Scan your web server for vulnerabilities, a misconfiguration in FREE with Nikto scanner
97% of applications tested by Trustwave had one or more weaknesses.
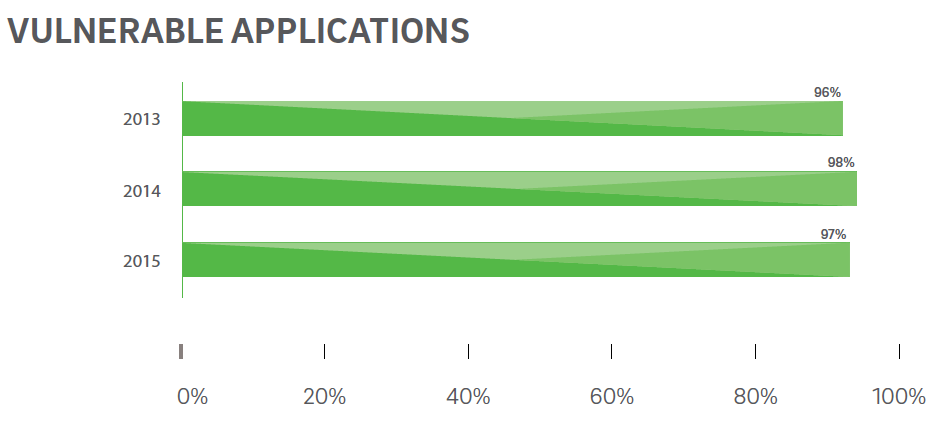
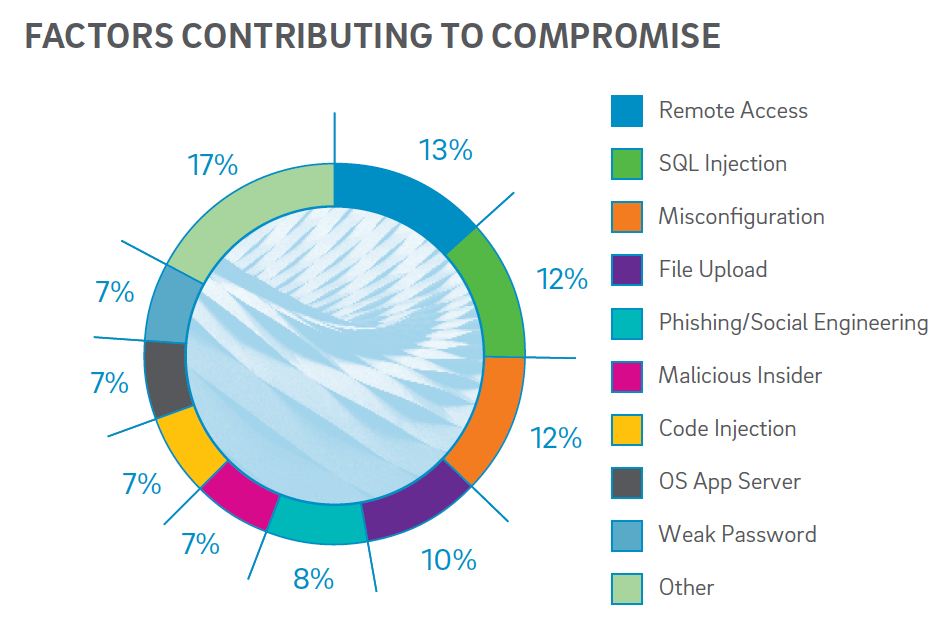
And 14% of investigated intrusion was due to misconfiguration. Misconfiguration can lead to serious risks.
There are a number of online vulnerability scanners to test your web applications on the Internet. However, if you are looking to test Intranet applications or in-house applications, then you can use the Nikto web scanner.
Nikto is an open-source scanner and you can use it with any web servers (Apache, Nginx, IHS, OHS, Litespeed, etc.). Sounds like a perfect in-house tool for web server scanning. It is capable of scanning for over 6700 items to detect misconfiguration, risky files, etc. and some of the features include;
- You can save the report in HTML, XML, CSV
- It supports SSL
- Scan multiple ports on the server
- Find subdomain
- Apache user enumeration
- Checks for outdated components
- Detect parking sites
Let’s get started with installation and how to use this tool.
There are many ways to use Nikto.
- Using Kali Linux
- Docker container
- Use the binary on UNIX-based distro or Windows.
Note: performing scan makes lots of requests to your web server. You acknowledge the risk and perform against only your servers.
Using Nikto on Kali Linux
Since it’s inbuilt in Kali, you don’t need to install anything.
- Login into Kali Linux
- Go to Applications >> Vulnerability Analysis and click nikto
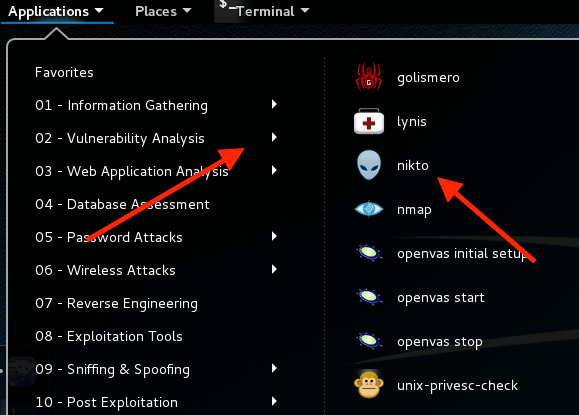
It will open the terminal where you can run the scanning against your web server. There is multiple syntaxes you can use to run the scan. However, the quickest way to do is below.
# nikto –h $webserverurlDon’t forget to change $webserverurl with your web server actual IP or FQDN.
root@Chandan:~# nikto -h thewebchecker.com
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 128.199.222.244
+ Target Hostname: thewebchecker.com
+ Target Port: 80
+ Start Time: 2016-08-22 06:33:13 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0x2c39 0x53a938fc104ed
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ Uncommon header 'x-ob_mode' found, with contents: 1
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
+ 7596 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2016-08-22 06:54:44 (GMT8) (1291 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedAs you can see the above scan is against the default configuration of Apache 2.4, and there are many items that needs attention.
You can refer to my Apache Security & Hardening Guide to fix these.
Using Nikto on CentOS
- Login to CentOS or any Linux based OS
- Download the latest version from Github using wget
wget https://github.com/sullo/nikto/archive/master.zip .- Extract using unzip command
unzip master.zip- It will create a new folder called “nikto-master”
- Go inside the folder nikto-master > program
cd nikto-master/program- Execute
nikto.plwith the target domain
Once installed execute nikto and should be fine. This time, I will run a scan against the Nginx webserver to see how it performs.
./nikto.pl -h $IPADDRESS[root@lab program]# ./nikto.pl -h XX.XX.137.171
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: XX.XX.137.171
+ Target Hostname: XX.XX.137.171
+ Target Port: 80
+ Start Time: 2020-06-07 07:39:40 (GMT0)
---------------------------------------------------------------------------
+ Server: nginx/1.14.1
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /httpd.conf: Apache httpd.conf configuration file
+ /httpd.conf.bak: Apache httpd.conf configuration file
+ 8075 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2020-06-07 07:39:50 (GMT0) (10 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
[root@lab program]#So as you can see default Nginx, the webserver configuration is vulnerable too and this security guide will help you to mitigate them.
Troubleshooting
You may encounter the following error when running on CentOS and if so you can fix as explained below.
ERROR -1
+ WARNING: Module JSON::PP missing. -Savedir and replay functionality cannot be used.OR
ERROR: Required module not found: Getopt::Long
ERROR: Required module not found: Time::Local
ERROR: Required module not found: Time::HiRes qw(sleep ualarm gettimeofday tv_interval)If you are getting the above warning, then you need to install the Perl module by the following.
# yum install perl-CPAN*or using DNF is using CentOS 8
# dnf install perl-CPAN*ERROR – 2
perl: warning: Setting locale failed.For this, you need to export the locale on the terminal as explained here.
export LC_CTYPE=en_US.UTF-8
export LC_ALL=en_US.UTF-8ERROR – 3
Can't locate bignum.pm in @INC (you may need to install the bignum module)You need to install the Perl bignum module.
# yum install perl-bignumor using DNF if CentOS 8
# dnf install perl-bignumConclusion
Go ahead and play around with the Nikto software and if interested in learning more then check out this hacking and penetration testing course.

