Learn the features of the WebKnight web application firewall for the IIS and installation procedure.
As a Middleware administrator, web engineer – you may have to work on the IIS web server and if you are given the responsibility to manage the production environment then at some point you need to deal with security.
If you are new to the Microsoft IIS web server, then you may check out this online course.
The vulnerability report by Acunetix on the IIS Web Server shows that 7% of sample targets were vulnerable.

The securing web application is always challenging considering the increase in online threats. You should consider all the possibilities to keep your website secure from the hacker. If you are looking to secure a site hosted on IIS, then you may consider using WebKnight WAF.
WebKnight is an open-source web application firewall for the IIS web server by AQTRONiX. It helps to block malicious requests by scanning all the requests reaching the IIS.
Let’s go through some of the features it has before jumping into the installation procedure.
- Administration interface – useful to manage WebKnight and statistics
- Logging – log blocked or all requests processed by WebKnight
- Compatibility – use with WebDAV, Cold Fusion, OWA, Share Point, etc.
- Brute force attacks protection
- Block IP – useful to block incoming request from a certain IP when you know it’s malicious
- Hotlinking protection
- Robots blocking
- Scan GET and POST payloads
- Run-time update – no need to restart IIS when you make changes to WebKnight
- SSL sessions encryption
- SQLi, XSS, CSRF, Information leakage protection
I hope now you have an idea what WebKnight WAF can do so let’s proceed with the installation.
WebKnight is compatible with all the major latest versions of IIS 5, 6, 7, 7.5, 8, 8.5 & 10.
Pre-requisite
- The supported version of IIS must be installed
- ISAPI filters and extensions must be enabled
How to enable ISAPI filters & extensions?
Skip this and go to next if you already have this enabled. Below instruction is for Windows 8
- Go to Control Panel >> Program and Features
- Click “Turn Windows features on or off”
- Expand “Internet Information Services” >> World Wide Web Services >> Application Development Features and select ISAPI Extensions & Filters

- Click OK
Download & Install WebKnight
The first thing you need to do is to download the WAF by going to the official URL. Download the latest version (as I write it’s 4.4). It will download in zip format.

Extract the downloaded zip file, and it will create a new folder – WebKnight.4.4
- Go inside the WebKnight.4.4/Setup/x64
- Double click on WebKnight windows installer to start the installation
- Click next

- Accept the license agreement
- Select the “Complete” and click Install

- It may take a few minutes and once done; you will get completion message.
- Select “Launch Configuration Utility” and click Finish
This concludes you have installed a WebKnight web application firewall successfully and the default configuration is ready to protect your IIS Web Server.
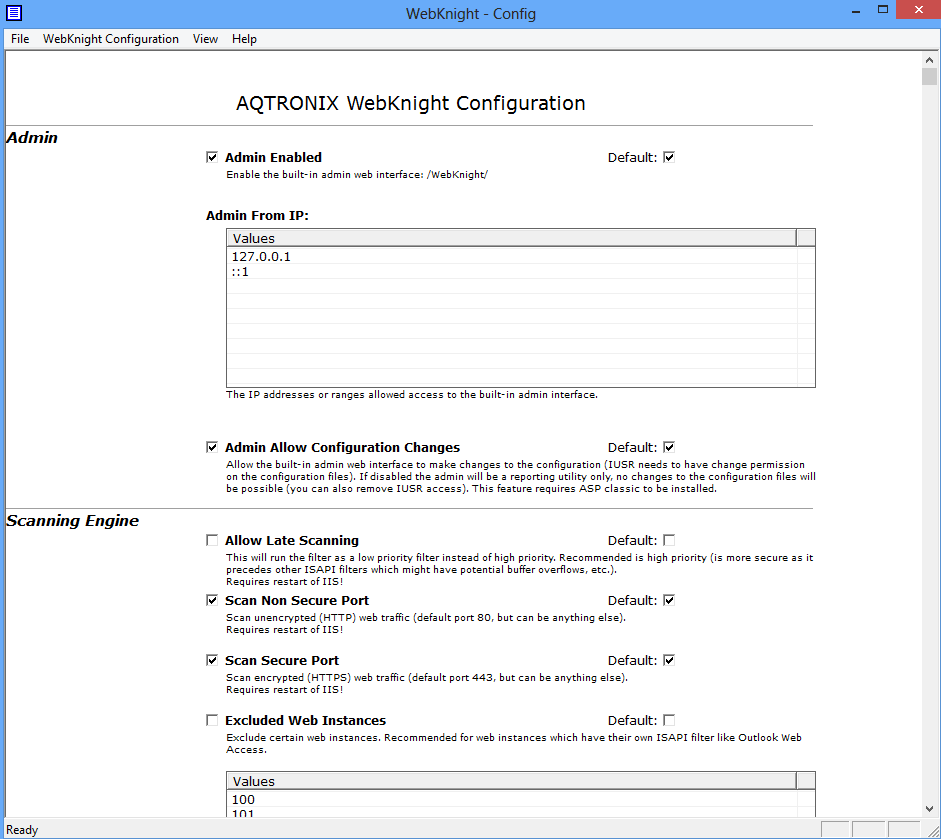
Now you can tweak the configuration based on your needs. Let’s go through some of the essential configurations.
Logging
by default, it will write only blocked requests however if you wish to write all the logs then scroll down to Logging section and select “Log Allowed”.
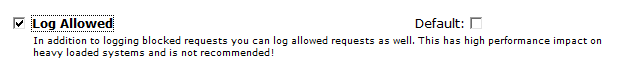
In the logging section, you can also enable other metrics like User-Agent, X-Forwarded-For, etc.
Method
GET, HEAD & POST is enabled if you need to allow another method then scroll to the Methods section and add them.
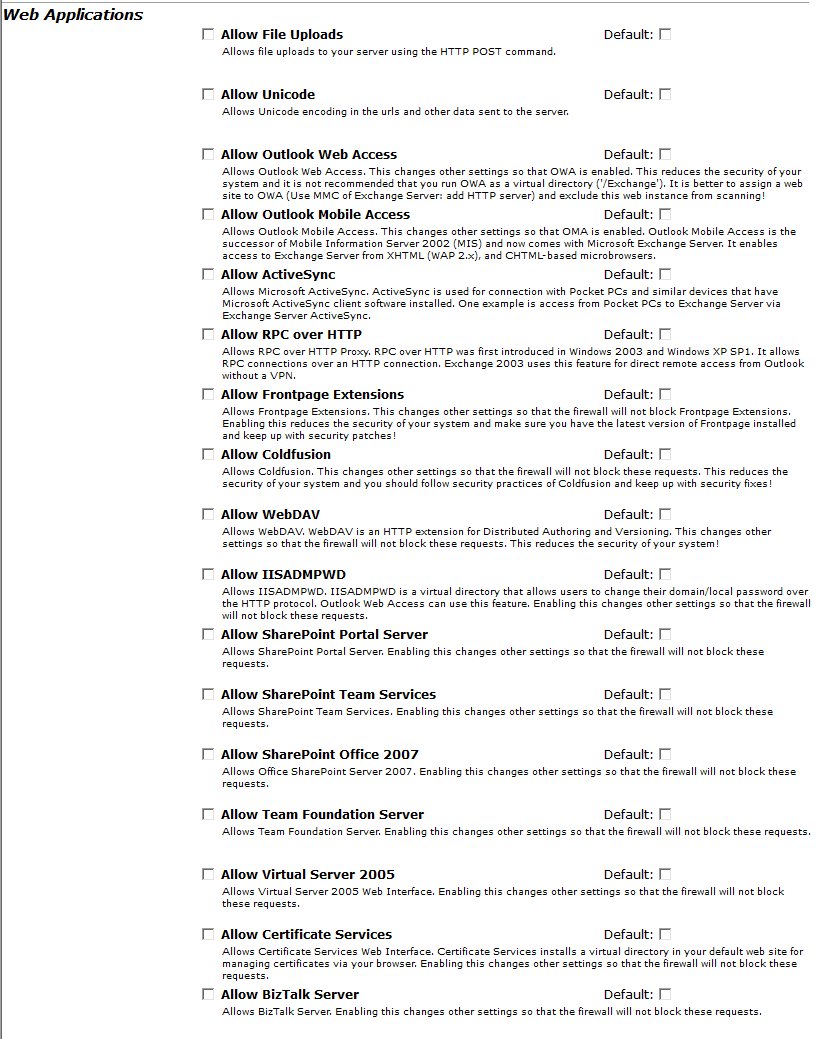
Web Applications
As mentioned earlier, WebKnight is compatible with other applications and select the one you need in this section.
Whenever you make changes, you must save by going to File >> Save for configuration to be active.
Let’s try some malicious requests to see how this WAF handles.
Script execution
I tried /?<script>xss attack</script> in the URL and it blocked.
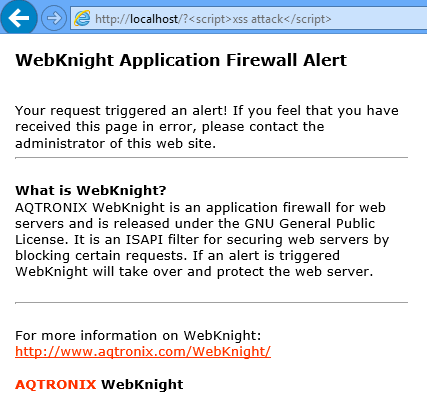
Well done!
Let’s see the log
2016-08-31 ; 14:05:46 ; W3SVC1 ; OnPreprocHeaders ; ::1 ; ; localhost ; GET ; /?<script>xss%20attack</script> ; BLOCKED: URL is not RFC compliant ; / ; <script>xss%20attack</script> ; BLOCKED: Parameter name not valid '<script>xss attack</script>' ; BLOCKED: '<script' not allowed in querystring ; HTTP/1.1 ; Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; WOW64; Trident/6.0) ; ; MONITORED: IP address (previous alert) ; Referer: '' ; User-Agent: 'Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; WOW64; Trident/6.0)' ; From: '' ; Accept-Language: 'en-US' ; Accept: 'text/html, application/xhtml+xml, */*' ; Content-Type: ''So as you can see in the log, it blocked because URL is not RFC compliant.
WebKnight open-source WAF for IIS looks promising, and default configuration protects web servers from various security attacks.
Try out to see if this is something you are looking for. If not you can always leverage cloud-based security providers like SUCURI for complete website security solutions.

