In ethical hacking and penetration testing, password cracking is crucial in gaining access to a system or a server.
In systems and databases, passwords are rarely saved in plain-text form.
Passwords are always hashed before being stored in the database, and the hash is compared during the verification process.
Depending on the encryption employed, different systems store password hashes in different ways. And if you have hashes, you can easily crack any password.
And in this article, we’ll explore how to crack password hashes using a handy and excellent Hashcat command-line tool.
So let’s get started.
But before that…
What is a Hash function?
Hashing is the process of converting a normal input text into a fixed-size string of text using some mathematical function which is known as the Hash Function. Any text, regardless of length, can be turned into a random combination of integers and alphabets using an algorithm.
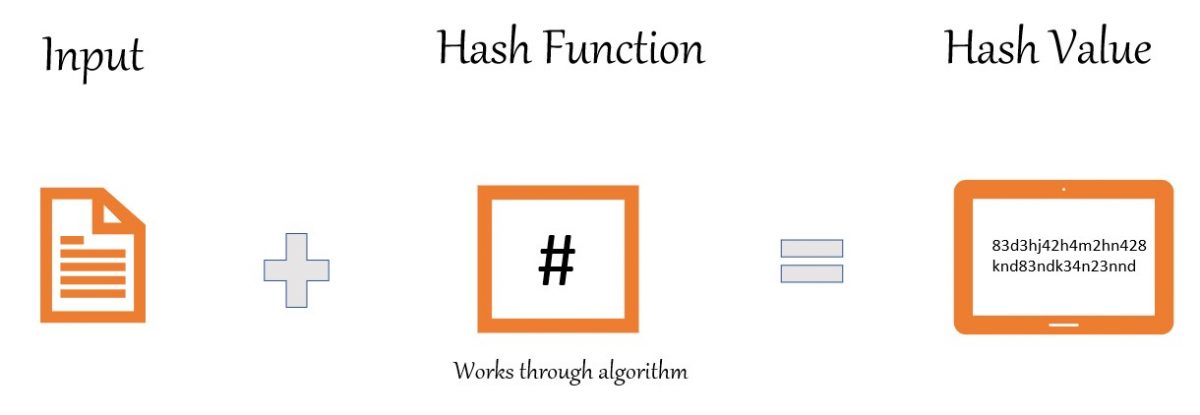
- Input refers to the message that will be hashed.
- The hash function is the encryption algorithm like MD5 and SHA-256 that converts a string into a hash value.
- And finally, the hash value is the result.
What is Hashcat?
Hashcat is the quickest password recovery tool. It was designed to break the high complex passwords in a short amount of time. And this tool is also capable of both wordlist and brute force attacks.
Hashcat has two variants. CPU and GPU (Graphical Processing Unit) based. The GPU-based tool can crack the hashes in less time than the CPU. You can check the GPU driver requirements on their official website.
Features
- Free and open-source
- More than 200 hash type variations can be implemented.
- Supports multi-operating systems like Linux, Windows, and macOS.
- Multi-Platforms like CPU and GPU support are available.
- Multiple hashes can be cracked at the same time.
- Hex-salt and hex-charset files are supported, along with the automatic performance tuning.
- A built-in benchmarking system is available.
- Distributed cracking networks can be supported using overlays.
And you can see other features also from their website.
Installation of Hashcat
First, make sure your Linux system is up to date with the newest programs and tools.
For this, open a terminal and type:
$ sudo apt update && sudo apt upgradeHashcat is usually pre-installed in Kali Linux. You can find the tool under the password cracking section. But if you need to install it manually in any Linux distribution, type the following command in the terminal.
$ sudo apt-get install hashcatHow to Use Hashcat
To get started with Hashcat, we’ll need some password hashes. If you don’t have a hash to crack, we will create some hashes first.
To create hashes using the command line, just follow the below format.
echo -n "input" | algorithm | tr -d "-">>outputfienameFor example, you can see I turned some words into hashes using the md5 algorithm below.
┌──(root💀kali)-[/home/writer/Desktop]
└─# echo -n "geekflare" | md5sum | tr -d "-">>crackhash.txt
echo -n "password123" | md5sum | tr -d "-">>crackhash.txt
echo -n "Webtechnology" | md5sum | tr -d "-">>crackhash.txt
echo -n "microsoftteams" | md5sum | tr -d "-">>crackhash.txt
echo -n "recyclebin" | md5sum | tr -d "-">>crackhash.txtAnd the output will be saved in the crackhash.txt file.
Now we will check the hashes which were saved in the given file.
┌──(root💀kali)-[/home/writer/Desktop]
└─# cat crackhash.txt
066d45208667198296e0688629e28b14
482c811da5d5b4bcd497ffeaa98491e3
72a2bc267579aae943326d17e14a8048
2192d208d304b75bcd00b29bc8de5024
caae8dd682acb088ed63e2d492fe1e13You can see, now we have some hashes to crack. This is the procedure to create a hash by using the algorithm of your choice.
The next step is to kick start a Hashcat tool in your Linux machine. Just use the following command to use Hashcat.
$ hashcat --helpIt’ll bring up all of the options you’ll need to know to run the tool. On the terminal, you can find all the attack and hashcat modes.
The general form of the hashcat command is
$ hashcat -a num -m num hashfile wordlistfileHere the ‘num’ represents a specific attack and hash mode to use. If you scroll the terminal, you can find the exact numbers for every attack and hash mode, like for md4 – the number is 0, and for sha256 algorithm – the number is 1740.
The wordlist I am going to use is rockyou wordlist. You can easily find that wordlist in the path /usr/share/wordlists.
You can even use the locate command to find that wordlist path.
┌──(root💀kali)-[/home/writer]
└─# locate rockyou.txt
And finally, to crack the hashes using the wordlist file, use the following command.
$ hashcat -a 0 -m 0 ./crackhash.txt rockyou.txtAfter running this command, you may get a runtime error ( Token length exception error ) which can be resolved easily.
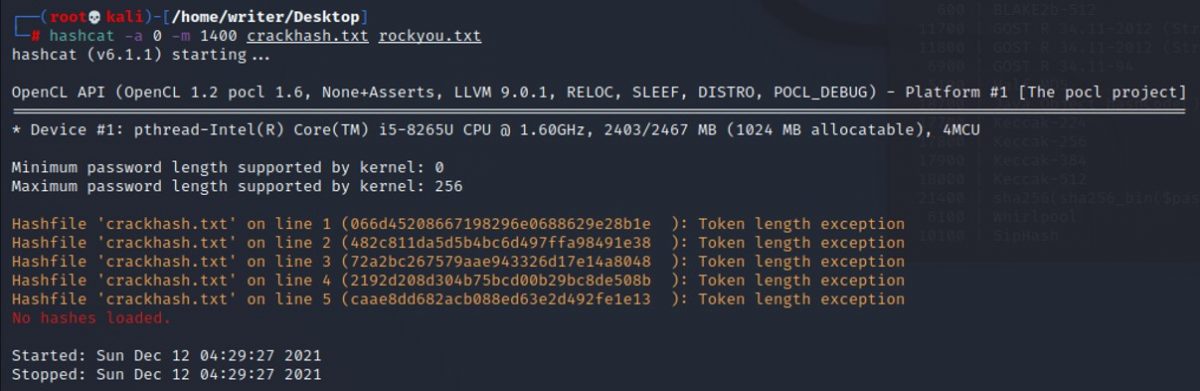
To resolve this, save each hash separately in a different file. This error occurs if you have a low CPU or GPU speed. If your computer has a high-speed processor, you can easily crack all the hashes at the same time as a single file itself.
So after fixing the error and everything, the result will be like this.
┌──(root💀kali)-[/home/writer/Desktop]
└─# hashcat -a 0 -m 0 hashcrack.txt rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-8265U CPU @ 1.60GHz, 2403/2467 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Dictionary cache built:
* Filename..: rockyou.txt
* Passwords.: 14344405
* Bytes.....: 139921671
* Keyspace..: 14344398
* Runtime...: 1 sec
8276b0e763d7c9044d255e025fe0c212: geekflare@987654
Session..........: hashcat
Status...........: Cracked
Hash.Name........: MD5
Hash.Target......: 8276b0e763d7c9044d255e025fe0c212
Time.Started.....: Sun Dec 12 08:06:15 2021 (0 secs)
Time.Estimated...: Sun Dec 12 08:06:15 2021 (0 secs)
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1059.6 kH/s (0.52ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 4096/14344398 (0.03%)
Rejected.........: 0/4096 (0.00%)
Restore.Point....: 0/14344398 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: 123456 -> pampam
Started: Sun Dec 12 08:06:13 2021
Stopped: Sun Dec 12 08:06:16 2021In the above result, after the dictionary cache details, you can notice, the hash was cracked, and the password was revealed.
Conclusion
I hope you have gained a better understanding of using Hashcat to crack passwords.
You may also be interested in knowing about the various brute-force tools for penetration testing and some of the best pentesting tools.

