Vulnerability scanning helps find security issues in software, servers, and networks. It detects outdated software, missing patches, weak credentials, and configuration errors, helping organizations minimize the risk of cyberattacks.
Open-source vulnerability scanners are free to use. They offer transparency, community support, and flexibility for customization. However, choosing the right open-source tool is tricky, as its features, usability, and update frequency can vary.
In this article, I’ve listed the best open-source vulnerability scanners based on performance, scan depth, integration capabilities, and community support.
If you’re looking for premium or managed options, check out our list of top web vulnerability scanners.
- 1. Nmap
- 2. Greenbone OpenVAS
- 3. reNgine
- 4. Dirsearch
- 5. w3af
- 6. Nikto
- 7. Wfuzz
- 8. Zed Attack Proxy
- 9. OSV Scanner
- 10. CloudSploit
- 11. Wapiti
- Show less
You can trust Geekflare
At Geekflare, trust and transparency are paramount. Our team of experts, with over 185 years of combined experience in business and technology, tests and reviews software, ensuring our ratings and awards are unbiased and reliable. Learn how we test.
1. Nmap
Nmap is a free, open-source network scanner that helps detect active hosts, services, OS versions, and uncover potential security risks. It performs deep scans using raw IP packets and is compatible with Linux, Windows, and macOS.
You can use it to audit security, manage upgrades, and monitor host or service uptime. It comes with tools like Zenmap (GUI), Ncat, Ndiff, and Nping for added flexibility.
I like Nmap’s ability to handle both small and large networks. It offers command-line and GUI options. It is easy to use but powerful enough for experts.
Nmap is trusted globally by security teams for network discovery and vulnerability scanning, supported by a strong community, extensive documentation, and versatile output formats including interactive, plain text, and XML.
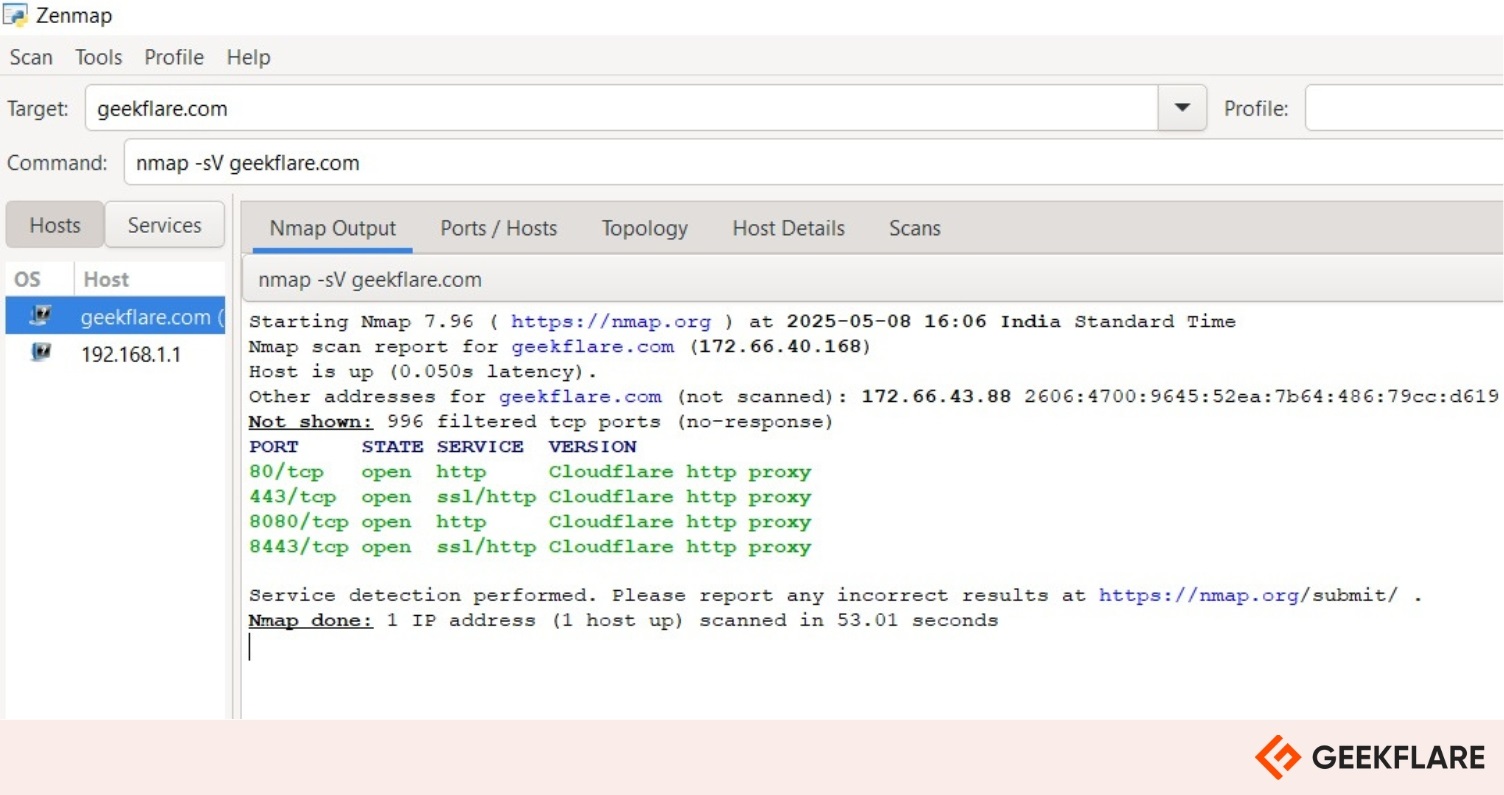
Nmap Key Features
- Scans ports to identify which services are open, closed, or filtered.
- Detects running services and pinpoints their exact versions on the target host.
- Identifies the operating system and version based on network behavior analysis.
- Uses custom scripts to uncover vulnerabilities in services like SMB and HTTP.
- Detects firewalls and packet filters that may block or restrict traffic.
2. Greenbone OpenVAS
Greenbone OpenVAS is an open-source vulnerability scanner made for flexible and deep security checks. It supports both unauthenticated and authenticated scans. It handles internet and industrial protocols, so it suits many environments.
You can tune it for performance when scanning large networks. OpenVAS uses a vast and daily updated database of Network Vulnerability Tests (NVTs) to detect known vulnerabilities. It includes a built-in programming language, letting you create custom tests.
Greenbone OpenVAS Key Features
- Detects system misconfigurations that may enable unauthorized access.
- Identifies outdated or unpatched software commonly targeted by attackers.
- Flags weak or default passwords to reduce risk of compromise.
- Scans for exposed services and open ports vulnerable to attacks.
- Discovers web application flaws like SQL injection and XSS.
- Assess network devices for firmware and configuration vulnerabilities.
3. reNgine
reNgine helps small teams scan web apps faster and smarter. It automates information gathering with customizable scanning engines.
reNgine offers real-time scanning and continuous monitoring. You can react fast during recon without waiting for full scans. It supports scheduled scans and sends alerts through Discord, Slack, or Telegram. You can quickly scan new subdomains or dive deeper into vulnerabilities as soon as they’re found.
It links data across scans to give more accurate results. It stores findings in a database, so you don’t lose past scan data. Whether testing your own apps or checking for bugs, reNgine simplifies the job and saves time.
reNgine Key Features
- Automates vulnerability detection using advanced tools like Nuclei, Dalfox, and CRLFuzzer.
- Detects exposed or misconfigured Amazon S3 buckets.
- Generates vulnerability details, impact, and fixes using local LLMs (Large Language Models).
- Highlights common CVEs (Common Vulnerabilities and Exposures), vulnerable targets, and trends.
- Integrates built-in CVE lookup and CMS detection for deeper context.
- Sends vulnerability findings directly to HackerOne.
- Supports scanning multiple targets or findings in parallel.
4. Dirsearch
Dirsearch is a fast, simple command-line tool written in Python that helps discover hidden files and directories on websites. It supports installation via Git, PyPI, Docker, or as a ZIP archive.
It needs Python 3.9 or higher. It uses wordlists and file extensions to try different paths. You can force or overwrite extensions. Dirsearch supports recursive scanning, filters, proxies, authentication, and raw requests. You can use it with threads or in Async mode.
Reports are available in many formats, such as JSON, HTML, or CSV. It’s easy to pause scans and continue later. You can customize scans using configuration files and many flexible options to suit your needs.

Dirsearch Key Features
- Scans directories and files to find hidden or unlisted paths that may expose vulnerabilities.
- Supports recursive and deep-recursive scans, revealing deeply nested insecure endpoints.
- Offers advanced filtering by status codes, response sizes, or regex to eliminate noise and spotlight high-risk entries.
- Loads targets directly from Nmap reports.
- Enables scanning via HTTP proxies to maintain anonymity and bypass network-level restrictions.
5. w3af
w3af is a free, open-source vulnerability scanner tool that checks web applications for security vulnerabilities. It can find more than 200 types of vulnerabilities, such as Cross-Site Scripting (XSS), SQL Injection, or OS Command Injection.
It lets users create their own plugins and scripts for special needs. It can act like a middleman (HTTP proxy) to capture and change website traffic. w3af also creates detailed reports, showing security issues and actions taken during testing.
w3af is developed in Python, making it cross-platform and compatible with any system that supports Python, including most Linux distributions, FreeBSD, OpenBSD, and macOS.
w3af Key Features
- Offers both a command-line interface (CLI) and a graphical user interface (GUI) for flexibility in user interaction.
- Supports multiple authentication methods, including Basic, NTLM, and form-based.
- Integrates with Metasploit for advanced exploitation capabilities.
6. Nikto
Nikto is an open-source (GPL) scanner that is designed to perform complete tests against web servers to identify security vulnerabilities and configuration issues. It identifies web servers and software running on the target server, which gives administrators a better understanding of their system’s setup.
Nikto is not designed to be a stealthy tool, as it aims to test web servers as quickly as possible. Its activities are often visible in log files or in IPS/IDS systems. But it supports LibWhisker’s anti-IDS methods, which can help users test their IDS systems or attempt to evade detection in specific scenarios.
For a step-by-step guide, check out this article on how to use the Nikto scanner to find web server vulnerabilities.
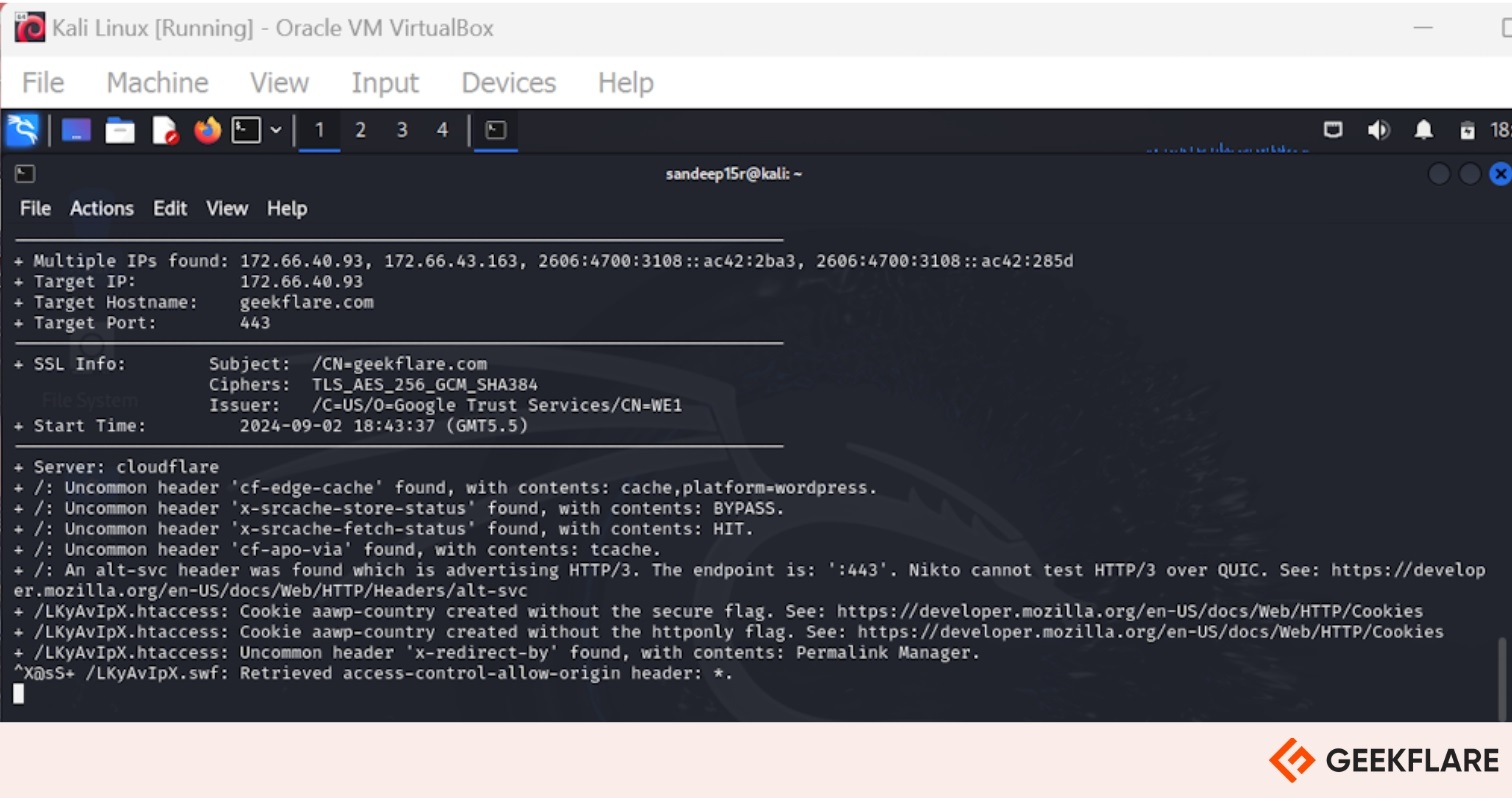
Nikto Key Features
- Supports SSL and full HTTP proxy for secure and flexible scanning.
- Generates customizable reports using a powerful template engine.
- Ability to scan multiple ports on a server or multiple servers via an input file
- Offers scan tuning to include or exclude specific classes of vulnerability checks.
- Minimizes false positives using techniques like header analysis, content comparison, and hashing.
- Handles authentication via Basic and NTLM mechanisms.
7. Wfuzz
Wfuzz (Web Fuzzer) is an application assessment tool for penetration testing. You can fuzz the data in the HTTP request for any field to exploit and audit the web applications.
It also supports brute-force attacks by allowing users to test multiple values for specific parameters. This can be particularly useful for discovering weak credentials or sensitive information that might be exposed through incorrect configurations.
Wfuzz Key Features
- Payload customization & fuzzing capabilities that fuzz different parts of HTTP requests, including parameters, headers, and cookies, to identify weaknesses in input validation.
- Wfuzz is built as a modular framework. So it will be easy for developers to create & integrate custom plugins.
- HTTP Header and Authentication Testing
- Wfuzz can be integrated with other security tools, such as Burp Suite. It allows users to make use of previous HTTP requests & responses from other tools.
It can also perform directory and file fuzzing to identify sensitive files and other resources on the web server.
8. Zed Attack Proxy
ZAP by Checkmarx is an open-source security testing tool designed for everyone, especially beginners. It helps you find vulnerabilities in your web applications with ease.
You can start quickly using the ZAP Quick Start Guide. ZAP also offers powerful automation options to streamline your security tests. Its Marketplace lets you extend its features with community-contributed add-ons.
Whether you want to scan manually or automate the process, ZAP makes it simple and flexible. Plus, the active community, blog, and video tutorials offer plenty of help.
ZAP Key Features
- ZAP has a spidering functionality that helps identify and map out all accessible endpoints within the target web application.
- It supports manual testing by providing an interactive proxy. Users can intercept & modify requests between the client and the server.
- ZAP supports fuzzer plugins to fuzz-test various inputs of the target application to discover potential vulnerabilities.
9. OSV Scanner
OSV-Scanner helps you find security vulnerabilities in your project’s dependencies. It acts as the official frontend for the OSV database, linking your software packages to known issues.
Since OSV is open source, it offers several advantages over closed databases. Every advisory comes from trusted, public sources like RustSec. Anyone can suggest improvements, which makes the database highly accurate.
Its OSV format clearly maps exactly which versions are affected, so you get fewer false alarms and more actionable alerts, saving both time and effort.
10. CloudSploit
CloudSploit is an open-source Cloud Security Posture Management (CSPM) tool that helps detect security risks in cloud accounts like Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud Infrastructure (OCI), and GitHub.
It scans your infrastructure and reports potential misconfigurations and threats. You can deploy CloudSploit in two ways:
- Self-Hosted: Run CloudSploit locally with a straightforward setup process, giving you full control.
- Managed (Aqua Wave): Opt for the hosted commercial version for a hassle-free, fully managed experience.
CloudSploit makes it simple to spot risks early and secure your cloud environments.
CloudSploit Key Features
- Maps findings to compliance standards like HIPAA, PCI, and CIS Benchmarks.
- Supports export in table, text, CSV, JSON, and JUnit XML formats.
- Allows scan customization via plugins, result suppression, and ignoring passing checks.
11. Wapiti
Wapiti is a free and open-source web application vulnerability scanner that assesses the security of websites. It operates as a “black-box” scanner, which means it doesn’t require access to the application’s source code. Instead, it analyzes the deployed web application by crawling its web pages & looking for potential vulnerabilities.
Wapiti offers several options to control the behavior of the crawler, such as skipping specific parameter names during the attack, setting a maximum time for the scan process, adding custom HTTP headers, and more.
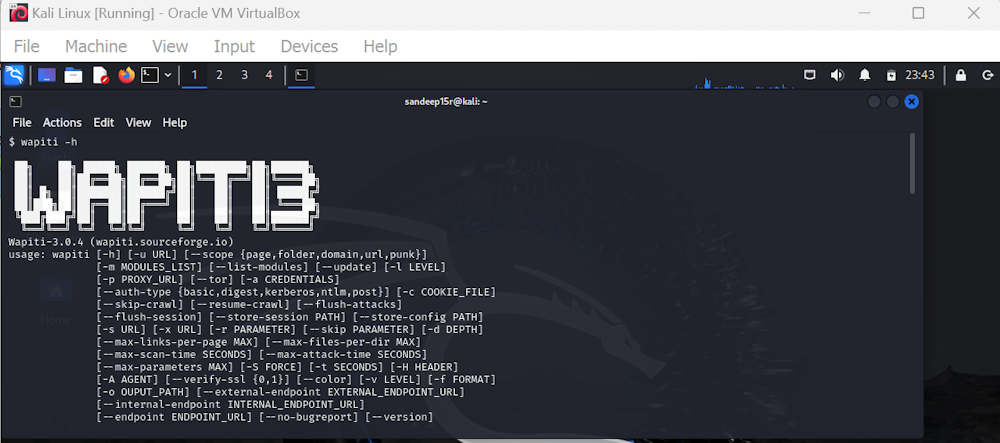
Wapiti Key Features
- Detects vulnerabilities like file disclosure, XXE, CRLF injection, and open redirects.
- Enables custom payload injection for deep vulnerability analysis.
- Users can activate or deactivate SSL certificate verification during the scan.
- Supports HTTP/HTTPS/SOCKS5 proxies.
- Allows authentication via Basic, Digest, NTLM, or custom login forms (GET/POST).
- Imports cookies from Chrome or Firefox browsers and supports MITM proxy to explore the target using the user’s browser.
Honorable Mentions
Here are some more open-source vulnerability scanners you can explore:
12. Vega
Vega is a free and open-source tool for finding security issues in web applications. It lets you scan websites for vulnerabilities like SQL injection and cross-site scripting using an easy-to-use graphical interface.
13. sqlmap
sqlmap is a free and open-source tool that helps find and exploit SQL injection flaws in websites. It automates the process of detecting database vulnerabilities and can even take over the database server.
14. Grabber
Grabber is a free and open-source web application scanner that helps find security issues in small websites. It checks for common vulnerabilities like XSS, SQL injection, and file inclusion without needing access to the site’s code.
15. Brakeman
Brakeman is a free and open-source security scanner for Ruby on Rails applications. It checks your code for common security issues without running the app.
Final Words
Keeping a constant vigil on one’s security posture is critical, and these open-source vulnerability scanners help do just that. They offer robust protection at a fraction of the cost it would’ve taken with premium cybersecurity tools offered as SaaS.
However, before deploying them company-wide, verify key aspects such as integration capabilities, support, and overall performance through a pilot implementation. Also, don’t overlook version updates and security patches to keep the scanners operating at their best.
What’s Next
-
 EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.
EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.


