Find Node.js security vulnerabilities and protect them by fixing them before someone hacks your application.
There are some online tools to help you find the common security vulnerability in PHP, WordPress, Joomla, etc, but here lies the twist! they may not be able to detect if your application is built on Node.js.
One of the recent findings suggests that more than 80% of users found their Node.js application vulnerable.

These vulnerabilities, which could be of hundreds of types considerable once, are due to misconfiguration, outdated NPM packages, etc., and the following security scanner should be able to help you in finding the security escape clause.
This article explains how to find Node.js Security vulnerabilities and secure them before someone hacks your application.
I would also like to highlight that this article focuses on tools to find a vulnerability. I would suggest checking out “How to Secure Node.js from online threats” for configuring security protection.
Snyk
Snyk is a handy option for finding vulnerabilities in containers, code dependencies, and infrastructure as code. Whether it’s development tools, automation pipelines, or Workflow, Snyk integrates directly!
In the recent update, Snyk has included SPDX v3.20. The level of detail will improve, but the number of license detections should remain the same. Additionally, it supports npm lockfile v3 projects.
Don’t think! It’s the end! It has some more advantages, including,
- With Snyk, you will be on alert by getting notifications of new vulnerabilities.
- It will help you to prevent adding more dependencies.
The fun fact here lies that, If you deploy your Node.js application in a container, you might also be adding insecure packages. The Snyk Container CLI can assist you in identifying a base image that reduces your application’s attack surface.
NodeJSScan
In technical terms, NodeJSScan is a static security code scanner (SAST) specially developed for Node.js. The language it is based on is Python. This tool is supported by libsast, a generic SAST for security engineers, and semgrep, an open-source and the fastest static analysis engine for finding vulnerabilities in third-party dependencies.

To run nodejsscan, you have the command in hand, i.e., ./run.sh. This command will help you run the nodejsscan web user interface at http://127.0.0.1:9090.
Coming to its Integration, you can create Slack or email alerts for notifications regarding vulnerabilities.
Overall, it can find vulnerabilities and make your application more secure. It depends on your wise selection of the tool which can help you fight security loopholes. I would suggest Node JS Scan is a viable option.
AuditJS
If you are searching for a perfect vulnerability finder, start building your trust in AuditJS. AuditJS has a special OSS Index v3 REST API sword to identify known vulnerabilities. It can locate outdated package versions as well.
AuditJS supports npm, Angular, yarn, and Bower package managers for projects with dependencies installed in the node_modules folder.

The installation process includes several ways, like via npx, which offers the least permanent installation, and the command for it is “npx auditjs@latest ossi,” or you can opt for global install, which provides the most permanent installation, and the command for it is “npm install -g auditjs”.
After my review, I would suggest installing via npx installation. Global installations are generally discouraged in the Node.js community.
Detectify
Detectify is another tool to find vulnerabilities in your web application. It has recently earned a name in the market and emerged as a reliable option. It offers continuous scanning to test your apps for the latest vulnerabilities. It also supports the scheduling of scans to be parallel with your convenience.

I guess you may find it a bit out of the box; you can create integrations with customizable parameters and send critical security findings to the tools you use daily.
Finally, I would also like to highlight another feature that it offers: a complete overview of all vulnerabilities regardless of their asset.
MegaLinter
MegaLinter is considered one of the most efficient tools for avoiding technical debt, and this tool helps us deliver clean and productive code so that users can consume time during the workflow.
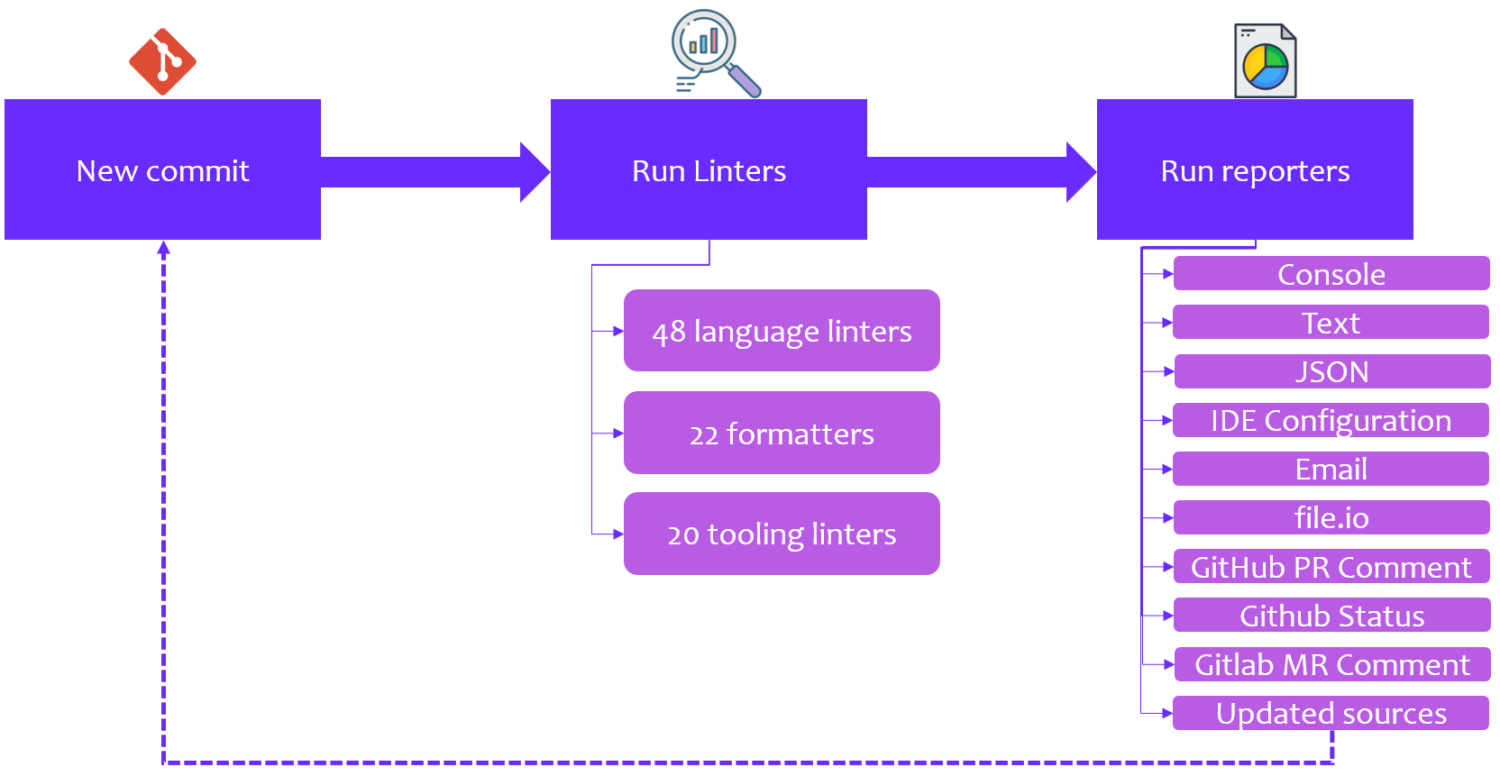
MegaLinter helps us follow best practices regarding code review as the following tool allows coders to update and analyze code on each pull request automatically. It mainly helps optimize the process of code review, enabling users to save a massive amount of time.
However, in terms of verifying error logs, MegaLinter helps developers to practice some best techniques; as a result, they can efficiently execute significant code errors without any failure.
Along with all such significant factors, this tool also provides a list of IDE plugins that helps developers to install required plugins to perform various tasks efficiently.
Apart from all such multiple aspects, one of the significant features of this tool is that it is entirely open source and free for every developer.
This tool is independent as it does not require any external application; it works efficiently on any CI tool, and we can also use it on our local system. However, this tool is compatible with every programming language.
As a result, any developer can easily switch to MegaLinter to maintain a clean and error-free coding environment. Below we present a detailed video description of how to use the following tool:
RetireJS
There are various tools to establish trust; here comes the next one: RetireJS. Developers should understand that simplifying development is admirable, but you must stay up-to-date on security fixes.
RetireJS Team has a clear understanding and vision to help their users detect known vulnerabilities. RetireJS is based on JavaScript, TypScript, and Shell. There are various ways you can use RetireJS,
- As CLS (Command Line Scanner)
- As GP (Grunt Plugin)
- As GT (Gulp Task)
- As Web Browser Extension
Browser Extension is mentioned above in the list of usage procedures of RetireJS! The thing to be highlighted here is these Extension scans for insecure libraries and put warnings on the developer’s panel. These small features, combined with several others, make RetireJS one of the best options for finding vulnerabilities in your Node.JS Application.
eslint-plugin-security
The next on the list is Eslint-Plugin-Security. It is specially made for Node Security. This tool will help you find and identify vulnerabilities with ease. The installation process gives you two options: npm or yarn!
npm install –save-dev eslint-plugin-security
yarn add –dev eslint-plugin-security
During my go-through, I found some false potential threats that human intervention can bypass. After all the necessary check-ins, eslint-plugin-security holds a particular spot because of its specialty for Node.js.
Node-Secure CLI
Node-Secure CLI tool is a dependable option for Node.js vulnerabilities. The team has developed a CLI/API which can thoroughly analyze the dependency tree of a given local package.json or npm package and track down the loopholes in the repository.

During the usage, you may find nodes are red in UI. But, I suggest not to be worried. This happens only when the package has been flagged with haswarnings or hasMinifiedCode
Node-Secure CLI offers a lot of features, among them some have been listed below,
- AST Analysis – You can run it on each .js/.mjs file in the packages.
- Complete Analysis – It will provide you with the entire composition for every package.
- Strong Coverage – This tool allows you to analyze npm packages and local node.js projects.
From the overall look and feel of this tool, I believe, with its ability to track and analyze vulnerabilities. Developers can proactively identify and address potential vulnerabilities.
Conclusion
The above tools should help scan your node.js application for a security vulnerability so you can secure them. On top of protecting core Node.js applications, you should also consider using WAF to protect from online threats and DDoS attacks.

