Applications have become the number one target for attackers.
Hackers are constantly scanning for vulnerabilities in your application code. If they find one, the result isn’t just a headache, it’s a data breach that can impact your business and destroy customer trust.
With threats evolving so quickly, traditional security measures often struggle to keep up. So, what is the solution?
You need to let your apps protect themselves.
It sounds unreal?
Well, the technology exists. It’s called Runtime Application Self-Protection (RASP). By integrating RASP, your applications gain a built-in shield that identifies and blocks attacks in real-time, from the inside out.
in this article, we’ll explore the top RASP tools that help you build secure applications.
OpenRASP
OpenRASP is an open-source RASP solution by Baidu. Unlike traditional Web Application Firewalls (WAFs) that rely on checking network signatures against a database of known threats, OpenRASP integrates directly into the application server via instrumentation.
OpenRASP places hooks on sensitive functions within your application such as database queries, file operations, and network requests. This allows the tool to examine inputs in real-time and block malicious code before it is executed. Because it understands the context of the request, it is immune to malformed protocol evasions that often trick WAF.
Key Features
- Detection logic is implemented via JavaScript plugins.
- It typically only triggers alarms for attacks that would actually succeed, filtering out the noise.
- It uses a semantic engine to identify anomalies like code injection or deserialization without needing constant signature updates.
- It provides detailed stack traces in its logs which is easier for developers to locate and fix the vulnerability.
OpenRASP supports Java and PHP. It integrates with existing SIEM/SOC tools like Flume, rsyslog, and LogStash by exporting alarms in standard JSON format.
Jscrambler Code Integrity
Jscrambler specializes in client-side RASP to protect your web applications from abuse, tampering, code theft, and piracy. It is a go-to solution for enterprises to secure JavaScript logic and intellectual property.
Jscrambler combines enterprise-level JavaScript obfuscation with runtime protection. Every time you build your application, Jscrambler transforms your code into a secure version that hides the logic while keeping the original functionality intact. This makes it incredibly difficult for attackers to reverse-engineer.
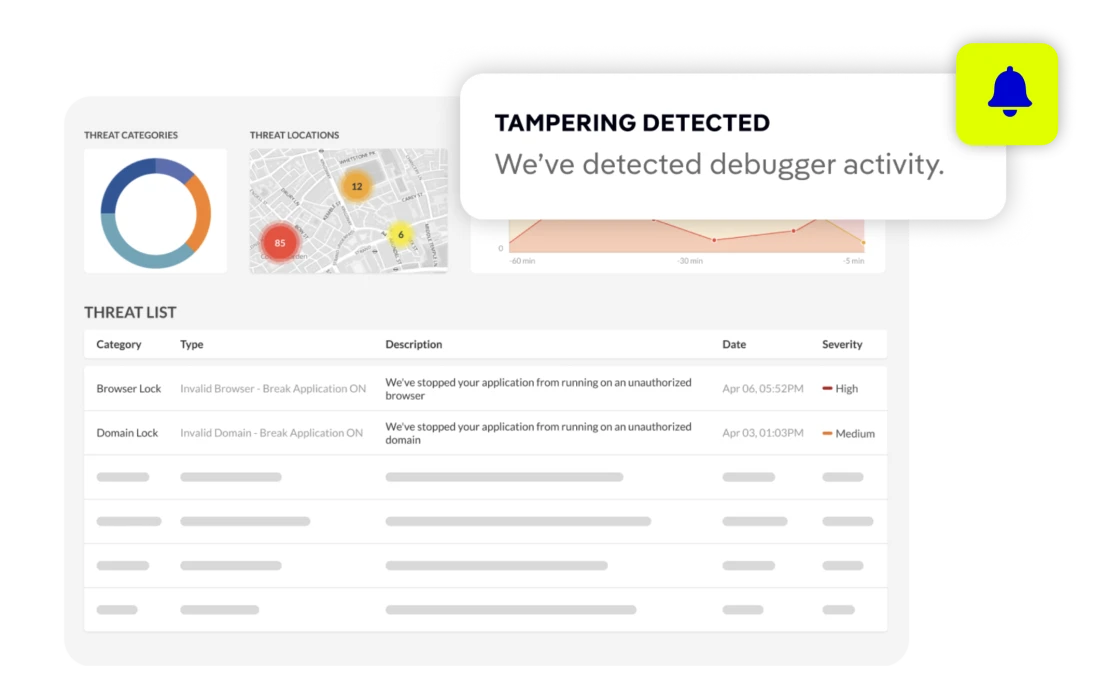
Key Features
- You can restrict where your app runs. If someone tries to run your code on an unauthorized domain, browser, or OS, the application will break.
- Jscrambler monitors your code as it runs on the client’s browser. It detects tampering, debugging, and monkey patching attempts in real-time.
- You can set up automatic reactions to threats, such as redirecting the attacker, triggering a custom function, or crashing the app to prevent data theft.
Jscrambler fits into CI/CD pipelines and is compatible with all major JavaScript frameworks React, Angular, Vue, etc. It offers a dashboard for monitoring security alerts and managing team access.
Imperva RASP
Imperva RASP (formerly Prevoty) is a market leader in the runtime protection space. It is famous for its ability to protect both legacy applications and cloud-native apps with a single autonomous plugin.
Unlike tools that rely on signatures or pattern matching, Imperva uses a patented technique called Language Theoretic Security (LANGSEC). This method analyzes the payload within the context of how the code will actually execute.
By understanding the intent of the code, Imperva can neutralize known attacks and Zero-Day exploits without needing constant signature updates.
Imperva offers massive coverage against the OWASP Top 10 and beyond, including:
- Injections: SQLi, Command Injection, OGNL, JSON, XML, and HTML Injection.
- Data Integrity: XSS, CSRF, and Clickjacking.
- Weak Configurations: Insecure cookies, weak cryptography, logging sensitive info, and path traversal.
Contrast Security
Contrast Security takes a unique approach by embedding sensors into the application code using instrumentation. This allows the software to protect itself from within.
Contrast sees the data flow inside the running application. It builds a real-time map of your software called the Contrast Graph which covers your custom code, APIs, and third-party dependencies.
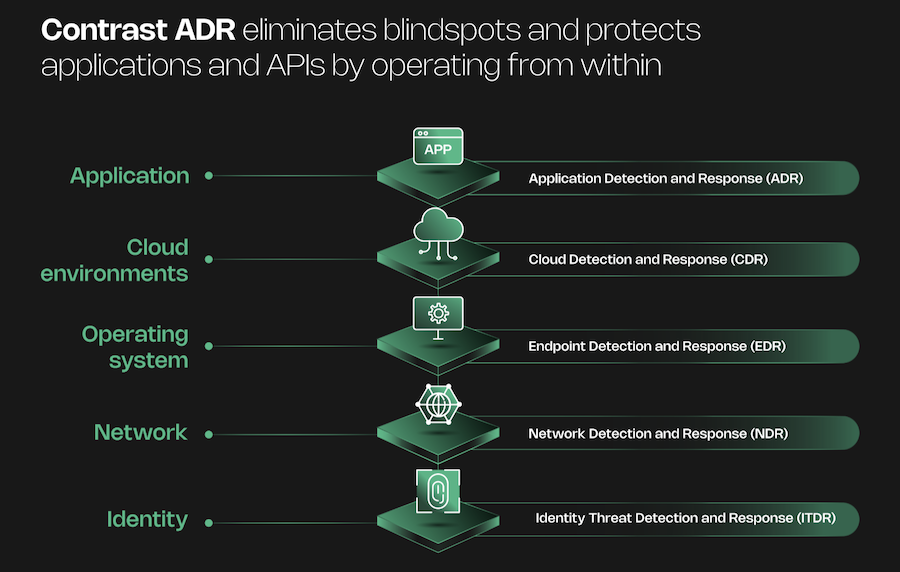
Key Features
- Application Detection and Response (ADR) detects and blocks exploits including Zero-Days in production by analyzing how the application processes data.
- It uses AST to find vulnerabilities during development and ADR to block attacks in production.
- Using Contrast AI Smart Fix, it suggests targeted code fixes that developers can apply in minutes.
- It automatically creates an inventory of all libraries and dependencies.
UUSEC WAF
UUSEC WAF is a comprehensive web application security platform that goes beyond traditional traffic filtering. In its Business Edition, it integrates a RASP module alongside a Host Intrusion Prevention System (HIPS), creating a unique Three-Layer Defense architecture.
The Three-Layer Defense
- Traffic Layer (WAF): It uses AI and semantic engines to filter malicious web traffic before it reaches the server.
- System Layer (HIPS): It protects the underlying operating system by intercepting low-level attacks at the kernel layer.
- Runtime Layer (RASP): The RASP module inserts itself directly into the runtime engine like Java JVM or PHP Zend. It tracks the execution context in real-time to detect and block complex exploits, including Zero-Day vulnerabilities that bypass the WAF.
Datadog ASM
Best for DevSecOps teams who want Security and Observability.
Datadog has rapidly evolved from cloud monitoring solutions into a major player in application security, largely due to its strategic acquisitions of Sqreen and Hdiv. By integrating these technologies, Datadog ASM delivers code-aware protection.
Datadog leverages the same agents used for performance monitoring (APM) to provide security. This means if you are already using Datadog, you likely have the infrastructure for RASP installed, you just need to enable it.
Key Features
- It traces attacks from the IP address down to the specific line of code and stack trace.
- Identify Account Takeovers (ATO), credential stuffing, and abuse of sensitive flows like checkout or login pages.
- You can choose to block threats at the Edge or deep inside the application service layer.
- Because security alerts are correlated with logs, traces, and metrics, you can see exactly how an attack impacted your application’s performance and stability in real-time.
Datadog offers 14-days free trial.
What is RASP?
RASP protects an application while it is running. Unlike perimeter defenses, RASP analyzes both the application’s behavior and the context of that behavior to identify malicious inputs.
It continuously monitors the app to detect and mitigate attacks without requiring human intervention.
RASP incorporates security directly into the running application, regardless of where the server resides. By intercepting calls from the app to the system, it validates requests directly inside the application. It protects both web and non-web apps and can be deployed without altering your application’s logic.
Essentially, RASP software integrates with the application’s runtime environment to provide a built-in shield against threats.
RASP vs. WAF
While both tools aim to secure applications, they operate at completely different layers of the stack.
- WAF inspects incoming HTTP packets for known attack signatures. It operates based on probability, guessing if a payload is malicious based on its appearance.
- RASP hooks into the application’s execution flow. It operates based on actual behavior, monitoring if a payload attempts to execute a malicious command.
- Because WAFs lack visibility into the application logic, they often block safe requests that merely resemble attacks. RASP eliminates this guesswork. It analyzes the data after it has been decoded and processed by the app.
- WAF requires constant manual tuning to match new application logic. RASP, however, travels with the application. No matter how often you deploy or which language you use, RASP automatically adapts to protect the new code immediately.
Which RASP is right for you?
Integrating Runtime Application Self-Protection is one of the highest ROI security decisions you can make.
- Go with OpenRASP if you have a strong engineering team that wants an open-source solution you can customize yourself.
- Choose Jscrambler if your primary risk is on the client-side.
- Select Contrast Security or Imperva if you are a large enterprise needing virtual patching, and support for legacy applications.
- Pick Datadog or UUSEC if you want to consolidate your tool stack.



