
Identifying a spoofed email doesn’t require technical expertise. Often, a spoofed email has several telltale signs that indicate it’s not actually coming from the sender it claims to be.
Here are some tips to identify a spoofed email.
- Check the Sender’s Email Address: Inspecting email headers is a useful way to detect fraudulent emails. Spoofed emails often contain slight misspellings or extra characters to appear legitimate. Always verify if the display name matches the email address, as scammers often use a legitimate-looking display name while the actual email address is suspicious.
- Look for Unusual Language or Grammar Errors: If emails have awkward phrasing, spelling mistakes, or poor grammar, they are big red flags.
- Verify Links: You should always hover over links in the email. If they appear suspicious or don’t match legitimate sites, it is a clear sign of a spoofed email.
- Check for Urgency or Unusual Requests: Be extra careful about emails that include urgent requests for personal information or sensitive data. You should always double-check these emails and confirm the request via an alternative channel.
- Examine the Email’s Tone and Content: If the tone or content of the email seems unusual for the sender, it might be spoofed.
- Check for Missing Personalization: Legitimate emails from trusted companies or individuals usually include personalized information like your name, account details, or order information. Spoofed emails often lack these details.
Also, you should analyze the email header. It should pass SPF, DKIM, and DMARC authentication. If it fails any of those, you should be extra cautious about handling the email.
How Is Email Spoofing Different From Phishing
Email spoofing is the act of forging the sender’s email address to make it appear as though the message has come from a trusted entity. On the other hand, phishing is a broad category of cyberattacks that aim to steal confidential information, install malicious software, and fulfill various other malicious objectives. Email spoofing is an attack vector often used across multiple phishing attacks.
Here is a quick table explaining the key differences between email spoofing and phishing based on purposes, tactics, outcomes, and other factors.
| Aspect | Email Spoofing | Phishing |
|---|---|---|
| Purpose | Impersonates to deceive, spreading malware | Steals personal data or financial information, spreading malware |
| Tacttics | Alters the “From” field in email headers | Uses fake emails (email spoofing), websites, or links to trick recipients |
| Outcome | Spreads malware, bypasses filters, or impersonates users | Theft of sensitive information, financial losses |
| Scope | Focused on faking the email sender’s identity | Broader attack, often using email spoofing as a tactic. |
Legal Implications of Email Spoofing
Email spoofing, if used for purposes other than training, testing, or education, can have serious legal implications. Various legal authorities and regulations have made rules against email spoofing.
For example, The CAN-SPAM Act prohibits deceptive email practices in the U.S. It requires accurate “From,” “To,” “Reply-To,” and routing information, including the domain name and email address. The sender must be clearly identified, and violations can result in fines of up to $51,744 per email.
The UK Fraud Act 2006 provides users protection against phishing emails. India also has a strict law to prevent email spoofing. The Indian IT Act 2000 has various provisions against cyberattacks, including phishing.
Countries worldwide are working hard to prevent email spoofing, but hackers continue to target users with spoofed emails. As a business owner, it’s your responsibility to protect sensitive data from your customers and vendors.
Depending on your industry, you might be subject to data protection regulations like GDPR, HIPAA, or PCI DSS. A data breach due to email spoofing can result in significant financial and reputational damage.
To minimize the risk, you should strengthen your defenses and take proactive steps to mitigate email spoofing attacks.
Can I Use ChatGPT to Spoof Emails?
No, you cannot use ChatGPT to spoof email. Email spoofing is unethical and illegal, for it requires impersonating trusted individuals and organizations to trick unsuspecting users into believing that spoofed emails originated from trusted entities.
OpenAI ChatGPT is an ethical Generative AI chatbot that helps users generate content based on prompts. You can use it to produce various types of content, including email copy, product descriptions, a document summary, and more.
You can use ChatGPT to create realistic phishing emails and train your employees on how clever hackers craft spoofed messages. This will help employees recognize and avoid potential threats.
Reasons for Email Spoofing
Threat actors and scammers carry out email spoofing attacks for various reasons, often driven by malicious intent. These reasons include installing malware on victims’ devices, bypassing block lists, stealing identity, and more. Let’s explore common reasons for email spoofing.
Anonymity
Spoofing displays names and addresses in emails and provides threat actors with a cloak of anonymity. Threat actors can send fraudulent messages without using their real names and addresses by using the name and address of a trusted individual or organization in their email headers.
For example, a cybercriminal might send an email claiming to be from a well-known company, like a bank, asking users to verify their account details. Recipients may feel compelled to respond, unaware that they are communicating with a malicious actor rather than a legitimate institution. This way, the threat actor will get to know the victims’ login credentials without exposing their true identity.
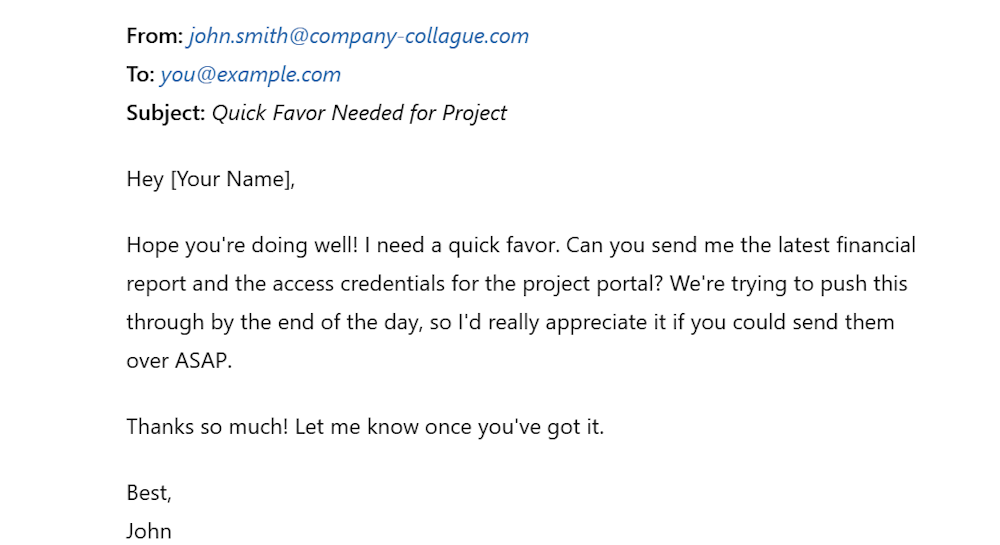
Impersonating a Trusted Individual or Organization
Hackers often spoof email addresses to impersonate trusted individuals or organizations to exploit recipients’ trust in those entities.
An attacker, for example, might spoof an email from a colleague requesting sensitive information or urgent action on a project. The email could contain phrases that mimic the colleague’s usual communication style to make the email more convincing.
Identity Theft
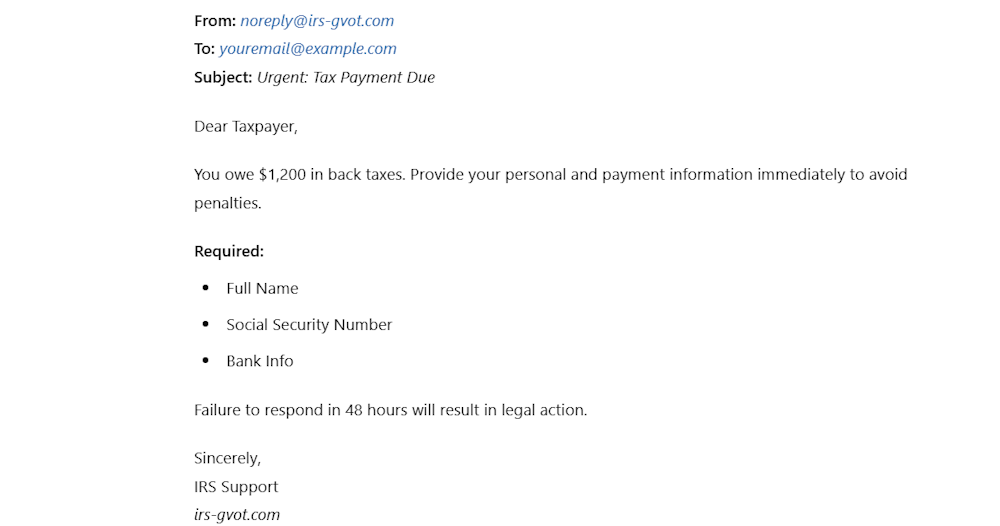
One of the primary goals of email spoofing is to facilitate identity theft. Threat actors or scammers often send emails that appear to come from reputable sources, asking recipients to provide personally identifiable information (PII) such as phone numbers, Social Security numbers, or bank account details.
For example, an email might claim to be from the IRS and state that the recipient owes back taxes and must provide personal information to resolve the issue. Once the attacker has this information, they can commit fraud or open accounts in the victim’s name.
Bypassing Block Lists
Most email providers allow users to block or mark suspicious emails as spam. Cybercriminals frequently use spoofing to bypass email filters and block lists that protect users from spam and malicious content because new spoofed email addresses are unlikely to be included in users’ spam or block lists.
Spreading Malware
Spoofed emails are commonly used to distribute malware, which can infect the recipient’s device when links are clicked or attachments are opened.
For example, an email might appear to be a security alert from a trusted software provider urging the recipient to download an “important update.” When the recipient clicks the link, they unknowingly download malware that can steal personal information or compromise their system.
As unsuspecting users trust emails that seem to come from familiar sources, the malicious technique effectively installs malware on the victims’ devices.
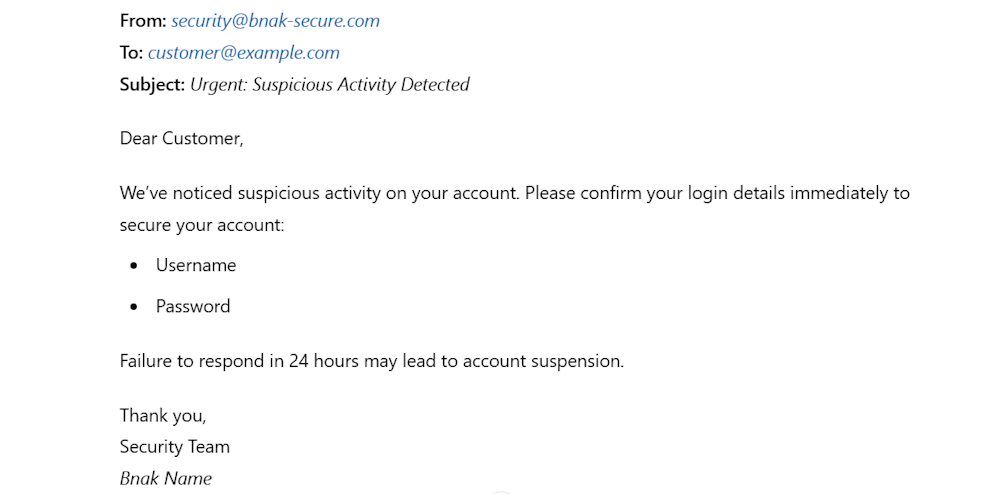
Man-in-the-Middle (MITM) Attacks
Hackers can use email spoofing to carry out Man-in-the-Middle (MITM) attacks. For example, an attacker might spoof an email from a bank department and ask a user to confirm their login credentials to examine an alleged suspicious transaction. If the users share their credentials, the attacker uses this information to watch transactions and communications between the bank and the victim.
Phishing
Email spoofing is a common tactic used in phishing attacks. Attackers impersonate trusted individuals or organizations to deceive users into revealing sensitive information, transferring money, or unknowingly installing malware on their devices. These spoofed emails often appear legitimate, making it easier for cybercriminals to manipulate victims into harmful actions.
Business Email Compromise
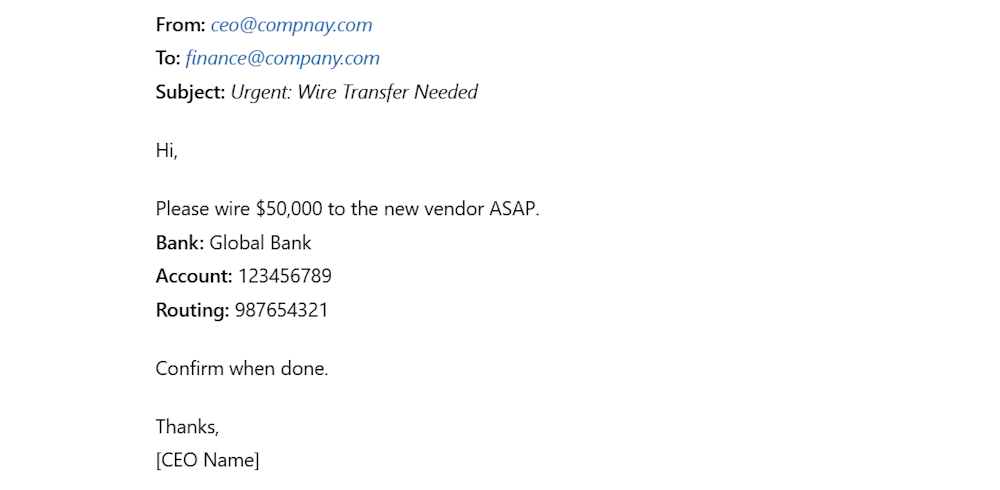
Business Email Compromise (BEC) is a type of cyberattack where attackers impersonate high-level executives, such as the CEO or CFO, to trick organizations into sharing confidential information, transferring funds, or carrying out other malicious actions. These attackers often use spoofed email addresses that closely resemble legitimate ones, making it hard for recipients to detect the fraud.
For example, a cybercriminal may spoof the email of a company’s CEO, sending a message to the finance department requesting an urgent wire transfer to a new vendor. The email appears legitimate, complete with the CEO’s signature and company branding. The finance team, trusting the familiar name and the urgency of the request, completes the transfer without realizing the email was part of a Business Email Compromise (BEC) attack.
Damaging the Sender’s Reputation
Threat actors also leverage email spoofing to harm the reputation of a legitimate sender. They do so by sending out false or damaging messages under the guise of a trusted sense.
For instance, a cybercriminal could spoof an email from a well-known charity, sending offensive or misleading messages to donors. When recipients believe the email is legitimate, the charity’s reputation suffers, leading to loss of donations and public trust, as people associate the offensive content with the actual organization. This tarnishes the charity’s image, even if they had no involvement.
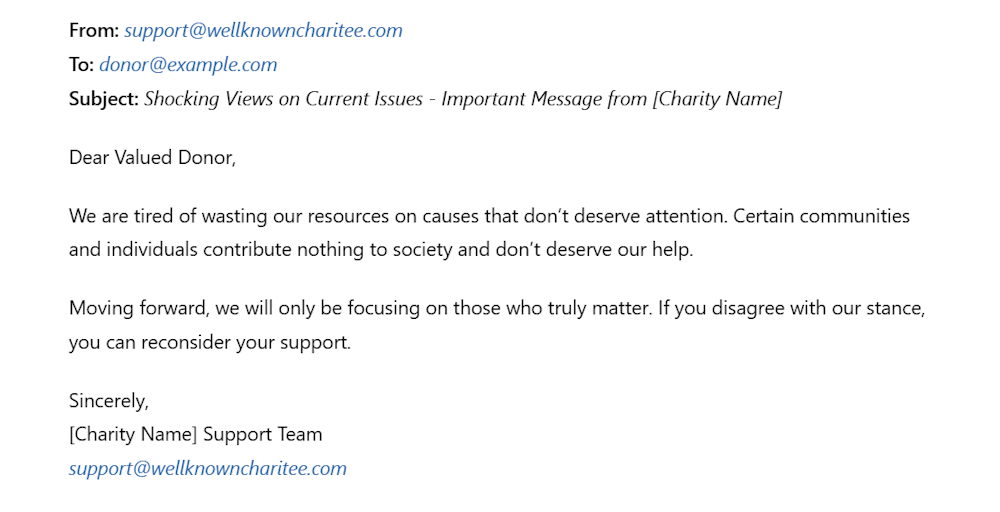
Manipulate Opinions
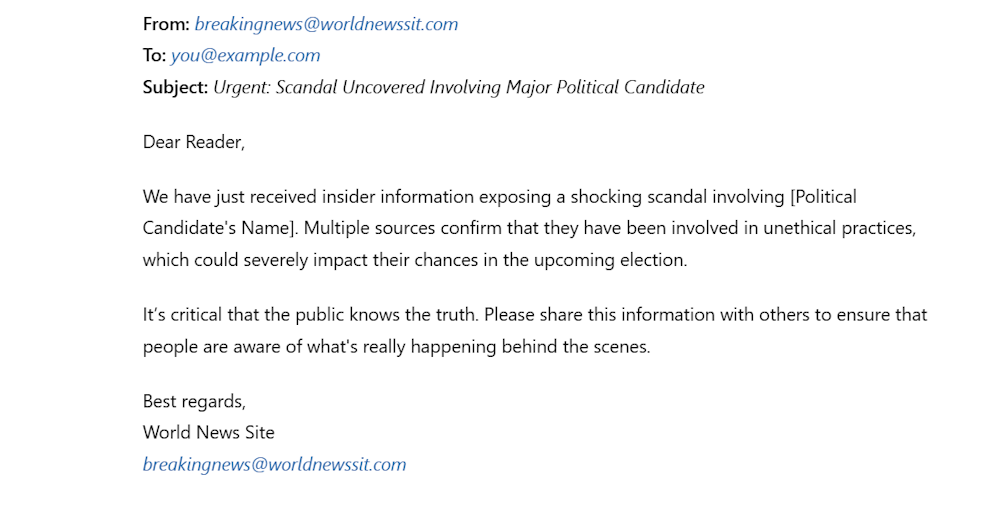
Hackers can employ email spoofing to change people’s opinions. To do so, they send fake emails that seem to come from trusted sources. For example, they might pretend to be a well-known person or news outlet and send false information to influence people’s thoughts about an issue, like politics or a company’s reputation. If people believe the email is real, they may start to trust and spread fake information, which can shape opinions based on lies.
How Can You Protect Against Email Spoofing?
To protect yourself against email spoofing, you must implement authentication protocols and email security solutions, inspect email headers, and follow cybersecurity best practices. Let’s explore these methods in detail.
Use Email Authentication Frameworks
You can use the following authentication frameworks to prevent hackers from exploiting SMTP vulnerability and spoofing emails.
Sender Policy Framework
Sender Policy Framework (SPF) ensures that only authorized servers can send emails from your domain by adding a specific record to the domain’s DNS settings. When an email is received, the recipient’s mail server checks the SPF record to verify if the sending server is authorized. If not, the email may be flagged as spam or a phishing attempt. SPF helps prevent spammers from using your domain to send fraudulent emails.
DomainKeys Identified Mail (DKIM)
DKIM is an authentication method that uses digital signatures to ensure emails’ authenticity and integrity. Here is how the process works.
In this process, the sender selects email fields like the “from” address, subject, or email body to include in the DKIM signature. The system then creates a hash, encrypts it with the sender’s private key, and attaches it to the email. The recipient’s server uses the sender’s public key to decrypt the hash and verify the email’s authenticity.
Domain-Based Message Authentication, Reporting, and Conformance
Domain-Based Message Authentication, Reporting, and Conformance (DMARC) allows domain owners to set instructions for handling emails that fail authentication checks. It combines SPF and DKIM, instructing email servers to reject or quarantine suspicious messages.
Implement Secure Email Gateways
Implementing secure email gateways, such as SpamTitan, Mimecast, and Sophos email security, can effectively protect your organization from email spoofing. These email security solutions will automatically authenticate using SPF, DKIM, and DMARC to let trusted senders in, scan your email attachments for malware, and use machine learning to analyze email content to block malicious emails.
Inspect Email Headers
Analyzing message headers can reveal inconsistencies between the display name and the sender address. So, you should encourage your employees to inspect the headers of suspicious emails that require immediate action.
In a legitimate email, the display name, From address, and Reply-to address should generally align, but they don’t always have to be identical. Here are some tips to help.
- Display Name: This is the name you see before the email address. It might differ slightly (e.g., “Support Team” vs. “[email protected]”), but it should still make sense in context.
- From Address: This should match the organization’s domain. If it doesn’t, it can be a sign of spoofing.
- Reply-to Address: While it can be different in some cases (e.g., “[email protected]” as From but “[email protected]” as Reply-to), it should be related to the same domain.
Any significant inconsistencies, such as different domains or unrelated addresses, are a red flag for spoofing.
Explore More on Email Security
-
 EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.
EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.


