You are a potential victim of Wi-Fi Pineapple attacks if you use public Wi-Fi networks without observing safe online practices.
While security professionals can use the Wi-Fi Pineapple device to conduct penetration testing, criminals can use the tool illegally to execute man-in-the-middle attacks, evil portals, fake HTTPS, and other exploits.
In this article, you will learn about the Wi-Fi Pineapple device, understand what it is, and how to use it legitimately to identify security vulnerabilities.
We will also see how criminals can use the device illegally to steal sensitive information from unsuspecting users. So, let’s start.
What is Wi-Fi Pineapple?
Wi-Fi Pineapple is a portable, penetration-testing device for identifying vulnerabilities in wireless networks. The Wi-Fi pineapple devices are almost similar to standard wireless access points.
However, they have more power, longer ranges, and a higher number of supported devices. The devices have additional features designed to perform penetration testing and network auditing.

During the tests, professionals can legally simulate password cracking, rogue access points, man-in-the-middle attacks, and more. This allows them to identify and address vulnerabilities in wireless networks.
Generally, the device is readily available, easy to use, and inexpensive. Penetration testers, ethical hackers, and cybercriminals can use the pineapple device for various reasons.
When used legitimately, the device provides a powerful network auditing tool. However, criminals can use it to illegally spy network traffic and execute various Wi-Fi pineapple attacks that allow them to steal private data or compromise user devices.
Popular Wi-Fi Pineapple Attacks
Cybercriminals can use the Wi-Fi pineapple to intercept the network traffic as it flows between a device and the internet. Since it can listen and pass the information unchanged, it is difficult for users to know when they are under attack or when someone is stealing their personal data.
Usually, a Wi-Fi-enabled device will continuously broadcast some information as it attempts to find available Wi-Fi networks. Once the pineapple device captures the broadcasted wireless networks, it can rebroadcast and inform the user’s device that the networks are available. However, these are fake wireless access networks with the same name.
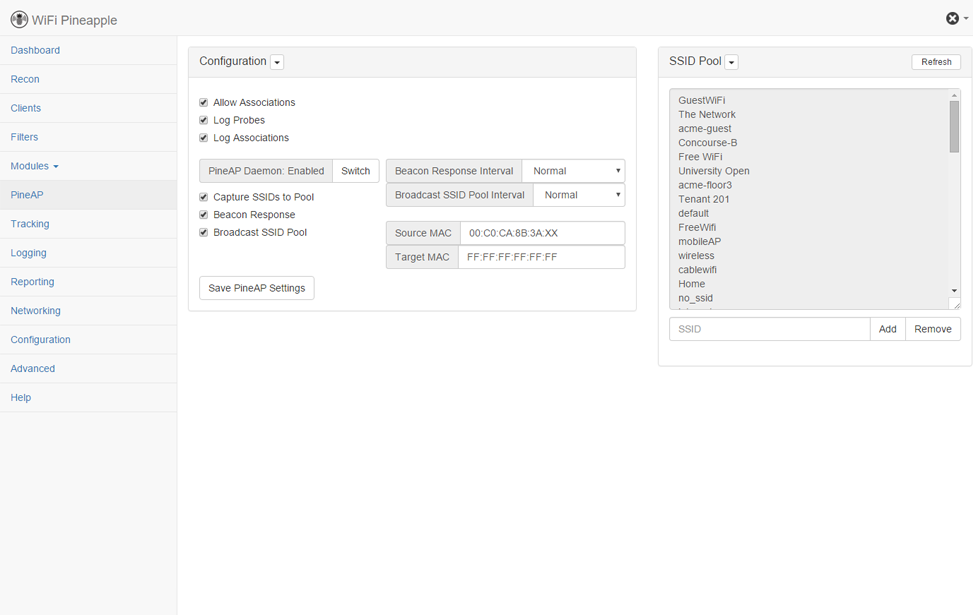
The user will then connect to the fake network, usually without providing a password. If the device is set to automatically connect to available wireless networks, it will automatically connect to the fake access point controlled by the criminals without any user input.
Once you connect to the compromised public wireless network, the criminals can capture and steal passwords, credit card details, and other sensitive information as it flows between your device and the internet.
Additionally, once on the rogue access point (RAP), the criminals can redirect you to a fake logging portal or server they control. For example, they can direct users to fake websites like Amazon, eBay, Facebook, or other popular sites.
The attacker will then steal private information such as login credentials, credit card details, addresses, and other data the user submits.
Some of the main Wi-Fi pineapple attacks include:
#1. Man-in-the-middle (MITM) Attacks
Using the Wi-Fi pineapple device, the criminals can create a fake access point that allows them to execute man-in-the-middle (MITM) attacks. Initially, they will trick a user into connecting to the internet using a fake wireless network that they control.
In this attack, the criminals will quietly intercept and relay the traffic between the victim’s device and the internet, often stealing sensitive information such as passwords, banking details, and other sensitive data. The bad actors can then use the private data to make illegal transactions or use the banking or credit card details to steal or transfer money from the victim’s accounts.
#2. Wall of Sheep
If users access a network without protecting their identity, an admin or someone listening to the network activities can see the sensitive information, such as the username and password. The Wall of Sheep is a demonstration where security professionals or hackers display a list of devices, websites visited, and sometimes login credentials users submit over insecure public networks.
The Wi-Fi pineapple has a Wall of Sheep feature (DWall) that, when enabled, allows administrators or criminals to eavesdrop on the user’s activities, including visited websites and private information submitted. It usually occurs when users send unencrypted data over wireless networks.
The idea of the Wall of Sheep is to shame users and help them practice safe online practices. For testing or warning purposes, the list is displayed on a large screen where everyone can see the exposed information. However, attackers can use the same strategy to steal private information and compromise the affected accounts and devices.
#3. Evil Portal Attacks
In this attack, the criminals create a fake website that looks similar to a genuine one. As users try to connect to the legitimate site via a public wireless network, the attackers direct them to the fake website.
The evil portal emulates popular and trustworthy websites, login pages, and other platforms accessible over the internet. For example, criminals can create a social media or e-commerce website such as Walmart, eBay, or Amazon and then direct users there.
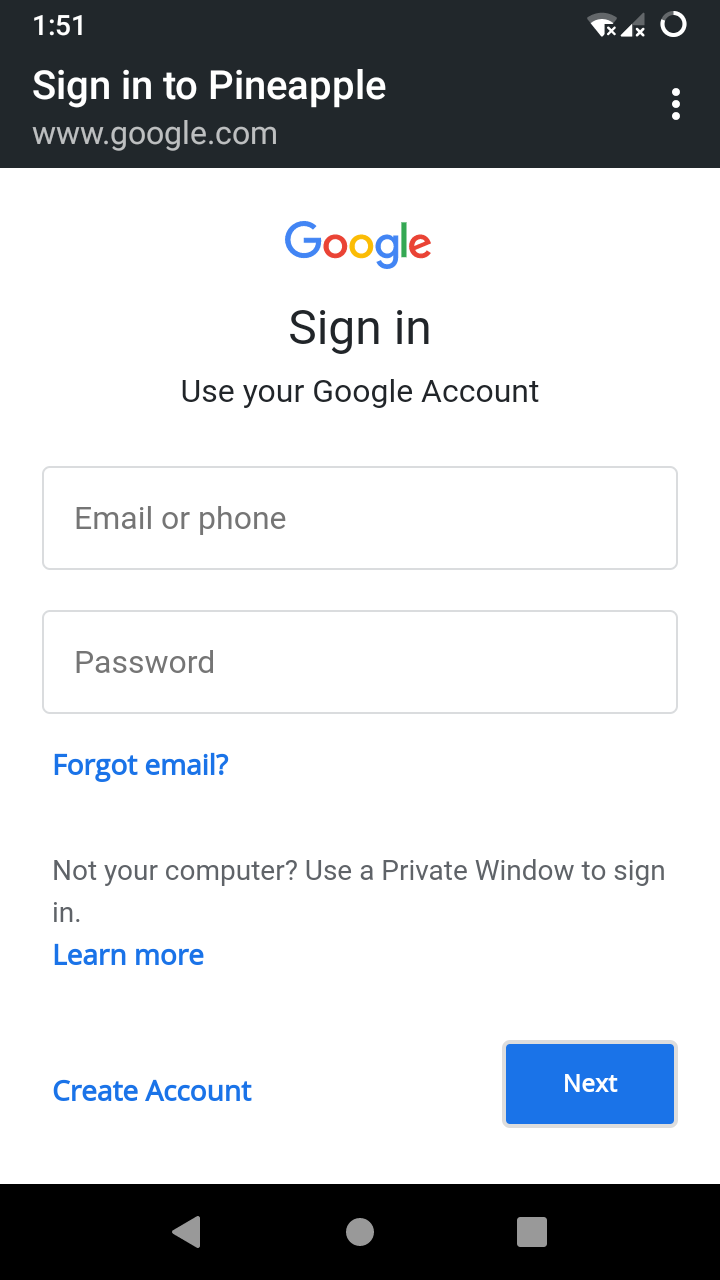
Almost similar to the MITM attacks, the technique allows criminals to steal usernames, passwords, credit card information, phone numbers, addresses, and any other sensitive data the victim submits on the fake website. Additionally, they can infect the user’s device with malware or viruses.
#4. Fake HTTPS
Secure websites often use the HTTPS protocol to encrypt data and protect the websites and their users. In the fake HTTPS exploit, a hacker, using the Wi-Fi pineapple, sits between the user and the website.
When a user requests a website (most do not add HTTPS), the communication uses the less secure HTTP connection to the attacker. The attacker then connects the user to the less secure HTTP version of the website. In such a communication, the data is transmitted as plain text, and the attacker can see sensitive information.
Protection Against Wi-Fi Pineapple Attacks
Protecting yourself against Wi-Fi pineapple attacks requires practicing safe online activities and avoiding most public wireless networks unless unavoidable. Below are some of the main ways to remain safe:
- Do not connect to unsecured public wireless networks. Most criminals will offer free Wi-Fi, which most often doesn’t require a password to join. However, it may request that you register with an email address and, preferably, a password. And as usual, most users prefer using the same password for all accounts to avoid forgetting. This allows attackers to steal personal information such as account names, email addresses, usernames, passwords, credit card details, and any other information you may submit.
- Avoid connecting to insecure websites and giving sensitive personal information such as passwords, banking information, etc. For this, you need to ensure that you only connect to websites that use HTTPS, and you can verify this by the green lock icon at the beginning of the URL.
- Use a VPN (virtual private network), which protects the data by encrypting it before transmitting it over the internet. In such a case, even if the device connects to the pineapple, the criminals cannot read the data in transit. Most VPNs provide end-to-end encryption such that no one can decipher or read the information flowing between a device and the internet, even if you are connected through a fake pineapple AP.
- Ensure that you are connected to a Wi-Fi network that corresponds to your physical location. Otherwise, you should be suspicious if you are connected to a work wireless network while working at home or away from the office. It is important to note that the Wi-Fi Pineapple can generate fake network names or SSIDs based on what the laptop or mobile device is broadcasting.
- Always forget the public wireless networks saved on your device. This prevents the device from broadcasting the saved networks and thus denying the criminals the ability to capture the information and create fake access points that your device may automatically connect to.
- Disable the automatically connect option and Wi-Fi radio whenever not in use. This ensures that your device does not automatically connect to available wireless networks. If you leave the setting on, your device will continuously broadcast the saved wireless SSID or network names, and attackers can use the Wi-Fi pineapple to establish the name. They will then create a wireless network with the same name, and your device will automatically connect to the fake AP, allowing criminals to capture sensitive information or direct you to a server under their control.
- Avoid accessing insecure websites, especially over public access points. Ideally, only access HTTPS-protected websites, and you can determine this by confirming that the website URL has a HTTPS if it has a green icon just before the URL. Some browsers may warn you whenever you try to access an insecure website without HTTPS. If you must access a website without HTTPS, use a VPN or avoid submitting sensitive information such as banking details, usernames, passwords, and other private data.

Wi-Fi Pineapple Penetration Testing Device
The Wi-Fi Pineapple is a powerful penetration testing tool that enables network professionals to identify and address security vulnerabilities in wireless networks. It is an inexpensive device that enables security teams to legally hack into their networks and identify vulnerabilities attackers can exploit.
The Wi-Fi Pineapple has an easy-to-use interface and several downloadable modules to audit wireless networks and identify vulnerabilities. For example, the free downloadable PineAP suite includes various tools for tracking, logging, sniffing traffic, conducting MITM attacks, cracking passwords, reconnaissance, and more.
Penetration testing is an authorized hacking practice that organizations can use to detect and address security vulnerabilities. However, the device is open to potential abuse, such as executing main in the middle (MITM) and other attacks if in the hands of bad actors.

Ideally, the pineapple allows ethical hackers to perform penetration testing and audit the security systems. While it provides various benefits, bad actors can misuse the tool by launching various malicious activities that allow them to steal private data from unsuspecting victims.
What to do if compromised in a Wi-Fi pineapple attack?
In case you fall victim to a Wi-Fi pineapple attack, you need to take some measures to prevent further damage.
- Change the passwords for all compromised accounts, especially those you accessed using the fake network. Additionally, enable multifactor authentication if it is not already active.
- Inform the institutions, such as the bank or credit card company with a compromised account, so that they can stop any new transaction until you are safe to do so.
- Install and update antivirus, antimalware, and other relevant security solutions. Afterward, scan your computer and clean it to see if it has been infected or compromised.
- Update your operating system, applications, and security software.
- If the data has been compromised, you may need to restore it from a clean backup.
Conclusion
The Wi-Fi Pineapple devices provide a powerful and effective network auditing tool. It can monitor network traffic, simulate several cyberattacks, and help security professionals identify vulnerabilities. However, criminals can use it to spy on network activities, perform MITM, fake portals, and other attacks that allow them to steal sensitive information such as usernames and passwords, credit card details, banking details, and other private data.
Usually, it is very easy to fall victim to Wi-Fi pineapple attacks unless one is very careful. One way to remain safe is to avoid public Wi-Fi networks. When this is unavoidable, you can use a VPN to encrypt the data and prevent criminals from stealing the information.
Besides using a VPN, it is best practice to use strong passwords, enable multifactor authentication, only visit HTTPS-enabled websites, be vigilant when using public wireless networks, and more. Additionally, disable the automatic connection, and always turn off the Wi-Fi radio on your device when not in use.
Next, check out the best Wi-Fi analyzer software for small to medium business networks.

