It’s always a good idea for an attacker to know where a WAF is typically utilized on a network before they start fingerprinting.
Penetration testers must be aware of a WAF before beginning a web application engagement since the outcome of their assaults may be impacted.
But before that…
What is WAF?
WAF (Web Application Firewall ) plays a significant role in website security. They filter and monitor the traffic. Web Application Firewalls provide protection against major flaws. Many organizations are modernizing their infrastructure to include web application firewalls. According to ethical hacking experts, web application firewalls cannot fix security issues on their own; adequate configuration is required to recognize and block external threats.
A WAF differs from a traditional firewall in that it may filter the content of specific online applications, whereas traditional firewalls act as a safety barrier between servers.
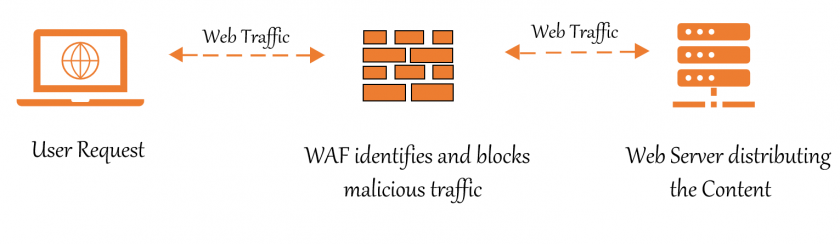
An HTTP interaction is subjected to a set of rules. These rules address typical vulnerabilities like cross-site scripting and SQL injection in general.
There are many free and open-source tools on the internet that can discover the firewalls behind web applications.
And in this article, we’ll look at the approaches and tools that can be used to discover a WAF.
Please note: In this tutorial, I have used my own site for enumerating the details. Don’t perform scanning or other hacking activity on any website without prior permission from the owner.
Manual Discovery
Detecting using TELNET
Telnet is mainly used by network administrators and penetration testers. Telnet enables you to connect to remote hosts over any port, as previously stated.
- HTTP parameters are often left (or inserted) in response headers by web application firewalls.
- Telnet can be used to obtain basic gathering information such as the server and cookies used in fingerprinting.
- Type
Telnet Targetwebsite.com 80
root@writer: # telnet Targetwebsite.com 80
Trying 18.166.248.208...
Connected to Targetwebsite.com.
Escape character is '^]'. After running the command above, write HEAD / HTTP / 1.1 and press the enter key.
root@writer: # telnet 18.166.248.208 80
Trying 18.166.248.208...
Connected to 18.166.248.208.
Escape character is '^]'.
HEAD / HTTP/1.1
Host: 18.166.248.208
HTTP/1.1 200 OK
Date: SUN, 10 Oct 2021 05:08:03 IST
Server: Apache X-Powered-By: PHP/5.3.5 ZendServer/5.0
Set-Cookie: SESSIONID VULN SITE=t25put8gliicvqf62u3ctgjm21; path=/
Expires: Thu, 19 Nov 1981 08:52:00 IST
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
X-Varnish: 4723782781
Age: 0
Via: 1.1 varnish
Connection: close
Content-Type: text/html
Connection closed by foreign host.It indicates the server on which the website is hosted and the back-end language on which it was created after using telnet on the target port 80.
Some WAF systems allow the header to be modified, and they can also cause the webserver to send HTTP replies that are different from the standard ones.
As shown in the result above, the webserver responded to our request and revealed that the firewall/edge gateway was Varnish.
Automated Discovery
#1. Detecting using NMAP
Nmap, which has a script that can identify a web application firewall, can also be used for this purpose.
- Nmap is a security assessment tool that many pen-testers and network administrators commonly utilize.
- Nmap is used to obtain information about the target.
- The script was run against the same webpage as before
- Type the command
nmap –script=http-waf-fingerprint targetweb.com
root@writer:# nmap --script=http-waf-fingerprint targetwebsite.com
Starting Nmap 7.90 ( https://nmap.org ) at 2021-10-10 07:58 IST
Nmap scan report for targetsite.com (18.166.248.208)
Host is up (0.24s latency).
Not shown: 982filtered ports
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
| http-waf-fingerprint:
| Detected WAF
| Citrix Netscaler
443/tcp open https
5432/tcp closed postgresql
8080/tcp closed http-proxy
Nmap done: 1 IP address (1 host up) scanned in 25.46 seconds After using the above Nmap command, the Citrix Netscaler firewall was detected.
#2. Detecting using Whatwaf
Whatwaf is a security tool for fingerprinting web apps and detecting the presence of any WAF. This tool is useful for determining whether a web application is protected by a WAF during security assessments.
If this is the case, bypassing and avoidance strategies may be helpful in further testing or exploiting the online application.
Firewall bypassing, application detection, application fingerprinting, and software identification are all frequent uses for WhatWaf. Network
Pen-testers and security professionals are the intended users of this program.
How to install WhatWaf?
Installation on Kali-Linux
sudo apt install python3-pip
git clone https://github.com/ekultek/whatwaf
cd whatwaf
sudo pip3 install -r requirements.txtAt launch, without a Python version, we can easily specify an executable file:
./whatwaf --help
However, because we did not install Python 2 dependencies, it is advised that you specifically provide the Python version.
python3 ./whatwaf --helpTool Usage
Whatwaf firewall detection tool is straightforward to use! We just need to execute the following command:
./whatwaf -u https://www.targetsite.comAs you can see below, this tool detected the firewall for the provided website URL.
Reminder! – I used my own site for the scanning
┌──(root💀kali)-[/home/writer/WhatWaf]
└─# ./whatwaf -u https://www.renjith.org
,------.
' .--. '
,--. .--. ,--. .--.| | | |
| | | | | | | |'--' | |
| | | | | | | | __. |
| |.'.| | | |.'.| | | .'
| | | | |___|
| ,'. |hat| ,'. |af .---.
'--' '--' '--' '--' '---'
/><script>alert("WhatWaf?<|>v2.0.3($dev)");</script>%00
[11:12:34][ERROR] you must install psutil first `pip install psutil` to start mining XMR
[11:12:34][INFO] checking for updates
[11:12:34][WARN] it is highly advised to use a proxy when using WhatWaf. do so by passing the proxy flag (IE `--proxy http://127.0.0.1:9050`) or by passing the Tor flag (IE `--tor`)
[11:12:34][INFO] using User-Agent 'whatwaf/2.0.3 (Language=2.7.18; Platform=Linux)'
[11:12:34][INFO] using default payloads
[11:12:34][INFO] testing connection to target URL before starting attack
[11:12:35][SUCCESS] connection succeeded, continuing
[11:12:35][INFO] running single web application 'https://www.renjith.org'
[11:12:35][WARN] URL does not appear to have a query (parameter), this may interfere with the detection results
[11:12:35][INFO] request type: GET
[11:12:35][INFO] gathering HTTP responses
[11:12:42][INFO] gathering normal response to compare against
[11:12:42][INFO] loading firewall detection scripts
[11:12:42][INFO] running firewall detection checks
[11:12:44][FIREWALL] detected website protection identified as 'Apache Generic'
[11:12:44][INFO] starting bypass analysis
[11:12:44][INFO] loading payload tampering scripts
[11:12:45][INFO] running tampering bypass checks
[11:19:09][SUCCESS] apparent working tampers for target:
------------------------------
(#1) description: tamper payload by changing characters into a wildcard
example: '/bin/cat /et?/?asswd'
load path: content.tampers.randomwildcard
------------------------------As shown in the result above, the webserver responded to our request and revealed that the firewall was Apache. We can also use the tor service to scan for the WAF, but it may increase the latency.
./whatwaf -u https://www.targetsite.com --tor
The main advantage of the Whatwaf tool is, it automatically tries to give the payloads to bypass the revealed firewall.
#3. Detecting Using Wafw00f
The most well-known tool for detecting the web application firewall is Wafw00f. Wafw00f sends an HTTP request to the web application firewall to identify it. When sending HTTP requests fails, wafw00f makes a malicious HTTP request. If making a malicious HTTP request fails, wafw00f examines prior HTTP requests and employs a simple algorithm to determine whether the web application firewall reacts to our attacks.
Wafw00f isn’t preinstalled in Kali Linux distributions.
How to install Wafw00f?
The zip package is available for download from the official GitHub source.
Download the Wafwoof Tool. You can also use the git client to clone the repository. To get the package, run the commands:
$ git clone https://github.com/EnableSecurity/wafw00f.gitTo download the wafw00f tool in the system, navigate to the wafw00f folder or directory and perform the following command.
$ python setup.py installThe setup file will be processed, and wafw00f will be installed in the system.
Tool Usage
To use this tool, run this command.
$ wafw00f <url>REMINDER – Only scan the websites that you are permitted to test
┌──(root💀kali)-[/home/writer/wafw00f]
└─# wafw00f https://webhashes.com
______
/ \
( Woof! )
\ ____/ )
,, ) (_
.-. - _______ ( |__|
()``; |==|_______) .)|__|
/ (' /|\ ( |__|
( / ) / | \ . |__|
\(_)_)) / | \ |__|
~ WAFW00F : v2.1.0 ~
The Web Application Firewall Fingerprinting Toolkit
[*] Checking https://whatismyip.com
[+] The site https://whatismyip.com is behind Cloudflare (Cloudflare Inc.) WAF.
[~] Number of requests : 2Too bad, firewall was detected!
We will try a different target website for the discussion purpose.
┌──(root💀kali)-[/home/writer/wafw00f]
└─# wafw00f https://renjith.org
______
/ \
( Woof! )
\ ____/ )
,, ) (_
.-. - _______ ( |__|
()``; |==|_______) .)|__|
/ (' /|\ ( |__|
( / ) / | \ . |__|
\(_)_)) / | \ |__|
~ WAFW00F : v2.1.0 ~
The Web Application Firewall Fingerprinting Toolkit
[*] Checking https://renjith.org
[+] Generic Detection results:
[-] No WAF detected by the generic detection
[~] Number of requests: 7
No Firewall is detected this time.
And to use it in verbose mode, run the following command.
wafw00f <url> -v You can see a few additional capabilities of this utility by executing this command.
wafw00f <url> --help Wrapping Up 👨💻
In this article, we looked at different strategies and tools for detecting web application firewalls. This is an important activity that must be performed during the information collection stage of every web application penetration test.
Furthermore, knowing that a WAF is in place allows the penetration tester to try various approaches to get around the defenses and exploit any holes in the online application.
According to an ethical hacking researcher, having a web application firewall (WAF) is increasingly necessary. Analyzing your web application logs to detect new assaults occurring on the back-end web application server is always important. This allows you to customize rules in your web application firewall to provide the highest level of protection.
You may also be interested in reading: Vulnerabilities using Nikto Scanner.

