IoT projects are a web of interconnected devices and sensors to collect and share data for automation, monitoring, etc. in industries such as healthcare, manufacturing, retail, agriculture, transportation, automotive, and more.
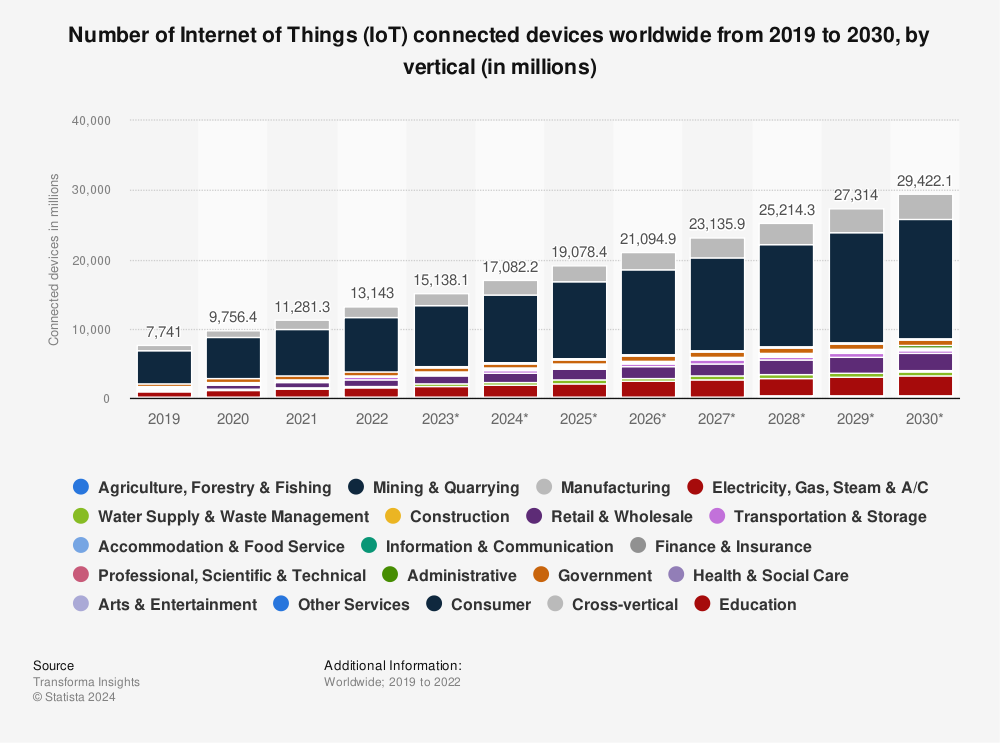
The number of active IoT devices in 2020 was over 9 billion, and this number is expected to touch 29.422 billion by 2030, per Statista. However, exponential growth comes with a host of significant IoT challenges. Things such as device diversity, optimal connectivity, data collection and sharing security, scalability, etc., are some of the key issues we are going to delve into.
Common Challenges in IoT Projects
The below 4 are the main challenges in IoT projects in planning, implementation and maintenance.
- Technical Challenges
- Security and Privacy Challenges
- Scalability and Integration Challenges
- Regulatory and Compliance Issues
The following sections will discuss the above challenges in detail with the most practiced IoT solutions.
Technical Challenges
Technical issues primarily cover device diversity, connectivity and data handling, which a business should prepare for upfront while planning IoT implementation.
Device Diversity
Device diversity is the biggest weakness that no IoT project can completely escape from. It complicates IoT software development, deployment, maintenance, and integration with existing infrastructure.
Specifically, ensuring seamless device interoperability becomes complex since each IoT device can have different operative and communication protocols. Moreover, ensuring a consistent user experience across connected devices is critical.
Solutions
- Utilize widely accepted IoT communication protocols (such as MQTT, CoAP, and HTTP) to ensure devices can interoperate effectively.
- Modular software design ensures easy updates, maintenance, and integrations.
Connectivity Issues
Device connectivity is a significant IoT challenge because devices are sometimes installed in remote & inaccessible locations, which might not have the best of network coverage.
Signal interference is another problem IoT connections battle within obstructive surroundings.
Constant internet connectivity is often a power-hungry process. This means the IoT device should have access to seamless power through supply lines, which isn’t straightforward, owing to the number and location of IoT devices. An alternative is using batteries, which again limits the output, thanks to their size and maintenance.
Areas with poor network can be restrictive for devices (like security cameras) exchanging real-time data due to greater latency.
Solutions
- Use multiple connectivity protocols such as cellular, Wi-Fi, and satellite to ensure uninterrupted connectivity in remote locations.
- Implement mesh networking to allow devices to relay signals to each other for better coverage.
- Mitigate signal interference by using less congested frequency bands or dynamically switching bands based on real-time analysis.
- Optimize antenna design and placement for better connectivity.
- Utilize energy-efficient connectivity protocols (like LoRaWAN, Bluetooth Low Energy (BLE), etc.) for minimum power consumption.
- Smart power management techniques like duty cycling can improve the energy efficiency of IoT devices, especially the ones running on battery power.
Data Management
Data management is a critical domain with problems spawning across data transmission, storage, processing, and analysis.
IoT devices transmit huge chunks of real or near-real-time data, which can be in many different formats and structures. Data transmission can also suffer from 3rd party interference, such as man-in-the-middle attacks.
Data processing delays can pose significant risks, since the ultimate aim of any IoT project is to get the information needed to take remedial action quickly in case of an emergency.
Solutions
- Use cloud storage providers such as Amazon S3, Google Cloud, and Azure Blob for a scalable IoT storage solution.
- Deploy techniques like data compression and aggregation to reduce the data transmission size.
- Use flexible data models (like JSON and Avro) to accommodate diverse data formats.
- Store raw data in data lakes for diverse analytics, and remain open to adopting more efficient analysis techniques and tools as they emerge in the future.
- Encrypt data at rest and in transit for robust security.
- Deploy edge computing platforms such as AWS IoT Greengrass, Azure IoT Edge, or Google Cloud IoT Edge to process and analyze data closer to the source.
Security and Privacy Challenges
Security and privacy are crucial aspects of managing data-heavy phenomenon such as the Internet of Things. One must deploy preventive measures and also prepare for the fateful outcome in case nothing works. Some of the well-known IoT security issues are data breaches and unauthorized access, as explained below.
Data Breaches
Cyberattacks causing data breaches are one of the biggest hurdles for any business implementing IoT on a scale. Such events bring a multitude of risks (including lawsuits) that can prove fatal to any organization if not handled properly and in advance.
Data breaches can expose sensitive customer information, trade secrets, and other confidential data. This can result in irreparable damage to the brand image and cause financial losses.
Solutions
- Keep all IoT devices secure with the latest firmware updates and security patches.
- Divide IoT devices into segments to minimize the impact of a potential threat.
- Appoint 3rd-party agencies periodically to conduct security audits for the entire IoT project.
- Consider obtaining cybersecurity insurance to mitigate financial risks associated with data breaches.
Unauthorized Access
Unauthorized access poses unique and threatening risks to any business IoT infrastructure, which can result in privacy issues, intellectual property theft, and even business closure.
IoT devices often collect the personal data of their users, which can result in privacy violations (and possible lawsuits) if it leaks out to places like the dark web. Intellectual property theft can undermine an organization’s competitive advantage.
At the very least, unauthorized access can result in temporary stoppage in the IoT operations of any business, which can translate in significant financial losses. Besides, reputation damage is another aftereffect which can cause existing customers fleeing to competition and harm future prospects.
Finally, such incidents can lead to compliance violations, resulting in fines, legal penalties, and loss of business licenses.
Solutions
- Implement multifactor authentication to prevent unauthorized access.
- Deploy firewalls and Intrusion Detection Systems (IDS) for a robust cybersecurity blanket.
- Limit access to IoT devices and systems to only individuals needing it for their job responsibilities.
Scalability and Integration Challenges
Scaling IoT projects, though it looks straightforward, brings significant problems, such as massive data volumes, device management, bandwidth and computing requirements, etc. Likewise, integration with existing infrastructure can become tedious because of interoperability and security challenges with legacy systems.
Remedial measures for scaling IoT projects can include using edge computing, cloud data services, container orchestration tools, etc. For smoother integration, businesses can deploy middleware, APIs, and modular software design.
Regulatory and Compliance Issues
Being compliant with the privacy laws in the concerned jurisdiction is vital for every business IoT project. These can include GDPR, CCPA, etc., depending on the operational area.
In addition, an IoT project can be subjected to cybersecurity regulations, device safety certifications, environmental regulations, interoperability standards, trade regulations, and more.
Consequently, it’s best to conduct extensive research upfront and implement location-based policies from the planning stage itself.
Future-Proofing IoT Projects
Making IoT projects future-proof is crucial for the security, scalability, longevity, and relevancy of such endeavors against changing technological landscapes. Ultimately, these projects are significant investments, and it’s desirable for any organization to preserve their value for the maximum possible duration.
The below strategies can help in the future-proofing of IoT projects.
- Modular design: Build IoT systems using a modular design to ensure easy upgrade, replacement, and overall maintenance without disturbing other components or needing an entire redesign.
- Standardization: Deploy open standards and protocols for communication and interoperability between IoT devices and systems. This approach will guarantee compatibility with other devices from different vendors and future technologies.
- Scalability: Consider the potential for increased data volumes, more devices, larger user base, and evolving functionalities by choosing a horizontally scalable tech stack.
- Security: Implement robust security protocols, such as device physical security, data encryption, authentication, timely updates, vulnerability audits, and more, from the get-go.
- Feedback: Analyze device data and user interactions to identify areas for improvement and optimize your project over time.
- Awareness: Stay informed about emerging technologies, changing regulatory requirements, and general IoT industry trends.
Conclusion
IoT is the backbone of the ongoing technological revolution. It’s everywhere, and the future is about its exponentially widespread adoption across businesses and individuals.
However, because of its diversity, IoT projects need careful planning and implementation with strategies like standardized protocols, modular design, scalability, regulatory compliance, efficient data management, and more as discussed in this article.
Besides, every business should consider future-proofing their IoT projects for the utmost longevity and value. To help you with these challenges of the Internet of Things, we have something more in these best IoT platforms and IoT architecture tutorials.
Frequently Asked Questions about IoT Projects
Creating an IoT project involves multiple steps, starting from planning & research, choosing hardware & communication protocols, to developing software, implementing security measures, designing user interface, testing, deploying, monitoring, and maintenance.
This can be a long and complex process, where joining IoT communities can prove helpful.
IoT implementation is a complex endeavor needing multiple things, such as device interoperability, data management, security, and compliance, to work perfectly in tandem. Owing to these many variables in the success equation, it’s common to spot IoT projects that fall short of reaching their full potential.

![IoT Projects Common Challenges and Solutions [2024] (2)](https://geekflare.com/cdn-cgi/image/width=1200,height=630,fit=crop,quality=90,format=auto,onerror=redirect,metadata=none/wp-content/uploads/2024/04/IoT-Projects-Common-Challenges-and-Solutions-2024-2.jpg)