SSL/TLS certificates secure websites by encrypting communication between users and servers. Troubleshooting them is essential to prevent security risks from misconfigurations, expired certificates, or weak encryption, which can impact trust and SEO rankings.
However, manually handling SSL/TLS certificates—including creation, testing, conversion, and configuration—can be complex and time-consuming. To simplify SSL/TLS management, various online tools automate verification, diagnose certificate issues, and analyze configurations.
In this article, we’ve researched and compiled the best SSL checker tools to efficiently troubleshoot TLS and certificate issues, ensuring your website remains secure and compliant.
- 1. Qualys SSL Labs
- 2. SSLStore SSL Checker
- 3. Domsignal
- 4. Wormly SSL Tester
- 5. DigiCert SSL Certificate Checker
- 6. Siterelic TLS Scanner API
- 7. Comodo SSL Checker
- 8. ImmuniWeb SSL Security Test
- 9. SSLShopper SSL Checker
- 10. MDN HTTP Observatory
- 11. SSLChecker.com
- 12. SSL Diagnos
- 13. GocertsSSL SSL Checker
- 14. TLS-Scan
- 15. testssl.sh
- 16. OpenSSL CSR Wizard
- 17. Domsignal Mixed Content Checker
- 18. SSL Shopper CSR Decoder
- 19. SSLyze
- 20. SSLLabs Scan
- 21. SSL Scan
- 22. SSL Converter
- 23. SSL Shopper Certificate Decoder
- 24. Mozilla SSL Configuration Generator
- Show less
You can trust Geekflare
At Geekflare, trust and transparency are paramount. Our team of experts, with over 185 years of combined experience in business and technology, tests and reviews software, ensuring our ratings and awards are unbiased and reliable. Learn how we test.
1. Qualys SSL Labs
SSL Server Test by Qualys SSL LABS is one of the most popular SSL testing tools to check all the latest vulnerabilities & misconfiguration, certificate issuer, validity, protocol details, cipher suites, and handshake simulation.
It tests the website’s SSL certificate on multiple servers to make sure the test results are accurate.
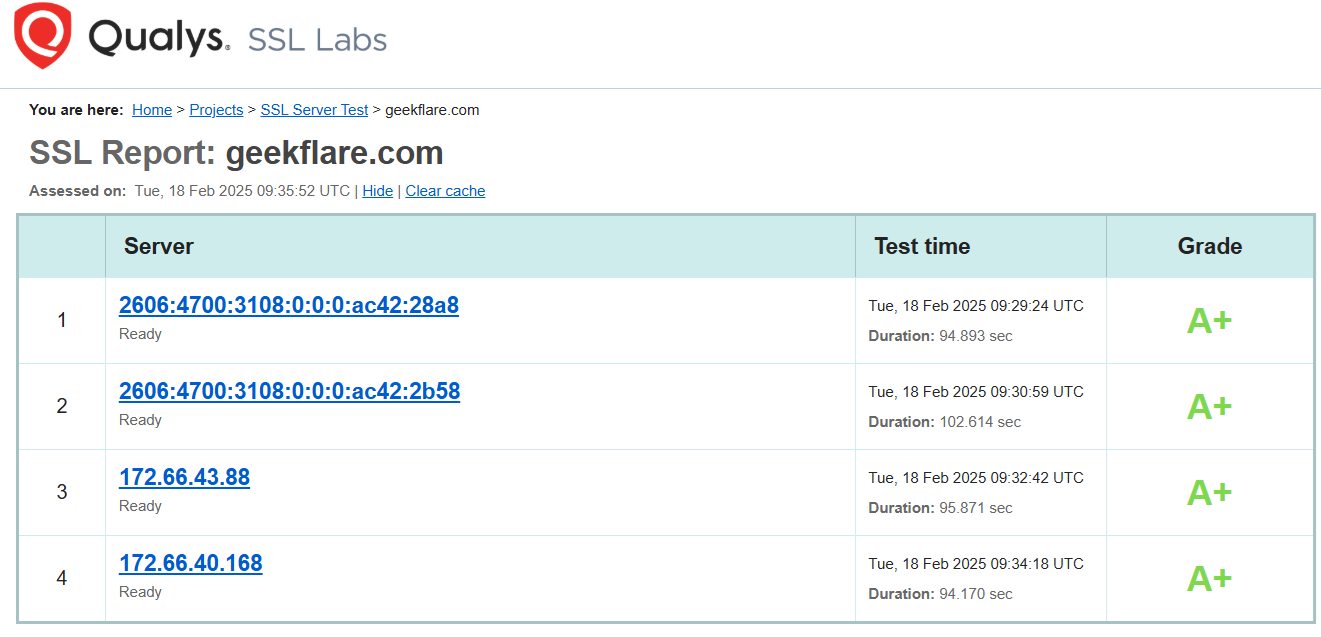
Test results provide detailed technical information; it is advisable for system administrators, auditors, and web security engineers to know and fix any weak parameters.

SSL Labs tool also lets you know if the website has deployed HTTP Strict Transport Security (HSTS). HSTS prevents attacks like cookie hijacking and protocol downgrades. By using this tool regularly, you can keep track of any vulnerabilities well in advance. It also lets you know the authenticity of the DNS certifying authority to measure the website’s trustworthiness.
2. SSLStore SSL Checker
SSL Store SSL Checker lets you quickly identify if a chain certificate is implemented correctly. It’s a great idea to proactively test after SSL cert implementation to ensure the chain certificate is not broken.
It provides detailed information by providing your server’s hostname or IP address, including the Common Name, server type, issuer, validity period, and certificate chaining.
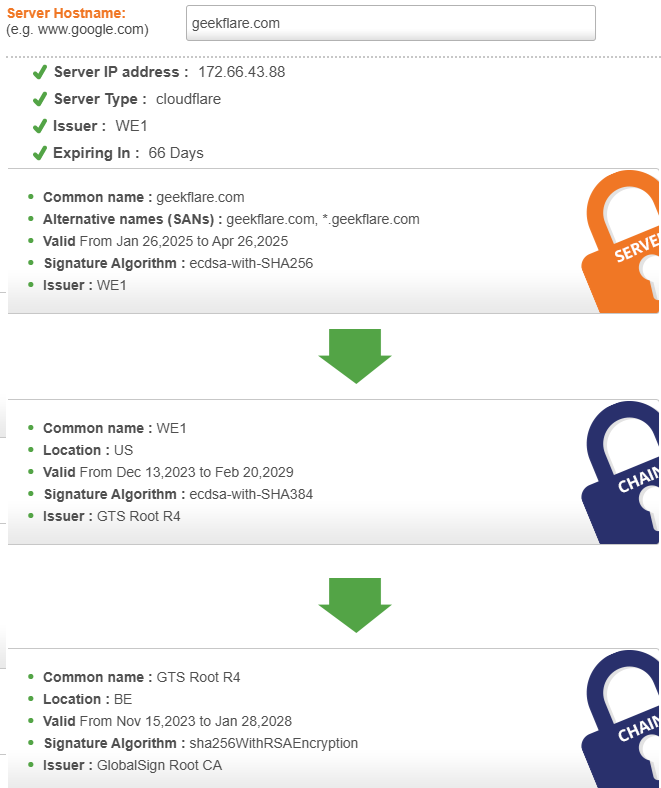
This ensures that your SSL certificate is correctly installed and trusted by browsers, helping to prevent potential security warnings for users.
3. Domsignal
Domsignal has two SSL/TSL tools. The first one checks the TLS version, and the second is for an in-depth analysis of your security protocols, including certificate details, server preferences, vulnerabilities, etc.
TLS Test: This quickly scans the supported TLS version up to the latest TLS 1.3.

TLS Scanner: This entails detailed testing to find out the common misconfiguration and vulnerabilities.

The result includes:
- Supported protocol with versions
- Server handshake preference
- Vulnerabilities test like heart bleed, Ticketbleed, ROBOT, CRIME, BREACH, POODLE, DROWN, LOGJAM, BEAST, LUCKY13, RC4, and a lot more.
- Certificate details
4. Wormly SSL Tester
Wormly SSL Tester Wormly SSL Tester conducts a thorough analysis of over 65 security metrics, providing a comprehensive status report and an overall security score.
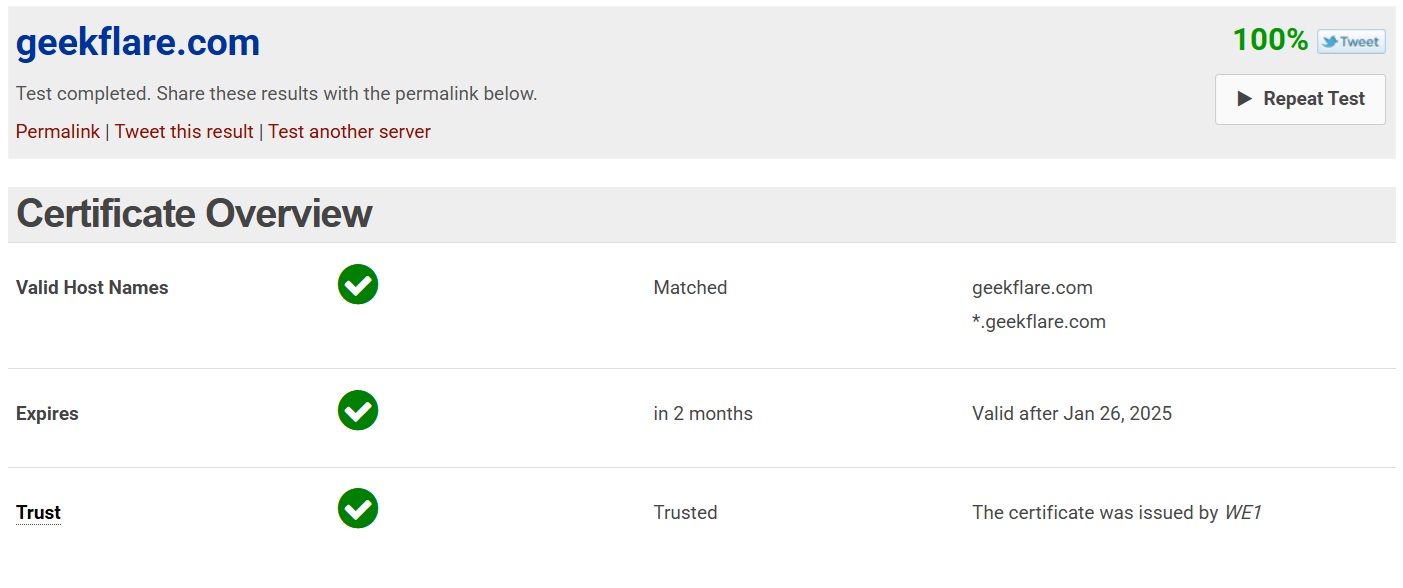
The detailed report includes a certificate overview (Common Name, expiration details, and trust chain verification), encryption cipher details, public key size, secure renegotiation status, and support for various protocols such as SSLv3, SSLv2, TLSv1, and TLS1.2.
5. DigiCert SSL Certificate Checker
DigiCert’s SSL Certificate Checker allows you to verify SSL/TLS certificates for your websites. Just enter your website domain name, and it checks for issues like installation errors, certificate chain problems, and expiry warnings.
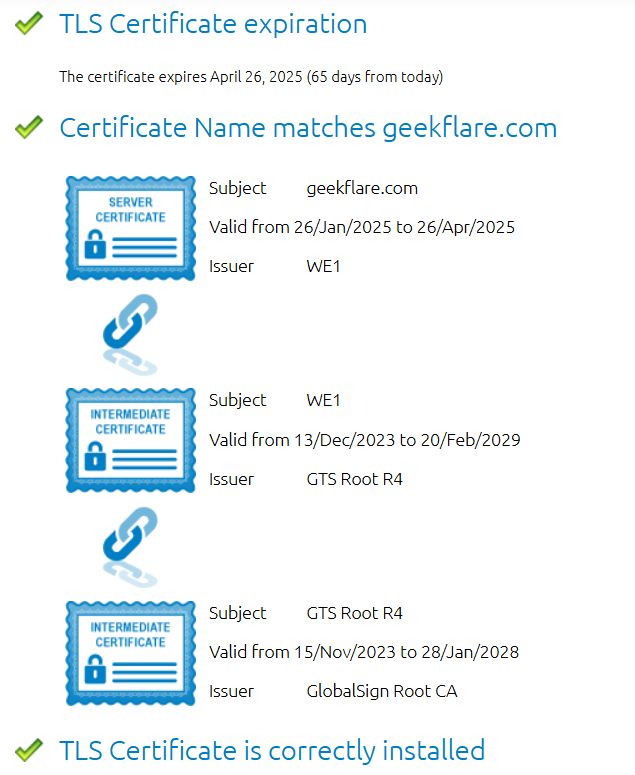
The tool also provides details such as the resolved IP address, certificate issuer, serial number, key length, signature algorithm, supported SSL ciphers, and expiration date. It’s useful if you are looking to verify what ciphers your server supports.
6. Geekflare TLS Scanner API
Geekflare’s TLS Scanner API offers a complete solution for evaluating a website’s TLS configuration, providing insights into supported protocols, certificate issuer details, expiration dates, Subject Alternative Names (SAN), and Common Names (CN).
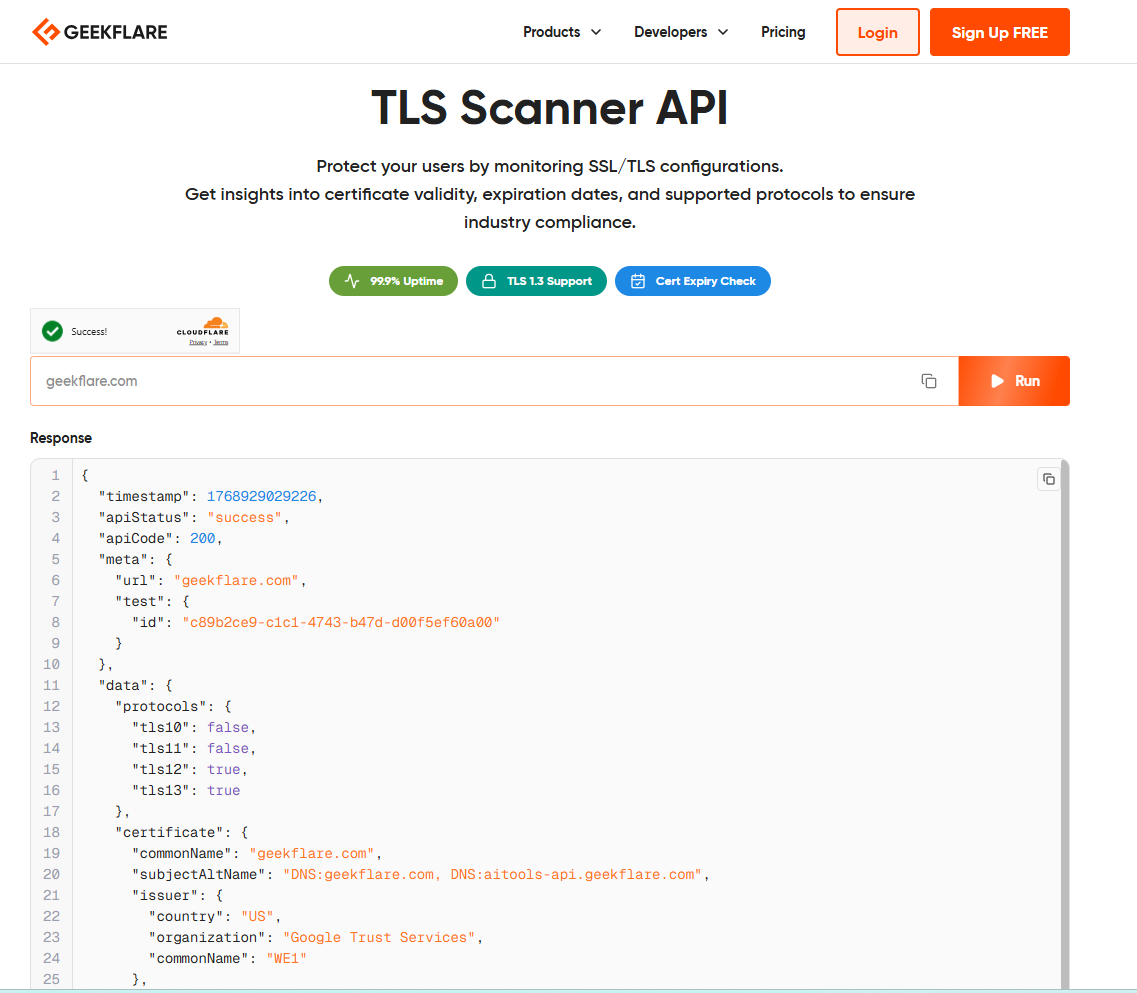
With a scalable and reliable infrastructure powered by Google Cloud, Geekflare API can handle millions of requests monthly, offering flexible plans to accommodate various needs. You can start with a free plan that offers 500 monthly credits. If you need more, paid plans begin at $9/month for 5000 credits.
7. Comodo SSL Checker
Comodo SSL Checker helps you verify the validity and setup of SSL/TLS certificates on any website. It checks key details like the Common Name, server type, certificate issuer, validity period, and certificate chain.
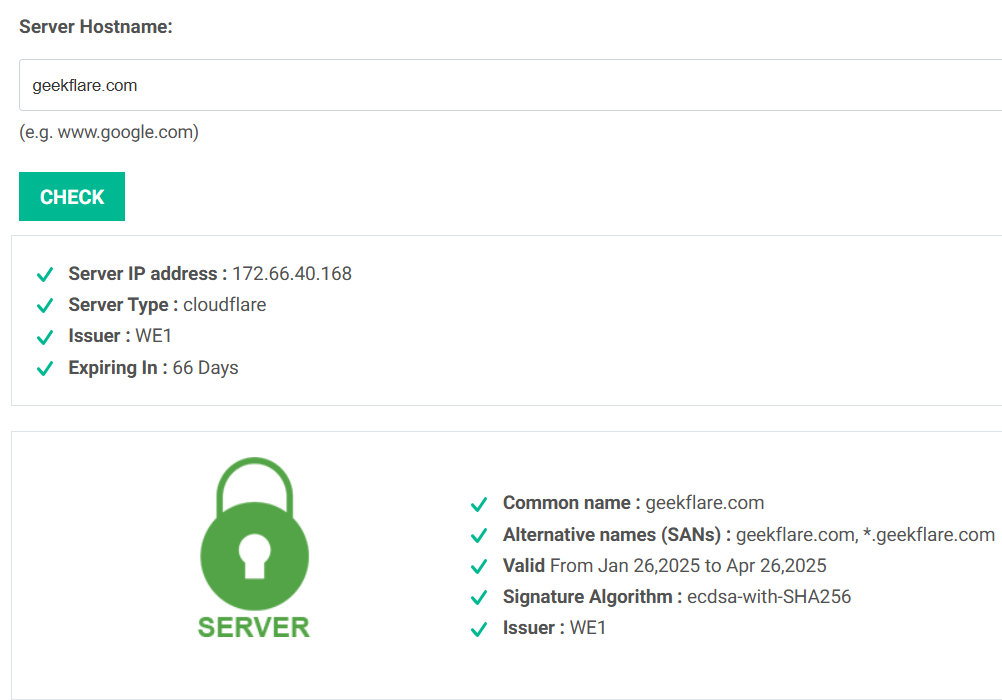
You just enter your website URL and click “Check” to instantly confirm your SSL setup and trustworthiness.
8. ImmuniWeb SSL Security Test
ImmuniWeb SSL Security Test helps you evaluate the security and compliance of your website’s SSL/TLS certificates. It provides in-depth analysis, including certificate validation, protocol support, and vulnerability detection against common threats like Heartbleed and POODLE.
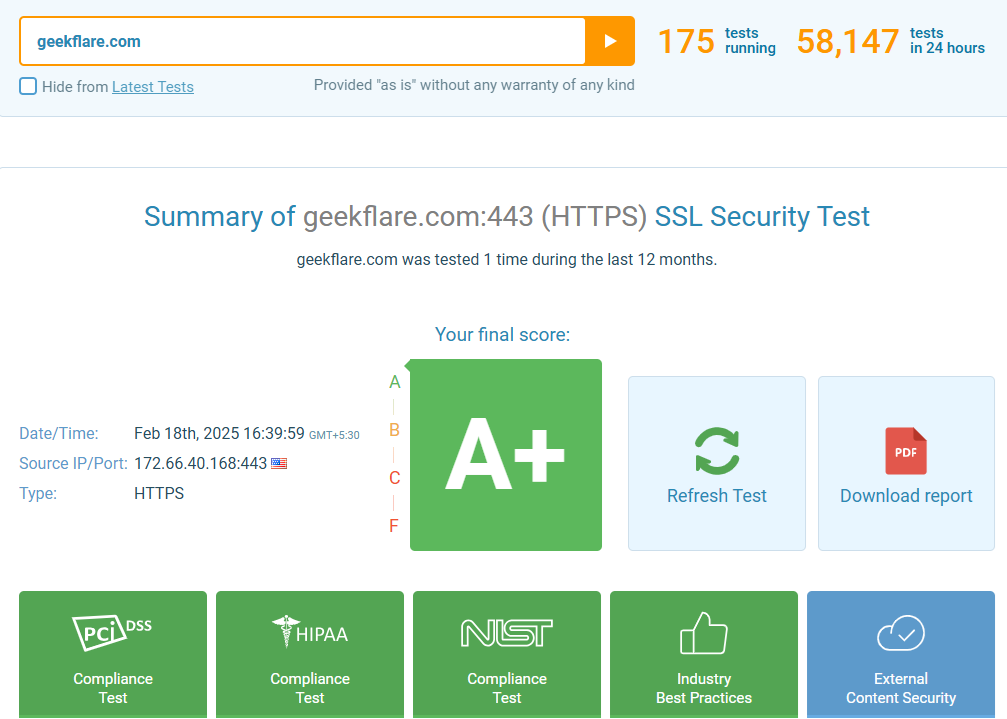
It also checks GDPR, PCI DSS, and HIPAA compliance, making it useful for organizations that prioritize cybersecurity.
9. SSLShopper SSL Checker
SSL Checker by SSL Shopper helps you to check certificate issuer, expiry details & chain implementation. This can be handy for visualizing the chain cert implementation.
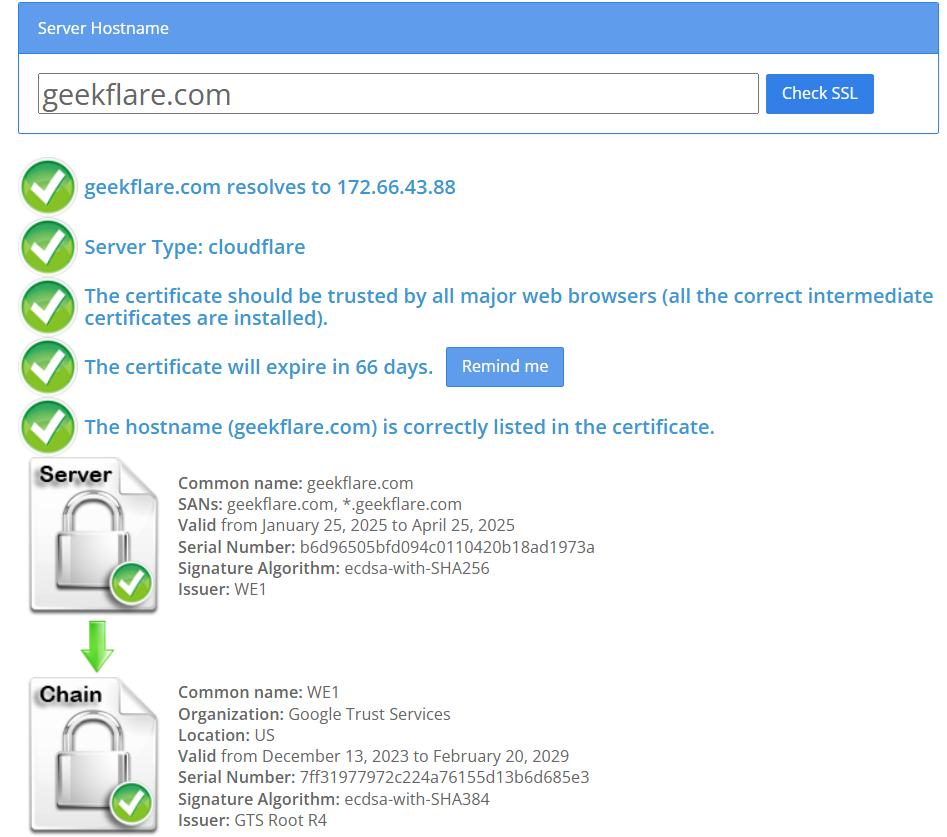
It provides detailed insights into the certificate issuer, expiration date, and supported encryption algorithms, ensuring websites maintain secure HTTPS connections.
10. MDN HTTP Observatory
MDN HTTP Observatory is a tool developed by Mozilla to help web developers assess and enhance the security of their websites.
It analyzes a site’s HTTP headers and other key security configurations, like TLS cipher details, certificate details, and OWASP-recommended secure headers, providing an overall score and grade and actionable recommendations to improve security.

It also has the option to show third-party scan results from SSL Labs, ImmuniWeb, HSTS Preload, Secure Headers, and CryptCheck.
11. SSLChecker.com
SSLChecker.com is a very basic tool that gives you information about the website’s SSL certificate, SSL errors, if any, expiry date, issuer name, and location. The tool also lets you set a reminder to renew your SSL certificate.
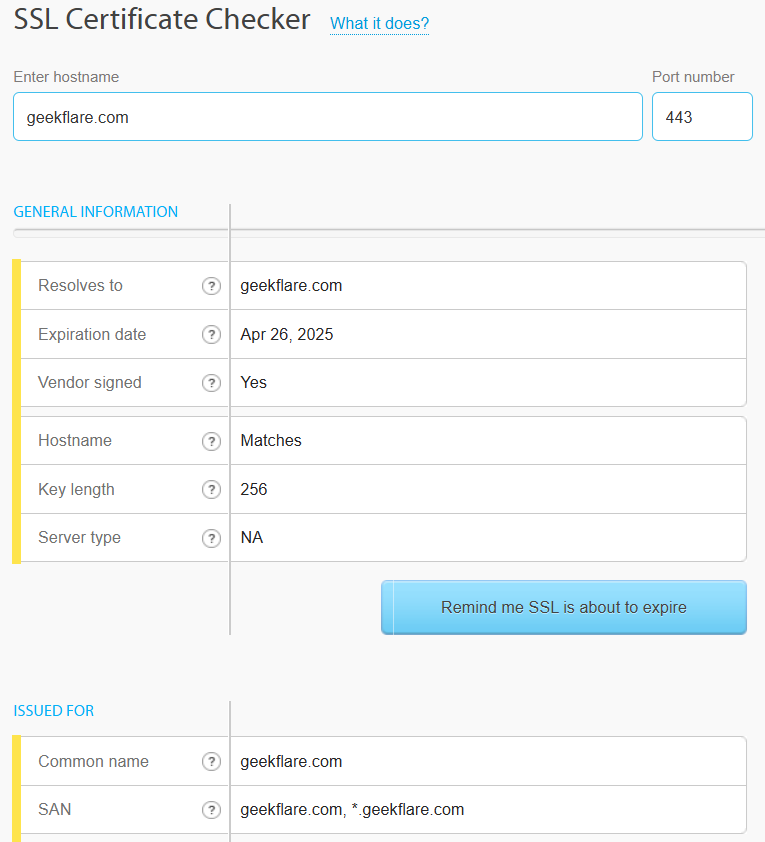
It also gives the certificate chain to establish trust, so that you can verify the authenticity of a website you are dealing with.
12. SSL Diagnos
SSL Diagnos is an open-source tool that evaluates the security of SSL/TLS implementations on servers and clients. It provides detailed information on supported protocols—such as PCT, SSLv2, SSLv3, TLS, and DTLS—and cipher suites, helping users assess their systems’ security. The tool supports protocols like POP3S, SIP, SMTP, and explicit FTPS, making it versatile for various applications.
It also includes tests for known vulnerabilities like Heartbleed (CVE-2014-0160) and BEAST (CVE-2011-3389), aiding in identifying and addressing potential security risks. It offers a companion tool, SSLPressure, which operates independently of OpenSSL to evaluate the full range of possible SSL protocols on a server.
13. GocertsSSL SSL Checker
GeoCerts SSL Checker installation tool allows users to verify the status, validity, and configuration of their SSL/TLS certificates. Users can check for common SSL issues like expiration dates, certificate chain errors, and misconfiguration by entering a domain name.
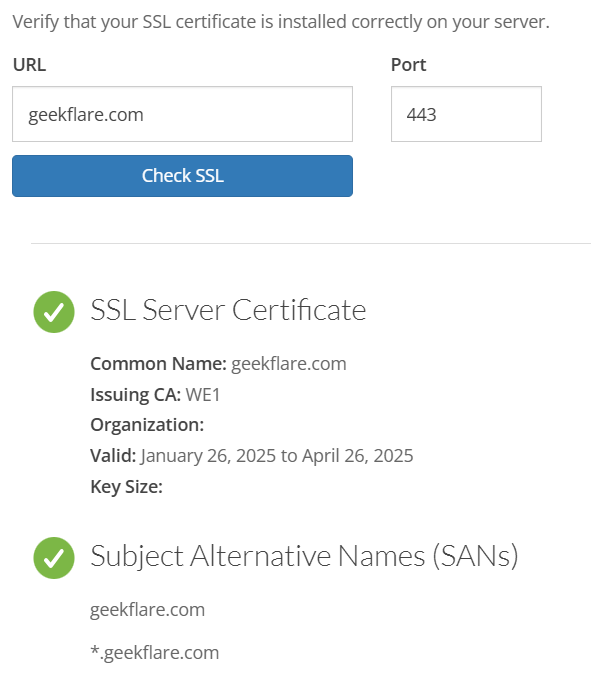
It provides essential details like issuer information, encryption algorithms, and protocol support to ensure a website’s security compliance.
14. TLS-Scan
TLS-Scan is a non-blocking SSL/TLS scanner that evaluates server TLS configurations. It retrieves certificate details and outputs metrics in JSON format, including:
- Hostname verification checks
- TLS compression checks
- Cipher and TLS version enumeration checks
- Session reuse checks
It supports protocols like TLS, SMTP, STARTTLS, and MySQL. The output can be integrated into log analyzers such as Splunk or ELK. Pre-built binaries are available for Linux and macOS platforms.
15. testssl.sh
testssl.sh is a free, open-source command-line tool that checks a server’s SSL/TLS configuration on any port. It provides detailed information on supported ciphers, protocols, and potential vulnerabilities, ensuring your encryption settings meet current security standards.
It is compatible with Linux, macOS, FreeBSD, NetBSD, and Windows (via WSL, MSYS2, or Cygwin).
16. OpenSSL CSR Wizard
DigiCert’s OpenSSL Certificate Signing Request (CSR) Wizard simplifies generating a CSR for your server. By inputting details such as your domain name (Common Name), organization, city, state, and country, the wizard creates a customized OpenSSL command tailored to your specifications.
17. Domsignal Mixed Content Checker
If you’ve moved your website from HTTP to HTTPS, make sure all resources (JS, CSS, images, etc.) load over HTTPS. Otherwise, users may see a “Mixed Content” warning. To check for insecure resources, use the Mixed Content Checker by DomSignal.
This tool scans your site for mixed content issues—when secure (HTTPS) pages load non-secure (HTTP) resources—which can create security risks and trigger browser warnings.
18. SSL Shopper CSR Decoder
SSL Shopper’s CSR Decoder is a tool that decodes your CSR, allowing you to verify its contents before submitting it to a Certificate Authority.
After providing the CSR input, it displays the embedded information, such as the organization name, domain, and public key details, ensuring accuracy and completeness. This verification helps prevent potential issues during SSL certificate issuance.
Verification tools are very handy when you have generated CSR with SAN (Subject Alternative Name) or wildcard and are unsure if CSR has picked them.
19. SSLyze
SSLyze is a Python library and command-line tool that connects to an SSL endpoint and performs a scan to identify any SSL/TLS misconfiguration. It evaluates encryption settings—including certificates, cipher suites, and elliptic curves—and checks for vulnerabilities to known TLS attacks such as Heartbleed and ROBOT.
It supports non-HTTP servers, including SMTP, XMPP, LDAP, POP, IMAP, RDP, Postgres, and FTP. Users can integrate SSLyze into CI/CD pipelines to monitor server compliance with Mozilla’s recommended TLS configurations.
Scan through SSLyze is fast as a test is distributed through multiple processes. It offers a fully documented Python API, enabling developers to run scans directly from Python applications. The tool is open-source and available under the AGPL-3.0 license.
SSLyze is also available in Kali Linux. If you are new to Kali then check out how to install Kali Linux on VMWare Fusion.
20. SSLLabs Scan
The SSLLabs Scan tool is a command-line client developed by SSL Labs. It interfaces with their assessment APIs, enabling automated and bulk testing of SSL/TLS configurations on public internet servers.
This tool is handy for system administrators and security professionals who want to integrate SSL/TLS testing into automated workflows and continuous monitoring systems. It allows for comprehensive server security analysis by initiating assessments and retrieving detailed reports directly from the command line.
21. SSL Scan
SSL Scan is an open-source command-line tool that assesses SSL/TLS-enabled services by identifying supported cipher suites, protocols, and key exchange methods. It provides detailed information about a server’s SSL/TLS configuration, including certificate details and potential vulnerabilities like Heartbleed.
It supports various platforms, including Linux, Windows, and macOS. The tool is open-source and actively maintained, with the latest release being version 2.1.6.
22. SSL Converter
The SSL Converter tool from SSL Checker allows you to easily change your SSL certificate between formats like PEM, DER, PKCS#7, and PKCS#12. This functionality is essential for server compatibility and certificate management. You can upload their certificate files and select the desired output format for quick and efficient conversion.
23. SSL Shopper Certificate Decoder
SSL Shopper’s Certificate Decoder decodes PEM-encoded SSL certificates, allowing you to verify their contents and ensure they contain the correct information.
After providing your certificate information, it will display details such as the issuer, subject, validity period, and public key information to confirm certificate details before installation or troubleshooting issues with existing certificates.
24. Mozilla SSL Configuration Generator
The Mozilla SSL Configuration Generator is a tool that allows you to create optimized SSL/TLS configurations for various server software. By selecting your specific server (e.g., Apache, Nginx, HAProxy) and desired compatibility level—Modern, Intermediate, or Old—the generator provides tailored configuration snippets that align with Mozilla’s security guidelines.
Conclusion
I hope the above-listed free online tool is sufficient to validate the SSL certificate parameter and gives useful technical information for auditing to keep the web application secure. If you are looking to learn in-depth about SSL/TLS operations, then check out these Udemy courses.

