24 Best SSL Checker Tools to Troubleshoot TLS and Certificate Issues
Stay up to date on Tech and Business News. Join Geekflare Newsletter →
Safeguard your online presence with expert security tips and tools. Protect against malware, enhance website security, and stay ahead of the latest cyber threats.

24 Best SSL Checker Tools to Troubleshoot TLS and Certificate Issues

12 HTTP Client and Web Debugging Proxy Tools
Best Website Defacement Monitoring Tools in 2025

9 Best Tools to Monitor Website Changes in 2025

Best Enterprise Password Managers for 2025

9 Best Threat Intelligence Platforms in 2025

18 Best Web Application Firewall Software [Top Picks]

Red Light, Green Light: Endpoint Security Edition

8 Vulnerable Web Applications to Practice Hacking Legally

13 Best GRC Tools to Manage Risk and Compliance
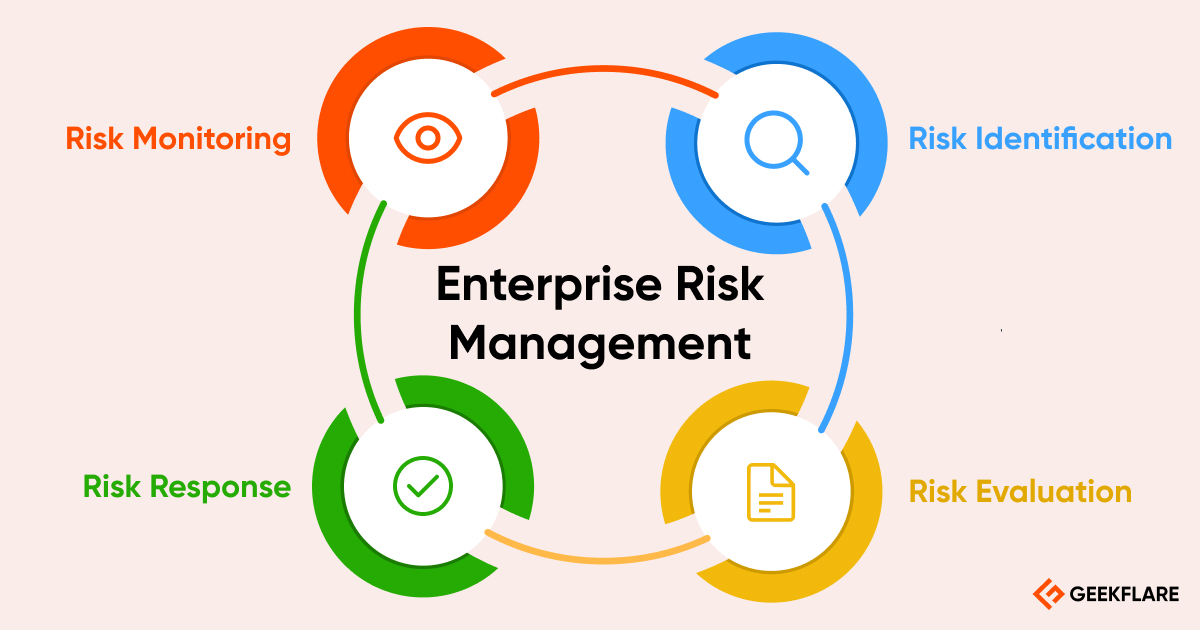
15 Best ERM Software for 2025
Best IPS Software for Real-Time Threat Defense

Astra Pentest Reviewed – Easy, Continuous Vulnerability Scanning & Compliance

8 Best SOAR Tools and Solutions for Small to Enterprise Business
5 Runtime Application Self-Protection (RASP) Tools for Modern Applications

Network Security – Basics and 12 Learning Resources

10 Best Incident Response Tools for Your Organization

Best OSINT Tools for Cyber Investigations

8 Tools to Scan Node.js Applications for Security Vulnerability
How to Find Real IP (Origin) address of Website?

14 Tools to Monitor SSL Certificate Expiry from Cloud and Scripts

19 Phishing Statistics and Trends [Updated 2025]

15 Open Source Vulnerability Scanners for 2025

28 FREE Forensic Investigation Tools for IT Security Expert

How to Implement CSP frame-ancestors in Apache, Nginx and WordPress?

How To Check What Technology a Website Is Built With?
How to Install Kali Linux with VMware Fusion? [Step by Step Guide]
How to Find the Subdomains of a Domain

How to Unblock Websites: Best Methods and Tools

Is Dashlane Worth the Hype? My Testing Experience in 2025