Did you lately get an email from your CEO asking to transfer money to a ‘vendor’? Don’t do it! It’s a CEO fraud or whaling phishing fraud. Whaling phishing is a type of cyber-based attack where CEOs and senior executives are targets. In whaling phishing, an email is sent in an attempt to impersonate the senior official so that money, sensitive information or access can be gained.
Here are some salient points about whaling phishing:
- Through research and social engineering is done through even social media channels
- Personalization of email so that it looks believable
- The style of writing of a senior professional is copied so that the email appears to have originated from a source of authority
In this article, I’ve provided my first-hand experience of CEO fraud and explained how it works with some examples. I have also highlighted how to prevent whaling phishing fraud, after all, awareness is key!
Let’s start this with a little background story.
CEO Fraud happened to me almost two months after I joined Geekflare as a full-time writer.

It wasn’t evident straightaway, as the scamster was using a reputed domain name Virgin Media (caneae@virginmedia.com), and I thought my CEO was somehow connected to this telecommunications company since both are located in the United Kingdom.
So, I responded to the initial ‘I would like to assign you a task, are you free?’ positively. Next, the sender detailed a task encompassing INR 24,610 (~$300) transfer to a vendor, the details of which would’ve been shared had I agreed.
But this made me a little suspicious, and I asked the sender to prove their identity before I could transfer anything. A few emails later, the fraudster called quits, and I sent the conversation to my actual CEO and Virgin Media IT cell.
Though I had no prior training to handle this kind of fraud, I was lucky not to fall into this trap.
But we shouldn’t rely on sheer luck; instead, know this upfront and educate others.
What is CEO Fraud or Whaling Phishing?
What happened to me actually comes under spear phishing, an attack targeted at a particular organization or some of its employees. It will be known as a whaling phishing attack if the target is a high-profile employee (like a c-suite) of any institution.
The Federal Bureau of Investigation, USA, tags these scams under the Business Email Compromise (BEC) or Email Account Compromise (EAC).
Email scams accounted for nearly $2.4 billion in losses in 2021, per the FBI Internet Crime Report.
FBI Internet Crime Report
, which accounted for nearly $2.4 billion in losses in 2021, per this Internet Crime Report.
Geographically, Nigeria is the number one country hosting 46% of CEO frauds, followed by the US (27%) and the UK (15%).
How Does Whaling Phishing Work?

Notably, CEO fraud doesn’t need any technical skills or criminal know-how. All you will get is a random email and social engineering to trick you into sending funds or revealing sensitive details for further course of illicit action.
Let’s check out a few ways bad actors do this ‘currently.’
Examples of Whaling Phishing
Type 1
A random email address imposing as the CEO asking for some money is the simplest form of such trickery. And this one is easy to spot. All you have to look for is the email address (and not the name).
Generally, the domain name (xyz@companyname.com) gives away fraud. However, the email address may indicate a renowned organization (as it was in my case). Here’s a more obviously engineered example.
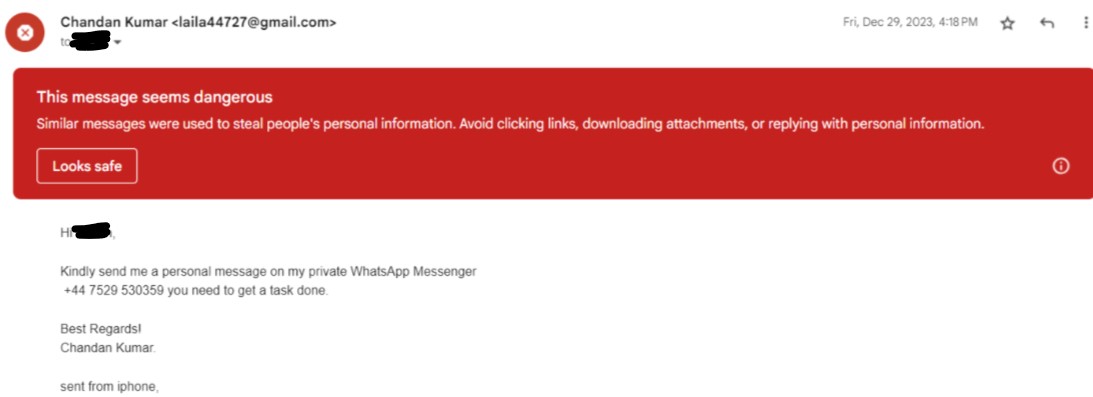
These awards added legitimacy to the scam, which may victimize an uninformed professional. In addition, the email address can look genuine but with slight unnoticeable changes, like @gmial.com in place of @gmail.com.
Finally, it can be from a legitimate but compromised email address, making it extremely tough to detect the scam.
Type 2
Another more sophisticated technique uses video calls. This includes a ‘managed’ email address of a top-ranking official sending ‘urgent’ online meeting requests to its employees, mostly in the finance department.
Next, the participants see an image without audio (or with a deepfake audio) with a claim that the connection isn’t working as expected.
Subsequently, the ‘business executive’ asks to initiate a wire transfer to unknown bank accounts, from where the money gets siphoned off via other channels (read cryptocurrencies) after a successful fraud.
Type 3
This one is a variation of Type 1 but targets business partners and not employees, getting a name–invoice fraud–more suited to its modus operandi.
In this case, an organization’s client gets an email to pay an invoice to specific bank accounts urgently.

This one has the highest success rate as it’s normally pulled off using a hacked company email address. And since email is the way, sometimes exclusively, professionals communicate, it results in huge financial and reputation losses to the target organization.
How to Prevent Whaling Phishing
As an employee, it’s tough to reject a request from your own CEO. This psyche is the prime cause of perpetrators getting success easily with just a random email.

In addition to questioning financial requests, it’s best to ask for a video meeting before ‘cooperating.’
Moreover, in most cases, you just need to check the email address carefully. This may not belong to your organization or may have misspelled versions of the company name.
Besides, an institution can’t register all domain extensions. So, you need to beware of getting an email from [email protected] when the official address should be [email protected].
Lastly, you might be receiving emails from a company address operated from ‘outside’ or a rogue internal member. The key to such a situation is verbal confirmation or keeping multiple executives in the loop before making any payments.
And the most effective way to protect your organization, if you lead one, is incorporating phishing simulation in routine employee training. Because these fraudsters constantly evolve. So, giving a single, one-time warning won’t help your employees much.
Wrapping Up!
Unfortunately, we depend heavily on business emails, leaving big loopholes criminals often exploit.
While there isn’t a substitute for this form of communication yet, we can add business partners on applications such as Slack or even WhatsApp. This will help quickly confirm if anything seems suspicious and avoid such setbacks.
PS: If I were you, I would not miss this article covering types of cybercrimes for added internet literacy.

