Lattice-based cryptography technique is an excellent method of securing information using a series of mathematical formulae.
Cryptography comes in multiple flavors. In general, it uses a series of codes to encrypt your data.
For the longest time, cryptographic tools like encryption schemes followed ad-hoc designs. Security was completely based on heuristics and intuition.
Also, codes are easier to break; hence, securing data is a question for those who are using code-based security designs.
Another problem is that existing standards of cryptography are not that reliable. The development of quantum computers can further break the standards, resulting in an increased feat among users.
Therefore, encrypting personal information is essential for everyone. Subsequently, there was a requirement for a new idea or technique that no one could break. We needed improved standards that can secure data even after using quantum computers.
After a lot of brainstorming, a new method has evolved, i.e., Lattice-based Cryptography.
In this article, I’ll discuss lattice-based cryptography, its importance, how it works, and more.
Here we go!
What Is Cryptography?

Cryptography is a technique of securing communications and information using a wide range of codes so that the information can be read and processed by those for whom they are intended. This will prevent unauthorized access to the data.
The term “cryptography” is created by combining two words – crypt and writing.
Here, “crypt” means “hidden” and “graphy” means “writing”.
The methods used to protect your information are obtained from different mathematical concepts and some rule-based calculations, i.e., algorithms to turn messages into a hardcore problem that seems to be difficult to decode.
There are three types of Cryptography:
- Symmetric Key Cryptography: It is a type of encryption system that allows the sender of a message and its receiver to use a single key to code and decode messages. This method is simpler and faster.
- Hash Functions: In this algorithm, you don’t need any key. A hash value is calculated as plain text, which is difficult for contents to be recovered. Various OS use this method to encrypt passwords.
- Asymmetric Key Cryptography: Under this technique, a pair of keys has been used to code and decode information – one key for encryption and another key for decryption. The first key is public, but the second key is a private key that only the receiver knows.
What’s Lattice-Based Cryptography?
Lattice-based cryptography is a simple term used for the building of cryptographic algorithms that involve lattices. It is used for post-quantum cryptography to secure information. Unlike known-public schemes, lattice-based schemes are more resilient and can withstand attacks from quantum computers.
Now, if you are wondering what a lattice is in the context of lattice-based cryptography, let me make that clear for you.
A lattice resembles a grid as in graph paper that uses a set of points located in a criss-cross way. This is not finite; instead, a lattice defines a pattern that keeps continuing infinitely. A set of points is known as a vector where you can add numbers in any integer multiples. The hard part is finding the points from this infinite grid that are close to some point, let’s say 0.
Additionally, lattice-based cryptography uses complex mathematical problems to encrypt the data, making it difficult for attackers to solve these kinds of problems and steal data.
Talking about its history, lattice-based cryptography was first introduced by Miklos Ajtai in the year 1996, whose security was based on lattice problems.
In 1998, Joseph H. Silverman, Jill Pipher, and Jeffrey Hoofstein introduced a lattice-based public key encryption scheme. However, the encryption scheme is not that hard to solve. Finally, in 2005, Oded Regev introduced the first public key encryption scheme that is proven to withstand even in the worst-case scenario.
Since then, the follow-up work has continued to improve the efficiency of the original encryption scheme. In 2009, Craig Gentry came up with the first homomorphic encryption scheme based on complex lattice problems.
Examples: CRYSTALS-Dilithium (digital signature algorithm) and CRYSTALS-KYBER (public key encryption and key establishment algorithm).
How Does Lattice-Based Cryptography Work?
To understand the working principle of lattice-based, let’s dive into some important terms:
- Lattices: Lattices are basically thought of as a regular-spaced grid of a set of points that are infinite in number.
- Vector: A vector is the name of a point, and the numbers on it are called coordinates. For example, (2,3) is a vector having two coordinates – 2 and 3. A lattice is a collection of these vectors in an infinite series.
- Basis: Lattices have large objects, but computers have a finite amount of memory. So, mathematicians and cryptographers thought of a succinct way to use lattices. So, they use the “basis” of a lattice. It is a collection of vectors used to present any point in the lattice grid that forms a lattice.
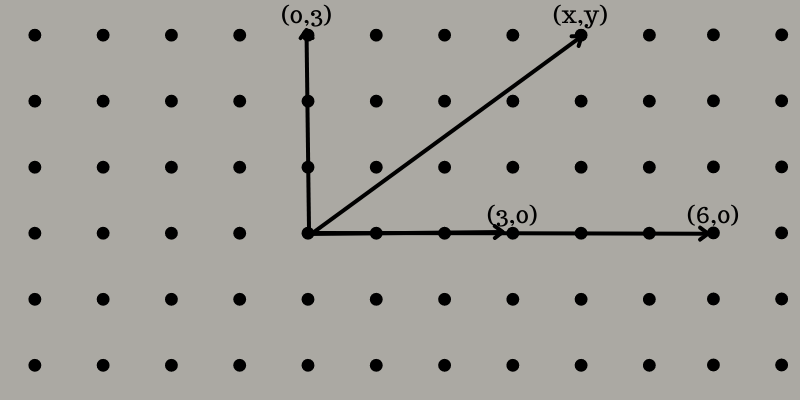
Now, let’s take a 2D lattice as an example to understand the concept easily. Here, you will find a grid of points on a flat surface like a piece of paper. Let’s choose two or more points that are not a single line going through the origin.
For example, you choose (3,0) and (0,3). To generate the third point using these points, you need to choose two whole numbers, like 2 and -1. Multiple the coordinates of (3,0) by 2 to get (6,0) and (0,3) by -1 to get (0, -3). Add the result points to get (6,-3).
With this method, you can generate the entire grid of points, evenly spaced from each other vertically and horizontally. You can name the coordinates as (x,y), where you see x and y are even numbers, including 0.
Lattices are classified into three categories:
- Aperiodic: An aperiodic lattice is a pattern that doesn’t repeat exactly, but there are no overlaps and gaps.
- Chaotic: A chaotic lattice is a pattern with overlaps and gaps, introducing randomness in your equation.
- Periodic: A periodic lattice is a pattern that repeats again and again with no overlaps and gaps.
Every lattice works as a pattern where the one with the known vector can only decrypt the message. Since it has many patterns, the attacker finds it difficult to find the origin point and key to decrypt it. Whether you have lattices with 10 points or 100 points, the one with the correct key can only decrypt the information.
If an attacker is asked to pick two random points, it will be difficult to determine which point on 10-point lattice patterns leads to the 100-point lattice. Thus, if you know the key, you can easily decode the message.
Benefits of Lattice-Based Cryptography
Lattice-based cryptography offers a lot of benefits for individuals and businesses.

Lower Energy Consumption
Energy consumption increases with the increase in the usage of any system. Despite being faster, lattice-based cryptography consumes less energy as compared to other encryption schemes. This is because lattice-based cryptography is implemented in hardware, resulting in less power consumption.
For example, processors designed for cryptocurrency mining are more energy efficient than traditional processors when using lattice-based cryptography.
High-Speed Computation
Unlike other cryptography algorithms, the encryption scheme of lattices is computed much faster. Faster computation times result in increased performance, giving better responses in real-time, such as online gaming or streaming media.
Easy to Implement and Flexible
Nowadays, businesses are looking for flexible options and saving time. Lattice-based cryptography is easy to implement as it requires less amount of resources and is highly accessible. You can also implement it on off-the-shelf hardware easily.
Additionally, lattice-based cryptography is used in multiple applications, such as digital signatures, key exchange, and password-based encryption. Do not limit yourself to one design; instead, you can construct lattices in different ways you can. Thus, it offers a lot of flexibility.
Reasonable Key Sizes
Lattice-based cryptography key sizes are small but not as small as classical cryptographic algorithms or quantum-safe isogeny-based schemes. Thus, you can use these keys in standard protocols.
Diverse Usage

Lattices let users solve a variety of security challenges, including practical constructions like signatures and key agreement schemes. In addition, you can get to construct security channels across your organization to secure everyone’s data, such as fully homomorphic encryption and identity-based encryption.
Mathematical Foundation
Since the algorithm is completely based on mathematical problems, it is hard to get a real solution to it unless you know the key. This gives assurance to individuals and professionals about their information security.
Understandability
The algorithms used in lattice-based cryptography are based on simple linear algebra that requires a less mathematical background to understand the concept of its working. Thus, you can implement this in no time, giving you fast security and efficiency.
Learning Resources
If you want to learn more about technology, here are some books and courses you can refer to. These are available online and can help you to become a pro in this security method. Let’s dive into these books and courses.

#1. Lattice-based Cryptosystems: A Design Perspective
| Preview | Product | Rating | |
|---|---|---|---|

|
Lattice-Based Cryptosystems: A Design Perspective | Buy on Amazon |
The authors of the book, Jiang Zhang and Zhenfeng Zhang, focus on the lattice-based cryptosystems that are widely considered to be the most promising post-quantum crypto schemes. This book provides fundamental insights into the proper construction of the security layer from hard lattice problems.
The primary concept is to inform you about the tool that can be used to choose the choice of lattice for designing cryptosystems. This includes designing attribute-based encryption, digital signatures, key change, identity-based encryption, and public-key encryption.
#2. Lattice-based Public-Key Cryptography in Hardware
| Preview | Product | Rating | |
|---|---|---|---|

|
Lattice-Based Public-Key Cryptography in Hardware (Computer Architecture and Design Methodologies) | Buy on Amazon |
The book is written by Sujoy Sinha Roy and Ingrid Verbauwhede. They describe how efficient the implementation of public-key cryptography is, which addresses critical security challenges of large amounts of data generated by the network of connected devices. The devices can be tiny Radio Frequency Identification tags, desktops, and more.
The authors also investigate the implementation of post-quantum homomorphic encryption and public-key cryptography schemes.
#3. Lattices and Their Application in Cryptography:
| Preview | Product | Rating | |
|---|---|---|---|

|
Lattices and their application in Cryptography | Buy on Amazon |
This thesis was written by Merve Cakir in the year 2014. The aim of this thesis is to identify the features of lattice-based cryptosystems and how the use of signature and encryption schemes is becoming insecure with the coming of a quantum computer.
In the thesis, the author proposed alternative cryptography based on the worst scenario of lattice problems. The hardness and security of computational problems are analyzed by offering collaboration between complexity theory, public-key cryptography, and linear algebra.
#4. Basic to Advance Level Cryptography

This course is introduced by Udemy that gives you a clear idea of cryptography and some related terminologies. In this course, you will learn about cryptography, hashing, hacking and breaking code, cryptanalysis, and encryption decryption.
You will find 5 sections, including 17 lectures, and the total duration of the course i.e., 2h 7m. To enroll yourself in this course, you just need to have a basic knowledge of computers and high school mathematics.
Conclusion
Cryptography is a simple yet powerful tool to protect the information saved in your systems. It works with the help of complex mathematical problems and different algorithms for securing data, which is everyone’s primary goal these days.
Lattice-based cryptography is one of the most secure security mechanisms that use simple linear algebra to encrypt the data. It includes lattices, vectors, and basis that are used to construct a tough pattern. The decryption method depends on the patterns, and for that, you need to know the origin point. If you have the key, you can easily decrypt data.
Thus, lattice-based cryptography is a proven technique to secure the data of individuals and businesses operating in multiple industries, from IT and security service firms to finance and many more.
You may also read Cloud Cryptography.

