Every day, thousands of websites get attacked, resulting in data breaches, financial losses, and reputational damage. Protecting websites from cyber threats is essential, and the first line of defense is to use a website security scanner to find vulnerabilities, malware, and misconfiguration.
There is no shortage of website security scanners, but too many options can be confusing, and not every security scanner is reliable. That’s where Geekflare comes in. We have tested and listed the most reliable scanner to test websites, API, and cloud infrastructure to strengthen the website’s security posture.
- 1. Sucuri – Best for Malware Detection and Removal
- 2. HostedScan – Best for Automated Vulnerability Scanning
- 3. Intruder – Best for Continuous Vulnerability Scanning
- 4. Attaxion – Best for External Attack Surface Management
- 5. Qualys – Best for Cloud-Based Security and Compliance
- 6. Quttera – Best for Web Malware Scanning
- 7. UpGuard – Best for Vendor Risk Management
- 8. SiteGuarding – Best for Real-Time Website Protection
- 9. Detectify – Best for Small to Medium Business
- 10. Probely – Best for Web & API Vulnerability Scan
- 11. Pentest Tools – Best for Web Penetration Testing
- 12. ImmuniWeb – Best FREE Security Scanner
- 13. Invicti – Best for DAST+IAST Scanning
- 14. Veracode – Best to Find and Fix Runtime Vulnerabilities
- 15. Qualys SSL Labs – Best for TLS Testing
- Show less
You can trust Geekflare
Imagine the satisfaction of finding just what you needed. We understand that feeling, too, so we go to great lengths to evaluate freemium, subscribe to the premium plan if required, have a cup of coffee, and test the products to provide unbiased reviews! While we may earn affiliate commissions, our primary focus remains steadfast: delivering unbiased editorial insights, and in-depth reviews. See how we test.
Sucuri
Best for Malware Detection and Removal
Sucuri is a website security and performance optimization tool mostly known for its manual malware removal. It has one of the best WordPress scanners, although it supports other platforms, including Magento, Joomla, phpBB, and Drupal.
Sucuri brings a combination of automation and manual expertise to fix most issues, including a hacked website. Every Sucuri subscription gets features such as SLA-backed unlimited manual malware removal support, a cloud-based WAF, and periodic website scans.
The Sucuri subscriptions also offer a content delivery network for additional redundancy and speed enhancement. Users can also let their websites put to free Sucuri scans to find vulnerabilities, malware, outdated software, and other issues.
Sucuri Pros
Integrated CDN and SEO spam scanner
Offers website uptime monitoring
Provides email, SMS, Slack alerts, and reports
Sucuri Cons
Lack of active support
High cost associated with the service
Sucuri Pricing
- Basic: $199.99/year
- Pro: $299.99/year
- Business: $499.99/year
- Junio Dev: $999.98/year
HostedScan
Best for Automated Vulnerability Scanning
HostedScan Security is an online service that automates vulnerability scanning for any business. It provides 100% open-source scanners to scan networks, servers, and web applications for security risks.
HostedScan offers a network vulnerability scanner to identify CVEs and outdated software. It also provides a web application scanner to detect SQL injection, vulnerable JavaScript libraries, cross-site scripting, and other threats. Additionally, there is a full TCP and UDP port scanner to uncover firewall and network misconfiguration.
Furthermore, HostedScan includes a TLS/SSL scanner to validate certificates and check for SSL vulnerabilities like Heartbleed and Robot.
HostedScan offers centralized vulnerability management for prioritizing tasks, generating reports, and simplifying protection for both organizations and managed service providers. It allows for easy importing of domains, IPs, and cloud accounts in one place, helping secure clients and potentially increasing revenue for MSPs.
HostedScan has a free tier offering up to three scans (one per target) a month. Paid plans come with benefits such as more targets, unlimited rescanning, automatic scans, data retention, vulnerability reporting, and more.
HostedScan Pros
Real-time threat detection and notification
Extensive vulnerabilities scan
Offers white label reports
Offers free tier
HostedScan Cons
Clunky user interface
Restricted to open-source scans
HostedScan Pricing
- Free: $0
- Basic: $39/month
- Premium: $109/month
Intruder
Best for Continuous Vulnerability Scanning
Intruder is a cloud-based platform combining vulnerability scans, network monitoring, and threat response to secure your web apps, APIs, or entire infrastructure. It’s easy to set up and constantly scans the attack surface for possible loopholes. It scans initiate on its own whenever it notices any change, an exposed service, or a critical issue.
Intruder robust security checks include identifying missing patches, misconfigurations, web application issues such as SQL injection and cross-site scripting, and CMS issues.
Intruder simplifies compliance by presenting audit-ready reports. Intruder notifies users of serious threats, tagged with their context-based priority levels, with easy-to-follow steps for remediation. One can check the cyber hygiene score and get an estimated time to fix issues.
Intruder integrates with AWS, GCP, and Azure, which makes adding targets for vulnerability management easier. Besides, one can add external IPs and local devices running popular OSes, including Windows, macOS, and Linux. Developers can leverage Intruder API to add targets, start scans, and obtain results. Teams can try Intruder with its 14-day free trial.
Intruder Pros
Great customer support
Offers actionable reports
Powerful scans with a user-friendly interface
Intruder Cons
Expensive for small businesses or individuals
Slow scans
Intruder Pricing
- Essential: $79/month
- Pro: $169/month
- Premium: custom
Attaxion
Best for External Attack Surface Management
Attaxion is a machine learning-powered attack surface management platform to quickly identify assets, classify security issues, and automate remediation.
Attaxion starts with identifying your external assets, followed by mapping their connections to find security vulnerabilities. It helps protect websites, IPs, SSLs, emails, ports, cloud assets, and more.
Attaxion prepares in-depth reports, which allows users to filter issues and check the associated CWE and CVE IDs, timestamps, and other metadata. It helps security teams to effectively prioritize and address vulnerabilities based on business context and risk.
Besides, one gets detailed remediation guidance and automatic ticket creation for faster turnaround times. Finally, continuous monitoring helps scan incoming assets and keep an eye on the overall security posture.
Attaxion Pros
360-degree asset coverage
Single view of all vulnerabilities
Uncover Internet-facing assets using AI-powered discovery
Offers API access
Attaxion Cons
Lack of integrations
Negligible user feedback is available
Attaxion Pricing
Attaxion offers a base plan priced at $129 per month. Other plans and custom pricing are available for specific needs
Qualys
Best for Cloud-Based Security and Compliance
Qualys reveals runtime vulnerabilities, OWASP top 10, misconfigurations, malware, and PII exposures within web applications and APIs. It allows teams to seamlessly monitor cloud or on-premises environments.
Qualys helps integrate web app scanning directly into CI/CD environments or ITSM ticketing systems to reduce MTTR. This enables faster identification, prioritization, and remediation.
Qualys lets teams consolidate data from third-party & manual pen testing tools and the automated scans in one single interface for better efficiency.
SSL Server Test by Qualys is essential to scan your website for SSL/TLS misconfiguration and vulnerabilities. It provides an in-depth analysis of your URL, including expiry day, overall rating, cipher, SSL/TLS version, handshake simulation, protocol details, BEAST, and much more.

Qualys Pros
Centralized vulnerability management
Low false positive rate
Powerful scanning engine
Qualys Cons
Pricing barrier for organizations on a budget
Some users found the setup difficult
Qualys Pricing
Qualys offers custom pricing based on a number of IPs, apps, etc.
Quttera
Best for Web Malware Scanning
Quttera is a suite of cybersecurity tools, including malware scanning & removal, DDoS protection, and a web application firewall.
Quttera’s malware-scanning engine protects websites from server-side infections and external threats by scanning every database file and preventing the spread of malware. It also offers DDoS protection, blacklist removal, and uptime monitoring.
Quttera also features an automated malware removal mode to perform continuous integrity checks on the CMS, PHP files, plugins, etc. Its DNS/IP monitoring keeps one notified of any change in DNS records, nameservers, IP addresses, and MX records. Users can also request manual malware removal to take care of XSS injections, trojans, spyware, code and JavaScript injections, malicious iFrames & redirects, etc.
Subscribers also benefit from Quattera’a WAF, which shields against the most common vulnerabilities, such as OWASP Top 10, server misconfigurations, SQL injections, XSS, and zero-day exploits.
Quttera Pros
Manual malware removal for affected sites
Top-notch tech support
Quttera Cons
No free trial or free tier.
Limited users to take feedback from
Quttera Pricing
- Essential Security: $10/month
- Premium Security: $179/year
- Emergency: $249/year
UpGuard
Best for Vendor Risk Management
UpGuard has multiple cybersecurity solutions for inspecting the attack surface of a business and associated vendors. Besides, it offers attack surface management for small businesses without any vendor assessment modules.
UpGuard detects vulnerabilities related to the operating system and vendor software, including those listed on the CISA KEV catalog. Every issue gets tagged with the appropriate CVE ID and CVSS score.
UpGuard also helps mitigate issues like bait and switching, domain parking, website imitation, phishing, and other typosquatting-related risks. Its data leak search engine checks every corner of the internet for sensitive documents, user PII, employee credentials, API keys, and more to help businesses take timely critical action.
UpGuard’s platform helps businesses identify and address security vulnerabilities such as insecure SSL/TLS certificates, open ports, and insecure HTTP. Their remediation planner assists in evaluating risk, prioritizing tasks, planning, collaborating, and tracking progress in one dashboard.
Another UpGuard USP is the real-time monitoring of linked domains and automatic domain discovery to identify misconfigurations and understand the overall risk profile.
UpGuard Pros
Risk management across the supply chain
Extensive data security
Offers API Access
Custom report templates
UpGuard Cons
Limited integration capabilities
Expensive for SMEs.
UpGuard Pricing
UpGuard pricing starts from $5,999/year.
SiteGuarding
Best for Real-Time Website Protection
SiteGuarding provides real-time website protection services for popular platforms, including malware removal, firewall, monitoring, backup, and security audits.
SiteGuarding emphasizes using manual expertise in addition to security automation. Users get protection against vulnerabilities such as malware, SQL injection, and XSS. It performs server-side scanning, server log analysis, detects file changes, prevents hacks & DDoS attacks, and aids in blacklist removal.
Moreover, businesses get assistance in extension installation, maintenance, upgrades, and troubleshooting. One can do a website scan without subscribing to any paid plans and can benefit from the 14-days free trial.
SiteGuarding Pros
24/7 Live support
Comprehensive security services
Extensive platform support
SiteGuarding Cons
Least user control except for getting reports.
Lesser-known service.
SiteGuarding Pricing
- Basic: €9.95/month
- Standard: €14.95/month
- Premium: €24.95/month
- Business: €99.95/month
Detectify
Best for Small to Medium Business
Detectify is an automatic attack surface management solution built by a community of ethical hackers. It scans domains for vulnerabilities such as XSS, SSRF, RCE, and DNS issues and notifies teams of any accidental information disclosure.
Users benefit from the custom policies to monitor specific changes and get a complete security overview, with the ability to filter and prioritize remediation.
Detectify provides security scans for web applications at various stages of development to identify security issues like SQL injections and SSL misconfigurations. Users can schedule scans directly or through the Detectify API.
Detectify Pros
Self-serve option for small websites
Extensive reporting
Enterprise features such as API access, SSO, etc.
14-day free trial
Detectify Cons
Expensive for small projects
Some G2 users find the UI confusing
Detectify Pricing
- Application Scanning from €82/month
- Surface Monitoring from €275/month
Probely
Best for Web & API Vulnerability Scan
Probely is an automated vulnerability scanner that checks and reports APIs and web apps for security issues and helps businesses fix them. It makes use of its headless Chrome-based crawler to find vulnerabilities in JavaScript-heavy apps and single-page applications.
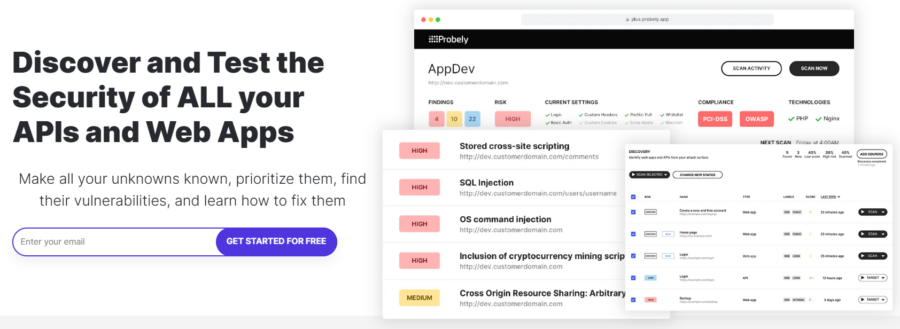
Probely offers flexibility by allowing direct integration into CI/CD pipelines or scheduling scans for application testing at scale. One can check the full list of vulnerabilities it detects in its help section, with the current one having XSS, SQL injection, OS command injection, Log4Shell, XEE, SSRF, RFI, and more.
The Probely scanner is highly accurate, especially with context-based vulnerability findings and supporting evidence. It provides detailed instructions on how to address issues and also includes an open-source agent for internal assets with similar scanning abilities.
Probely Pros
Free tier with five scans per month
Internal asset scans
Probely Cons
Limited scanning and report customization per some G2 users
Slightly expensive for small firms
Probely Pricing
- Lite: Free
- Pro: $98/month
- Enterprise: $665/month
Pentest Tools
Best for Web Penetration Testing
Pentest Tools Website Vulnerability Scanner is a reliable solution for detecting critical vulnerabilities such as XSS, SQL injection, and more. It is tested in real-life penetration testing engagements and automatically validates issues to eliminate false positives. It also has scanners for network health, SSL/TLS certificates, cloud misconfigurations, and DNS records.
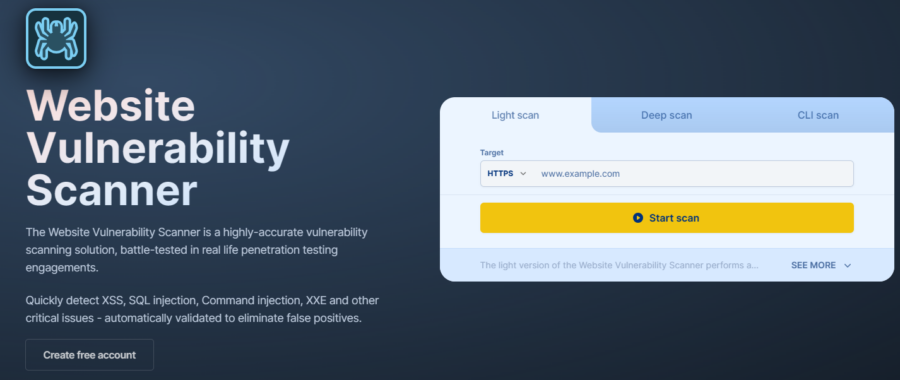
Pentest Tools web scanning uses a browser-based spider to scan single-page applications and JavaScript-rich websites with a low false positive rate. It can scan login-protected pages using multiple authentication protocols.
Pentest Tools is a cloud-based scanner that does not require local installation. It also allows scan scheduling and uses its REST API for integration into existing workflows, such as CI/CD pipelines. Besides, it supports scanning subjects hosted on internal networks, intranets, private clouds, etc.
Pentest Tools reports in a user-friendly way, with detailed guidance for manual validation and remediation. Users can experience all this goodness with the free tier, offering protection for up to five assets with two parallel scans.
Pentest Tools Pros
Range of tools for in-depth testing and security posture analysis
Easy to use, with good remediation assistance
Low false positives rate
Offers Out-of-band detection
Supports API integration
Pentest Tools Cons
UI can be slightly overwhelming for beginners
Paid plans can be pricey for individuals
Pentest Tools Pricing
- Free: $0
- Basic: $85/month
- Advanced: $190/month
- Teams: $395/month
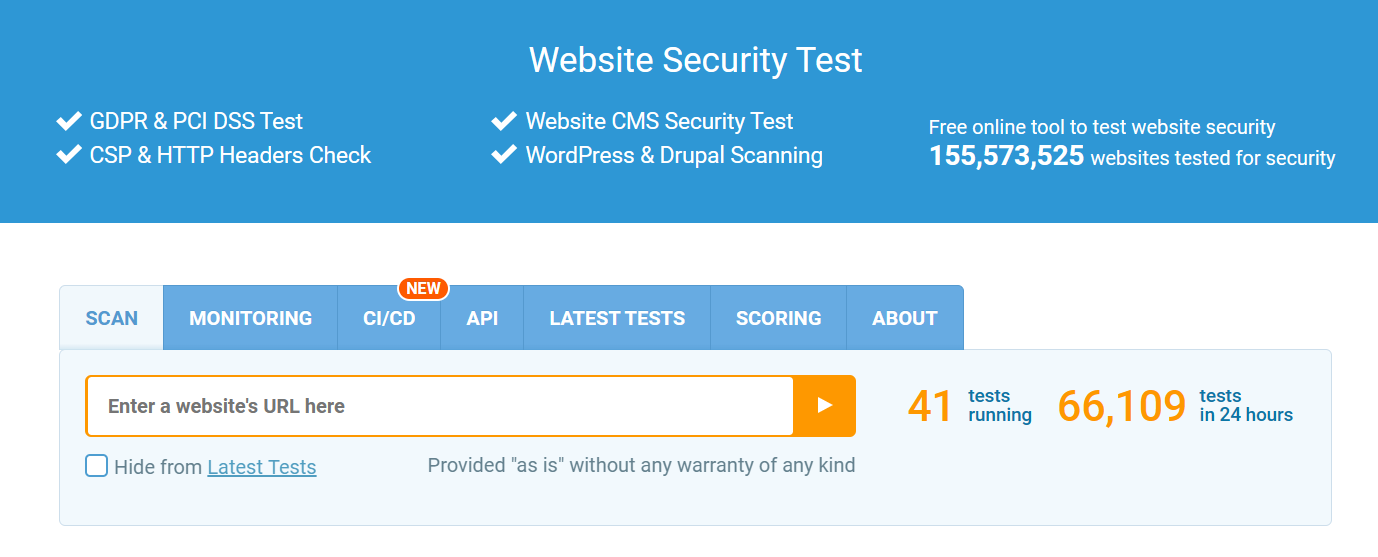
ImmuniWeb
Best FREE Security Scanner
ImmuniWeb has a suite of AI-powered security tools for websites, APIs, network assessment, cybersecurity compliance, and more. In addition, it works for single-page applications, cloud-native apps (at AWS, Azure, or GCP), and open-source apps.
ImmuniWeb Neuron, its web application security product, stands out from the rest of the competition by offering an SLA-backed zero-false positive guarantee. It supports automated testing and CI/CD workflow integration to ensure secure software development from the get-go.
ImmuniWeb web security scanning detects OWASP Top 10, OWASP API Top 10, insecure HTTP Headers, and SSL/TLS issues. Its vulnerability detection is compatible with 400+ CMSs, 150,000+ themes and plugins, 12,000+ JavaScript libraries, and 10,000+ known CVE-IDs. It also offers a mobile app vulnerability checker.
ImmuniWeb has quote based plans and a free scanner to test out its abilities.
ImmuniWeb Pros
Scan automation with extensive vulnerability support
Comprehensive attack surface management
Security addons for dark web monitoring, mobile app testing, etc.
ImmuniWeb Cons
Some users may find the reports too technical and difficult to understand
Limited customer support options
ImmuniWeb Pricing
ImmuniWeb offers custom pricing based on your specific requirements.
Invicti
Best for DAST+IAST Scanning
Invicti uses DAST+IAST-based scanning to safeguard websites, web applications, web services, and APIs from vulnerabilities, such as SQL injections, XSS, directory traversal, OS command injection, remote code execution, SSL issues, and more. It also runs configuration tests for web servers such as Apache, Nginx, and Microsoft IIS.
Invicti proof-based scanning reduces the number of false positives by safely and automatically exploiting vulnerabilities. Its vulnerability scanner deploys a Chrome-based crawling engine, which can work for even the most complex JavaScript/Ajax-based applications.
Although Invicti can function independently, teams can integrate it into their SDLC, DevOps, and CI/CD workflows to identify security issues early on.
Invciti comes in two editions: on-premise and hosted, and offers unlimited user seats without any cap on the number of scans.

Invicti Pros
Great customer support
Provides detailed reports and analysis
Low number of false positives
Invicti Cons
Lack of upfront pricing
Scans sometimes take a long time
Invicti Pricing
Invicti offers custom pricing based on your specific requirements.
Veracode
Best to Find and Fix Runtime Vulnerabilities
Veracode’s cloud-based dynamic analysis helps businesses run multiple scans to simultaneously identify runtime vulnerabilities in web applications and APIs, including those in pre-production or staging environments.
Its scanning engine supports easier integration with the existing tech stack to receive quick and actionable results with a low false positive rate. Veracode covers a wide range of security threats, such as open-source vulnerabilities and OWASP Top 10 (broken authentication, misconfigurations, injection, etc.).
Veracaode also maintains a database of the exclusive vulnerabilities discovered by their in-house researchers. It has a single interface indicating a business’s overall security posture, with the ability to benchmark against your industry peers.
Veracode Pros
High-quality automated testing
Integration with IDE and CI/CD pipelines.
AI-assisted flaw remediation
Veracode Cons
UI is non-intuitive
Absence of clear-cut subscription plans
Veracode Pricing
Veracode offers custom pricing based on your specific requirements.
Qualys SSL Labs
Best for TLS Testing
Qualys SSL Labs tests the security of websites and web servers, specifically focusing on TLS. It gives a detailed report on a website’s TLS configuration and identifies vulnerabilities that need to be addressed for a secure connection. It also provides a detailed SSL configuration analysis for any public-facing web server.
Qualys SSL Labs is a free tool that helps ensure websites are up to date with the latest security standards and protocols by providing constant updates and best practices. Simply input the domain name to receive results.
Qualys SSL Labs reports for certificate validity and strength, support for modern SSL/TLS protocols and cipher suites, browser compatibility, and a few other features such as forward secrecy, HSTS, and more. Finally, a website is graded based on the results.
Qualys SSL Labs Pros
100% Free & in-depth SSL configuration assessment
Offers detailed reporting
Qualys SSL Labs Cons
Provided information can be overwhelming for beginners
Little remediation guidance
Best Website Scanner Comparison
Here, we compare the best website scanners on the basis of scan depth, free trial, and key features.
| Website Scanner | Scan Depth | Free Tier/Trial | Key Features |
|---|---|---|---|
| Sucuri | WordPress, Magento, Joomla, phpBB, Drupal | No | Expert support, WAF, Free scans, CDN |
| HostedScan | Networks, Servers, Web Applications | Yes | Open-source scanners, Centralized vulnerability management |
| Intruder | Web Apps, APIs, CMS (WordPress, Drupal, Joomla, Squarespace) | 14-day Free Trial | Real-time protection, Automated scans, Network monitoring |
| Qualys | Web applications, APIs | No | Consolidated dashboard, manual testing |
| Attaxion | Websites, IPs, SSLs, Emails, Ports, Cloud assets | 30-Day Trial | Reports with CWE & CVE IDs |
| Quttera | Websites | No | Manual malware removal, Extensive cybersecurity |
| UpGuard | Operating systems, Vendor software, SSLs, Emails, Ports | No | Vulnerability detection with CVE ID & CVSS scores |
| SiteGuarding | WordPress, Joomla, Drupal, phpBB, Magento, PrestaShop & OpenCart | 14-day Free Trial | 24*7 Manual monitoring & protection |
| Detectify | Web applications | 14-day Free Trial | Scheduled scans, Remediation prioritization |
| Probely | APIs, Web Apps, Internal Assets | Yes | Context-based findings, Detailed remediation guidance |
| Pentest Tools | Web apps, APIs, CMS (WordPress, Drupal, Joomla, & SharePoint), Internal assets | Yes | Vulnerability validation & Remediation guidance |
| ImmuniWeb | Websites, Mobile apps, APIs, Networks, Cloud assets, SSL/TLS | No | Zero false positive SLA, CVE, CWE, & CVSS scores |
| Invicti | Websites, Web apps, Web services, APIs, Web servers | No | Proof-based scanning, Automatic vulnerability exploitation |
| Veracode | Web Apps, APIs | 14-day Free Trial | Benchmarking across industry, Low false positives |
| SSL Labs | Websites | 100% Free | Checks for supported browsers and TLS protocols |
What is a Website Security Scanner?
A website vulnerability scanner checks for security risks on the website, including source code, outgoing links, third-party libraries, and outdated software. It helps identify vulnerabilities such as malware, SQL injection, DDoS, and cross-site scripting. It helps to ensure the website stays protected from known threats, cyberattacks, and malicious requests.
How to Choose the Best Website Scanner?
Choosing the best website scanner means considering a few factors, such as potential vulnerability detection, user experience, and much more, as explained below.
- Website Complexity: A dynamic website is made up of different components, such as databases, APIs, plugins, and more. Consequently, the scanner should support these individual pieces for comprehensive reporting. On the other hand, simple scanners are enough for basic HTML websites.
- Technical Expertise: It’s important to consider the technical depth required for performing scans and understanding results. Some scanners may need manual configuration and result interpretation, while a few other tools might offer assessment assistance and recommendations.
- Vulnerability Coverage: These tools should at least cover the OWASP top 10 security risks and report emerging threats for the specific technology stack. Besides, it’s good to have an integrated network scanner for improving overall security and efficiency.
- Reporting & Remediation: Every scan should return an executive summary and the vulnerabilities with their severity levels (CVSS scores). Besides, pick a scanner that provides guidance on how to fix those vulnerabilities.
- Pricing & Scan Frequency: It’s important to consider the stakes before opting for the security package. Continuous scans are the safest, but there are tools like HostedScans, which lets you scan websites for vulnerabilities for free. However, there is no alternative to regular scanning. As a thumb rule, run vulnerability scans after implementing any change.
Best Practices to Secure Website
Website security is a multi-faceted phenomenon, best achieved by deploying stack-specific best practices. Still, here are some thumb rules to help you get started in the right direction.
- Keep everything updated: Keep the base code, plugins, and everything else updated to their latest versions.
- Access protection: Use strong passwords and two-factor authentication to protect access. Besides, try hiding/masking the login URL to avoid brute-force attacks.
- Limit third-party plugins: Third-party plugin integrations increase the attack surface. So, it’s advised to keep them at a minimum number for a better security posture.
- Real-time scans: Real-time scans can notify you immediately if an attack occurs, enabling you to take quick remedial action.
- Host your website in isolated environments: Websites hosted in isolated environments are generally safer than a league of projects co-hosted on a single server.
- Keep backups: Despite everything, hacks and breaches can happen to the biggest of websites. Ergo, take regular backups to have the latest copy of your website handy.
- Implement firewall: Having a web application firewall (WAF) helps regulate traffic between a website and the rest of the internet. It blocks malicious traffic and can be customized to fit the evolving threat landscape.
If you’re worried about cross-site scripting (XSS), choose a top XSS scanner that accurately detects both reflected and stored XSS attacks. It helps catch not just common issues but also more hidden, targeted threats.
Frequently Asked Questions
The most common web security threats involve SQL injection, cross-site scripting (XSS), DDoS, malware, phishing, brute force attacks, and more.
Regular website security scans should be conducted weekly to promptly identify vulnerabilities, and for high-traffic or sensitive sites, daily scans are recommended for maximum protection.

