Have you ever thought of outplaying hackers in their own game? Or perhaps you are tired of defending against bad tech guys. In either case, it is time to consider using honeypots and honeynets.
When talking about honeypots, you refer to specially designed computer systems that lure attackers and record their moves. Think of this as an intelligence collection system.
Currently, there are over 1.6 million sites today. Hackers continuously scan through internet addresses for poorly protected systems. A honeypot is a deliberately vulnerable possible hacker destination invoking penetration yet fully instrumented. If the attacker penetrates your system, you learn how they did it and equip yourself with the latest exploits imposed on your organization.
This article builds on honeypots and honeynets, diving into its core to educate you on this cybersecurity domain. By the end, you should have a solid understanding of the area and its role in security.
Honeypots aim to deceive the attacker and learn their behavior to improve your security policies. Let’s dive in.
What Is a Honeypot?
A honeypot is a security mechanism used to set traps for attackers. So, you intentionally compromise a computer system to allow the hacker to exploit security vulnerabilities. On your end, you are keen to study the attacker’s patterns and thus use the newly acquired knowledge to influence the security architecture of your digital product.
You can apply a honeypot to any computer resource, including software, networks, file servers, routers, etc. Your organization’s security team can use honeypots to investigate cybersecurity breaches gathering intel on how cybercrime is conducted.
Unlike traditional cybersecurity measures that attract legitimate activity, honeypots reduce the risk of false positives. Honeypots vary from one design to another. However, they will all narrow down to looking legitimate, vulnerable, and attracting cybercriminals.
Why Do You Need Honeypots?
Honeypots in cybersecurity have two primary uses, research and production. Most often, honeypots will balance rooting out and collecting information on cybercrime before legitimate targets are attacked while still luring attackers away from real targets.
Honeypots are efficient and cost-saving. You will no longer need to spend time and resources hunting for hackers but await hackers to attack falsified targets. Consequently, you can watch attackers while they think they have penetrated your system and are attempting to steal information.
You can use honeypots to evaluate the latest attack trends, map out original threat sources, and define security policies mitigating future threats.
Honeypots Designs
Honeypots are classified according to their aims and levels of interaction. If you look at the aims of honeypots, you can see that there are two designs: research and production honeypots.
- Production Honeypot: Deployed in production alongside servers. This class acts as the front-end trap.
- Research Honeypot: This class is tied explicitly to researchers and is used for analyzing hacker attacks and guiding on techniques to prevent these attacks. They educate you by containing data that you can trace back when stolen.
Next, we will explore types of honeypots.
Types of Honeypots
Different honeypots can be set up, each with a thorough and effective security strategy based on the threat you want to identify. Here is a breakdown of the available models.
#1. Email Traps

Alternatively known as spam traps. This type places fake email addresses in a hidden location where only automated address harvesters can find them. Since the addresses aren’t used for any other role than in the spam trap, you are sure that any email coming to them is spam.
All messages with content resembling that of the spam trap can be automatically blocked from the system, and the sender’s IP address added to the deny list.
#2. Decoy Database
In this method, you set up a database to monitor software vulnerabilities and attacks exploiting insecure architectures, SQL injections, other service exploitations, and abuse of privilege.
#3. Spider Honeypot
This class traps web crawlers (spiders) by creating crawler-only accessible websites and web pages. If you can detect crawlers, you can block bots and ad-network crawlers.
#4. Malware Honeypot

This model mimics software programs and application interfaces (APIs) to invoke malware attacks. You can analyze the malware characteristics to develop anti-malware software or address vulnerable API endpoints.
Honeypots can also be viewed in another dimension based on interaction levels. Here’s a breakdown:
- Low interaction honeypots: This class gives the attacker some small insights and network control. It stimulates frequently requested attacker services. This technique is less risky since it does include the primary operating system in its architecture. Although they need little resources and are easy to deploy, they are easily identifiable by experienced hackers and can avoid them.
- Medium interaction honeypots: This model allows relatively more interaction with hackers, unlike the low interaction ones. They are designed to expect certain activities and offer particular responses beyond what the basic or low interaction would.
- High interaction honeypots: In this case, you offer the attacker many services and activities. As the hacker takes time to bypass your security systems, the net gathers information about them. Therefore, these models involve real-time operating systems and are risky if the hacker identifies your honeypot. Although these honeypots are expensive and complex to implement, they provide a broad scope of information about the hacker.
How Do Honeypots Work?
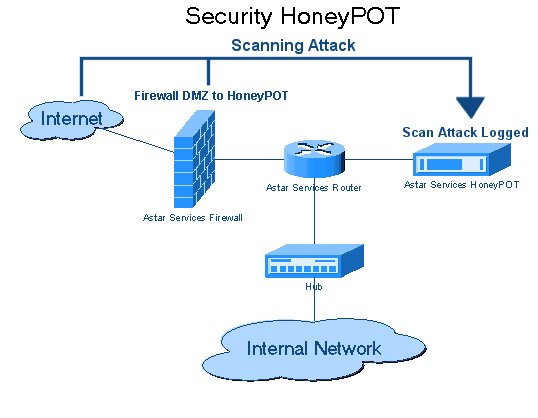
Compared to other cybersecurity defense measures, honeypots aren’t a clear defense line but a means to achieve advanced security on digital products. In all ways, a honeypot resembles a genuine computer system and is loaded with applications and data that cybercriminals deem ideal targets.
For instance, you can load your honeypot with sensitive dummy consumer data such as credit card numbers, personal information, transaction details, or bank account info. In other cases, your honeypot may take after a database with dummy trade secrets or valuable information. And whether you use compromised information or photos, the idea is to lure attackers interested in collecting intel.
As the hacker breaks into your honeypot to access the decoy data, your information technology (IT) team observes their procedural approach to breaching the system while noting the various techniques used and the failures and strengths of the system. This knowledge is then used to improve the overall defenses strengthening the network.
To lure a hacker into your system, you must create some vulnerabilities they can exploit. You can achieve this by exposing vulnerable ports that provide access to your system. Unfortunately, hackers are also smart enough to identify honeypots diverting them from real targets. To ensure your trap works, you must build an attractive honeypot that draws attention while seeming authentic.
Honeypot Limitations
Honeypot security systems are limited to detecting security breaches in legitimate systems and do not identify the attacker. There is also an associated risk. If the attacker successfully exploits the honeypot, they could proceed to hack your entire production network. Your honeypot must be successfully isolated to prevent the risk of exploiting your production systems.
As an improved solution, you can combine honeypots with other technologies to scale your security operations. For example, you can use the canary trap strategy that helps leak information by sharing multiple versions of sensitive information with whistleblowers.
Advantages of Honeypot
- It helps upgrade your organization’s security by playing defensive, highlighting your systems’ loopholes.
- Highlights zero-day attacks and records the type of attacks with the corresponding patterns used.
- Diverts attackers from real production network systems.
- Cost-effective with less frequent maintenance.
- Easy to deploy and work with.
Next, we will explore some of the disadvantages of Honeypot.
Disadvantages of Honeypot
- The manual effort required to analyze traffic and collected data is exhaustive. Honeypots are a means of gathering intel, not handling it.
- You are limited to identifying direct attacks only.
- Risks exposing attackers to other network zones if the honeypot’s server is compromised.
- Identifying the hacker’s behavior is time-consuming.
Now, explore the dangers of Honeypots.
Dangers of Honeypots

While the honeypot cybersecurity technology helps track the threat environment, they are limited to monitoring activities in the honeypots alone; they do not monitor every other aspect or area in your systems. A threat may exist, yet not directed to the honeypot. This operation model leaves you with another responsibility to monitor other system parts.
In successful honeypot operations, honeypots deceive hackers that they have accessed the central system. However, if they identify its honeypots, they could avert to your real system leaving the traps untouched.
Honeypots vs. Cyber Deception
The cybersecurity industry often uses “honeypot” and “cyber deception” interchangeably. However, there is a key difference between the two domains. As you have seen, honeypots are designed to lure attackers for security reasons.
In contrast, cyber deception is a technique using false systems, information, and services to either mislead the attacker or trap them. Both measures are helpful in security field operations, but you can consider deception an active defense method.
With many companies working with digital products, security professionals spend significant time keeping their systems attack free. You can imagine having built a robust, safe, and reliable network for your company.
However, can you be sure that the system cannot be breached? Are there weak points? Would an outsider get in, and if they did, what would happen next? Worry no more; honeynets are the answer.
What Are Honeynets?
Honeynets are decoy networks containing collections of honeypots in a highly monitored network. They resemble real networks, have multiple systems, and are hosted on one or a few servers, each representing a unique environment. For instance, you can have windows, a Mac, and a Linux honeypot machine.
Why Do You Need Honeynets?
Honeynets come as honeypots with advanced value-added features. You can use honeynets to:
- Divert intruders and collect a detailed analysis of their behavior and operation models or patterns.
- Terminate infected connections.
- As a database that stores large logs of login sessions from which you can view attackers’ intentions with your network or its data.
How Do Honeynets Work?

If you want to build a realistic hacker trap, you agree it isn’t a walk in the park. Honeynets rely on a series of elements that work together seamlessly. Here are the constituent parts:
- Honeypots: Specially designed computer systems that trap hackers, other times deployed for research, and occasionally as decoys that lure hackers from valuable resources. A net is formed when many pots come together.
- Applications and services: You must convince the hacker that they are breaking into a valid and worthwhile environment. The value needs to be crystal clear.
- No authorized user or activity: A true honeynet only traps hackers.
- Honeywalls: Here, you are aiming to study an attack. Your system must record the traffic moving through the honeynet.
You entice the hacker into one of your honeynets, and as they attempt to move deeper into your system, you begin your research.
Honeypots vs. Honeynets
Below is a summary of the differences between honeypots and honeynets:
- A honeypot is deployed on a single device, while the honeynet needs multiple devices and virtual systems.
- Honeypots have a low logging capacity, while honeynets have a high.
- The hardware capacity needed for the honeypot is low and moderate, while that of the honeynet is high and needs multiple devices.
- You are limited with the honeypot technologies, while honeynets involve multiple technologies like encryptions and threat analysis solutions.
- Honeypots have low accuracy, while honeynets have high.
Final Words
As you have seen, honeypots are single computer systems resembling natural (real) systems, while honeynets are collections of honeypots. Both are valuable tools for detecting attacks, collecting attack data, and studying the behavior of cyber security attackers.
You have also learned about honeypot types and designs and their roles in the business niche. You are also aware of the benefits and associated risks. If you are wondering which overpowers the other, the valuable part is the greater one.
If you have been worrying about a cost-effective solution for identifying malicious activity in your network, consider using honeypots and honeynets. If you want to learn how the hack works and the current threat landscape, consider following the Honeynet Project keenly.
Now, check out the introduction to cyber security basics for beginners.


