When purchasing remote access software for your business, for working from home, or for providing remote support and assistance to your clients, it’s crucial to rely on a solution that ensures the highest possible security.
The continuous rise in cyber-attacks paints a picture of a threat landscape that is perpetually and rapidly evolving. These attacks focus not only on individual users, but also on the cloud infrastructures that support the operation of multiple services. There have been significant attacks in the past on IT companies, effectively MSPs managing thousands of clients (see the SolarWinds case), a factor that dramatically multiplies the impact on businesses and strategic infrastructures.
Remote Desktop software certainly deserves special attention from IT security experts, as by definition, these are tools that allow remote access to systems, giving full control over them to the user.
Secure Remote Desktop sessions for IT Companies
When clients entrust an IT company with remote technical support, especially for servers and critical infrastructures, they want assurance that the software tools used guarantee the highest level of security.
Iperius Remote is one of the best software for remote control of PCs and Servers. It is a practical alternative to AnyDesk and TeamViewer, with all the necessary security requirements to comply with recent HIPAA and GDPR regulations.
Iperius Remote is multi-platform and works on Windows, Mac, and mobile devices iOS and Android.
This article focuses on several key points that uniquely characterize the security of Iperius Remote:
- 2FA: Two-Factor Authentication
- End-to-End Encryption
- TLS 1.3
- Automatic screen lock
- ISO 27001 certified cloud infrastructure
- Multi-level passwords
- Granular permissions
2FA: Two-Factor Authentication
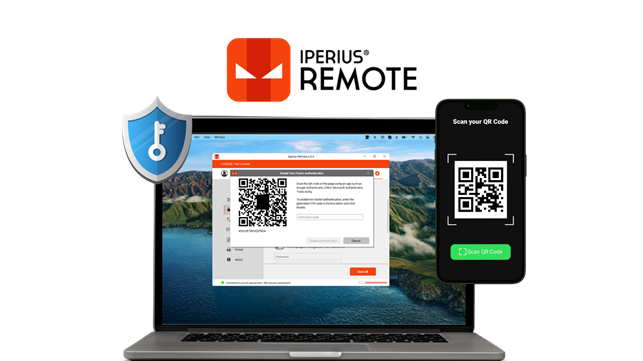
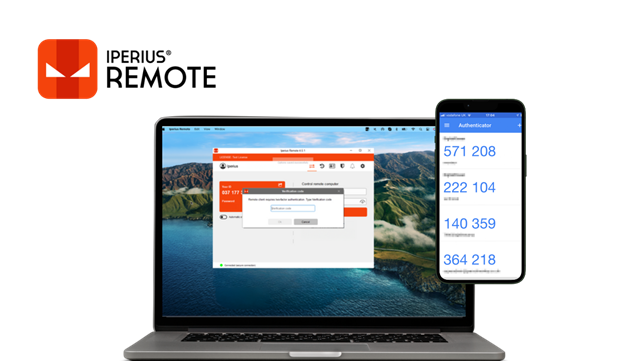
The safest way to protect a remote computer is to use two-factor authentication (2FA). Simply put, this means that anyone wanting to connect to that computer must generate an OTP from an authorized mobile device. This prevents any access that hasn’t gone through this additional layer of authentication, even if a malicious user somehow obtained the remote computer’s ID and password.
Learn how to enable two-factor authentication on Iperius Remote.
Once the program is opened on the remote machine to be protected, go to the security options and enable the 2FA option. A QR code will be displayed, which can be scanned with a compatible authentication app like Google Authenticator, via our mobile device.
Once done, close the window with the QR code. From that moment on, every time someone tries to connect to that remote computer, the OTP generated randomly by the authentication app will be required.
This achieves the highest level of security for accessing our personal or work computer, or for remotely accessing a company server for maintenance or monitoring.
End-to-End Encryption
Encryption is the method by which data transmitted over the internet or the content of a file is converted into a format accessible only to authorized users with the appropriate cryptographic key. It’s a process that transforms information into a format that prevents unauthorized individuals from reading it.
End-to-End Encryption (E2EE) represents a specific security technique where data is encrypted at every stage of its transfer from one device to another. The term “end-to-end” indicates that encryption occurs from the beginning to the end of the data’s journey, from the sender’s device to the recipient’s device. For example, in the case of sending an email, the starting point is the sender’s device, and the endpoint is the recipient’s device.
This technique ensures that communication is protected by preventing any third party from accessing the content of the messages, both during the transfer between devices and when the data passes through a server.
Using E2EE to send an email or transmit video information ensures that no one, including the network administrator, the Internet Service Provider (ISP), hackers, the government, or even the company managing the email delivery, can read the content of the message or a video transmission. This is because only the recipient has the unique key capable of decrypting the message.
Iperius Remote natively implements end-to-end encryption in all video transmissions (remote desktop), file transfers, and chat, thus avoiding any possibility of data interception or compromise.
TLS 1.3
TLS 1.3 is the latest available security protocol and is implemented by Iperius whenever possible, depending on the capabilities of the operating systems where the software is run.
TLS 1.3 protocol, used by HTTPS and other network protocols for encryption, represents the modern evolution of SSL. TLS 1.3 has removed support for cryptographic features considered less secure and has accelerated TLS handshake procedures, among other improvements.
To provide a timeframe, the IETF (Internet Engineering Task Force) published TLS 1.3 in August 2018. The previous version, TLS 1.2, had been standardized ten years earlier, in 2008.
What’s the difference between TLS 1.3 and TLS 1.2?
TLS 1.3 is faster and more secure than TLS 1.2 (which remains a very high security standard). One of the changes contributing to TLS 1.3’s increased speed is an update in the TLS handshake procedure:
TLS 1.3 handshakes require only one round trip (or back-and-forth communication) instead of two, shortening the process by a few milliseconds. Moreover, when the client is already connected, the TLS handshake can occur without any round trips, thus speeding up HTTPS connections, reducing latency, and improving the overall user experience.
Adding a technical note, it’s important to highlight that TLS 1.3 also improves security through the implementation of a more restricted and secure set of encryption algorithms and hash functions, eliminating those considered obsolete or risky. This choice aims to simplify security configuration and reduce the risk of incorrect configurations that could expose vulnerabilities.
Other Security Measures
All connections of Iperius Remote are protected through AES encryption or password hashing and rely on a server infrastructure in data centers certified ISO 27001 and protected from DDoS attacks, to ensure the highest reliability of the service.
At the application level, Iperius Remote offers protection thanks to multi-level passwords and very useful support features, such as automatic screen locking when a remote desktop session ends. Moreover, for connections where only screen sharing is needed, Iperius Remote allows limiting permissions, i.e., preventing the use of mouse and keyboard, copy and paste, and file transfer.
Clearly, Iperius Remote implements extensive logging features both at the level of local client applications and at the server level, to keep track of every action performed and every remote desktop session established.
Finally, Iperius Remote allows granular permission settings through its web administrative interface, where it’s possible to configure access and viewing permissions in the address book for various computers, in a granular way for operator users and for computer groups.
Operational Features of Iperius Remote
Here’s a brief overview of the operational aspect of Iperius Remote, i.e., the main functionalities of the software to maximize productivity for remote work or remote technical support:
- File transfer with copy and paste or drag and drop
- Shared address book and multiple address books
- Multi-user chat
- Remote printing
- Web administrative area to create groups and operators, set detailed permissions, and consult connection time statistics
- Screenshot and video recording of sessions
- Multi-monitor support
- Unattended access
- Multi-user sessions, allowing multiple operators to connect to the same remote computer
- Remote connection reversal / screen sharing
- Creation of MSI setups for large-scale installation via GPO
- Corporate Rebranding: Iperius is one of the few software programs that allow you to customize the client by changing the program’s name and icon
- Remote access to mobile devices
The Iperius Remote license: Unlimited remote devices!
With an Iperius Remote license for only €8.39 per month, you can enjoy unlimited access to any number of devices. You can create an unlimited number of accounts, have an unlimited list of devices in the address book, and connect to an unlimited number of remote computers.
Licenses and prices are based on the number of concurrent connections. With the free version, you can only make one connection at a time (there may still be license and time limits in case of continuous use).
Starting from the most affordable version, up to 2 concurrent connections can be opened, while for subsequent versions, 5-10-15-100 connections at the same time, or even more, can be established.
However, what all paid versions have in common is the absence of hidden limitations, making the cost of the product absolutely competitive:
- Unlimited remote devices (even unattended)
- Unlimited devices where you can use the license
- Unlimited accounts for operators
- Unlimited devices in the address book
- No limit to connection hours
Remote Access to iOS and Android devices
In the digital age, the need to access and control devices remotely has become increasingly pressing, both for professional and personal reasons. Responding to this need, Iperius Remote positions itself as a reliable and versatile solution for remote access, available for iOS and Android users.
The application is available on Google Play and the Apple Store, allowing users to easily download Iperius Remote Desktop and establish a secure connection with their devices from anywhere in the world.
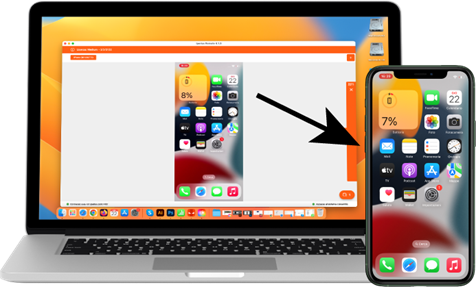
With Iperius Remote Desktop, users can connect to their mobile devices bidirectionally, allowing access from iOS/Android devices to Windows/Mac computers, and vice versa. You can connect to your iPhone and remotely view the phone screen, or you can remotely access your Android smartphone and control it as if you had it in your hands.
The application allows you to view the mobile device screen directly on the computer, offering the possibility to control applications, files, and settings remotely. Whether it’s sending messages, transferring files, or solving technical problems, Iperius Remote Desktop makes these operations simple and immediate, eliminating the need to physically have the device in hand.
Iperius Remote’s remote access is not limited to managing personal devices. In fact, the application also allows connecting from mobile devices to PC or MAC, facilitating remote assistance sessions to company servers or clients. This feature is particularly useful for IT professionals who need to provide remote technical support, optimizing intervention times and improving customer service.
Any connection type
The multi-platform nature of Iperius Remote is evident in the number of “directions” that the remote desktop connection can take:
Windows ➔ MAC
MAC ➔ Windows
Windows ➔ Windows
MAC ➔ MAC
iOS / Android ➔ Windows / MAC
Windows / MAC ➔ Android
Windows / MAC ➔ iOS (iPhone/iPad)
Related Articles
-
 EditorUsha, the editor-in-chief of Geekflare, is a tech-savvy and experienced marketer with a Master’s degree in Computer Applications. She has over a decade of experience in the tech industry, starting as a software engineer and then moving into digital marketing and team management.
EditorUsha, the editor-in-chief of Geekflare, is a tech-savvy and experienced marketer with a Master’s degree in Computer Applications. She has over a decade of experience in the tech industry, starting as a software engineer and then moving into digital marketing and team management.


