Endpoint Detection and Response (EDR) tools continuously monitor end-user devices to detect and respond to cybersecurity threats like malware. With 68% of organizations facing one or more endpoint attacks, deploying a reliable EDR solution is critical to protecting endpoints in your organization.
I’ve tested, analyzed, and researched 20 popular solutions, evaluating their features and capabilities. From these, I’ve selected the 13 best EDR tools. I also reviewed product documentation and verified EDR vendor claims using multiple data sources, including third-party customer review websites like G2, Capterra, and TrustRadius.
Below, I’ll discuss 10 out of the 13 EDR tools that are shortlisted. 👇🏼
- 1. Heimdal EDR – Best for Patch Management
- 2. Kaspersky Next EDR Expert – Best for Ransomware Protection
- 3. Bitdefender GravityZone EDR – Best for Correlation of Attacks Across Endpoints
- 4. SentinelOne Singularity Endpoint – Best for AI-powered Defense
- 5. Sophos Endpoint – Best for Ransomware Protection
- 6. CrowdStrike Falcon – Best for World-class Threat Intelligence
- 7. Broadcom Carbon Black EDR – Best for SOC Teams
- 8. Cynet EDR – Best for Continuous Risk Scanning
- 9. WatchGuard EDR – Best for Zero-Trust Application Service
- 10. Trellix EDR – Best for Simplifying EDR with AI
- Show less
You can trust Geekflare
At Geekflare, trust and transparency are paramount. Our team of experts, with over 185 years of combined experience in business and technology, tests and reviews software, ensuring our ratings and awards are unbiased and reliable. Learn how we test.
Best EDR Tools Comparison
I’ve compared the top 10 EDR tools based on key features, pricing, and the availability of a free trial. Check it out below!
Heimdal EDR | Kaspersky Next EDR Expert | Bitdefender GravityZone EDR | SentinelOne Singularity Endpoint | Sophos Endpoint | CrowdStrike Falcon | Broadcom Carbon Black EDR | Cynet EDR | WatchGuard EDR | Trellix EDR | |
Patch management, ransomware encryption protection, privileged access management | Ransomware protection, automated threat intelligence, MITRE ATT&CK mapping | Cross-endpoint attack correlation, HyperDetect tunable AI, cloud sandboxing | AI-powered detection, real-time response, behavioral analysis | CryptoGuard ransomware protection, behavioral analysis, anti-exploitation | AI-powered threat detection, threat hunting, memory scanning | Real-time threat hunting, attack chain visualization, automated watchlists | Continuous risk scanning, forensic investigation, network and file event visibility | Zero-trust application service,threat hunting, behavioral analysis | AI-guided threat investigation, integrated forensics, MITRE ATT&CK coverage | |
On-request | On-request | $220.49/year for 10 devices | On-request | On-request | $184.99/device/year | On-request | $7/endpoint/month | On-request | On-request | |
Now that you have a brief overview of these platforms, let’s discuss the top EDR tools individually in detail!
1. Heimdal EDR
Best for Patch Management
Heimdal EDR software includes advanced security tools to protect your endpoints and network from cyber threats. It combines Next-Gen Antivirus to detect hidden threats, Privileged Access Management to control who can access sensitive data, and Application Control to block risky apps.
It also features Ransomware Encryption Protection to stop hackers from locking files, Patch & Asset Management to keep software updated, and DNS Security to block harmful websites.
I like the fact that these 6 tools work together from a single agent and unified platform to strengthen your defenses. Its award-winning Patch & Asset Management allows you to deploy patches from anywhere in the world.
Heimdal EDR protects your business from many threats, such as phishing and social engineering, DNS and DoH vulnerabilities, brute-force attacks, advanced persistent threats (APTs), software exploits, and more.
Heimdal EDR Features
- Comprehensive visibility into your endpoint activities.
- Machine learning and AI-driven intelligence to offer proactive protection for your endpoints.
- Proactive Indicators of Compromise (IOCs) and improved Indicators of Attack (IOAs) to offer powerful EDR capabilities.
- The lightweight agent doesn’t affect your systems’ performance.
Heimdal EDR Pricing
Heimdal EDR pricing is based on the number of endpoints. You need to connect with the company to get the pricing details.
2. Kaspersky Next EDR Expert
Best for Ransomware Protection
Kaspersky Next EDR provides deeper visibility into all your corporate network endpoints. Based on Kaspersky’s award-winning Endpoint Protection Platform (EPP), it can automatically block mass attacks and automate EDR tasks. Consequently, your analyst will have more time to detect, prioritize, and prevent advanced threats and APT-like attacks.
I like its ability to contain threats quickly and mitigate security incidents across distributed infrastructures. During my research, I noted that its engines thwarted around 7 billion ransomware attacks over the past decade! This proves that it offers reliable ransomware protection.
Kaspersky Next EDR Expert uses a single agent for easy management through a cloud platform or offline console in air-gapped environments. It leverages threat intelligence and allows customizable threat detection.
The platform leverages threat intelligence to stay updated on new and evolving cyber threats, which helps detect attacks before they cause harm. It also allows businesses to customize threat detection based on their specific security needs.
Kaspersky Next EDR Expert Features
- Detects threats using Indicators of Compromise (IoC) and Indicators of Attack (IoA) with MITRE ATT&CK mapping.
- Uses automated threat intelligence and integrates with Kaspersky Private Security Network for real-time updates.
- Supports custom YARA rules and sandbox analysis to detect and analyze suspicious files.
- Utilizes cloud-based machine learning for APK analysis, verifies digital certificates, and integrates with external threat intelligence sources.
Kaspersky Next EDR Expert Pricing
Kaspersky Next EDR pricing is available on request. A free demo is available to explore its features. You can also try it for 30 days.
3. Bitdefender GravityZone EDR
Best for Correlation of Attacks Across Endpoints
Bitdefender GravityZone EDR provides cross-endpoint correlation to efficiently prevent ransomware and data breach attacks. I installed it on my laptop and tested it for a few days.
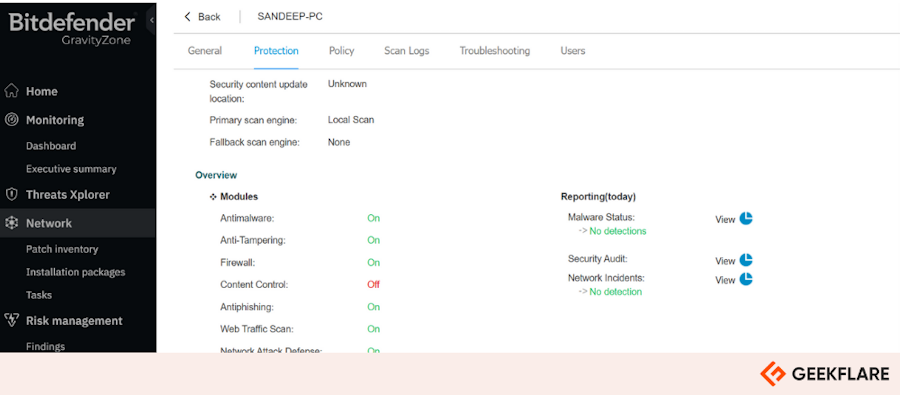
I liked its actionable insights and response remediation suggestions, which are very simple to comprehend. This ensures that a security analyst of any experience level can make informed decisions based on these recommendations.
GravityZone’s Risk Management strengthens security by identifying, scoring, and reducing risks from software vulnerabilities, misconfigurations, and risky user behavior. It helps minimize the attack surface by providing actionable insights and automated mitigation.
GravityZone EDR combines advanced security technologies to prevent and detect threats effectively. It includes Patch Management to fix vulnerabilities, Exploit Defense to block attacks, and Fileless Attack Defense to stop malware that runs in memory.
What’s more, its HyperDetect Tunable AI enhances threat detection, while Cloud Sandboxing analyzes suspicious files in a secure environment!
GravityZone EDR Features
- A high percentage of actionable detections with minimum noise in MITRE ATT&CK Evaluations.
- Automated attack correlation across endpoints for faster response.
- Visualization of the attack chain in real-time for quick analysis.
- Advanced search tools to detect IOCs, security events, and endpoint configurations to support regulatory compliance.
GravityZone EDR Pricing
GravityZone EDR offers three subscription plans—Small Business, Medium-to-Large Business, and Managed Service Providers.
The pricing for the Small Business Plan starts at $220.49/year for 10 devices. For other subscription plans, pricing is available upon request. It offers a free trial to explore the product.
4. SentinelOne Singularity Endpoint
Best for AI-powered Defense
Singularity Endpoint is an AI-powered EDR platform that protects, detects, and responds to security threats across all endpoints on your network, identities, and more.
It uses a lightweight, independent agent that runs efficiently without slowing down devices. The platform is designed to reduce system impact and minimize interactions with the kernel, which ensures stability and smooth performance while providing strong security.
Singularity Endpoint’s natural language querying on first and third-party data makes it simple to detect and investigate threats.
Also, it leverages AI models with strong safeguards to prevent misuse and false information (hallucinations). I’m impressed with its ability to streamline SecOps with GenAI.
With Singularity Endpoint, you get coverage across Windows, macOS, and Linux operating systems.
Singularity Endpoint Features
- Uses on-device AI to analyze behavior and patterns to autonomously block malware and ransomware.
- Provides visibility into system-level and identity-based attacks.
- Automated or one-click response and rollback actions for threat remediation.
- Storyline® links related events and provides real-time attack correlation and context.
- Correlates and prioritizes alerts across workstations, identities, and exposures.
Singularity Endpoint Pricing
Singularity Endpoint pricing is available upon request. Request a demo to experience the platform.
5. Sophos Endpoint
Best for Ransomware Protection
Sophos Endpoint comes with an AI-powered EDR that can help you detect, investigate, and respond to advanced multi-stage threats with precision.
It’s equipped with CryptoGuard, which checks file content for malicious encryption. If it finds any malicious process running on a victim’s computer or compromised network, it blocks the process instantly.
Sophos Endpoint protects your valuable data from new and novel file encryption attacks. I liked the fact that it can also reverse the damage caused by ransomware, meaning it can reverse any encrypted files to their original state.
CryptoGuard’s Master Boot Record (MBR) protection keeps your hard drives safe from ransomware that can render the computer unbootable.
I tried the tool on my PC and here’s what the dashboard looks like. 👇🏼
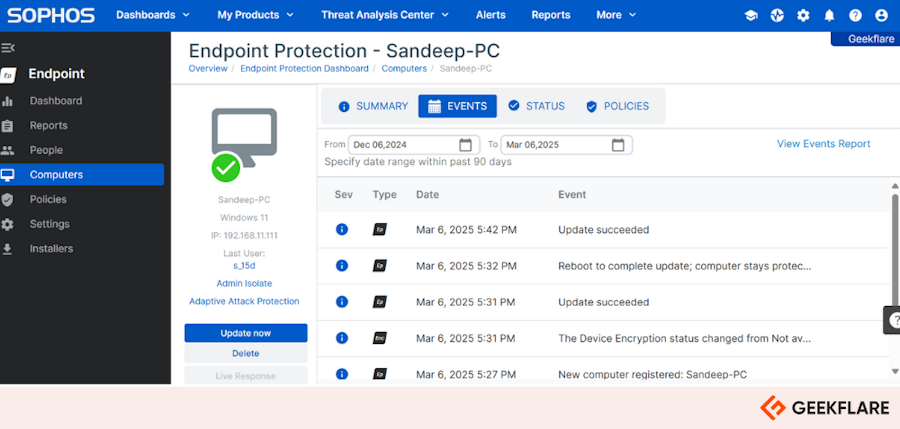
It works on all leading desktops and mobile devices, including Windows, macOS, Linux, Android, and iOS devices.
Sophos Endpoint Features
- Comprehensive prevention-first security blocks threats using multiple advanced techniques.
- Deep learning AI models protect against known and unknown attacks.
- Web, application, and peripheral controls reduce attack surfaces.
- Behavioral analysis, anti-ransomware, and anti-exploitation stop threats before escalation.
- Automatic “shields up” defense blocks suspicious activity instantly.
Sophos Endpoint Pricing
Sophos Endpoint follows custom pricing, so you need to contact the company to get the pricing details. A free trial is available to explore the product.
6. CrowdStrike Falcon
Best for World-class Threat Intelligence
CrowdStrike is a reputed name in the cybersecurity industry. CrowdStrike Falcon’s AI-powered detection, response, and protection is backed by world-class threat intelligence.
In SE Labs’s testing, it has achieved 100% ransomware detection,100% prevention, and 100% accuracy.
In my research, I have noted that CrowdStrike Falcon can prevent a wide range of threats, from commodity malware to fileless, and zero-day threats. Moreover, its threat intelligence, script control, industry-first indicators of attacks, and advanced memory scanning detect and block security threats early in the kill chain.
It lets you gain full visibility across the cloud, endpoints, and identities to detect and stop cross-domain attacks. Correlating threats across different areas prevents attackers from moving laterally within your systems, which reduces the risk of widespread breaches.
The platform’s Charlotte AI and AI-powered risk scoring help your security teams quickly identify and prioritize threats, reducing analysis time from hours to minutes.
It supports Windows, macOS, Linux, ChromeOS, Android, and iOS, including legacy operating systems.
CrowdStrike Falcon Features
- Next-gen antivirus.
- USB device control.
- Host firewall control.
- Threat hunting and intelligence.
CrowdStrike Falcon Pricing
CrowdStrike Falcon offers four plans—Go, Pro, Enterprise, and Complete MDR. EDR capabilities are available in the Falcon Enterprise plan and MDR plan.
The Falcon Enterprise plan costs $184.99/device/year, and the pricing of the MDR plan is available on request. A 15-day free trial is available.
7. Broadcom Carbon Black EDR
Best for SOC Teams
Broadcom Carbon Black EDR allows you to hunt security threats in real-time and visualize the complete attack kill chain using Carbon Black Cloud’s aggregated threat intelligence. Its ability to continuously record and store endpoint activity data makes it a useful tool for Security Operations Center (SOC) teams.
Carbon Black EDR helps your security teams avoid redundant threat hunting. It combines custom threat intelligence and cloud-delivered threat intel to detect known and evolving threats.
I liked its automated watchlist feature, which continuously monitors suspicious activity. So your security teams don’t have to waste time hunting the same threat twice. Integrations with other security tools help scale investigations across even the largest enterprises.
Carbon Black EDR gives incident responders remote access to infected systems for fast threat containment. They can securely connect to compromised hosts without needing to be on-site. As a result, they can pull or push files for investigation, kill malicious processes to stop attacks and perform memory dumps for deeper analysis.
It is compatible with Windows & Windows Server, MacOS, Red Hat, CentOS, Oracle RHCK, and SuSE. You can also deploy it on-premises and in the cloud.
Carbon Black EDR Features
- Default and customizable behavioral detection.
- Multiple customizable threat intel feeds.
- Automated watchlists capture queries.
- Process and binary search of centralized data for fast investigation.
- Interactive attack chain visualization.
- Live response for fast remediation.
Carbon Black EDR Pricing
Broadcom hasn’t published any pricing information for Carbon Black EDR on its website. You need to contact its sales team or partners to get pricing details.
8. Cynet EDR
Best for Continuous Risk Scanning
Cynet EDR is a part of the Cynet security platform that offers various security solutions, including EPP, Mobile Threat Detection (MTD), Network Detection and Response (NDR), and more. It combines signals across endpoints, users, networks, and deception technology to improve protection across your attack surface.
The platform continuously scans your endpoints for security gaps, detecting misconfigurations and unpatched software vulnerabilities. Identifying known Common Vulnerabilities and Exposures (CVEs) helps prevent exploits. You can also prioritize and categorize all identified risks with detailed contexts.
I like its capability to log any file or process action so you can easily carry out digital forensics. Also, it allows you to create complex automated investigations and remediation through playbooks, saving your security team tons of hours of manual work.
Additionally, Cynet EDR supports Active Directory integration, which lets you block and reset passwords as part of the remediation process.
Cynet EDR Features
- Windows events visibility.
- Network, files & processes event visibility.
- Custom detection policies.
- Forensic and automated investigations.
- Secure remote shell.
- Application and endpoint visibility.
Cynet EDR Pricing
Cynet offers two subscription packages—Elite and All in One. The Elite plan pricing starts at $7/endpoint/month. A free demo is available.
9. WatchGuard EDR
Best for Zero-Trust Application Service
WatchGuard EDR implements AI-driven technologies to continuously monitor your endpoint devices and servers to prevent malware and zero-day threats.
I like its Zero-Trust Application Service, which watches and classifies every app and processes it independently. It removes the need for manual alerts, so you don’t have to manage them yourself. With zero-trust application service in place, only trusted and verified programs can run on your devices.
WatchGuard’s Threat Hunting Service actively looks for hidden cyber threats before they cause damage. It uses continuous monitoring and advanced analytics based on the MITRE ATT&CK™ Framework. The platform also blocks ransomware and restores encrypted files.
Lastly, you get an always-on analysis to easily track suspicious behavior and patterns.
WatchGuard EDR Features
- Detects new and unknown malware using machine-learning-based Zero-Trust Application Service.
- Stops ransomware before it spreads with real-time scanning and antivirus protection.
- Analyzes suspicious hacking activity through advanced Threat Hunting Service.
- Blocks attackers from exploiting software vulnerabilities using behavioral analysis.
- Reduces IT workload by combining EPP and EDR for automated threat response.
- Automates threat remediation to clean up and restore systems quickly.
WatchGuard EDR Pricing
You need to contact the WatchGuard sales team or a reseller to learn the pricing details of WatchGuard EDR. It offers a free trial.
10. Trellix EDR
Best for Simplifying EDR with AI
Trellix EDR quickly identifies real threats, reducing time wasted on false alarms. Its AI-driven investigation automates threat analysis, which helps you respond faster and with precision. When a threat is detected, it can quickly remediate it.
It delivers clear, actionable threat alerts without unnecessary noise. Plus, you get early insights into threats before attacks.
Trellix EDR uses AI-guided investigations to give analysts quick insights into attacks. It generates detailed reports with one click, helping you close cases faster.
I like Trellix EDR because it continuously collects data and uses multiple analytic engines to detect suspicious behavior accurately. It helps make sense of alerts and guides the right response. All of this can save you time and improve threat management.
You can deploy it easily with Trellix® ePO software or SaaS-based ePO.
Trellix EDR Features
- Analyzes and correlates artifacts related to a threat.
- Links threat events, helping identify gaps and vulnerabilities.
- Covers MITRE ATT&CK Matrix framework.
- Offers integrated forensics that can capture data both online and offline.
Trellix EDR Pricing
Trellix EDR pricing is available upon request. You can watch an interactive demo to explore its features or request a personalized demo.
More EDR Solutions
Here are a few more EDR tools I’ve explored, but didn’t include in the top 10.
| EDR Tool | Best For |
|---|---|
| 11. Cybereason EDR | Best for ML-powered Detection |
| 12. ESET Enterprise Inspector | Best for Threat Detection and Digital Forensics |
| 13. Cortex XDR | Best for MITRE ATT&CK Coverage |
How To Pick the Best EDR Tool
To pick the best EDR tool, you must first examine your requirements. Check, for example, how many endpoints you need to monitor. Then, find EDR tools that have the following important features.
- Next-Gen Anomaly Detection: Find an EDR tool that leverages machine learning and AI for real-time threat detection and includes behavioral analysis.
- Threat Feeds and Attack Vectors: The tool must integrate with threat feeds for updated attack vectors and real-time updates.
- Integration with Other Security Platforms: Your chosen EDR tool should be compatible with existing security systems and offer user-friendly dashboards.
- Response Capabilities: The tool has to provide automated remediation and effective incident triage.
- Operating System Support and Agent Type: The EDR solution must support standard operating systems. You should also decide between agent-based and agentless solutions.
- Pricing and Customer Support: It should offer transparent pricing, comprehensive documentation, free trials, and quality customer support.
- MITRE Scores: Buy an EDR tool with high MITRE ATT&CK scores. The higher the score, the better the detection and response capabilities.
- Customization and Scalability: Custom detection implementation should be allowed to ensure scalability and growth with organizational needs.
I suggest you take free trials or demos of as many EDR tools as possible to find the best fit for your requirements.
Frequently Asked Questions About EDR Tools
EDR (Endpoint Detection and Response) is a cybersecurity solution that monitors, detects, and responds to threats on endpoints, including laptops, servers, workstations, and more. EDR tools use behavioral analysis, AI, and threat intelligence to identify attacks and automatically block or isolate threats.
EDR (Endpoint Detection and Response) focuses on detecting and responding to threats on endpoints like laptops and servers, using AI and threat intelligence.
XDR (Extended Detection and Response) extends security across networks, cloud, and applications, providing a centralized view for faster, broader threat detection and response across multiple environments.
Antivirus protects your devices by detecting and removing known malware using signature-based scanning.
Endpoint Protection Platform (EPP) offers broader security by preventing malware, ransomware, and fileless attacks using AI and behavioral analysis.
EDR (Endpoint Detection and Response) goes further by continuously monitoring endpoints, detecting advanced threats, and enabling real-time investigation and response.
-
 EditorAnirban Choudhury is as an editor at Geekflare, bringing over 7 years of experience in content creation related to VPNs, Proxies, Hosting, Antivirus, Gaming, and B2B2C technologies.
EditorAnirban Choudhury is as an editor at Geekflare, bringing over 7 years of experience in content creation related to VPNs, Proxies, Hosting, Antivirus, Gaming, and B2B2C technologies.


