Social engineering in cybersecurity covers a range of psychological tactics that cybercriminals use to manipulate people into taking certain actions they wouldn’t otherwise take. For instance, an attacker might use targeted psychological tricks to persuade a victim to share confidential information.
Threat actors require time, skills, and advanced tools to breach your secured corporate devices. However, tricking your unsuspecting employees into sharing login credentials is much easier. So, it is crucial to prevent social engineering attacks.
This article will explore social engineering, its various types, and how to prevent social engineering attacks.
Social engineering is the art of manipulating people to extract confidential information or trick them into taking certain actions they wouldn’t otherwise take.
In social engineering attacks, cybercriminals exploit human trust, emotion, and social behaviour to fulfil their malicious objectives.
For example, a cybercriminal can call an unsuspecting employee and say, ” Hi, this is Tom from IT. We’re doing urgent maintenance, and your account needs to be reset. Can you please share your password so I can make the updates?” If the employee shares the password, the hacker may have access to the company’s systems.
Social Engineering Attack Process
Cybercriminals use a structured process to carry out social engineering attacks. They often collect information about potential targets before communicating with them.
Here are the key steps involved in a typical social engineer attack:
- Research: An Attacker gathers information about their target by studying social media profiles, organizational hierarchies, and other publicly available information. They look for weaknesses or potential points of entry.
- Building Rapport: The attacker approaches the target, often pretending to be a trusted figure like a coworker or a tech support representative from a renowned company. They aim to build trust through friendly interactions or by exploiting familiarity.
- Exploitation and Manipulation: After gaining trust, the attacker makes specific requests. These could include login credentials, sensitive data, or access to restricted areas, usually by pretending it’s for a legitimate purpose.
- Execution: The attacker uses the obtained information to access systems or steal data. This step might involve installing malware, exfiltrating data, or using stolen credentials to gain further access.
- Disengagement: To avoid detection, the attacker removes traces of their presence, such as deleting messages or retracting suspicious communications.
Now, you know—what is social engineering in the cybersecurity context? Let’s explore the types of social engineering next.
In social engineering attacks, threat actors exploit human fear, trust, curiosity, and urgency to achieve their malicious objectives.
Here are key types of social engineering attacks, categorized by their techniques.
1. Phishing
Phishing is the most common type of social engineering attack. In phishing attacks, bad actors masquerade as trusted individuals or organizations to lure targets into sharing confidential data or installing malware on their devices. These actors most often rely on email to run phishing campaigns.
Here is an example of a phishing email.
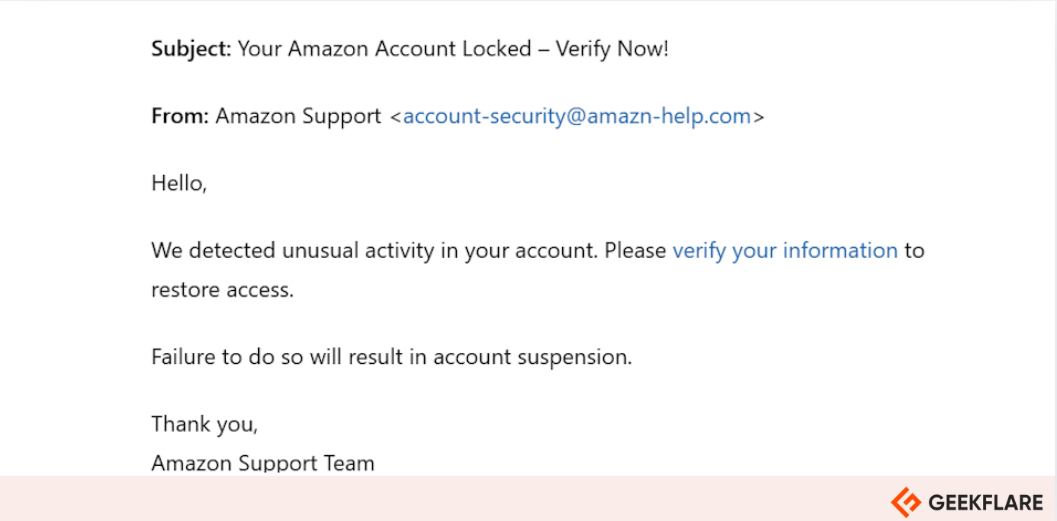
Clicking “verify your information” can lead the victim to a fake Amazon page designed to steal login credentials or install malware on their device.
Phishing attacks can come in various forms, such as vishing, smishing, and whaling. Let’s explore various types of phishing attacks below:
- Smishing: Smishing is a phishing attack in which cybercriminals leverage text messages to lure victims into downloading malware or disclosing sensitive information.
- Vishing: In a vishing attack, a scammer impersonates a trusted authority over the phone to manipulate the victim into following specific instructions provided by them.
- Spear Phishing: Spear phishing campaigns target specific individuals or organizations with messages tailored specifically to them, which increases the chances of success.
- Whaling: Whaling is a type of spear phishing attack in which attackers target high-level executives with personalized phishing campaigns. The goal is often to trick victims into authorizing a money transfer or sharing trade secrets.
- Clone Phishing: In clone phishing attacks, attackers clone real emails with attachments and resend them, impersonating the original senders. But they replace the original attachments with malicious ones to fulfil their nefarious objectives.
- Evil Twin Phishing: In Evil Twin attacks, bad actors create fake Wi-Fi networks that mimic legitimate brand hotspots. When users connect to these fake Wi-Fi networks, the bad actors can intercept and monitor their online activities.
- Angler Phishing: Angler phishing attacks target social media users. In these attacks, cybercriminals impersonate customer support agents of reputable brands to deceive dissatisfied customers into sharing sensitive information or installing malware on their devices.
2. Pretexting
In pretexting attacks, attackers fabricate stories to earn victims’ trust and trick them into sharing confidential information, sending money to the attackers, and downloading malware.
Cybercriminals tell their stories using legitimate-looking images, wording, and tones to increase the success of pretexting attacks. Pretexting attacks can occur online, in person, or on the phone.
3. Baiting
Baiting is a social engineering trick attackers use to lure people into revealing sensitive information or compromising their devices’ security by offering something enticing.
For example, an attacker might leave a USB flash drive labelled “Confidential” in a public place. Curious individuals who find it might plug it into their computers to see what’s on it, unknowingly installing malware.
4. Tailgating/Piggybacking
In a tailgating attack, a cybercriminal gains entry to a restricted area by closely following someone with legitimate access. This often occurs in places like office buildings or secure facilities.
The cybercriminal uses social engineering techniques—such as appearing rushed or carrying items—to prompt authorized personnel to hold doors open for them. To blend in, they may impersonate delivery or maintenance workers.
5. Quid Pro Quo
A Quid Pro Quo is a social engineering attack in which the attacker can offer a service in exchange for sensitive information or access to otherwise restricted resources.
For example, an attacker may promise a target some reward for fulfilling a survey that requires personal details to be submitted. Later, the attacker can use the personal details to carry out future malicious campaigns like phishing attacks.
6. Business Email Compromise
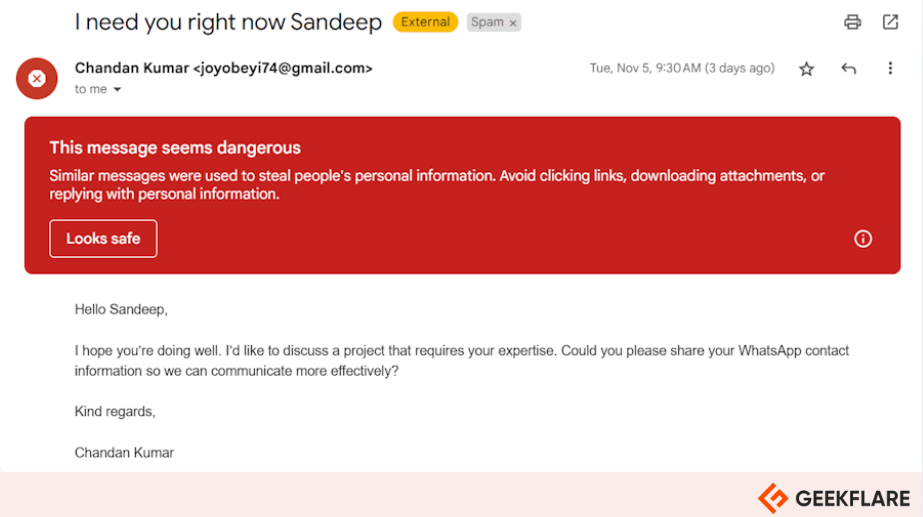
In a business email compromise attack, an attacker impersonates a trusted individual or organization through email to deceive targets into transferring money, divulging sensitive information, or performing unauthorized actions.
The attacker typically gains access to or spoofs a legitimate business email account. Then, they use social engineering tactics to trick employees, partners, or customers into making wire transfers, changing vendor payment information, and granting access to sensitive data.
7. Honey Trap
In a honeytrap social engineering attack, an attacker uses romantic or sexual persuasion to manipulate a target into sharing confidential information or granting access to secure systems.
8. Reverse Social Engineering
Reverse social engineering in cybersecurity is a tactic in which hackers do not initiate contact with their victims directly. Instead, they create a problem or situation that leads the victim to believe an issue needs resolution.
The victim then contacts the attacker, posing as a support executive or help desk representative. Following the attacker’s suggested steps, the victim unknowingly shares sensitive data or downloads malware.
Scareware, which creates a fake security warning, is an example of a reverse social engineering attack.
9. Watering Hole Attack
A watering hole attack is a social engineering tactic in which attackers compromise a trusted website frequently visited by members of a specific group they aim to infect. The objective of the attack is to infect the members’ devices and gain access to the corporate network they belong to.
For example, a cybercriminal wants to target a company’s finance team. Knowing they often visit a specific industry blog, the attacker infects this website with malware. When finance team members access the blog, their devices get compromised, allowing the attacker to infiltrate the company’s network and steal sensitive financial data.
Social engineering attacks can result in the loss of sensitive data, financial losses, and damage to your reputation. Let’s explore the following real-world examples below.
Google and Facebook Spear Phishing Campaign
Evaldas Rimasauskas set up a fake company pretending to be Taiwan-based Quanta Computer, which worked with Facebook and Google. He and his team then sent fraudulent invoices, successfully swindling $100 million from these tech giants.
UK Energy Company Deepfake Attack
A CEO of a UK-based energy firm fell prey to deepfake and transferred €220,000 to a fraudster, thinking he was transferring money to his boss. The fraudster used AI-based voice cloning technology to spoof his boss’s voice.
CEO Fraud Against FACC
Austrian aerospace parts company FACC lost €42 million in a cyber-fraud scheme. A scammer impersonated its CEO, Walter Stephan, and convinced an employee to transfer the money for a fake acquisition project.
Belgian Bank Whaling Attack
A Belgian bank lost over €70 million in a whaling attack. A scammer supposedly impersonated a high-level bank official, convincing an employee to transfer the funds based on a fake request they raised.
Identifying a social engineering attack is not rocket science. All social engineering attacks have telltale signs if you look for them closely.
We have listed common signs of social engineering attacks below:
- Unsolicited Requests: Any unsolicited request asking for personal information, urgent actions, or access to your systems or resources is a red flag. These unsolicited requests can come via emails, phones, and social media messages.
- Urgent or Threatening Language: To make social engineering attacks work, bad actors employ urgency and threatening language to pressure victims into acting quickly without careful consideration. Any communication starting with “immediate actions required” is a telltale sign of a social engineering attack.
- Too Good to Be True Offers: If you have received an unsolicited offer that seems too good to be true, there is a high chance that it is not true. So, if you receive an email claiming that you have won a lottery you don’t remember entering, be cautious. It is a social engineering attack.
- Suspicious Links and Attachments: Emails with suspicious links and attachments indicate social engineering attacks. You can hover over links in your emails to find where those links lead.
- Generic Greetings and Poor Grammar: Messages with generic greetings like “Dear Customer” or “Dear Valued User” and poor grammatical errors are clear indications of social engineering. Legitimate companies personalize their messages and avoid making silly grammatical errors. However, bad actors are increasingly leveraging GenAI to craft sophisticated phishing messages that don’t have grammatical mistakes.
- Mismatched Email Addresses: Cybercriminals use email addresses that look legitimate but contain slight variations to trick individuals. They can use misspelled domain names or different domain names. For example, a social engineering email can come from [email protected], while your bank’s correct address is [email protected].
- Requests for Secrecy: If a message requests that you maintain secrecy or confidentiality, double-check it before responding to it.
- Request for Verification: Attackers often ask victims to verify personal information or account details to ensure security. For example, they can ask you to verify your password, claiming your account has been breached. If you receive any unsolicited request for any kind of verification, it is a red flag.
- Bogus Contact Information: All social engineering attacks include bogus contact information. For example, it can have a personal email address, while the email claims to be from a reputed organization.
Recognizing the signs of social engineering outlined above can significantly reduce your risk of falling victim to various attack techniques.
Social engineering attacks exploit human nature, so the best defence against them is to educate your employees and amp up your defence to minimize the impacts of human error in your organization.
Here are some quick social engineering prevention techniques.
Educate Employees
Social engineering attacks exploit human psychology rather than vulnerabilities in your systems and networks. So, training your employees on various types of social engineering attacks can help them become more vigilant.
You should also run simulated attacks to assess their preparedness to fight social engineering campaigns.
Verify Requests
Another way to prevent social engineering attacks is to verify requests for sensitive data before responding. Encourage your employees to always confirm through a separate communication channel if there is a request for sensitive data.
For example, if an employee receives an email from someone claiming to be the CEO asking for payroll records, they shouldn’t respond immediately. Instead, they should verify by calling the CEO directly or sending a message on an internal platform.
This simple step helps confirm the request is legitimate and keeps sensitive data secure.
Use Multi-Factor Authentication (MFA)
Enforcing multi-factor authentication in your organization adds an extra layer of security to accounts. If hackers can trick your employees into sharing passwords, they cannot gain access to your accounts without other verification factors.
Limit Information Sharing
Cybercriminals leverage publicly available information to build their narratives and manipulate individuals. The more information they have about their targets, the more sophisticated their attacks will be. So, you should encourage your staff to limit sharing personal information online.
Establish Strong Security Policies
Security policies establish clear protocols for verifying identities and handling sensitive information, mandating employee training and strict access controls. As a result, employees are less likely to fall prey to social engineering attacks.
Moreover, these policies also include steps for responding to social engineering attacks and other cyberattacks, minimizing the potential damage caused by such incidents.
Encourage Reporting
Encouraging your employees to report any suspicious activity or social engineering attack helps build a proactive security culture and contributes to a collective defence mechanism. Insights gathered through reporting can help your security team implement the right types of security controls to block social engineering attacks.
Use Anti-Phishing Tools
Phishing is the most common type of social engineering attack. An anti-phishing tool can detect phishing emails and malicious websites in real time and monitor social media platforms for phishing attempts.
Implementing one of the best anti-phishing tools in your organization can significantly reduce the risk of these attacks.
Enforce Physical Security
Strong physical security can help prevent unauthorized personnel from entering your premises. By controlling who enters your premises, you can easily thwart tailgating attacks. Therefore, start using access control, surveillance, alarm systems, and other physical security measures to strengthen physical security.
Conclusion
Social engineering poses a significant cybersecurity threat because it exploits human behaviour. With AI advancements, cybercriminals can now craft even more convincing phishing campaigns.
Your defence against social engineering attacks is only as strong as your employees’ vigilance. To prevent such attacks, invest in proactive measures like training employees training, implementing an anti-phishing tool, enforcing multi-factor authentication, and promoting the verification of any requests for sensitive information.
Explore More on Cyberattacks
-
 EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.
EditorNarendra Mohan Mittal is a senior editor & writer at Geekflare. He is an experienced content manager with extensive experience in digital branding strategies.


