Unified Endpoint Management (UEM) software is becoming indispensable for IT teams managing a mix of company devices. As businesses embrace remote work and BYOD policies, UEM tools provide a single platform to manage and secure all endpoints like PCs, laptops, smartphones, tablets, IoT devices and more.
Choosing the best UEM software is a critical decision to streamline IT operations, strengthen security, and reduce costs. In this guide, we’ll explore the top UEM solutions, their core features and drawbacks, and answer common questions about UEM vs. MDM and how to pick the right platform.
UEM Software Filter
1. NinjaOne
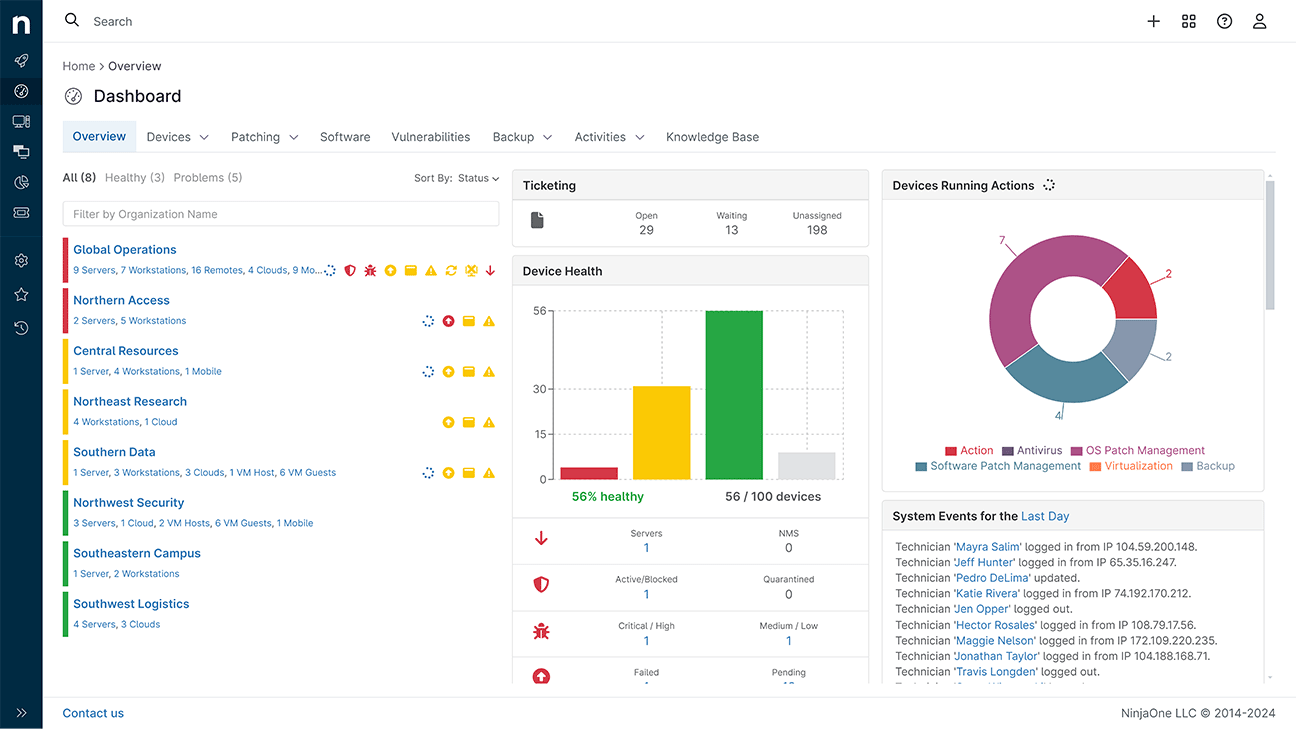
NinjaOne is a top-rated unified IT management platform popular among managed service providers (MSPs) and IT departments. It combines endpoint monitoring, remote management, and mobile device management into a cloud-based solution. NinjaOne is known for its ease of use and fast deployment, with no on-premises infrastructure needed.
SMBs appreciate NinjaOne’s all-in-one approach to device monitoring, patch management, software deployment, and backup. The platform also offers strong automation capabilities and integration with popular tools like CrowdStrike, HaloPSA, Okta, PagerDuty, etc.
Key Features
- Provides real-time health monitoring for all endpoints and automatically alerts technicians to issues so they can respond quickly.
- Supports automated patch deployment for Windows, macOS, Linux, and over 6000 3rd-party applications to reduce security risks.
- Offers one-click remote control to troubleshoot Windows or Mac endpoints from anywhere.
- Includes endpoint backup features to protect important files on distributed devices. This ensures business data on laptops or remote PCs can be restored in case of loss or ransomware.
- NinjaOne’s multi-tenant architecture lets service providers manage multiple client organizations under one console, with role-based access controls for each.
Limitations
- While NinjaOne covers essential UEM functions, some users note it lacks the advanced scripting and custom policy depth found in larger enterprise UEM.
- NinjaOne is a fully hosted SaaS platform. Organizations seeking an on-premises UEM solution because of compliance, would need to choose a different product.
NinjaOne pricing is per device and offers a free trial.
2. Action1
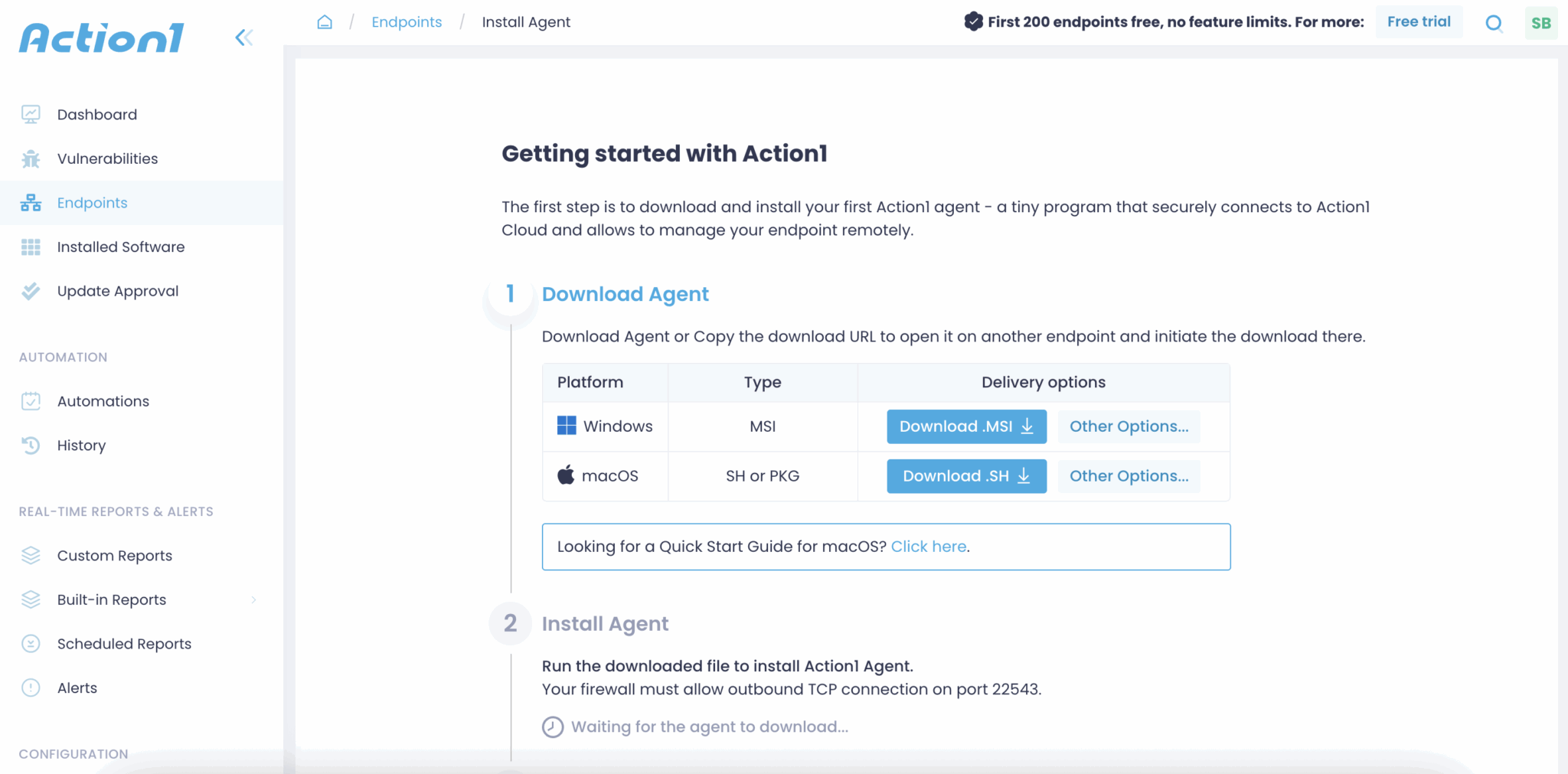
Action1 is a trusted unified endpoint management solution that automates cross-OS and third-party vulnerability remediation. It simplifies continuous patch compliance for both servers and workstations.
The platform provides a comprehensive inventory of hardware and software assets, enabling you to make informed decisions for endpoint management. You can also automate various IT tasks on endpoints with its rich script library or run your own custom scripts.
I liked Action1’s quick setup. You can begin patching endpoints in just 5 minutes and scale easily to any number of devices.
Being cloud-native, it removes the need for clunky integrations or legacy tools. You can even support users directly from your browser without a business VPN.
I also found its pre-configured report templates useful for creating detailed custom reports to monitor IT environments and pass compliance audits. Action1 includes role-based access control (RBAC), SSO, and MFA.
The company runs data centers in the USA, Europe, and Australia, ensuring compliance with regional data storage requirements.
It is compliant with SOC 2 Type II and ISO 27001:2022. So you can trust its security.
Key Features
- Automates patching, issue resolution, and configuration. This can enhance security and compliance while reducing your IT overhead costs.
- Offers a private repository with automated patching coverage for Windows, macOS, and third-party software. You can also patch customized software.
- Comes with built-in vulnerability remediation that helps you find vulnerable software and OS in real-time.
- Follows P2P distribution to minimize external bandwidth usage and offer faster deployment of large patches.
- Lets you get instant visibility into vulnerabilities, missing updates, and real-time patching progress. You can also view SLA-based patch compliance through a live dashboard.
I really like Action1’s wide integration support. You can easily integrate it with Entra ID, Okta, Duo, Google, and more. You can connect it with other tools via REST API or PowerShell scripting.
Limitations
- No free trial, though the company offers patch management for the first 200 endpoints free forever without any functional limitation.
- Support is available only via the Action1 Discord server for the free endpoints.
Action1 follows customized pricing. You need to contact the company for a pricing quote.
3. ManageEngine Endpoint Central
ManageEngine Endpoint Central is a powerful UEM and security solution by Zoho. It is known for its rich feature set tailored to Windows-centric environments, while also supporting macOS, Linux, iOS, Android and others. ManageEngine Endpoint Central allows you to manage all desktops, servers, laptops, and mobile devices from a single interface.
You can deploy Endpoint Central on-premises or use a cloud service, giving flexibility to those with strict data control requirements. It is a cost-effective solution and suitable for mid-sized enterprises.
As an IT manager, you can manage endpoints right from your Android and iPhone.
Key Features
- Built-in compliance auditing tracks and reporting. This is useful for regulatory compliance and internal security audits.
- Automates patching of OS and 3rd-party applications, OS imaging and deployment, and software distribution. Endpoint Central also includes IT asset management tools to track hardware/software inventory and licenses.
- Offers integrated security controls like BitLocker drive encryption management, USB device usage controls, antivirus definition updates, and ransomware detection.
- IT admins can remotely access and control any managed desktop or mobile device to assist users. It includes remote command prompt, file transfer, and chat for efficient support.
- Endpoint Central includes full MDM capabilities like configuring Wi-Fi, VPN, email profiles, deploying apps on mobile devices.
Limitations
- The management console can feel overwhelming. It may take significant time and training to master all modules.
- Certain advanced features like vulnerability scanning, data loss prevention, browser security are only available in the Security Edition which costs over 50% more than the UEM Edition.
- Subscription covers minimum 50 endpoints, not suitable for very small teams.
Endpoint Central has 4 subscriptions plans.
| Subscription Plan | Starting Price (base) | Good for |
|---|---|---|
| Professional Edition | $795/year | Patching, BYOD management |
| Enterprise Edition | $645/year | + Audit remote session, License management |
| UEM Edition | $1095/year | + OS deployment, Remote data wipe |
| Security Edition | $1695/year | + Vulnerability management, DLP, Privilege management |
4. Scalefusion
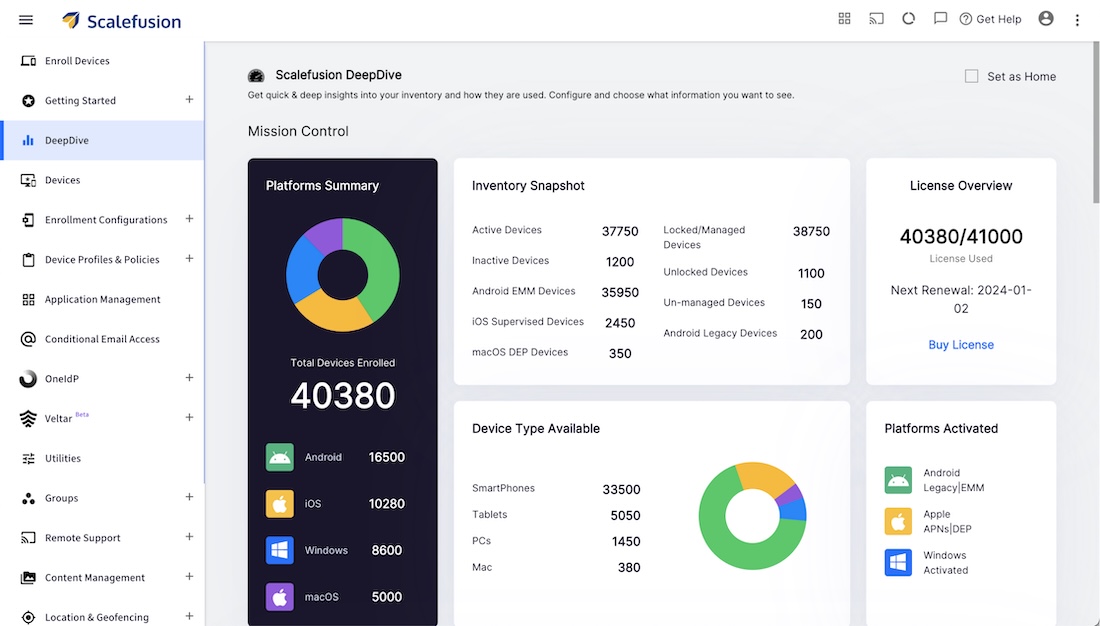
Scalefusion is a modern UEM solution built for mobility and ease of use. It is ideal for SMBs in industries like retail, logistics, healthcare. It integrates a zero-trust approach to enhance endpoint security.
You can manage Android, iOS, Windows, macOS, Linux, ChromeOS, Android TV, and Apple devices from a single intuitive dashboard. It allows you to enforce policies on company-owned devices as well as BYOD scenarios.
The enterprise plan includes AirThink AI, which helps administrators to generate custom scripts for supported OS.
Key Features
- Lock down devices into single-app or multi-app kiosk mode for business-specific usage (ideal for retail, restaurants, or field services). It also supports managing rugged devices (Zebra, Honeywell, etc.) and peripherals.
- IT admins can remotely cast a device screen and control it to troubleshoot issues in real time. You can also perform remote command execution (e.g., reboot device, update config) and a secure messaging with users.
- Push apps and content to devices. It provides an enterprise app store for users. Admins can manage app permissions and create compliance rules for allowed/disallowed apps.
- Detailed reports and dashboards provide insight into device compliance, usage, and potential security risks to make data-driven decisions.
Limitations
- Minimum 10 devices subscriptions are needed.
- AI & on-premises connector is available only in Enterprise plan.
- Essential plan includes only 1 administrator.
Scalefusion UEM has 4 pricing plans and affordable for small business.
| Plans | Pricing | Good for |
|---|---|---|
| Essential | $2/device/month | Basic device management, Kiosk mode, basic reports |
| Growth | $3.5/device/month | + Advanced management including BYOD, Content management |
| Business | $5/device/month | + Patch management, ITSM integration, Workflows |
| Enterprise | $6/device/month | + AI, Advanced RBAC, Deployment, SAML |
5. Citrix Endpoint Management
The Citrix Endpoint Management offering aimed at enterprises that require tight security and integration with Citrix’s digital workspace ecosystem. The platform excels at mobile application management and secure content delivery. It allows IT to control and protect a wide range of device types.
Citrix supports both cloud and on-premises deployments of its UEM, and it boasts over 300 granular policies for device and app management.
Key Features
- Provides a single console to manage device policies and also deliver mobile apps to users securely. IT admins can deploy apps to mobile devices and apply policies like app lockdown or remote wipe of app data via MDX technology.
- Citrix offers one of the most extensive sets of mobile security controls, including jailbroken device detection, geofencing, remote lock/wipe, encryption enforcement, and micro-VPN for secure app access.
- It integrates with Citrix Secure Hub, Secure Mail, Secure Web and other containerized apps that provide a safe environment for email, browsing, and document editing on mobile devices.
- For BYOD scenarios, Citrix Endpoint Management supports Android Enterprise work profiles and iOS User Enrollment to segregate work data on personal devices.
- Endpoint Management can integrate into Citrix Workspace, allowing unified access for users.
Limitations
- Citrix’s UEM solution is enterprise-grade and can be complex to deploy and maintain. Organizations without existing Citrix expertise may face a steep setup process.
- Lacks support for Linux, ChromeOS.
- If you only need stand-alone mobile device management without Citrix’s other products, the pricing might be less attractive compared to other UEM vendors.
6. Hexnode UEM
Hexnode UEM is an award-winning Unified Endpoint Management solution suited for SMBs. It is known for its user-friendly interface and a modular pricing model that ranges from basic mobile device management to full UEM features.
It supports all major platforms, including visionOS, Apple TV, Android TV, Fire OS, and ChromeOS. Industries like healthcare, education, and retail can choose Hexnode for its balance of functionality and affordability.
Key Features
- Ensure consistent security across all endpoints by implementing policy enforcement, passcode requirements, and encryption.
- You can lockdown devices into single-purpose kiosks or multi-app kiosk mode. This is useful for point-of-sale systems, digital signage, or any customer-facing tablets.
- Hexnode provides an enterprise app repository to deploy in-house apps or managed Google Play/Apple App Store apps to devices. App blacklisting/whitelisting helps block unwanted applications.
- Offers a range of reports like device inventory, app inventory, compliance status, device usage, etc. The UEM also integrates with ITSM, directory services, Google Workspace, Zendesk and more.
Limitations
- It doesn’t cover patch management and OS deployment as fully as Endpoint Central.
- Remote control and app management is only available in the higher plan (Ultimate).
- Minimum 15 devices subscription is needed.
Hexnode has 3 pricing plans and gives you a 14 days free trial.
| Plans | Pricing | Good for |
|---|---|---|
| Pro | $2.2/device/mo | MDM, Basic Kiosk |
| Enterprise | $3.2/device/mo | + Basic UEM, Advanced Kiosk management |
| Ultimate | $4.7/device/mo | + Advanced UEM, Enterprise integration |
7. 42Gears SureMDM
42Gears’s SureMDM is popular for managing rugged devices, IoT, and other non-traditional endpoints alongside standard mobile and desktop devices. 42Gears UEM is available as a cloud or on-premises, and it caters to businesses that require wide device coverage, including wearables, smart sensors, printers, and more.
The platform is often used in sectors like manufacturing, logistics, and retail, where frontline workers use specialized devices.
Key Features
- SureMDM provides kiosk mode capabilities to lock devices to specific apps or websites. Additionally, 42Gears offers companion products (SureLock, SureFox) for enhanced kiosk lockdown and a product called SureVideo for digital signage.
- IT admins can remotely view or control devices to diagnose issues. It also gathers device logs and allows remote execution of scripts/commands to troubleshoot issues.
- It also features Mobile Threat Defense integration to protect against malware and network attacks on mobile devices.
- Detailed dashboards for device status, data usage, location tracking, and more.
Limitations
- 42Gears shines in Android/rugged device control more than in desktop management.
- Multiple pricing add-ons can boost up overall subscriptions cost.
42Gears give you a 30-day free trial and SureMDM pricing plan starts at $3.99/month per device.
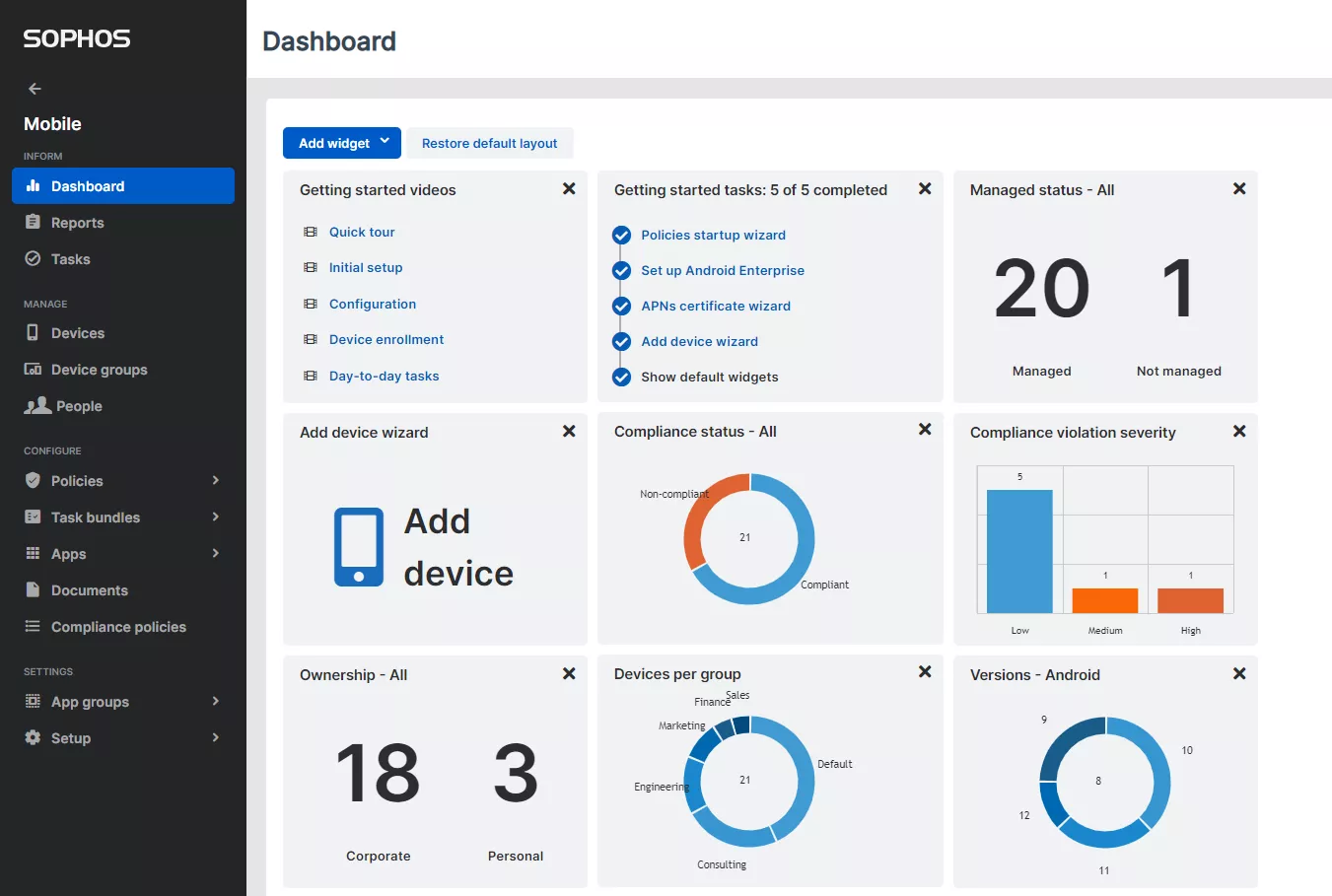
8. Sophos Mobile
Sophos Mobile is a secure UEM and Mobile Threat Defense solution from cybersecurity company Sophos. It stands out for its focus on security, integrating mobile device management with Sophos’s anti-malware, web protection, and content filtering.
Sophos Mobile is part of the Sophos Central platform and particularly attractive for organizations already using Sophos security platform or those who prioritize a security-centric approach to device management.
I like Sophos UEM pricing. It is per user-based, which can be cost-effective for BYOD-heavy environments. It simplifies cost calculations and license tracking for SMBs.
Key Features
- It integrates with Apple and Android management services for streamlined enrollment (DEP/ABM, Android Enterprise).
- Built-in Mobile Threat Defense via the Intercept X for Mobile app. This provides on-device malware scanning, malicious website blocking, phishing protection, and detection of risky apps or device compromises.
- Supports containerization approaches such as Android Work Profile and iOS User Enrollment to separate work data.
Limitations
- Sophos Mobile’s PC management is solid for security policies, but it is not a full PC lifecycle tool. It does not deploy software applications or patches to Windows/macOS in the way something like Microsoft Intune or ManageEngine would.
- Administrators not already familiar with Sophos Central may find UEM configuration non-intuitive. It gives you feeling toward security management rather than classic device management.
- Quote-based pricing, not transparent.
I would suggest Sophos UEM if you are prioritizing security than device management. You can request for a free trial to see how it works for you.
9. Workspace ONE UEM
Workspace ONE UEM (formally VMware UEM) is one of the industry-leading unified endpoint management platforms. It is trusted by many large enterprises for its extensive features, scalability, and integration capabilities.
It is scalable to tens or hundreds of thousands of devices. It allows the creation of smart groups and granular policies. Automation rules can dynamically adjust device policies or group membership based on device attributes.
Along with standard mobile and desktop, Omnissa UEM is capable of managing XR (eXtended Reality) devices. It is offered as both a cloud service and an on-premises product and excels in environments that require tight control and where integration with virtualization (VDI), identity management, or zero-trust security frameworks is a priority.
Key Features
- It covers onboarding with options like Apple DEP, Android zero-touch, etc., configuration management, software distribution, patch management, remote support, and retirement of devices.
- Having its roots in AirWatch, it offers best-in-class mobile device management for iOS, and Android OS. Features include telecom expense management, detailed mobile analytics, and a content container.
- Combined with VMware Workspace ONE Access and Carbon Black, the UEM can enforce conditional access. For example, blocking a device’s access to corporate resources if it is out of compliance or not managed.
Limitations
- Workspace ONE UEM is feature-packed, which makes it complex to learn and configure fully. Administrators often need formal training to use it effectively.
- Without planning, one can end up with messy configurations. The richness is a double-edged sword: it’s powerful, but easy to misconfigure if not careful.
The pricing is on the higher end. Licensing can be complicated with different editions and suitable for large enterprise only.
| Edition | Starting Price |
|---|---|
| Mobile Essentials | $3 per device, $5.40 per user |
| Desktop Essential | $4 per device, $7.20 per user |
| UEM Essential | $5.25 per device, $9.45 per user |
| Enterprise | $10 per device, $15 per user |
10. Ivanti Neurons for UEM
Ivanti Neurons for UEM is Ivanti’s cloud-based UEM, building on the company’s experience with LANDesk and MobileIron (both now part of Ivanti). The platform focuses on improving digital employee experience (DEX) that spans traditional device management and modern endpoint management in one solution.
Ivanti Neurons leverage AI automation to proactively maintain endpoints. It’s a strong choice for industries like healthcare, education, government, and finance, where a mix of device types and strong security is required.

Key Features
- Ivanti’s Neurons platform continuously discovers devices on the network and updates inventory data in real-time.
- A highlight is Ivanti’s use of automation “bots” to detect and remediate common device issues. For example, if a service stops or a configuration drifts from policy, Neurons can trigger a script or action to fix it without admin intervention.
- Ivanti Neurons is built to scale in large enterprises and supports integration with ITSM like ServiceNow and others. This triggers auto-generating tickets for non-compliant devices.
Limitations
- Initial setup and migration could be complex, requiring careful planning to unify mobile and desktop under Neurons.
- Ivanti Neurons admin interface has many modules and options. Staff training is often needed to fully utilize the platform and avoid confusion or misconfiguration.
Ivanti doesn’t publicize pricing, you need to get a quote tailored to your environment.
11. Matrix42 UEM
Matrix42 Unified Endpoint Management is a popular in Europe that combines client lifecycle management and enterprise mobility management. It provides a unified console for managing desktop and mobile devices.
Key Features
- Matrix42 covers OS deployment, software packaging and distribution, patch management, and configuration management for PCs and servers.
- The UEM console provides a single view of all endpoints with the ability to drill down into device details, deploy applications, or trigger remote actions. It also allows creation of dynamic groups to automate policy assignment.
- If used with Matrix42’s service management, end-users can have a portal to request software or device enrollment, which then the UEM can fulfill automatically.
- Matrix42 SUEM includes EgoSecure Data Protection, which provides endpoint security features like device control, encryption, and data loss prevention.
Limitations
- While Matrix42 covers essential UEM functions, large enterprises with complex needs might find gaps compared to solutions like Citrix UEM or Workspace One.
- Quoted-based pricing, often not transparent.
- Priority 24×7 support is an add-on.
You can free trial for 30-days to explore the features.
12. IBM MaaS360
IBM MaaS360 is an enterprise UEM solution delivered via the IBM Cloud. MaaS360 has been a long-time player in the MDM/UEM space and is recognized for its reliability and strong security features.
It is especially common in large enterprises and regulated industries. MaaS360 offers full unified endpoint management capabilities and differentiates with features like built-in Mobile Threat Management and IBM Watson AI insights for IT.
A standout feature is MaaS360 Advisor which uses IBM Watson AI to analyze your environment and provide risk insights or recommendations. For example, it might highlight anomaly patterns like devices that frequently go out of compliance or suggest policy tweaks for better security.
Another one is, it provides a suite of secure apps like browser, documents, chat that create a secure container on BYOD devices to keep corporate data isolated.
I would suggest IBM MaaS360 to mid-sized and large enterprise. You can start with the Essentials plan and upgrade as you grow and need.
| IBM MaaS360 Plan | Pricing |
|---|---|
| Essentials | $4 per device/month |
| Deluxe | $5 per device/month |
| Premier | $6.25 per device/month |
| Enterprise | $9 per device/month |
You can save 30% when you go for annual plan. They also offer a 30-day free trial.
Beyond Top Picks of UEM Software
I would also suggest checking out the following noteworthy UEM solutions.
| Cisco Meraki System Manager | Focused on security and suitable for enterprise using Cisco products. |
| HCL BigFix | Good for those looking for customized solutions. |
| Datto | Focused on backup and DR for MSP |
| Atera | Integrated ticketing system and RMM |
| Microsoft Intune | Suitable for enterprise heavily relying on the Microsoft ecosystem |
| Google Endpoint Management | Suitable for Google Workspace users |
Conclusion
Choosing the best UEM software for your organization requires balancing the scope of features, security, ease of use, and budget. All the solutions reviewed above are highly rated.
When evaluating UEM options, consider your device types and operating systems, your required integrations with IT service systems. Pilot testing a couple of top contenders in your environment is a best practice to gauge real-world performance and usability.
What is UEM software?
Unified Endpoint Management (UEM) software is a platform that allows organizations to manage and secure all types of endpoints from a single console.
With UEM software, administrators can remotely enroll devices, configure settings, push software or mobile apps, apply security policies, and monitor compliance for virtually any endpoint in the organization.
In essence, UEM software provides a unified, centralized approach to endpoint management. This simplifies administration because IT doesn’t have to switch between multiple systems. UEM solutions also help enforce consistent security across device types; for example, ensuring all devices have encryption enabled and adhere to company password policies can be done from one system.
UEM vs. MDM: What’s the difference?
Mobile Device Management (MDM) and Unified Endpoint Management (UEM) are related concepts, but there are important differences in scope:
- MDM refers to managing mobile devices specifically. MDM is a subset of endpoint management, limited to mobile devices and tablets.
- UEM is a broader evolution that encompasses MDM but also includes managing additional endpoint types such as PCs, laptops, and others. This means a UEM can do what an MDM does and also deploy software to desktops. UEM solutions typically integrate traditional PC management with modern MDM into one platform.
- UEM supports mobile and desktop operating systems like Windows, macOS, Linux, whereas basic MDM is primarily mobile OS like Android/iOS.
- UEM often includes advanced features like software distribution for PCs, endpoint security integration, and unified policy for all devices. MDM is centered on configurations and apps for mobile.
In summary, MDM = managing mobile devices and UEM = unified management of all endpoints (mobile, desktops, and beyond).
How to choose the right UEM software?
Choosing the right UEM solution requires evaluating both your technical requirements and business needs. Here are key factors and steps to consider:
- Start by listing all device types in your organization. How many Windows PCs? Macs? Android/iOS devices? Any Linux machines or IoT devices? The UEM software you choose must support all the platforms you use.
- Outline your critical management and security tasks. Common features to look for include:
- Can it automate onboarding of new devices?
- Does it cover passcode rules, Wi-Fi, VPN, email setups, certificate distribution, encryption enforcement, etc., across all OS?
- Can it deploy software applications and app updates remotely?
- For desktops, can it handle OS and application patching?
- Look for things like remote wipe, remote lock, jailbreak/root detection, antivirus integration, compliance checks, conditional access integration with IAM solutions.
- Consider the UI and admin experience.
- Decide if you prefer a cloud-based service or an on-premises solution.
- If you have or anticipate many devices, look at case studies or references to ensure the UEM can handle your scale.
- Evaluate how the UEM will integrate with your existing systems like directory services, ITSM, etc.
- Get quotes for your environment from multiple vendors. Factor in not just license costs but also implementation services if needed, and training.
- Finally, perform a pilot with your top 1–3 choices. Have IT admins and maybe even a subset of end-users provide feedback.
By carefully considering these factors, you’ll be able to select a UEM solution that fits your organization’s needs.













