Threat intelligence platforms provide contextualized, real-time threat data and analysis, enabling organizations to proactively identify and mitigate risks. Threat intelligence platforms help businesses understand the threat landscape and the tactics used by attackers so that businesses strengthen their defenses and prevent costly security breaches.
Threat intelligence platforms help in the identification of security risks, benefiting businesses by early detection and anticipation of cyber threats. Through this, businesses are better prepared for attacks, reducing the likelihood of data breaches that lead to potential financial loss. The operational expenses, too, are reduced through automation clubbed with real-time monitoring.
Geekflare has created this list of the best threat intelligence platforms, considering features like vulnerability threat evaluation, real-time incident detection, event log analyzer, etc.
- 1. NordStellar
- 2. Tenable Security Center
- 3. AutoFocus
- 4. Criminal IP
- 5. ManageEngine Log360
- 6. AlienVault USM
- 7. Qualys Threat Protection
- 8. SOCRadar
- 9. Solarwinds Security Event Manager
- Show less
1. NordStellar
NordStellar cyber threat intelligence helps you spot potential threats to your business. This allows your security team to detect risks sooner and respond quickly if those risks materialize.
Additionally, it provides your security officers with insights into how to reduce risk exposure and improve security posture.
The best thing about NordStellar cyberthreat intelligence is that you can integrate it into your existing Security Operations Center (SOC) tools to enhance your threat intelligence capabilities.
It can also support you in meeting compliance, such as DORA, SOC 2, and ISO 27001.
To provide you with reliable threat intelligence, NordStellar collects data from a vast, continuously updated network of sources scattered in the open, deep, and dark web.
Its sources include, but are not limited to, marketplaces, forums, and hidden channels that threat actors use.
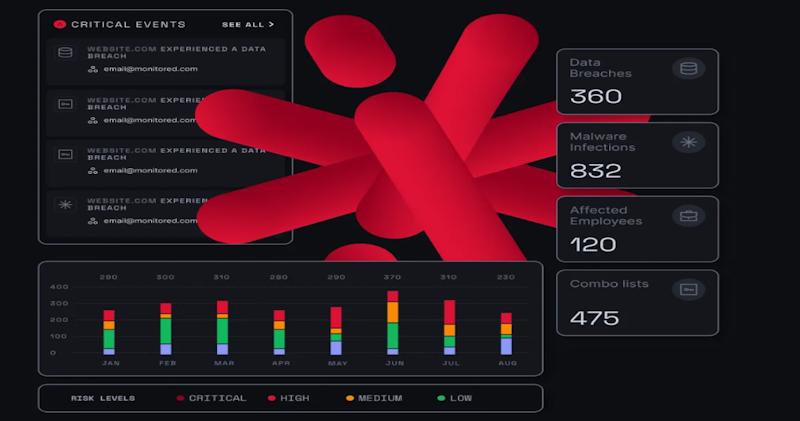
NordStellar Features
- Detects brand mentions, vendor risks, and leaked information about key people in your company on the dark web.
- Offers real-time data breach monitoring with full context of past and present attacks.
- Monitors your external attack surface, including internet-facing assets, IP addresses with open ports, and cloud services, to mitigate potential cyber risks.
- Discovers threat actors impersonating your brand so that you can take proactive actions.
It offers a free cybersecurity risk report, which includes your personalized Cyber Risk Score, key insights into web and network security, an overview of exposed data linked to your domain, and more.
NordStellar pricing starts at $3000/year for 5 users, one domain, and 200 monitored assets.
2. Tenable Security Center
Tenable Security Center (powered by Nessus Technology), is a vulnerability management platform that provides insight into your organization’s security posture and IT infrastructure. It collects and evaluates vulnerability data across your IT environment, analyzes vulnerability trends over time, and allows you to prioritize and take corrective action.

Tenable.sc product family (Tenanble.sc and Tenable.sc+) enables you to identify, investigate, prioritize, and remediate vulnerabilities so that you can protect your systems and data.
Tenable Security Center Product Features
- Streamlines compliance with industry standards, such as CERT, NIST, DISA STIG, DHS CDM, FISMA, PCI DSS, and HIPAA/HITECH.
- Provides a passive asset discovery features allow you to discover and identify IT assets on your network, such as servers, desktops, laptops, network devices, web apps, virtual machines, mobile, and cloud.
- Gives frequent updates through its Tenable Research team about the latest vulnerability checks, zero-day research, and configuration benchmarks to help you protect your organization.
- Maintains a library of over 67k Common Vulnerabilities and Exposures (CVEs).
- Has real-time detection of botnets and command and control traffic.
- Includes a single pane of glass to help you view and manage your network across all Tenable.sc consoles.
Tenable.sc is licensed per year, and per asset, its 1-year license starts at $5,364.25. You can save money by purchasing a multi-year license.
3. AutoFocus
AutoFocus from Palo Alto Networks is a cloud-based threat intelligence platform that allows you to identify critical attacks, conduct preliminary assessments, and take steps to remediate the situation without needing additional IT resources. The service gathers threat data from your company network, industry, and global intelligence feeds.
AutoFocus provides intel from Unit 42 –Palo Alto Network threat research team– about the latest malware campaigns. The threat report is viewable on your dashboard, giving you additional visibility into bad actors’ techniques, tactics, and procedures (TTP).
AutoFocus Product Features
- Provides visibility into the latest malware through its unit 42 research feed with information about their tactics, techniques, and procedures.
- Processes 46 million real-world DNS queries daily.
- Gathers intel from third-party sources like Cisco, Fortinet, and CheckPoint.
- Provides threat intelligence to security information and event management (SIEM)tools, in-house systems, and other third-party tools with an open and agile RESTful API.
- Includes pre-built tag groups for ransomware, banking trojan, and hacking tool.
- Allows creation of custom tags based on their search criteria.
- Is compatible with various standard data formats such as STIX, JSON, TXT, and CSV.
Pricing for AutoFocus is not advertised on the Palo Alto Network website. Buyers should contact the company sales team for quotes, and you can also request a product demo to learn more about the solution capabilities and how you can leverage it for your enterprise.
4. Criminal IP
Criminal IP is a CTI search engine that provides comprehensive threat information on all cyber assets. Using AI machine learning technology, it monitors open ports of IP addresses worldwide through a 24/7 scanning process and provides reports with a 5-level risk score.
In addition to being a powerful search engine, Criminal IP offers various applications such as Attack Surface Management, penetration testing, and vulnerability and malware analysis.
Criminal IP Product Features
- Analysis of vulnerabilities and provision of CVE information.
- Real-time collection and analysis of IP address data worldwide.
- Integration with various existing workflows and products.
Criminal IP’s free version provides basic online customer support with a response time of within 48 business hours.
5. ManageEngine Log360
ManageEngine Log360 is a log management and SIEM tool that provides companies with visibility into their network security, audits active directory changes, monitors their exchange servers and public cloud setup, and automates log management.
ManageEngine Log360 combines the capabilities of five ManageEngine tools, including ADAudit Plus, Event Log Analyzer, M365 Manager Plus, Exchange Reporter Plus, and Cloud Security Plus.

ManageEngine Log360 threat intelligence modules include a database that contains global malicious IPs and a STIX/TAXII threat feed processor that frequently retrieves data from global threat feeds and updates you.
ManageEngine Key Features
- Includes integrated cloud access security broker (CASB) capabilities to help monitor data in the cloud, detect shadow IT applications, and track sanctioned and unsanctioned applications.
- Detects threats across enterprise networks, endpoints, firewalls, web servers, databases, switches, routers, and other cloud sources.
- Has real-time incident detection and file integrity monitoring.
- Uses MITRE ATT&CK framework to prioritize threats that occur in the attack chain.
- Provides attack detection includes rule-based real-time correlation, behavior-based ML-based user and entity behavior analytics (UEBA), and signature-based MITRE ATT&CK.
- Includes integrated data loss prevention (DLP) for eDiscovery, data risks assessment, content-aware protection, and file integrity monitoring.
- Comes with real-time security analytics with integrated compliance management.
ManageEngine Log360 can be downloaded in one file and comes in two editions: free and professional. Users can experience the advanced features of the professional edition for a 30-day trial period, after which these features will be converted to their free edition.
6. AlienVault USM
AlienVault USM platform developed by AT&T. The solution provides threat detection, assessment, incident responses, and compliance management in one unified platform.

AlienVault USM receives updates from AlienVault Labs every 30 minutes about different types of attacks, emerging threats, suspicious behavior, vulnerabilities, and exploits they discover across the entire threat landscape.
AlienVault USM provides a unified view of your enterprise security architecture, enabling you to monitor your networks and devices on-premise or in remote locations. It also includes SIEM capabilities, cloud intrusion detection for AWS, Azure, and GCP, network intrusion detection (NIDS), host intrusion detection (HIDS), and endpoint detection and response (EDR).
AlienVault USM Product Features
- Provides real-time Botnet detection with command and control (C&C) traffic identification
- Has advanced persistent threat (APT) detection.
- Complies with various industry standards such as GDPR, PCI DSS, HIPAA, SOC 2, and ISO 27001.
- Has network and host IDS signatures.
- Allows data exfiltration detection with Centralized event and log data collection.
- AlientVault monitors cloud and on-premise environments from a single pane of glass, including AWS, Microsoft Azure, Microsoft Hyper-V, and VMWare.
Pricing for this solution starts at $1,075 per month for the essential plan. Potential buyers can sign up for a 14-day free trial to learn more about the tool’s capabilities.
7. Qualys Threat Protection
Qualys Threat Protection is a cloud service that provides advanced threat protection and response capabilities. It includes real-time threat indicators of vulnerabilities, maps findings from Qualys and external sources, and continuously correlates external threat information against your vulnerabilities and IT asset inventory.
With Qualys threat protection, you can manually create a custom dashboard from widgets and search queries and sort, filter, and refine search results.
Qualys Threat Protection Product Features
- Centralized control and visualization panel
- Provides live feed of vulnerability disclosures
- RTIs for zero-day attacks, public exploits, actively attacked, high lateral movement, high data loss, denial of service, malware, no patch, exploit kit, and easy exploit
- Includes a search engine that allows you to look for specific assets and vulnerabilities by creating ad hoc queries
- Qualys threat protection continuously correlates external threat information against your vulnerabilities and IT asset inventory
They offer a 30-day free trial to allow buyers to explore the tool’s capabilities before making a purchase decision.
8. SOCRadar
SOCRadar describes itself as a SaaS base Extended Threat Intelligence (XTI) platform that combines external attack surface management (EASM), digital risk protection services (DRPS), and cyber threat intelligence (CTI).
The platform improves your company’s security posture by providing visibility into its infrastructure, network, and data assets. SOCRadar’s capabilities include real-time threat intelligence, automated deep and dark web scans, and integrated incident response.
SOCRadar Product Features
- Integrates with existing security stacks such as SOAR, EDR, MDR and XDR, and SIEM solutions.
- Has over 150 feed sources with industry and region-based monitoring.
- Provides intel on various security risks, such as malware, botnet, ransomware, phishing, bad reputation, hacked website, distributed denial-of-service attacks (DDOS), honeypots, and attackers
- Provides over 6,000 combo list access (credential and credit card) with MITRE ATT & CK mapping.
- Comes with deep and dark web monitoring along with compromised credentials detection.
SOCRadar has two editions: cyber threat intelligence for SOC teams (CTI4SOC) and extended threat intelligence (XTI). Both plans are available in two versions –free and paid.
9. Solarwinds Security Event Manager
SolarWinds Security Event Manager is a SIEM platform that collects, normalizes, and correlates event log data from over 100 pre-built connectors, including network devices and applications.
With SolarWinds Security Event Manager, users effectively administer, manage, and monitor security policies and protect your network. It analyzes the collected logs in real-time and uses the information gathered to notify you of an issue before it causes severe damage to your enterprise infrastructures.
SolarWinds Security Event Manager Features
- Monitors your infrastructure 24/7.
- Has 100 pre-built connectors, including Atlassian JIRA, Cisco, Microsoft, IBM, Juniper Sophos, Linux, and more.
- Automates compliance risk management.
- Includes file integrity monitoring.
- Gathers logs, correlates events, and monitors threat data lists.
- Has over 700 built-in correlation rules.
- Users can export reports in PDF or CSV formats.
Solarwinds Security Event Manager offers a 30-day free trial with two licensing options. The tool is licensed based on the number of nodes sending log and event information.
What is Threat Intelligence Platform?
A Threat intelligence platform (TIP) is a technology that enables organizations to collect, analyze, and aggregate threat intelligence data from multiple sources. This information allows companies to proactively identify and mitigate potential security risks and defend against future attacks.
Cyber threat intelligence is an important enterprise security component. By monitoring the latest cyber threats and vulnerabilities, your organization can detect and respond to potential security breaches before they damage your IT assets.
How does Threat Intelligence Platform Work?
Threat intelligence platforms help companies mitigate the risks of data breaches by collecting threat intelligence data from multiple sources, including open-source intelligence (OSINT), deep and dark web, and proprietary threat intelligence feeds.
TIPs analyze the data, identify patterns, trends, and potential threats, then share this information with your SOC team and other security systems, such as firewalls, intrusion detection systems, and security information and event management (SIEM) systems, to mitigate damage to your IT infrastructure.
Benefits of Threat Intelligence Platforms
Threat intelligence platforms provide organizations with 4 main benefits, as listed below.
- Proactive threat detection
- Improved security posture
- Better resource allocation
- Streamlined security operations
Other advantages of TIPs include automated threat response, cost savings, and increased visibility.

