Did you know a hacker can make bank transfers or online purchases on your behalf without stealing your registration information?
We associate cookies with tracking and annoying online ads, but they also store search queries, allowing us to visit websites without entering a username and password.

However, if someone intercepts the cookie, then this can lead to a catastrophic cyberattack called session hijacking, which can put your sensitive data at risk at the hands of attackers, and it can do a lot of damage before you even know what happened.
Let’s find out what it is and how you can prevent it!
What is Session Hijacking?
In session hijacking, an attacker intercepts and takes over an established session between a user and a host, such as a web server, Telnet session, or any other TCP-based connection. A session starts once you log into a website or application, for example, a social networking website.

It continues while you are inside the account, checking your profile or participating in a thread, and ends when you log out of the system. But how does the web server know that every request you make is actually from you?
This is where cookies come in. After logging in, you submit your credentials to the web server. It confirms who you are and gives you a session ID using a cookie that will be attached to you for the duration of the session. That’s why you don’t log out of an application every time you visit someone’s profile and why the online store remembers what you put in your shopping cart even if you refresh the page.
But attackers can hijack the session if they use special session management techniques or steal your cookie. Thus, it can fool the web server into believing that the requests are coming from you, the authorized user.
The phenomenon of session hijacking became famous in the early 2000s, but it is still one of the most common methods used by hackers.
A recent example is the Lapsus$ Group, which became part of the FBI’s Most Wanted list this year.
Session Capture Types
Session hijacking can be divided into two main categories, depending on the perpetrator’s wants.
Active: In an active attack, the attacker takes over your session, thus taking the legitimate client’s connection to the resource. Depending on the session’s site, the hacker can make online purchases, change passwords, or recover accounts. A common example of an active attack is a brute force attack, XSS, or even DDoS.

Passive: In a passive attack, the attacker does not take over or alter the session. Instead, they quietly monitor the data traffic between your device and the server, collecting all sensitive information. Usually, IP Spoofing and malware injection are used to carry out passive injection attacks.

How Does Session Hijacking Work?
HTTP is a stateless protocol, meaning the server has no memory of the client’s operation. Each new HTTP request coincides with a new unit of work, or to put it more simply, the server serves pages to the client without remembering the client’s previous requests.
When we browse the web, however, we realize that applications ideally know who the client is (even too well!). Thanks to this “memory” of the server, ” it is possible to create modern reserved areas of websites, online banks, webmail services, etc.
To do this, an appendage was born that makes a stateless protocol like HTTP stateful: cookies.
Stateful Sessions
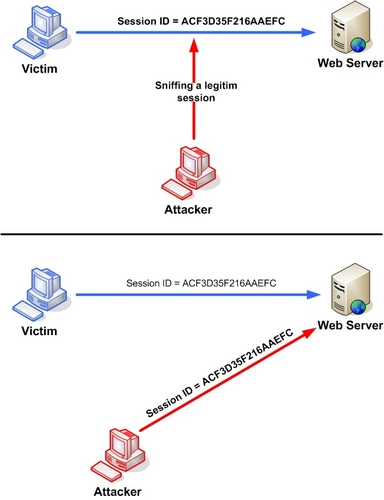
Once logged in, web applications that use the stateful session drop a session cookie. It means that they rely on this cookie to track the client. Inside the cookie is saved a unique code that allows the recognition of the client, for example:
SESSIONID=ACF3D35F216AAEFC
Anyone with the above-mentioned unique session id or code would be the authenticated client for the server. If an attacker could get this identifier, as seen in the picture below, they could exploit the session initially validated for their victim either by sniffing a legitimate session or even taking over the session completely. This identifier is usually embedded in the URL, in any form’s hidden field, or in cookies.
Stateless sessions
With the evolution of the web, solutions have arisen to manage the “memory” of the server without using session cookies. In a web application where the frontend and backend are well separated and talk only via API, the best solution might be a JWT (JSON Web Token), a signed token that allows the frontend to consume the APIs provided by the backend.
Usually, the JWT is saved in the browser’s sessionStorage, a memory area that the client keeps active until the tab is closed. Consequently, opening a new tab creates a new session (as opposed to what happens with cookies).
Stealing the client’s identification token allows you to steal the user’s session and thus carry out a session-hijacking attack. But how to steal that token?
Currently, the methods most used by hackers are:
#1. Session Side Jacking
This method uses insecure networks to find out your session ID. The attacker uses sniffing (special software) and usually targets public Wi-Fi or websites without an SSL certificate, which are known for poor security.
#2. Session Fixation
The victim uses the session ID created by the attacker. It can do this with a phishing attack (via a malicious link) that “fixes” your session ID.
#3. Brute Force
The most time-consuming and inefficient method. During this attack, the hacker does not steal your cookies. Instead, it tries every possible combination to guess your session ID.
#4. XSS or Cross-site Scripting
A hacker exploits vulnerabilities in websites or applications to inject malicious code. When a user visits the site, the script is activated, steals the user’s cookies, and sends them to the attacker.

#5. Malware Injection
Malicious software can perform unauthorized actions on your device to steal personal information. It is also often used to intercept cookies and send information to an attacker.
#6. IP Spoofing
A cybercriminal changes the source IP address of their packet to make it appear to be coming from you. Because of the fake IP, the web server thinks it’s you, and the session gets hijacked.
Session Hijacking Examples
#1. Firesheep
A Firefox extension (Firesheep) made by security researchers Erik Butler & Ian Gallagher in 2010 highlighted the importance of HTTPS and the dangers of unencrypted WiFi networks.
Firesheep allowed people on the same unencrypted WiFi network to sniff each other’s non-HTTPS activity. Using this, one could copy the session cookie and take over someone else’s online account.
Though it was made for security awareness, it highlighted the waiting-to-be-exploited loophole, which could have disastrous consequences for many users.
Reactively positively, many websites, including Facebook, Twitter (now X), etc., made HTTPS the default connecting protocol.
#2. YouTube Accounts Hijacking
Throughout 2021, YouTubers with high subscriber counts were the target of this cookie theft campaign.
The creators received phishing emails that took them to dangerous replicas of legitimate websites. A few users fell for this and ended up downloading malware on their devices, which helped the perpetrators steal session cookies for their YouTube accounts.
Ultimately, this resulted in their YouTube accounts being taken over and used for illicit purposes such as cryptocurrency scams. Besides, a few accounts were sold at online black markets for thousands of dollars, depending on the subscriber counts.
#3. FlyTrap
In 2021, FlyTrap surfaced as an Android malware that stole Facebook sessions by luring users to sign into malicious apps using their Facebook credentials.
The malicious applications available at the Google Play store were since removed. It deployed social engineering tactics, such as giving coupons, voting for their favorite soccer team, etc.
Ultimately, users would sign in via Facebook legitimately but within a web view portal designed to hijack the session cookies and personal information. Everything went to FlyTrap servers, which roughly victimized 10K users in over 140 countries.
How to Prevent Session Hijacking?
The possibility of session hijacking usually comes down to the security of the websites or applications you use. However, there are steps you can take to protect yourself:
- Avoid public Wi-Fi, as free hotspots are ideal for cybercriminals. They usually have poor security and can be easily spoofed by hackers. Not to mention that they are always full of potential victims whose data traffic is constantly compromised.
- Any site not using an SSL certificate makes you vulnerable, as it cannot encrypt traffic. Check if the site is secure by looking for a small padlock next to the URL.

- Install an anti-malware application to detect and protect your device from malware and rats that can steal personal information.
- Avoid downloading malware by using official app stores or websites to download apps.
- If you receive a message asking you to click on an unfamiliar link, don’t do it. This could be a phishing attack that can infect your device and steal personal information.
The user can do little against a Session Hijacking attack. On the contrary, however, the application can notice that a different device has connected with the same session identifier. And relying on that, you can design mitigation strategies such as:
- Associate to each session some technical fingerprint or characteristics of the connected device to detect changes in the registered parameters. This information must be saved in the cookie (for stateful sessions) or the JWT (for stateless sessions), absolutely encrypted.
- If the session is cookie-based, drop the cookie with the HTTPOnly attribute to make it unreachable in case of an XSS attack.
- Configure an Intrusion Detection System (IDS), Intrusion Prevention System (IPS), or networking monitoring solution.
- Some services perform secondary checks on the user’s identity. For example, a web server could check with each request that the user’s IP address matches the last one used during that session. However, this does not prevent attacks from someone sharing the same IP address and could be frustrating for users whose IP address may change during a browsing session.
- Alternatively, some services will change the cookie value with each and every request. This drastically reduces the window in which an attacker can operate and makes it easier to identify if an attack has occurred, but can cause other technical problems.
- Use different multifactor authentication (MFA) solutions for each user session.
- Keep all systems up to date with the latest patches and security updates.
FAQ
Session hijacking involves pretending to be the user, whereas spoofing involves replacing the user. Over the last few years, some security analysts have begun to characterize the latter as a type of session hijacking.
Final Words
Session hijacking is a method by which a hacker can communicate with a server pretending to be a genuine user, using the session token or cookie.
The frequency of session hijacking attacks has increased recently; therefore, it has become increasingly important to understand such attacks and follow preventive measures.
However, just as technology is developing, the attacks are also becoming more sophisticated; therefore, it’s essential to create active mitigation strategies against session hijacking.


