You can do some crazy hacking stuff just by searching on Google! 🤯
Yes, you heard that right. It is called Google Hacking or Google Dorking.
As a content writer, I have used Google Dorks several times for SEO and research purposes. It helps me find specific posts from my competitors and lock down underserved topics for my content strategy.
Similarly, you can use the Google Dorking commands as per your requirement.
However, before diving into Google Dorking, you must understand various terminologies such as Dorks, Recon, and much more. Also, you need to know where to draw the line.
Google Dorking is not illegal as long as the information collected is used for research purposes. If you use the collected information to blackmail the “target,” Google Dorking can quickly head into the realms of illegal activity⚠️.
And Google doesn’t like that. It even penalizes the IP address from where the Dorking commands are coming. And you can face a criminal charge, too, so beware.
So, in this Google Dorking, aka Google Hacking guide, I’ll share everything you need to know about this amazing ethical hacking technique and how to use it to your advantage.
What is Google Dorking?
Google Dorking is a search technique to find information not generally shown in Google search results. It is done using advanced search operators and strings called dorks.
In other words, Google Dorking is a backdoor to bypass the Google algorithm to find information not displayed on Google’s search engine results – for example, a particular company’s admin page or a login page.
You can even find confidential documents, such as PDFs, excel sheets, etc., using appropriate Google Dorking commands.
If used in good faith, Google Dorking can help you find specific documents or web pages – filtering out irrelevant search results and saving time.
However, if used in bad faith, it can help hackers access data and files of a specific company or an individual that are unsecured or accidentally uploaded to the internet.
Thus, to dork or not to dork depends on how accountable you can be too!
How Google Dorking Works?
Individuals like you and me can use Google Dorking for research purposes. However, it is mostly used by cybersecurity experts to understand the loopholes in the system. These are mostly ethical hackers, also known as white-hat hackers.
Even black-hat hackers use Google Dorking to identify websites with security vulnerabilities. They find sensitive data and files about their “targets” and use them maliciously.
(Mr. Robot fan, anyone? 😃)

Since the early 2000s, search engines have been used as a tool for Google Dorking. And Google’s widespread web crawling capabilities facilitate Dorking.
With the right Google Dork query, attackers can access a lot of information they couldn’t get with simple Google searches. This information includes the following:
- Passwords and usernames
- Email address lists
- Confidential documents
- Personally identifiable information – financial, demographic, location, etc.
- Website vulnerabilities
According to Norton Statistics, nearly 88% of businesses witness a cybersecurity attack within a year. This means businesses are targeted almost every day.
Ethical hackers use the collected information to fix the vulnerabilities in their systems, but unethical hackers use it for illegal activities, such as cybercrime, cyberterrorism, industrial espionage, identity theft, and cyberstalking.
Hackers may also sell this data to other criminals on the dark web for large sums of money. Here are the phases of how a hacker uses Google Dorking methods to steal personal information:
#1. Reconnaissance
The first stage in hacking is collecting as much information as possible about the target. From confidential documents to usernames and passwords, all the hackers can find. This stage is also known as recon, footprinting, or even fingerprinting.
Google Dorking is a way of passive recon, meaning hackers access publicly available files online.
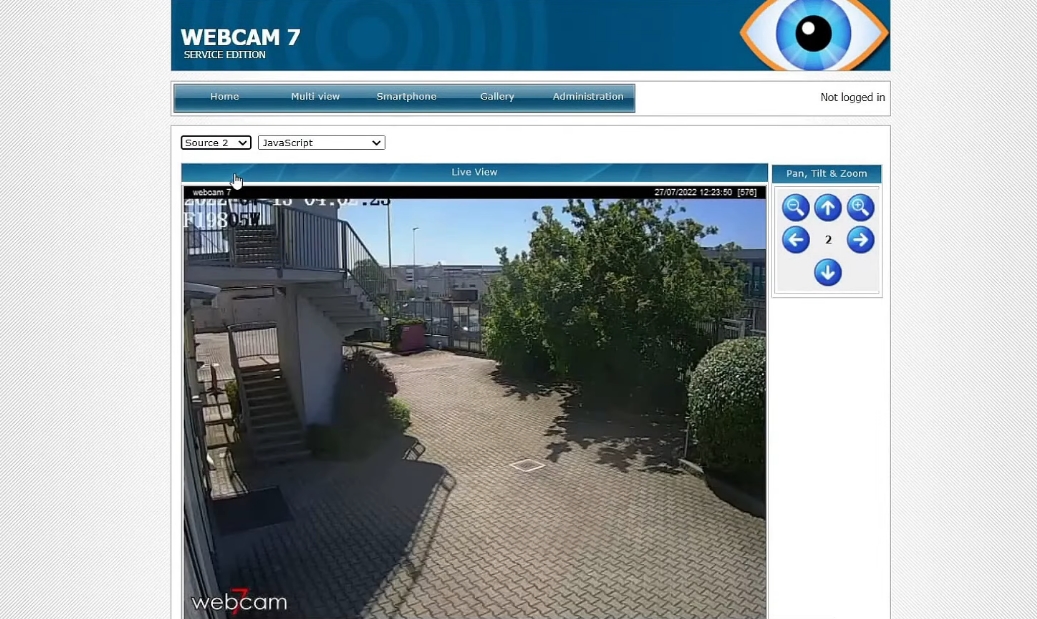
The publicly available files could be accidentally made online. For example, they accidentally uploaded a PDF file containing usernames and passwords or left their webcams open to the internet.
#2. Scanning
At this stage, the hacker has collected the data – web page URLs, PDFs, excel sheets, email lists, etc. The hacker will scan it by opening and reading the files, cleaning the links, or using a scanning tool to find the information wanted.
#3. Gaining Access
At this stage, the hacker uses the collected information and gains access to the system/database.
#4. Maintaining Access
The hacker establishes a connection (temporary or permanent) with the system/database to reconnect to the target, if and when needed, easily.
If the connection breaks or the hacker wishes to return to the system/database later, they can do so using this connection.
#5. Exit
At this stage, the hacker clears their tracks and exits the system/database without a trace. The hacker removes all exploits and back doors and clears the logs.
Legality of Google Dorking
As I mentioned, Google Dorking is not illegal if used only for research purposes.
In fact, only phase 1 (reconnaissance) comes under the definition of Google Dorking, i.e., searching for information using advanced search strings and operators.

The moment you click on the search results, access a URL, download a document, or access links without proper permission, you enter phase 2.
Beyond this phase, you may be accountable for computer crimes punishable by law.
So, click with caution and good faith👍.
Furthermore, to Google Dork, you use advanced dork queries and search strings to filter out the irrelevant results and find exactly what you want.
Google Dork Query – Meaning & Examples
Some common query operations in Google Dorking can help you find specific information while filtering out irrelevant results.
I use some of these Google Dork queries – such as allintitle, inurl, filetype, etc. – all the time when doing SERP analysis for a topic. This helps me put down the exact content strategy for that particular topic.
I will share some of the most common and useful Google Dork queries. I will share the query’s function, results, and how to use the findings to your advantage. Here are some of the most common operators used in Google Dorking.
#1. Site
If you want to look for webpages of only a particular website, you can use the query operator site:. This query restricts your search to a particular website, top-level domain, or subdomain.
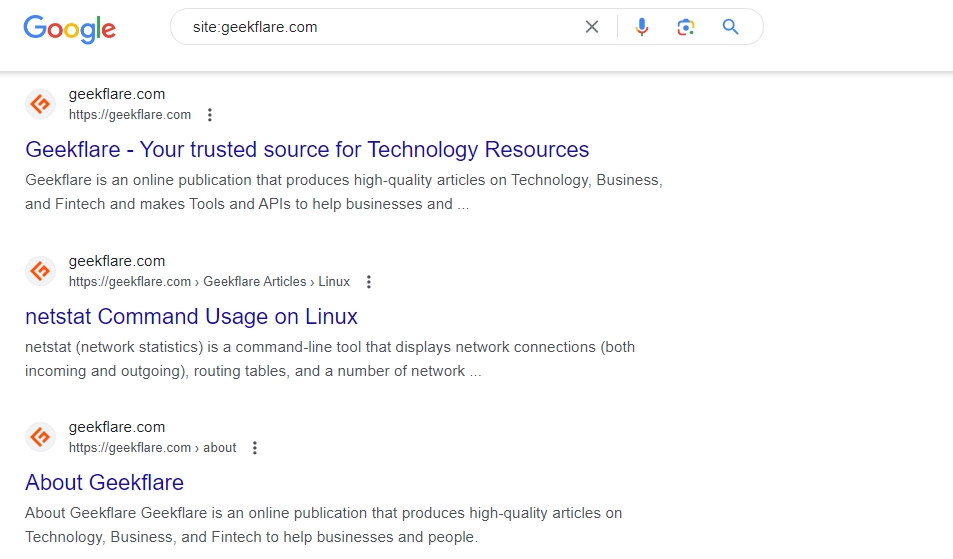
This query will show you the public web pages of that particular website, top-level domain, or subdomain. You can even combine this query with other queries to get even more specific with your search results.
#2. Intitle/Allintitle
Inserting your primary keyword in your SEO title (aka meta title) is one of the most age-old and effective SEO practices. So, using the intitle: dork query, you can find particular webpages with keywords in their SEO titles.
You can even combine it with site: query to get even specific results. For example, if you want to find articles on Geekflare but only about Windows 10, you can enter this dork query.
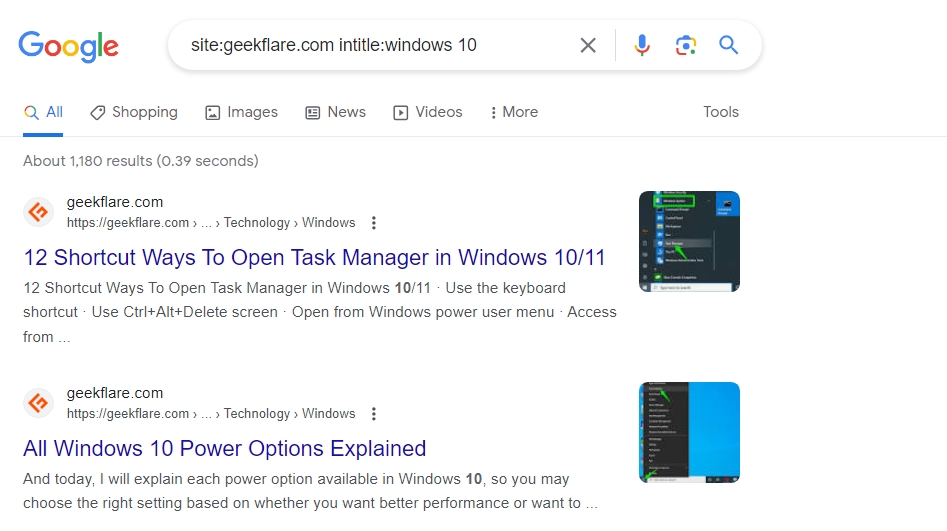
This Google Dorking method is really useful when you want to find results around a specific search term. If you combine it with other queries, you can drastically improve your SERP analysis.

Alternatively, you can also use the dork query allintitle: if you have multiple search terms and want all of them in the title of the results. Then, you can use allintitle: query instead of intitle:.
#3. Inurl/Allinurl
The inurl: dork command is very similar to intitle: command. The only difference is that this query looks for a particular search term in the URLs of the websites.

Alternatively, you can even use allinurl: Dorking query to find URLs with multiple search terms. This query will give you URLs with all the search terms present in it.
For example, the primary keyword in the URL and an optimized URL structure are essential for ranking on Google. So, if I am a new Digital Marketing Agency in New York and want to see my local competition, I can easily do so using the allinurl: command.

You can even include an additional operator like “- (minus)” to exclude results from a particular source. You can do the same with allintitle: query. Here’s an example:
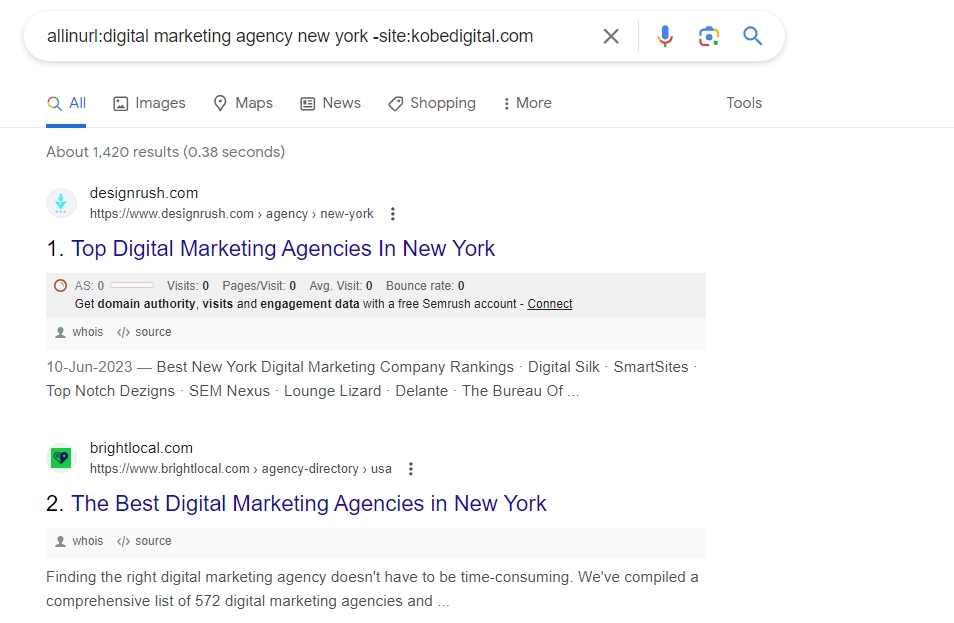
The inurl:/allinurl: dork query can be really useful to estimate how many web pages you will be fighting for to rank for that particular search term and, most importantly, the domain authority you need to rank for that search term.
#4. Intext
The intext: Dork query finds websites/webpages with the search term in their texts. It is really useful for SEO experts to find competitors’ web pages with the search term – a certain keyword.

You can even use an additional operator like quotation marks (“”) to find the webpages with exact search term in their body text. You can combine it with the site: query to find results of a particular website.
It is one of the Google search tricks that most SEO experts use. 😉
#5. Filetype
Using the filetype: search operator, you can find files such as PDFs, XLS, Doc, etc.. This search query is extremely useful if you are looking for specific reports, manuals, or studies.
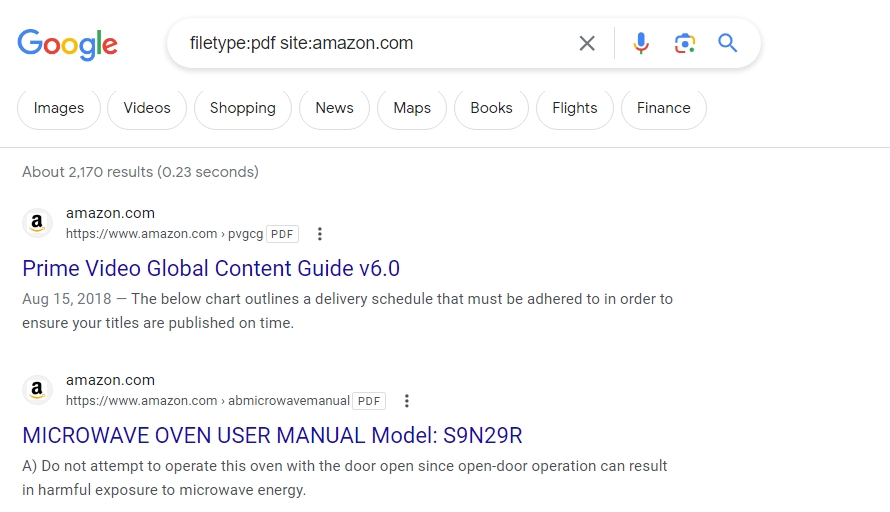
In Google Dorking, filetype: command is one of the most-used commands by hackers to find accidentally leaked and confidential documents. These documents might contain sensitive information such as IP addresses, passwords, etc.
Hackers use this information for penetration testing (pentesting) and to bypass paywalls to access resources.
#6. Cache
Using the Cache: command, Google Search will fetch the last saved copy of a particular website (Google cache) if it exists. It’s useful for rediscovering a website before its downtime or latest update.
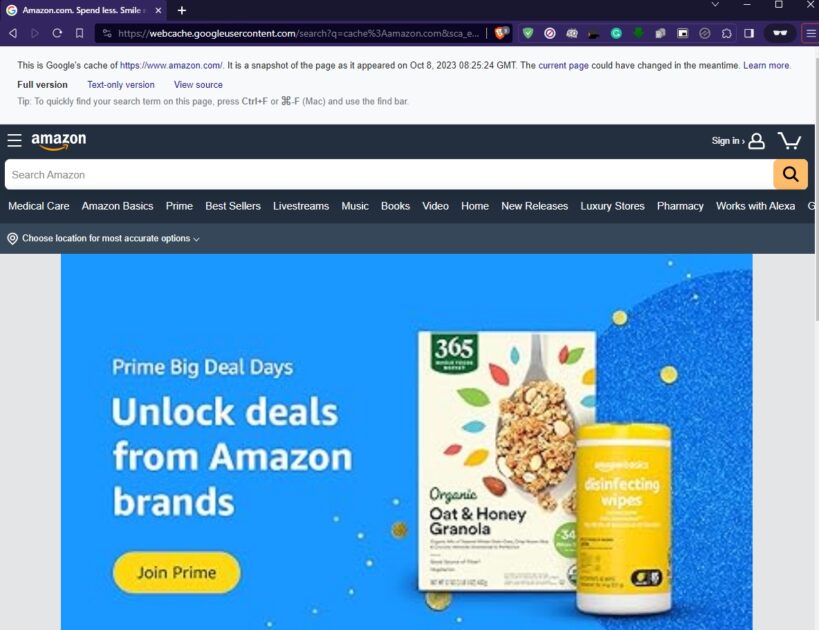
Whenever a user accesses a website using Google, a cached version of that page is created in Google’s system. You can access this cached version using the cache: command if the original website is temporarily down or you want to view an older version of the website.
#7. Link
The link: Google Dork query is helpful if you want to find which web pages link to a specific URL.

If you want to analyze the backlinks pointing to your website, you can use tools like Semrush or Ahrefs.
However, if you don’t want to invest in a backlink analytics tool, then this Google Dorking method is a free and useful way to analyze where your backlinks are coming from.
#8. Map
Using the map: Dorking command lets you find a map of the given location. Google Search will show you the map directly instead of the web pages.

On macOS, you may see a prompt to open the Maps application. This query is useful to find a particular location’s map quickly.
Google Hacking Database is a repository where users post various search operator strings that you can use to get started with Google Dorking.
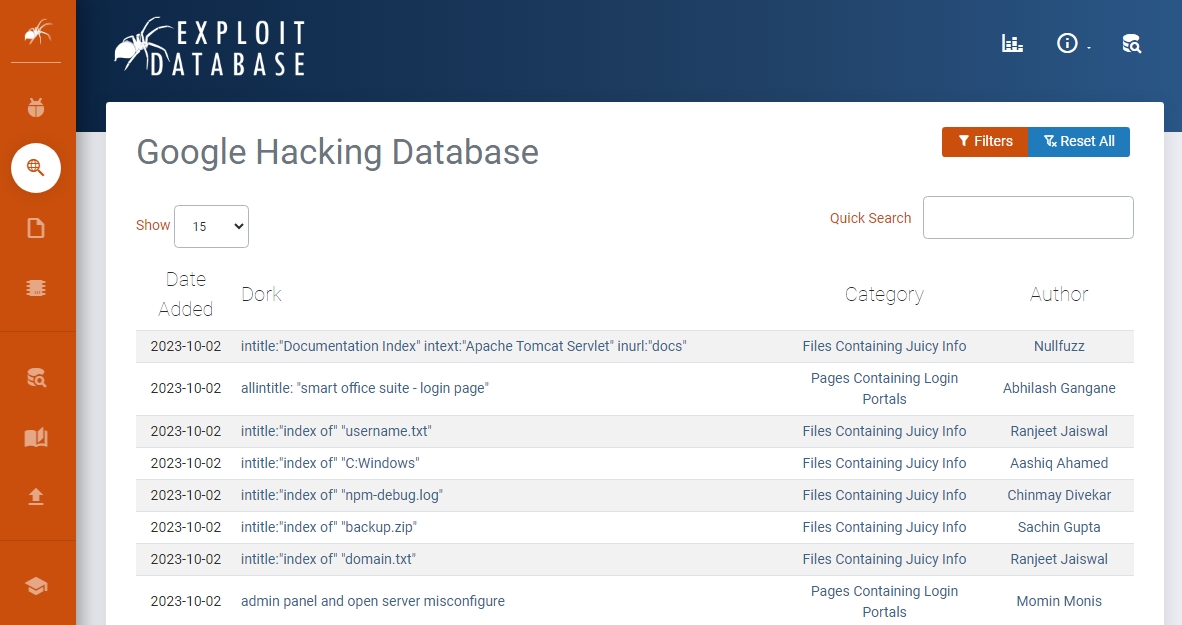
However, I recommend you use these search strings cautiously because some of these strings lead to webcams and corporate company login pages.
How to Protect Yourself from Google Dorking?
Whether you’re an individual or a business, you must protect yourself from Google Dorking. You can take the following steps to ensure that your data on the internet is safe.
- Ensure that the private pages and documents are password-protected.
- Implement IP-based restrictions.
- Encrypt sensitive information – usernames, passwords, email IDs, phone numbers, etc.
- Find and disable Google Dorks using vulnerability scanning tools.
- Do regular dork queries yourself on your websites to find and fix the loopholes before the attackers find them.
- Use Google Search Console to remove sensitive content from your website
- Use robots.txt file to hide and block bot access to sensitive files.
Although 100% internet security is a myth, you can implement the steps to minimize the chances of falling prey to unethical hacking.
Google Dorking Penalties by Google
Google Dorking can give you immense information by filtering out unnecessary or unrelated search results. However, if used unethically, it can gather the attention of law enforcement authorities.
Most of the time, Google will warn you when you overdo the Dorking. It will start verifying your search queries. If you still go overboard, Google can even ban your IP address.
To Dork or Not to Dork?
In this Google Dorking guide, we discussed everything about this powerful search technique that allows you to find specific information and publicly exposed vulnerabilities. For penetration testers, it’s their everyday job.
Also, with the Google Hacking Database, you get a collection of pre-made Google Dorks. However, I’d again like to remind you to use Dorking ethically and with permission.
Follow ethical guidelines and request permission when using Dorking for security audits.
If ethical hacking is up your alley, you should also check out how to become a bug bounty hunter in 2023?

