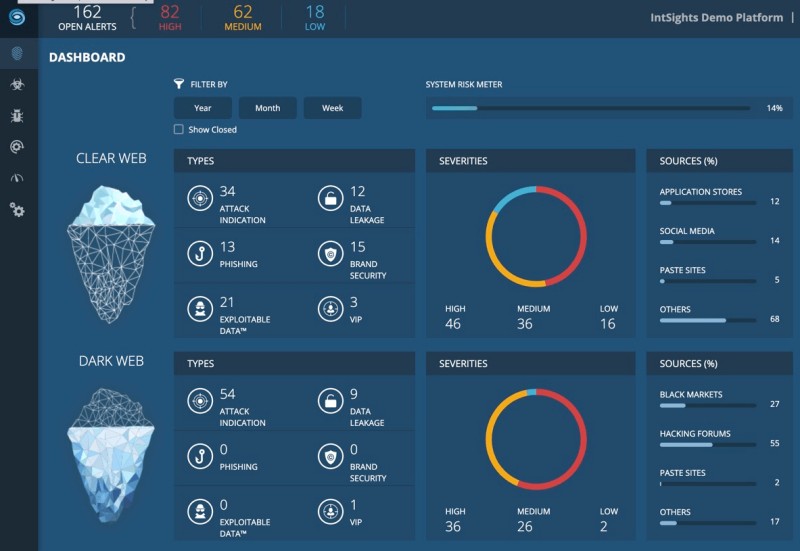
The Dark Web is an untold part of the web that anyone can access, not only you but also criminals, paedophiles, and terrorists.
Many of you might have heard about Dark Web crimes and identity theft that businesses and consumers face.
But what exactly is the Dark Web, and how can it impact you?
It’s actually made up of a set of websites that are hidden from the public. And if your data is compromised, it might be there, stolen by a cybercriminal who might be misusing it for their personal gain.
In this article, I’ll discuss the Dark Web, what Dark Web investigation is, why it is crucial, and some of the best Dark Web investigation tools.
What Is the Dark Web?

In the late 1990s, two organizations dedicated to research in the US department of defense developed an encrypted and anonymized network that protects sensitive information and communication of US spies.
But this network couldn’t be accessed by regular internet surfers. This secret network nowadays is called the Dark Web.
The Dark Web, also called the Darknet, is a part of the Deep Web that includes all website pages which you won’t be able to find on Google and in other search engine results. You can only access the Dark Web when you access your email, log in to Netflix, sign on to your e-banking account, and more.
When you first hear the term “Dark Web”, the first thing you may think is that it is something illegal. However, many people are aware of the fact that it is a required source of threat intelligence for various corporations.
But retaining and attracting the Dark Web can be costly and difficult due to its heightened privacy in accessing content.
To this, you can use a good Dark Web monitoring tool to easily investigate the Dark Web and ensure your data is not stolen and uploaded there. This will avoid manual work and save you time, effort, and resources, not to mention the risks that may come along.
What Is Dark Web Investigation?
When you investigate or monitor the Deep Web and/or Dark web, you look out for data related to your organization. This can be done via Dark Web monitoring.
Different monitoring and investigation tools will help you uncover stolen or leaked information, such as credentials, passwords, intellectual property, and classified documents that are shared by criminals and attackers.

Data breaching is the most common issue nowadays. Millions of information get sold or shared on the Dark Web by cybercriminals. Since it is a new concept, many organizations are still unaware of it. Due to this, criminals find it easy to steal information and continue misusing it while the organization has no clue about what’s going on.
Manually searching for information on the darknet is a complex job. You can take numerous steps to protect your information, make sure passwords are protected, and more. But if you investigate the Dark Web again, you will find some of the information is still out there.
To overcome such issues, you need an investigation tool that detects your information by crawling, searching, and extracting data from millions of sources inside the Dark Web.
Let’s see some of the best Dark Web investigation tools and how they can help you find and protect your data.
Perform data-driven investigations with Social Links and stay on the safer side. It collects massive data volumes from open internet sources like social media, the Dark Web, messengers, and blockchains to analyze and get a complete view needed to perform and streamline your investigations.

Social Links helps cybersecurity professionals, corporates, governments and private investigators, and law enforcement agencies from 80+ countries.
Features:
- Gain up-to-date, accurate insights and live information from 500+ data sources, such as WhatsApp, Facebook, Instagram, Telegram, and more.
- Anonymously access Dark Web marketplaces like Hydra, 8chan, Dread, Raddle, etc.
- Search through 2000 public sources with 1 billion identity datasets.
- Leverage AI technologies like facial recognition, DNA profiling, object detection, and Deepfake detection.
- Use over 1000 built-in search methods.
- View transactions, destinations, addresses, tokens, and senders from major cryptocurrency blockchains.
- Get data from multiple sources in a single place.
- Utilize leading for data analysis such as Spiderfoot HX, i2, Maltego, etc.
- Export data easily to enable detailed reports, cross-checking, and reintegration.
Social Links offers open-source intelligence (OSINT) tools and social media investigation solutions for organizations and individuals. Their security products include:
- SL Professional: This all-in-one OSINT solution allows you to conduct deeper investigations across the Dark Web, social media, etc. It’s available for Maltego and i2 platforms. It accelerates investigations by performing full-cycle data analysis, from data extraction to visualization.
- SL Private Platform: This is an on-premise enterprise-grade platform with many customization options, search methods, and private data storage. It allows you to perform an in-depth investigation of the Dark Web while keeping the data secure and private.
- SL API: It has a range of data analysis and extraction methods and is connected directly to users’ in-house platform through the API.
Skurio
Skurio is an all-around Dark Web monitoring software solution that lets you safely monitor activities and inspect whether your data is compromised or not. No matter where your data is stored, you can protect it using this tool.

Features:
- Automated Dark Web monitoring: Skurio’s automated Dark Web monitoring tool offers enhanced protection from digital risks. It performs around-the-clock scanning for the Dark Web, Deep Web, and Surface Web for your data. Its extensive source feeds have IRC chatrooms, data dumps, social sources, bin sites, and Dark Web sites for efficient detection of sensitive information.
- Alert monitoring: You can easily configure an alert monitor for your emails, domains, products, services, brands, and other data types you want to search for. You can do this using pattern matching and keyword searches. In addition, Skurio offers specialist monitoring for user data breaches and typo-squatting domain registrations to protect users from fraud and scams.
- Collaboration tools: Manage investigations, add comments, create reports, and share results with Skurio’s collaboration tools. Plus, you can integrate feeds to SOC systems using their API integration tools.
- Notifications: Get instant notifications via text, email, or Slack. The moment Skurio detects your data on the Dark Web or any other place on the internet, it will inform you immediately.
Furthermore, Skurio keeps on adding new sources constantly to the monitoring platform and including websites of interest for your industry and business. So, instead of wasting time researching, filtering false positives, and compiling information, you can use Skurio to focus on gaining intelligence from accurate, relevant results.
Rapid7
Keep your organization safe from external threats with Rapid7. It will allow you to gain deeper visibility into all your external online threats and help your customers and employees stay secure with proactive Dark Web monitoring.
Rapid7 helps you mitigate online threats with features like contextualized alerts offering a rapid response. It will also let you easily prioritize your mitigation efforts in order to reduce the investigation time and accelerate alert triage.
Features:
- It can quickly turn brilliance into action with automated alert responses and faster detections across the environment. It happens due to the integration of plug-and-play with your existing technologies, including EDR, SOAR, SIEM, firewall, and more.
- You can manage your SecOps workflows and simplify them through advanced mapping and investigation capabilities that provide contextualized alerts along with a low signal-to-noise ratio. Also, you will get unlimited access to expert analysis to lessen investigation times and accelerate response and alert triage.
- Its intuitive dashboard and accelerated onboarding allow you to get up and running. It will help you get rapid ROI along with digital risk protection, which is tailored as per your organization’s footprint.
- Rapid7 offers several features, such as digital risk protection, Dark Web Protection, IOC management, threat protection, seamless automation, rapid remediation and takedown, expansive threat library, advanced investigating, threat mapping, and more.
Eliminate useless threats coming externally before they create problems in your business by speaking to its experts. Get the free demo that covers your visibility, risk, and response automation.
Silo Web Isolation
Silo Web Isolation by Authentic8 shifts web risks to an isolated cloud-native environment that you can control easily. To meet your demanding requirements, you can configure Silo as per your needs.
The Silo platform offers a secure execution environment for your web-based activities. It is built with the goal of isolating all critical data and web code from the endpoint. It also follows the principles of browsing capabilities that should be auditable and configurable like an enterprise workflow.
Features:
- Silo provides a cloud-based solution, deployable in seconds. It doesn’t require any infrastructure investment; rather, it focuses on scaling that lets IT solve business problems faster.
- Silo is capable of integrating with browsers and workflows using APIs that let IT define a particular experience for the users.
- Unlike traditional security solutions, Silo allows you to deploy software across user populations with just a click. Silo can scale up and down depending on your changes, allowing you to provide the right solutions to your users on time.
- Silo enables you to define access, use policies across locations, web resources, and locations, and authentication. Whether you require a throwaway browser or a locked-down environment, Silo gives control of IT precedented over the web.
- Silo plays intelligently with the IT technology stack, from directory services to secure web gateways, SIEM solutions, and identity management platforms.
- Silo meets all the regulated standards, from federal agencies to healthcare providers and Swiss banks. All data is protected and encrypted to the highest standards.
Whether conducting investigations online or accessing sensitive data, Silo helps you in your mission by crafting an anonymous and secure browsing environment all the time.
Skopenow
Unleash the potential of open-source intelligence with Skopenow and conduct OSINT investigations in your organizations. It builds court-ready, comprehensive, and digital reports instantly on people and businesses.
Skopenow analyzes and collects available information from the data sources, such as the Dark Web, contact data, court records, associated vehicles, and social media.
Features:
- Establish a digital footprint by collating and collecting relevant metadata and information into the automated report, allowing you to start an investigation once your report is loaded.
- Skopenow is a free-to-try application that comes with core features like behavior and object recognition, heat mapping, automated reports, and social media analytics.
- You will get real-time intelligence like the collection, analysis, and sorting of open-source data.
- You can use red flags, including keywords and behaviors. Keep personal information and investigations anonymous and secure while identifying and searching persons of interest.
- Visualize and identify location data easily across your digital presence to provide a frequency-based timeline and heatmap.
- Generate reports that contain all essential and relevant metadata to ensure an easy flow from the computer to the courtroom.
Book a demo to start investing and securing your data.
Webz.io
Webz.io is one of the most robust Dark Web investigation tools, which lets your machines monitor risks with ease and efficiency. It looks out for threats by crawling, indexing, and collecting data from Dark Web networks. In addition, it feeds your machine with data in the required context.

Webz.io crawls forums, sites, marketplaces, etc., in the Dark Web to transform web data into structured and standardized data feeds. It can also extract password-protected or encrypted illicit content, keywords, sites, entities, and more.
Features:
- Webz.io provides a data feed with the profiling of groups, threat agents, and relevant platforms.
- It collects and maintains critical information that helps machines identify and classify to take quick action.
- Gain real-time insights to secure your organizations from cyber risks, such as phishing, ransomware, and cyber attacks.
- Craft an alert system that can detect fraud automatically for leaked card numbers, monitor blockchain addresses, PII, etc.
- Eliminate risk factors, including unlicensed use, leaked information, counterfeiting attempts, and more, to avoid a security crisis.
- Search transactions and cryptocurrency address to trace footprints and follow the money as part of compliance, anti-money laundering, and more.
See Webz.io in real action by talking to an expert and experiencing the real power.
DarkIQ
Monitor and prevent security incidents against your suppliers, people, and brand with actionable alerts from the Dark Web. DarkIQ helps you identify cyber criminals before they attack so that you can prevent security breaches from happening in the first place.

Features:
- DarkIQ is the secret weapon that monitors the dark web continuously for cybercriminal activities. It categorizes, detects, and alerts you to threats so that you can take required action in real time.
- It provides enriched Dark Web data and information to have actionable intelligence. This will reduce unnecessary alerts and false positives so that you can focus on the threats.
- It gives your organization access to Dark and Deep Web marketplaces, onion sites, forums, social chats, phishing sites, domains, CVEs, code repositories, and more.
- DarkIQ offers complete visibility into the Dark Web traffic from the network, which is a key indicator of unwanted activities.
- DarkIQ prioritizes alerts based on dark web intelligence so that it can identify and indicate the real threat.
- It finds Dark Web indicators of the previous breach that might have left you exposed to the next attacks.
- It provides full visibility into Deep and Dark Web exposure of cybercriminals and suppliers that targets third parties to enhance security on the supply chain.
- It helps build threat models based on the intelligence of the Dark Web with its opportunity, intent, and capability of threat groups.
- DarkIQ investigates the chain of events to inform response and mitigation to prevent an attack beforehand.
Illuminate threats and prevent attacks with DarkIQ. See it in action by booking a demo.
Conclusion
It’s easier for cybercriminals or hackers to steal your sensitive information and access your information without your knowledge. They can also upload your personal or organizational data on the Dark Web for personal benefits.
With a reliable and efficient Dark Web investigation tool, you can scan for your information on the Dark Web and maintain online security. The tool can also help you mitigate future risks by providing deeper security visibility with rapid monitoring.
You may also explore what dark data is all about and the best dark web monitoring tools.

